环境搭建
下载代码
https://github.com/lenve/javaboy-code-samples/tree/master/shiro/shiro-basic
将上面地址里的tree/master换成trunk,然后用svn co检出
svn co https://github.com/lenve/javaboy-code-samples/trunk/shiro/shiro-basic

导入idea
修改pom.xml文件
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-web</artifactId>
<version>1.4.2</version>
</dependency>
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-spring</artifactId>
<version>1.4.2</version>
</dependency>
修改shiroConfig.java
@Bean
ShiroFilterFactoryBean shiroFilterFactoryBean() {
ShiroFilterFactoryBean bean = new ShiroFilterFactoryBean();
...
...
//map.put("/*", "authc");
map.put("/hello/*", "authc");
bean.setFilterChainDefinitionMap(map);
return bean;
}
修改同目录下LoginController.java
@GetMapping("/hello/{currentPage}")
public String hello(@PathVariable Integer currentPage) {
return "hello";
}
启动web服务
检查
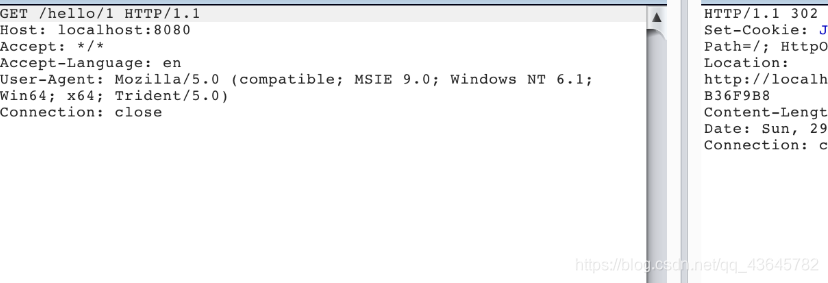
访问/hello/1接口,会跳转
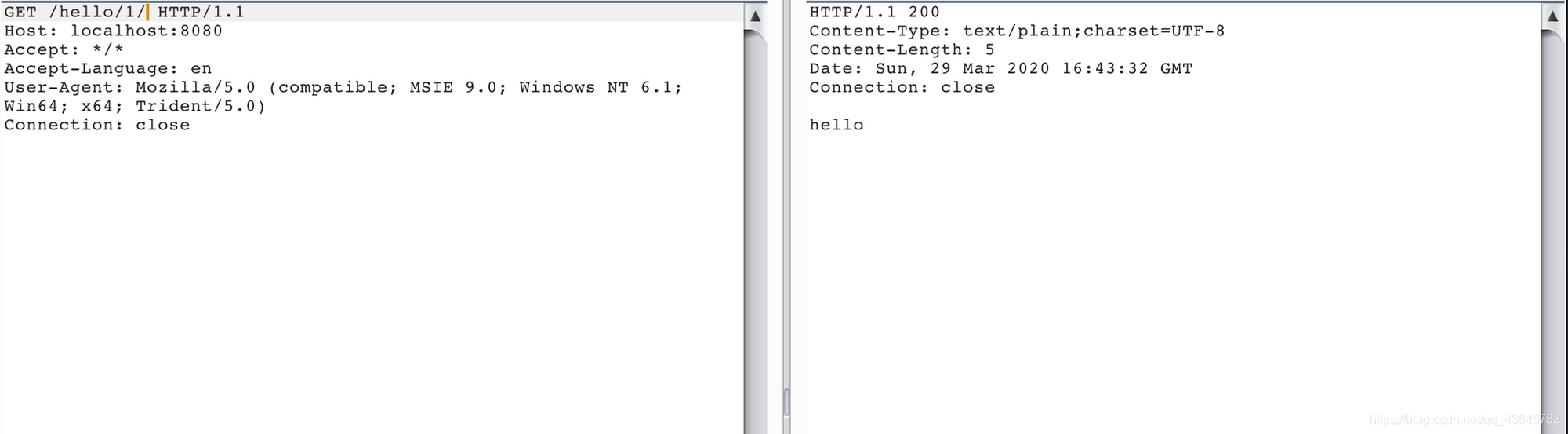
访问/hello/1/,获取到了资源
参考文章
https://segmentfault.com/a/1190000019440231
https://blog.riskivy.com/shiro-%e6%9d%83%e9%99%90%e7%bb%95%e8%bf%87%e6%bc%8f%e6%b4%9e%e5%88%86%e6%9e%90%ef%bc%88cve-2020-1957%ef%bc%89/