1- 生成证书文件
openssl genrsa -out leman.com.key 2048 #创建根证书的私匙
openssl req -new -subj "/C=CN/ST=GuangDong/L=ShenZhen/O=leman/OU=leman.com/CN=leman.com" -key leman.com.key -out leman.com.csr #用私钥创建签名请求
openssl x509 -req -days 3650 -in leman.com.csr -signkey leman.com.key -out leman.com.crt #用Key签名证书
root@raspberrypi:/home/pi# openssl x509 -req -days 3650 -in leman.com.csr -signkey leman.com.key -out leman.com.crt
Signature ok
subject=C = CN, ST = GuangDong, L = ShenZhen, O = leman, OU = leman.com, CN = leman.com
Getting Private key
2- nginx配置ssl验证
ls -l /var/www/ssl/ #把证书移到该目录下
total 12
-rw-r--r-- 1 root root 1229 Jun 21 22:25 leman.com.crt
-rw-r--r-- 1 root root 1009 Jun 21 22:24 leman.com.csr
-rw------- 1 root root 1675 Jun 21 22:20 leman.com.key
##写入nginx配置文件
cat /etc/nginx/sites-enabled/leman.com.conf
server {
listen 443 ssl;
server_name leman.com;
root /var/www/https;
index index.html;
access_log /var/log/nginx/leman.com.access_log;
ssl on;
ssl_certificate /var/www/ssl/leman.com.crt;
ssl_certificate_key /var/www/ssl/leman.com.key;
ssl_session_timeout 5m;
ssl_protocols SSLv2 SSLv3 TLSv1;
ssl_ciphers EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH;
ssl_prefer_server_ciphers on;
}
mkdir -p /var/www/https/
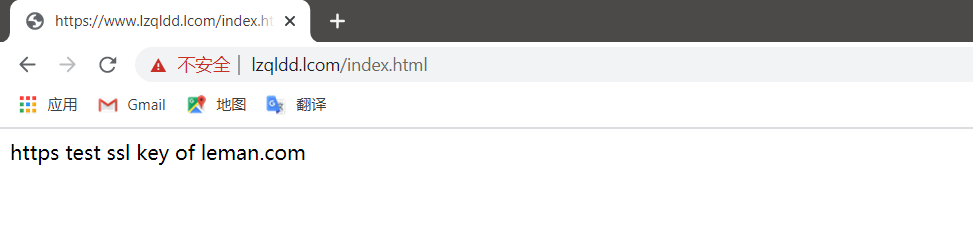
echo "https test ssl key of leman.com" > /var/www/https/index.html
systemctl restart nginx #重启nginx服务
3- 浏览器打开nginx服务器地址