本实验将继续采用从我之前的FabricCA单机多节点(Fabric 学习七)Fabric2.4.x 区块链多机部署(重新整一遍)_FD—moremore的博客-CSDN博客为目标构建,在学习七中我使用三个orderer节点,两个组织以及组织下各有两个peer节点组成网络。
所以在容器配置中我们会设定一个tlsCA和一个orderer的CA(我这里设置为组织0),以及两个普通组织(内有peer节点)的CA,共四个CA。
一、编写CA容器启动配置docker-compose-ca.yaml
注意:CA服务器数据库默认支持三种:sqlite、mysql和postgresql,这里我们设置成我主机上的mysql,当然,在启动前一定要先在自己的mysql中创建好数据库才行。
1.1 本地创建数据库
1.2 编写容器启动文件:
version: '2.0'
networks:
fabric-ca:
name: fabric-ca
services:
ca-tls:
container_name: ca-tls
image: hyperledger/fabric-ca
command: sh -c 'fabric-ca-server start -d -b tls-ca-admin:tls-ca-adminpw --port 7053'
environment:
- FABRIC_CA_SERVER_HOME=/tmp/hyperledger/fabric-ca/crypto
- FABRIC_CA_SERVER_TLS_ENABLED=true
- FABRIC_CA_SERVER_CSR_CN=ca-tls
- FABRIC_CA_SERVER_CSR_HOSTS=0.0.0.0
- FABRIC_CA_SERVER_DEBUG=true
- FABRIC_CA_SERVER_DB_TYPE=mysql
- FABRIC_CA_SERVER_DB_DATASOURCE=root:123456@tcp(10.65.119.182:3306)/fabric_ca_tls?parseTime=true
volumes:
- /tmp/hyperledger/tls-ca:/tmp/hyperledger/fabric-ca
networks:
- fabric-ca
ports:
- 7053:7053
rca-org0:
container_name: rca-org0
image: hyperledger/fabric-ca
command: sh -c 'fabric-ca-server start -d -b rca-org0-admin:rca-org0-adminpw --port 7054'
environment:
- FABRIC_CA_SERVER_HOME=/tmp/hyperledger/fabric-ca/crypto
- FABRIC_CA_SERVER_TLS_ENABLED=true
- FABRIC_CA_SERVER_CSR_CN=rca-org0
- FABRIC_CA_SERVER_CSR_HOSTS=0.0.0.0
- FABRIC_CA_SERVER_DEBUG=true
- FABRIC_CA_SERVER_DB_TYPE=mysql
- FABRIC_CA_SERVER_DB_DATASOURCE=root:123456@tcp(10.65.119.182:3306)/fabric_rca_org0?parseTime=true
volumes:
- /tmp/hyperledger/org0/ca:/tmp/hyperledger/fabric-ca
networks:
- fabric-ca
ports:
- 7054:7054
rca-org1:
container_name: rca-org1
image: hyperledger/fabric-ca
command: sh -c 'fabric-ca-server start -d -b rca-org1-admin:rca-org1-adminpw'
environment:
- FABRIC_CA_SERVER_HOME=/tmp/hyperledger/fabric-ca/crypto
- FABRIC_CA_SERVER_TLS_ENABLED=true
- FABRIC_CA_SERVER_CSR_CN=rca-org1
- FABRIC_CA_SERVER_CSR_HOSTS=0.0.0.0
- FABRIC_CA_SERVER_DEBUG=true
- FABRIC_CA_SERVER_DB_TYPE=mysql
- FABRIC_CA_SERVER_DB_DATASOURCE=root:123456@tcp(10.65.119.182:3306)/fabric_rca_org1?parseTime=true
volumes:
- /tmp/hyperledger/org1/ca:/tmp/hyperledger/fabric-ca
networks:
- fabric-ca
ports:
- 7055:7055
rca-org2:
container_name: rca-org2
image: hyperledger/fabric-ca
command: sh -c 'fabric-ca-server start -d -b rca-org2-admin:rca-org2-adminpw --port 7056'
environment:
- FABRIC_CA_SERVER_HOME=/tmp/hyperledger/fabric-ca/crypto
- FABRIC_CA_SERVER_TLS_ENABLED=true
- FABRIC_CA_SERVER_CSR_CN=rca-org2
- FABRIC_CA_SERVER_CSR_HOSTS=0.0.0.0
- FABRIC_CA_SERVER_DEBUG=true
- FABRIC_CA_SERVER_DB_TYPE=mysql
- FABRIC_CA_SERVER_DB_DATASOURCE=root:123456@tcp(10.65.119.182:3306)/fabric_rca_org2?parseTime=true
volumes:
- /tmp/hyperledger/org2/ca:/tmp/hyperledger/fabric-ca
networks:
- fabric-ca
ports:
- 7056:70561.3 打开容器
docker-compose -f docker-compose-ca.yaml up -d或者关闭容器可以使用:
docker-compose -f docker-compose-ca.yaml down
1.4 会出现的问题
经过上述步骤可能会发现容器启动是成功了,但是转眼这些容器都挂掉了。


