Kubernetes Dashboard(仪表盘)是Kubernetes项目中基于Web监控和操作界面的项目。
在早期的版本中 Kubernetes可以在 Dashboard 中看到 heapster 提供的一些图表信息,
在后续的版本中会陆续移除掉 heapster,现在更加流行的监控工具是 prometheus,prometheus 是 Google
内部监控报警系统的开源版本,所以这里的Dashboard 不会看到有图表信息。
实验环境
- nginx01:20.0.0.49(负载均衡服务器)
- nginx02:20.0.0.50 (负载均衡服务器)
- Master: 20.0.0.41
- Master2: 20.0.0.44
- Node01:20.0.0.42
- Node02:20.0.0.43
- 本篇文章接着上篇多节点部署与负载均衡部署继续部署,实验环境不变。
一:web页面部署
- 首先检查两个master节点检查pod资源是否正常
'//检查node节点是否运行正常'
[root@master ~]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
20.0.0.42 Ready <none> 8d v1.12.3
20.0.0.43 Ready <none> 8d v1.12.3
'//检查创建的pod资源是否运行正常'
[root@master ~]# kubectl get pods
NAME READY STATUS RESTARTS AGE
nginx-dbddb74b8-js4rs 1/1 Running 2 6d
- master节点创建dashboard工作目录
下载的网址(直接复制即可):https://github.com/kubernetes/kubernetes/tree/master/cluster/addons/dashboard
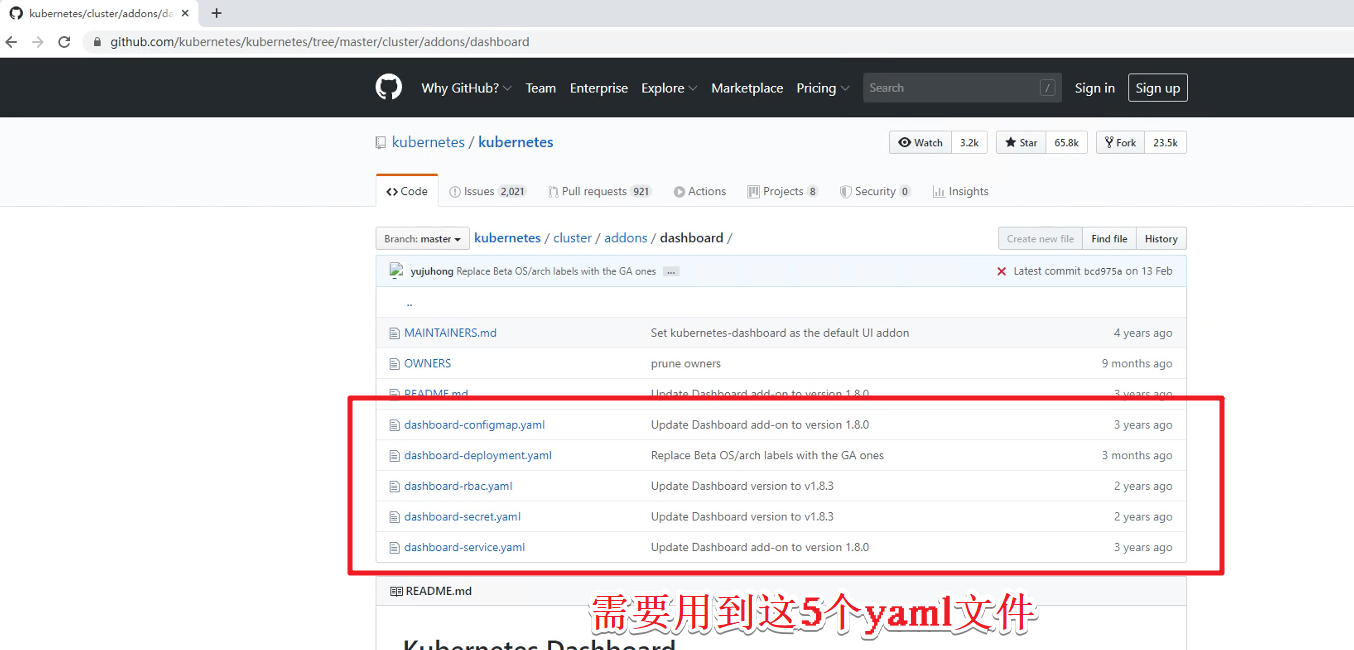
'//这边我们已经下载到本地,直接复制到目录使用'
[root@master ~]# cd /root/k8s/
[root@master k8s]# mkdir dashboard '//创建dashboard工作目录
[root@master k8s]# cd dashboard/
[root@master dashboard]# rz -E '//把几个yuml文件复制到目录'
rz waiting to receive.
