高性能七层反向代理(达到NGINX的八九成效率),支持热更新,并对接到包括容器编排框架在内的多种后端服务
整体架构
因为是七层反向代理,所以是通过开放http,https端口接收域名请求并转发,不支持直接通过ip和端口进行转发 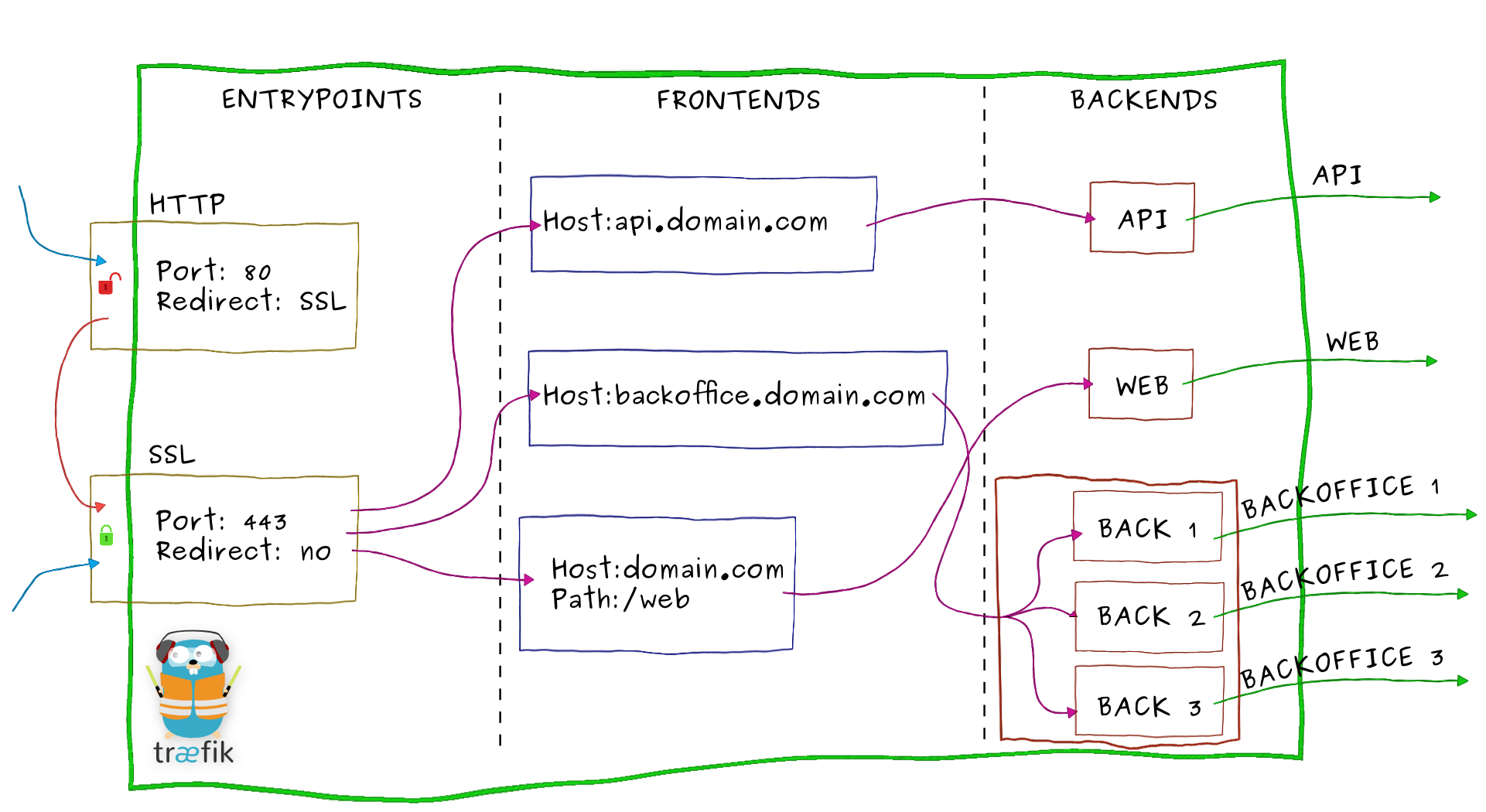
配置
配置加载优先级:KV Store(包括Consule、etcd、ZK) > Arguments命令参数 > ConfigFile配置文件 > Default
配置文件
#entrypoints配置
[entryPoints]
[entryPoints.http]
address = ":80"
[entryPoints.http.redirect]
entryPoint = "https"
[entryPoints.https]
address = ":443"
#frontends配置
[frontends]
[frontends.myfront]
backend = "mybackend"
passHostHeader = true
passTLSCert = true
priority = 10
entrypoints = ["https"]
[frontends.myfront.headers.customresponseheaders] #自定义头部
X-MY-Response-Header = "xxx"
[frontends.myfront.headers.customrequestheaders]
X-MY-Request-Herder = "xxx"
[frontends.myfront.routes.test_1]
rule = "Host:my.com"
#backends配置
[backends]
[backends.mybackend]
[backends.mybackend.circuitbreaker]
expression = "NetworkErrorRatio() > 0.5"
[backends.mybackend.LoadBalancer]
method = "drr" #或者使用静态值wrr
[backends.mybackend.loadbalancer.stickiness] #基于cookie的会话黏性配置
cookieName = "my_cookie" #自定义植入的黏性cookie名
[backends.mybackend.healthcheck]
path = "/health"
interval = "10s"
port = 8080
[backends.mybackend.maxconn]
amount = 1000 #并发上限
extractorfunc = "request.host" #其他候选值:client.ip、request.header.字段名
[backends.mybackend.servers.server1]
url = "http://172.17.0.2:80"
weight = 1
[backends.mybackend.servers.server2]
url = "http://172.17.0.3:80"
weight = 2
[acme]
email = "[email protected]"
storage = "acme.json"
onHostRule = true #自动为acme.entryPoint下的新域名申请证书
onDemand = true #在新域名接受第一次https请求时申请证书
caServer = "https://acme-staging.api.letsencrypt.org/directory" #默认是申请生产证书,这里改为申请staging证书进行测试
entryPoint = "https"
[acme.httpChallenge]
entryPoint = "http"
[[acme.domains]]
main = "local1.com"
sans = ["test1.local1.com", "test2.local1.com"]
[[acme.domains]]
main = "local2.com"
sans = ["test1.local2.com", "test2.local2.com"]
#ping健康检查配置(健康时:traefik healthcheck命令退出码为0,/ping接口返回200状态)
[ping]
entryPoint = "traefik" #指定是哪个entrypoint
标签
traefik支持自动解析service对象的标签
* traefik.enable=false
* traefik.domain=
* traefik.port=80
* traefik.frontend.entryPoints=http,https
* traefik.protocol=https
* traefik.weight=10
* traefik.frontend.rule=Host:test.traefik.io
* raefik.backend.loadbalancer.method=drr
* traefik.backend.loadbalancer.stickiness=true
* 具体参考https://docs.traefik.io/configuration/backends/rancher/#labels-overriding-default-behaviour
docker-compose部署