为什么会出现这种情况呢?
为解决这个问题,我打开了Docker Portainer,去看看这些容器失败的日志:
第一个问题:连接MySQL出现Host is not allowed to connect to this MySQL server。
解决办法:这是由于本地的账号可以连接数据库,但是不允许远程来连接数据库,于是我们需要对mysql的权限进行修改。
1)mysql -u root -p 连接数据库

2)use mysql;
3)update user set host = '%' where user = 'root';
4) FLUSH PRIVILEGES;

重新再打开容器,会发现:

确实已经连接上数据库,但是又爆了第二个错误。
问题二:Error occurred initializing database: Failed to create MySQL tables: Error creating certificates table: Error 1067: Invalid default value for 'expiry'。
解决方法:解决了把mysql的严格模式关掉就好了!--sql-mode=""
1)找到自己mysql的my.ini配置文件
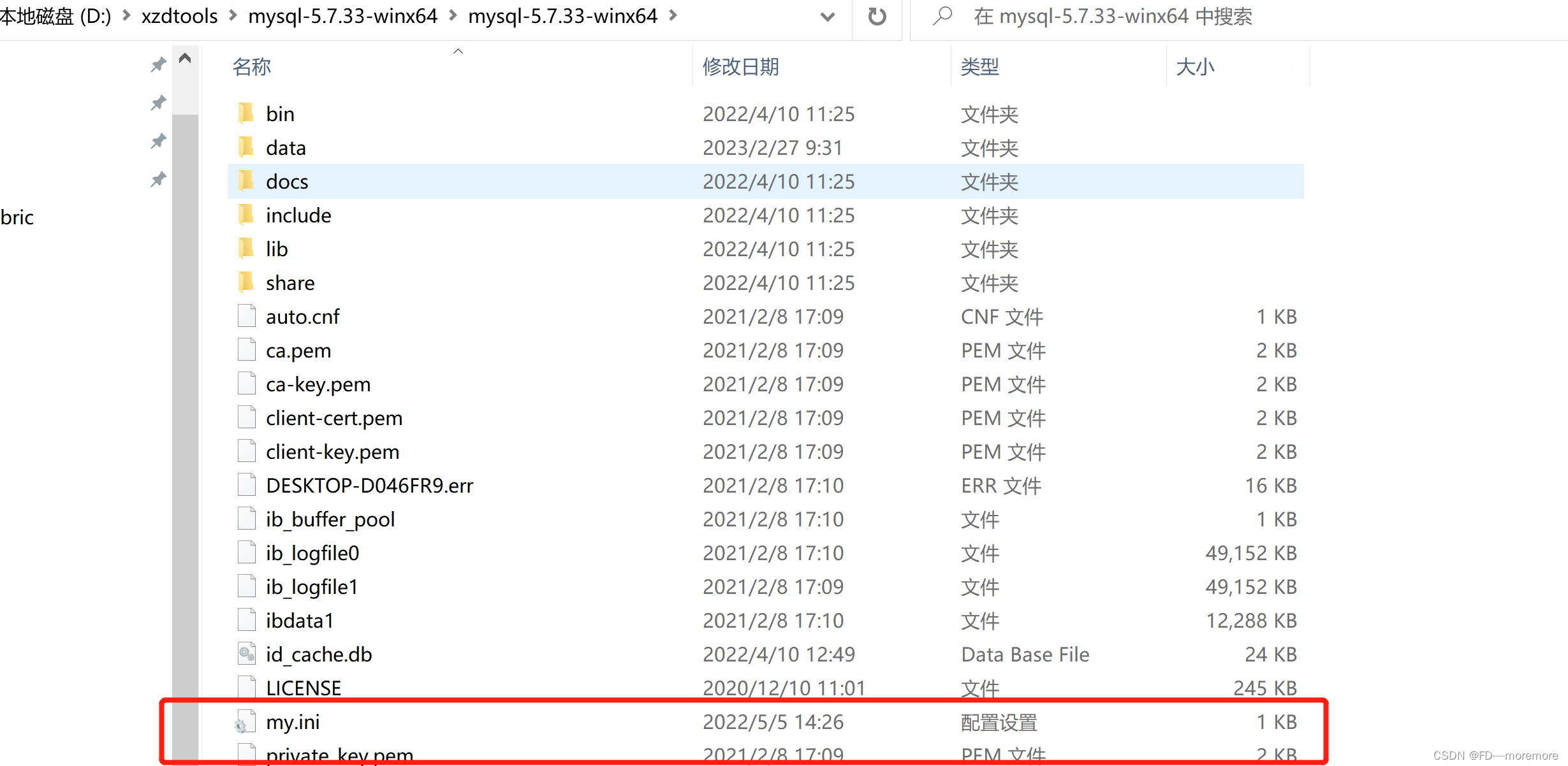
2)进入配置my.ini:
在这里设置成:
sql_mode=NO_ZERO_IN_DATE,NO_ZERO_DATE,ERROR_FOR_DIVISION_BY_ZERO,NO_ENGINE_SUBSTITUTION
把STRICT_TRANS_TABLES去掉。
3)然后重启一下mysql服务:

之后重新打开容器:

1.5 完成后查看
1、首先我们查看一下docker日志:

可以发现现在四个CA都完美的开起来了,同时点击日志:
 没有报错!那就完美!
没有报错!那就完美!
2、然后我们可以查看一下数据库:

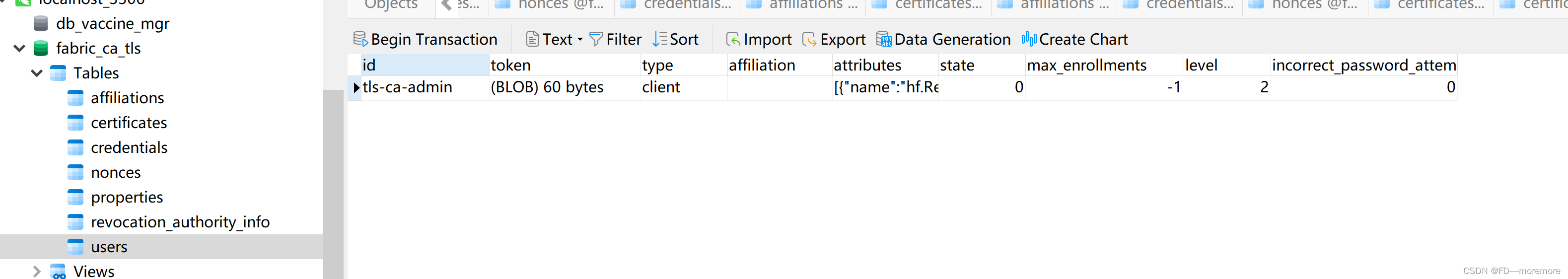
上面可以看到指定的初始化管理员信息也存进去了。
3、查看一下工作目录结构
tree /tmp/hyperledger/tmp/hyperledger
├── org0
├── org1
├── org2
└── tls-ca可以进行接下来的操作了。
二、在CA上注册成员并颁发证书
2.1 准备工作
1、我们需要将fabric-ca-client这个bin中的二进制文件放到该目录下。
sudo cp /xxxxxxxx/bin/fabric-ca-client /tmp/hyperledger/2.然后我们到/tmp/hyperledger目录下:
cd /tmp/hyperledgertree ./可以发现目录结构为:
/tmp/hyperledger
├── fabric-ca-client