[root@master dashboard]# ls
dashboard-configmap.yaml dashboard-rbac.yaml dashboard-service.yaml
dashboard-controller.yaml dashboard-secret.yaml k8s-admin.yaml
dashboard-configmap.yaml:配置应用
dashboard-rbac.yaml :授权访问api 角色控制
dashboard-service.yaml:发布应用 搭建的容器要发布被别人访问
dashboard-controller.yaml:控制权
dashboard-secret.yaml:安全加密
k8s-admin.yaml:生成令牌
1.1:创建相应的pod
- 创建访问控制的pod
'create:创建 -f:引用文件'
[root@master dashboard]# kubectl create -f dashboard-rbac.yaml
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
#查看dashboard-rbac.yaml
kind: Role '//资源类型'
apiVersion: rbac.authorization.k8s.io/v1 '//指定api版本'
metadata: '//指定资源数据'
labels: '//自定义标签'
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-minimal '//创建资源名称'
namespace: kube-system '//命名空间 公共命名空间'
rules:
.....省略信息................
#role是dashboard-rbac.yaml文件中指明的Kind,-n是指定namespace,同样在配置文件中可以查看
[root@master dashboard]# kubectl get role -n kube-system
NAME AGE
extension-apiserver-authentication-reader 9d
kubernetes-dashboard-minimal 2m32s '//创建成功'
system::leader-locking-kube-controller-manager 9d
system::leader-locking-kube-scheduler 9d
system:controller:bootstrap-signer 9d
system:controller:cloud-provider 9d
system:controller:token-cleaner 9d
- 创建安全的pod
[root@master dashboard]# kubectl create -f dashboard-secret.yaml
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-key-holder created
'//查看资源'
[root@master dashboard]# kubectl get Secret -n kube-system
NAME TYPE DATA AGE
default-token-nkl6z kubernetes.io/service-account-token 3 9d
kubernetes-dashboard-certs Opaque 0 33m
kubernetes-dashboard-key-holder Opaque 2 33m
kubernetes-dashboard-token-qj5b4 kubernetes.io/service-account-token 3 12m
- 创意配置的pod
[root@master dashboard]# kubectl create -f dashboard-configmap.yaml
configmap/kubernetes-dashboard-settings created
[root@master dashboard]# kubectl get configmap -n kube-system
NAME DATA AGE
extension-apiserver-authentication 1 9d