version: '2'
services:
reverse-proxy:
image: traefik
command: --api --docker #启用WebUI,监听docker
ports:
- "80:80" #http端口
- "8080:8080" #WebUI(--api选项)
volumes:
- /var/run/docker.sock:/var/run/docker.sock
- ~/traefik.toml:/etc/traefik/traefik.toml #自定义配置(可选)
K8S部署
RBAC授权
如果集群配置了RBAC,则需要对traefik授权访问
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: traefik-ingress-controller
rules:
- apiGroups:
- ""
resources:
- services
- endpoints
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- extensions
resources:
- ingresses
verbs:
- get
- list
- watch
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: traefik-ingress-controller
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: traefik-ingress-controller
subjects:
- kind: ServiceAccount
name: traefik-ingress-controller
namespace: kube-system
DaemonSet部署
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: traefik-ingress-controller
namespace: kube-system
---
kind: DaemonSet
apiVersion: extensions/v1beta1
metadata:
name: traefik-ingress-controller
namespace: kube-system
labels:
k8s-app: traefik-ingress-lb
spec:
template:
metadata:
labels:
k8s-app: traefik-ingress-lb
name: traefik-ingress-lb
spec:
serviceAccountName: traefik-ingress-controller
terminationGracePeriodSeconds: 60
hostNetwork: true
containers:
- image: traefik
name: traefik-ingress-lb
ports:
- name: http
containerPort: 80
hostPort: 80
- name: admin
containerPort: 8080
securityContext:
privileged: true
args:
- --api
- --kubernetes
- --logLevel=INFO
---
kind: Service
apiVersion: v1
metadata:
name: traefik-ingress-service
namespace: kube-system
spec:
selector:
k8s-app: traefik-ingress-lb
ports:
- protocol: TCP
port: 80
name: web
- protocol: TCP
port: 8080
name: admin
type: NodePort
创建TraefikUI入口
apiVersion: v1
kind: Service
metadata:
name: traefik-web-ui
namespace: kube-system
spec:
selector:
k8s-app: traefik-ingress-lb
ports:
- port: 80
targetPort: 8080
---
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: traefik-web-ui
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: traefik-ui.example.com
http:
paths:
- backend:
serviceName: traefik-web-ui
servicePort: 80
Http Basic
针对TraefikUI的访问认证保护
htpasswd -c ./auth 用户名 #根据提示输入密码
kubectl create secret generic mysecret --from-file auth --namespace=monitoring
#在traefik ui ingress对象上注册如下annotations
ingress.kubernetes.io/auth-type: "basic"
ingress.kubernetes.io/auth-secret: "mysecret"