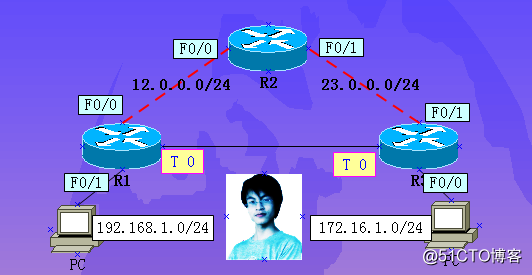
第一步:配置基本路由:见图
第二步:配置tunnel
R1(config)#interface tunnel 1
R1(config-if)#ip add 10.0.0.1 255.255.255.252
R1(config-if)#tu so f0/0
R1(config-if)#tu destination 23.0.0.3
R3(config)#int tunnel 1
R3(config-if)#ip add 10.0.0.2 255.255.255.252
R3(config-if)#tu so f0/1
R3(config-if)#tu de 12.0.0.1
//上面三行分别是:
- 定义tunnel的ip地址
- 定义隧道的源地址,可以写接口
- 定义隧道的目标地址
第三步:配置路由协议
R3(config)#ip route 0.0.0.0 0.0.0.0 f0/1
R1(config)#ip route 0.0.0.0 0.0.0.0 f0/0
R1(config)#router ei 1
R1(config-router)#no au
R1(config-router)#net 129.168.1.1
R1(config-router)#net 10.0.0.0
R3(config)#router ei 1
R3(config-router)#no au
R3(config-router)#net 10.0.0.0
R3(config-router)#net 172.16.1.1
//R2 为ISP不能运行路由协议,这是因为运营商不可能将大量的路由信息转发到本地路由
第四步:配置IPSEC ***
R1(config)#crypto isakmp enable
R1(config)#crypto isakmp key 6 ccie address 23.0.0.3
R1(config)#crypto isakmp policy 10
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#encryption 3des
R1(config-isakmp)#group 2
R1(config-isakmp)#hash md5
R1(config)#crypto ipsec transform-set r1 esp-3des esp-sha-hmac
R1(cfg-crypto-trans)#mode transport
R1(config)#access-list 100 permit ip 192.168.1.0 0.0.0.255 172.16.1.0 0.0.0.255
R1(config)#int tunnel 1
R1(config-if)#crypto map libo1
R1(config)#crypto map libo1 1 ipsec-isakmp
R1(config-crypto-map)#set peer 23.0.0.3
R1(config-crypto-map)#set transform-set r1
R1(config-crypto-map)#match add 100
//以上步骤为IPSEC ***的全部过程
R2上的配置与之对应
第五步:测试
R1#ping 172.16.1.1 so 192.168.1.1 repeat 20
Type escape sequence to abort.
Sending 20, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
.!!!!!!!!!!!!!!!!!!!
Success rate is 95 percent (19/20), round-trip min/avg/max = 12/55/148 ms
//这里通了19个包,我们猜想会用19个包加密
R1#sh crypto engine connections active
ID Interface IP-Address State Algorithm Encrypt Decrypt
1 Tunnel1 10.0.0.1 set HMAC_MD5+3DES_56_C 0 0
2 Tunnel1 10.0.0.1 set HMAC_MD5+3DES_56_C 0 0
2001 Tunnel1 12.0.0.1 set 3DES+SHA 19 0
2002 Tunnel1 12.0.0.1 set 3DES+SHA 0 19
//这里看到有19个包加密
第六步:为了使公司内部的 pc有一个良好的上网环境,我们组R1与R3做PAT
R1(config)#access-list 111 deny ip 192.168.1.0 0.0.0.255 172.16.1.0 0.0.0.255
R1(config)#access-list 111 permit ip 192.168.1.0 0.0.0.255 any
R3(config)#access-list 111 deny ip 172.16.1.0 0.0.0.255 192.168.1.0 0.0.0.255
R3(config)#access-list 111 permit ip 172.16.1.0 0.0.0.255 any
R1(config)#ip nat inside source list 111 interface f0/0 overload
//这里注意的是,出接口要在f0/0
第七步:定义inside和outside接口
R1(config)#int f0/1
R1(config-if)#ip nat inside
R1(config-if)#int f0/0
R1(config-if)#ip nat outside
第八步:综合测试包括PAT和***
- 先测试PAT
pc1#ping 2.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
!!!!! //ping正常
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/46/92 ms
pc1#2.2.2.2
Trying 2.2.2.2 ... Open
R2#exi //这里显示成功
[Connection to 2.2.2.2 closed by foreign host]
R1#sh ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 12.0.0.1:1 192.168.1.2:1 2.2.2.2:1 2.2.2.2:1
tcp 12.0.0.1:11000 192.168.1.2:11000 2.2.2.2:23 2.2.2.2:23
//这里表明pat成功
- 再测试GRE OVER IPSEC ***
pc1#ping 172.16.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 108/143/204 ms
R1#sh crypto engine connections active
ID Interface IP-Address State Algorithm Encrypt Decrypt
2 Tunnel1 10.0.0.1 set HMAC_MD5+3DES_56_C 0 0
2001 Tunnel1 12.0.0.1 set 3DES+SHA 24 0
2002 Tunnel1 12.0.0.1 set 3DES+SHA 0 24
//加上上面19个一共为24个包被加密