kubernetes-dashboard-settings 0 35s
- 创建控制器的pod
[root@master dashboard]# kubectl create -f dashboard-controller.yaml
serviceaccount/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
- 创建server服务pod
[root@master dashboard]# kubectl create -f dashboard-service.yaml
service/kubernetes-dashboard created
- 查看创建完成的pod资源
[root@master dashboard]# kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
kubernetes-dashboard-65f974f565-qw4jp 1/1 Running 0 2m1s
#查看资源
[root@master dashboard]# kubectl get Service -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes-dashboard NodePort 10.0.0.31 <none> 443:30001/TCP 18m
'这边做了一个端口映射'
'//pod资源只是提供程序应用,一旦service创建了,那么pod资源会被提供出去可以访问,端口伴随着service出现的,通过nodeport端口访问web界面'
- 查看pod资源在哪个节点
[root@master dashboard]# kubectl get pods -n kube-system -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE
kubernetes-dashboard-65f974f565-qw4jp 1/1 Running 0 23m 172.17.5.3 20.0.0.43 <none>
'//pods创建在20.0.0.43节点'
#节点查看
[root@node2 ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
0bc68fa89072 siriuszg/kubernetes-dashboard-amd64 "/dashboard --insecu…" 25 minutes ago Up 25 minutes k8s_kubernetes-dashboard_kubernetes-dashboard-65f974f565-qw4jp_kube-system_0ebd332f-0959-11eb-b238-000c29bdbf8a_0
04fecefad69a registry.cn-hangzhou.aliyuncs.com/google-containers/pause-amd64:3.0 "/pause" 25 minutes ago Up 25 minutes k8s_POD_kubernetes-dashboard-65f974f565-qw4jp_kube-system_0ebd332f-0959-11eb-b238-000c29bdbf8a_0
- 查看如何访问
#svc是Service简写
[root@master dashboard]# kubectl get pods,svc -n kube-system
NAME READY STATUS RESTARTS AGE
pod/kubernetes-dashboard-65f974f565-qw4jp 1/1 Running 0 20m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes-dashboard NodePort 10.0.0.31 <none> 443:30001/TCP 20m
1.2:客户端访问web界面进行验证
用火狐就可直接访问
访问网址:https://20.0.0.43:30001 ,之后会自动跳转页面
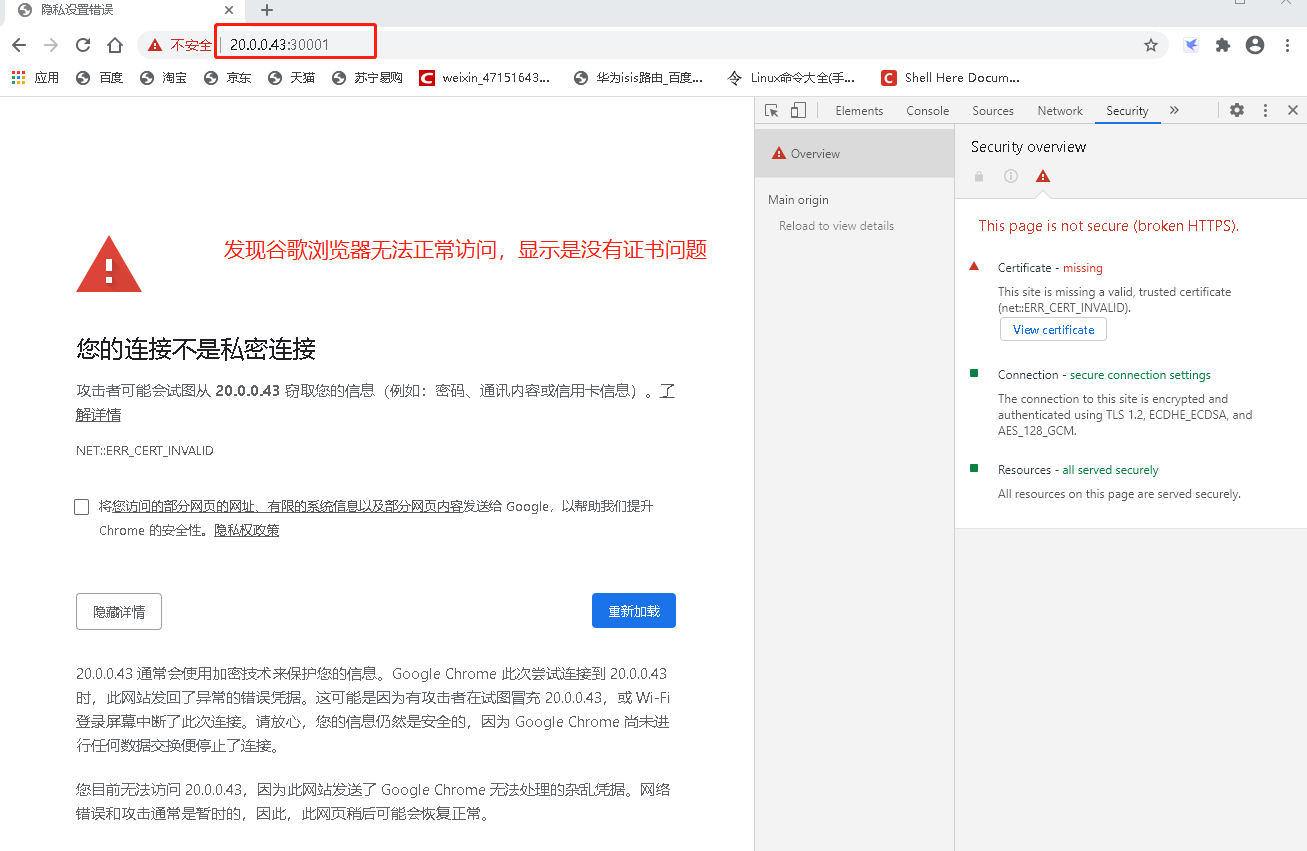
- 访问页面时就会报错,出现无法访问的问题,下面我们就来解决这个访问问题
