比如无线网卡上的各种beacon帧很多,很烦,可以直接
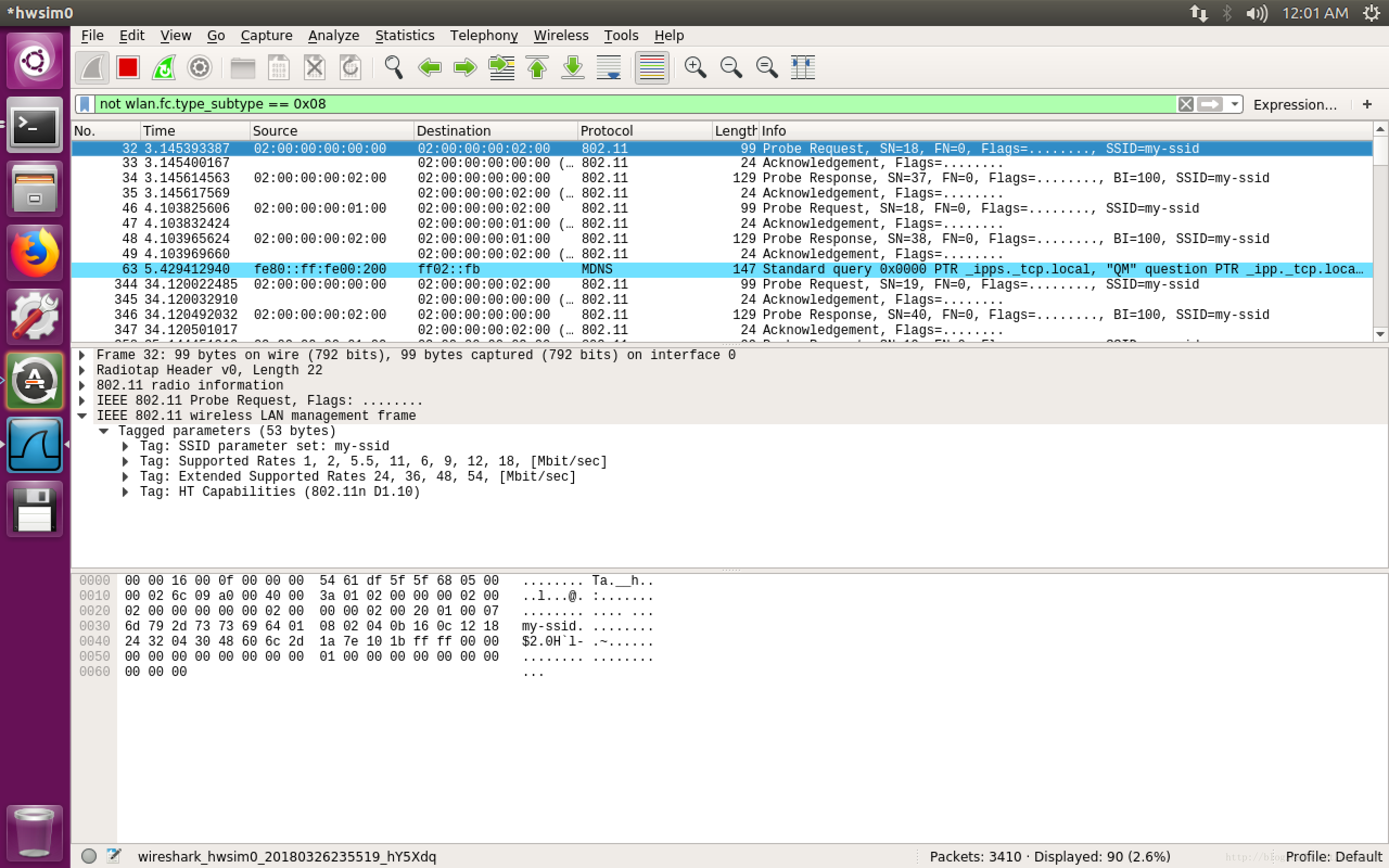
not wlan.fc.type_subtype == 0x08打开wireshark,满脸的802.11 beacon帧
去除掉beacon帧后。
参考:
https://my.oschina.net/665544/blog/1647001
Management frame
wlan.fc.type == 0
Control frame
wlan.fc.type == 1
Data frame
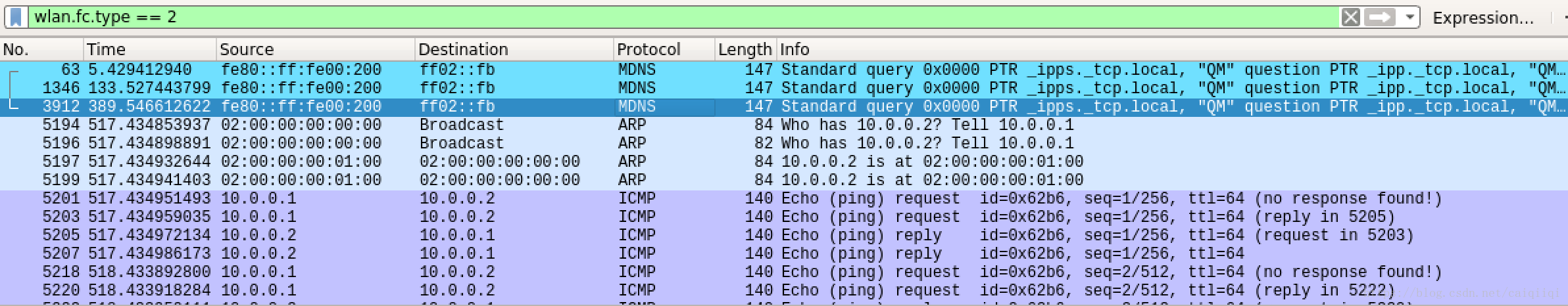
wlan.fc.type == 2
Association request
wlan.fc.type_subtype == 0x00
Association response
wlan.fc.type_subtype == 0x01
Reassociation request
wlan.fc.type_subtype == 0x02
Reassociation response
wlan.fc.type_subtype == 0x03
Probe request
wlan.fc.type_subtype == 0x04
Probe response
wlan.fc.type_subtype == 0x05
Beacon
wlan.fc.type_subtype == 0x08
Disassociate
wlan.fc.type_subtype == 0x0A
Authentication
wlan.fc.type_subtype == 0x0B
Deauthentication
wlan.fc.type_subtype == 0x0C
Action frame
wlan.fc.type_subtype == 0x0D
Block ACK requests
wlan.fc.type_subtype == 0x18
Block ACK
wlan.fc.type_subtype == 0x19
Power save poll
wlan.fc.type_subtype == 0x1A
Request to send
wlan.fc.type_subtype == 0x1B
Clear to send
wlan.fc.type_subtype == 0x1C
ACK
wlan.fc.type_subtype == 0x1D
Contention free period end
wlan.fc.type_subtype == 0x1E
NULL data
wlan.fc.type_subtype == 0x24
QoS data
wlan.fc.type_subtype == 0x28
Null QoS data
wlan.fc.type_subtype == 0x2C然后用sta1 ping sta2
mininet-wifi> sta1 ping sta2
PING 10.0.0.2 (10.0.0.2) 56(84) bytes of data.
64 bytes from 10.0.0.2: icmp_seq=1 ttl=64 time=0.180 ms
64 bytes from 10.0.0.2: icmp_seq=2 ttl=64 time=0.110 ms
^C
--- 10.0.0.2 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 999ms
rtt min/avg/max/mdev = 0.110/0.145/0.180/0.035 ms然后在wireshark中只查看数据帧。过滤语法:
wlan.fc.type == 2顺便修改一下wireshark的column,加上源/目端口,更容易知道数据包是哪个进程发起和接收的。