1.3:解决谷歌无法验证证书问题
- 创建证书
'创建证书文件'
[root@master dashboard]# vim dashboard-cert.sh
cat > dashboard-csr.json <<EOF
{
"CN": "Dashboard",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "BeiJing",
"ST": "BeiJing"
}
]
}
EOF
K8S_CA=$1
cfssl gencert -ca=$K8S_CA/ca.pem -ca-key=$K8S_CA/ca-key.pem -config=$K8S_CA/ca-config.json -profile=kubernetes dashboard-csr.json | cfssljson -bare dashboard
kubectl delete secret kubernetes-dashboard-certs -n kube-system
kubectl create secret generic kubernetes-dashboard-certs --from-file=./ -n kube-system
- 生成证书到指定目录
[root@master dashboard]# vim dashboard-cert.sh
[root@master dashboard]# bash dashboard-cert.sh /root/k8s/k8s-cert/
2020/10/08 20:09:09 [INFO] generate received request
2020/10/08 20:09:09 [INFO] received CSR
2020/10/08 20:09:09 [INFO] generating key: rsa-2048
2020/10/08 20:09:09 [INFO] encoded CSR
2020/10/08 20:09:09 [INFO] signed certificate with serial number 390578559397620142063511696436940771020239162569
2020/10/08 20:09:09 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
secret "kubernetes-dashboard-certs" deleted
secret/kubernetes-dashboard-certs created
- 修改控制的配置文件
[root@master dashboard]# vim dashboard-controller.yaml
# PLATFORM-SPECIFIC ARGS HERE
- --auto-generate-certificates '//下面添加两行'
- --tls-key-file=dashboard-key.pem
- --tls-cert-file=dashboard.pem
- 重新部署更新
[root@master dashboard]# kubectl apply -f dashboard-controller.yaml
Warning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl apply
serviceaccount/kubernetes-dashboard configured
Warning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl apply
deployment.apps/kubernetes-dashboard configured
'//查看访问'
[root@master dashboard]# kubectl get pods,svc -n kube-system
NAME READY STATUS RESTARTS AGE
pod/kubernetes-dashboard-7dffbccd68-lcwbd 1/1 Running 0 104m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes-dashboard NodePort 10.0.0.31 <none> 443:30001/TCP 154m
'查看pod资源在哪个节点 已经换成20.0.0.42节点了'
[root@master dashboard]# kubectl get pods -n kube-system -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE
kubernetes-dashboard-7dffbccd68-lcwbd 1/1 Running 0 105m 172.17.93.2 20.0.0.42 <none>
- 再次进行访问erb界面
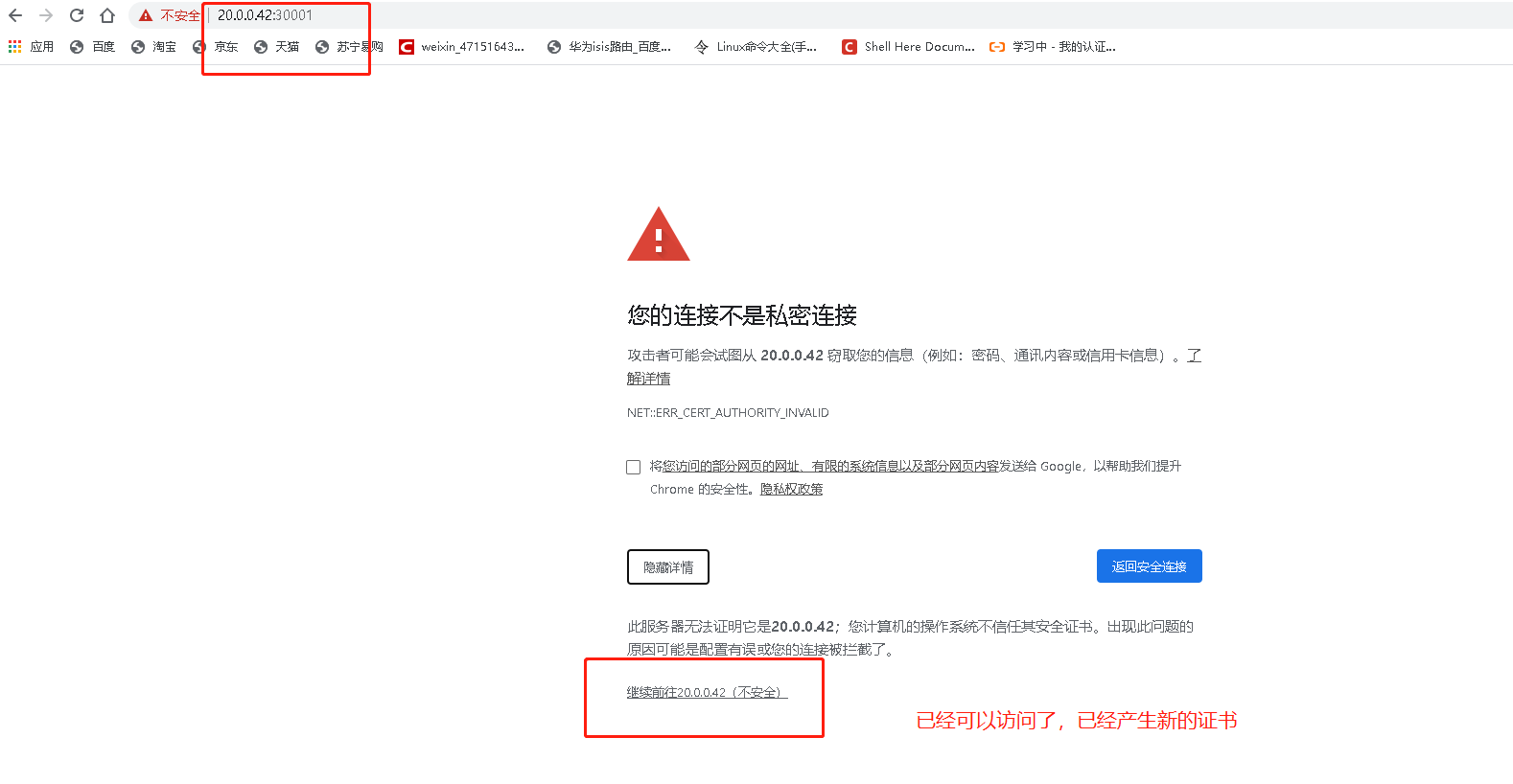
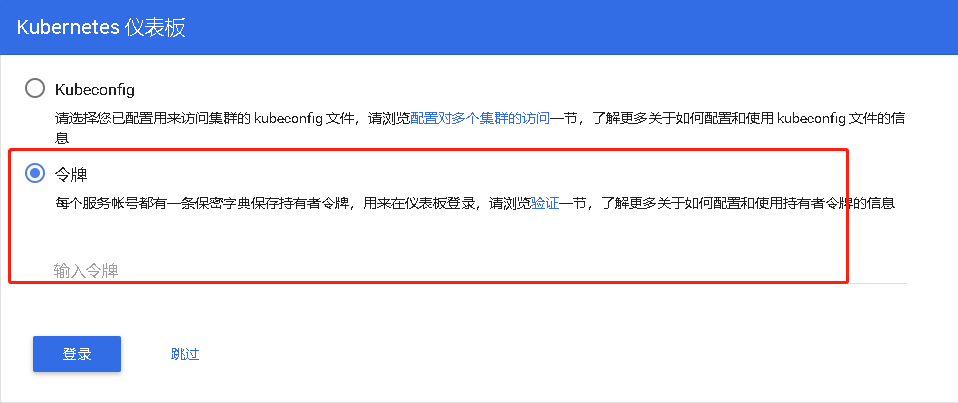
1.4:使用令牌进行访问
- 生成令牌
[root@master dashboard]# kubectl create -f k8s-admin.yaml
serviceaccount/dashboard-admin created
clusterrolebinding.rbac.authorization.k8s.io/dashboard-admin created
[root@master dashboard]# kubectl get secret -n kube-system
NAME TYPE DATA AGE
dashboard-admin-token-8mhdr kubernetes.io/service-account-token 3 41s '//令牌已经生成'
default-token-nkl6z kubernetes.io/service-account-token 3 9d
kubernetes-dashboard-certs Opaque 11 136m
kubernetes-dashboard-key-holder Opaque 2 3h20m
kubernetes-dashboard-token-qj5b4 kubernetes.io/service-account-token 3 179m
- 查看令牌
[root@master dashboard]# kubectl describe secret dashboard-admin-token-8mhdr -n kube-system
Name: dashboard-admin-token-8mhdr
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: 1845d357-0972-11eb-a2d8-000c2984c1e3
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1359 bytes
namespace: 11 bytes
token: #复制下方令牌,填写到浏览器中即可
eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tOG1oZHIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMTg0NWQzNTctMDk3Mi0xMWViLWEyZDgtMDAwYzI5ODRjMWUzIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.URRYRf_7QgkJeKNqAhJpS8rAWsvtc8ahqz52408pPfLULl5h2WwpoKaG-l24FC6tzwrUSvSKUevSPA3O4xnKgJ0H2WJef3KiHVG_8CRrJ-e3HiQKfk_Meb7NcCor6mZgBLP1KeO4q79whD7IWRBcdE3Z06pB0xOiyKhENUYA1dECYS5hYIo8IfwVQ4lNypDDRre7WUIsqQpbzDqkb8nb7ni-6PRqzEPxEimY8V9zrHYX8GsXUqblpMg-4adNN79pMQHDn-mYlmYXNe7UNEYBlQzVKmpJ2dEZ2lGTcwUiHFueuXvb6GwqLXIPd_08OtRB6X9HNMVn6Nf3PPz2A6vPyA
复制令牌

- 至此,即可在web界面进行监控群集节点的信息,及创建资源对象(一般不会在这上面进行创建资源对象)