├── org0
├── org1
├── org2
└── tls-ca2.2 注册 TLS CA 管理员,注册节点身份
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/tls-ca/crypto/tls-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/tls-ca/admin
cp /tmp/hyperledger/tls-ca/crypto/ca-cert.pem /tmp/hyperledger/tls-ca/crypto/tls-ca-cert.pem
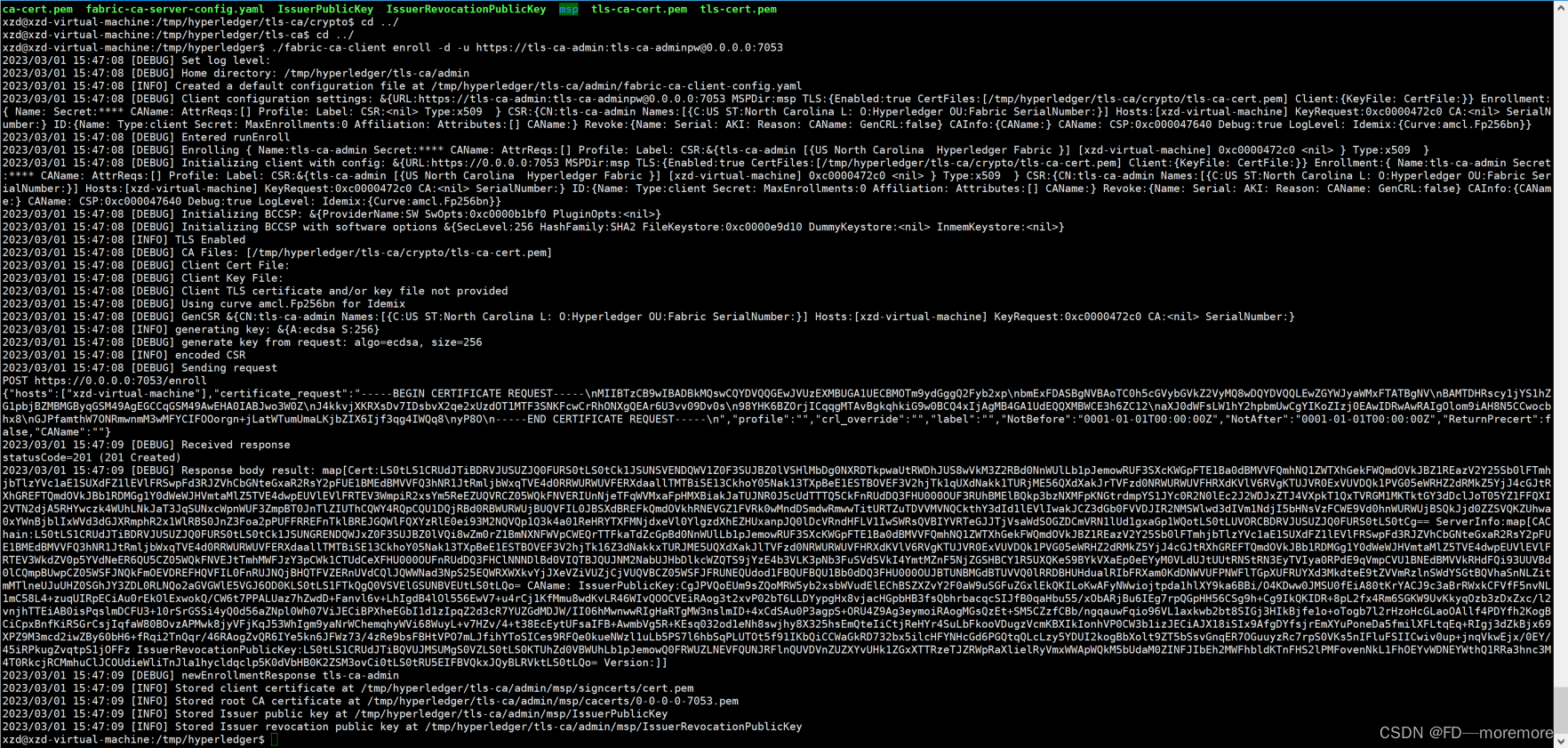
./fabric-ca-client enroll -d -u https://tls-ca-admin:[email protected]:7053
结果如下:可以看到tls-ca管理员对应的证书

2.3 将节点注册到tlsCA上
1、将org1的两个peer节点注册到tlsCA上:(必须先注册才可以进行enroll)
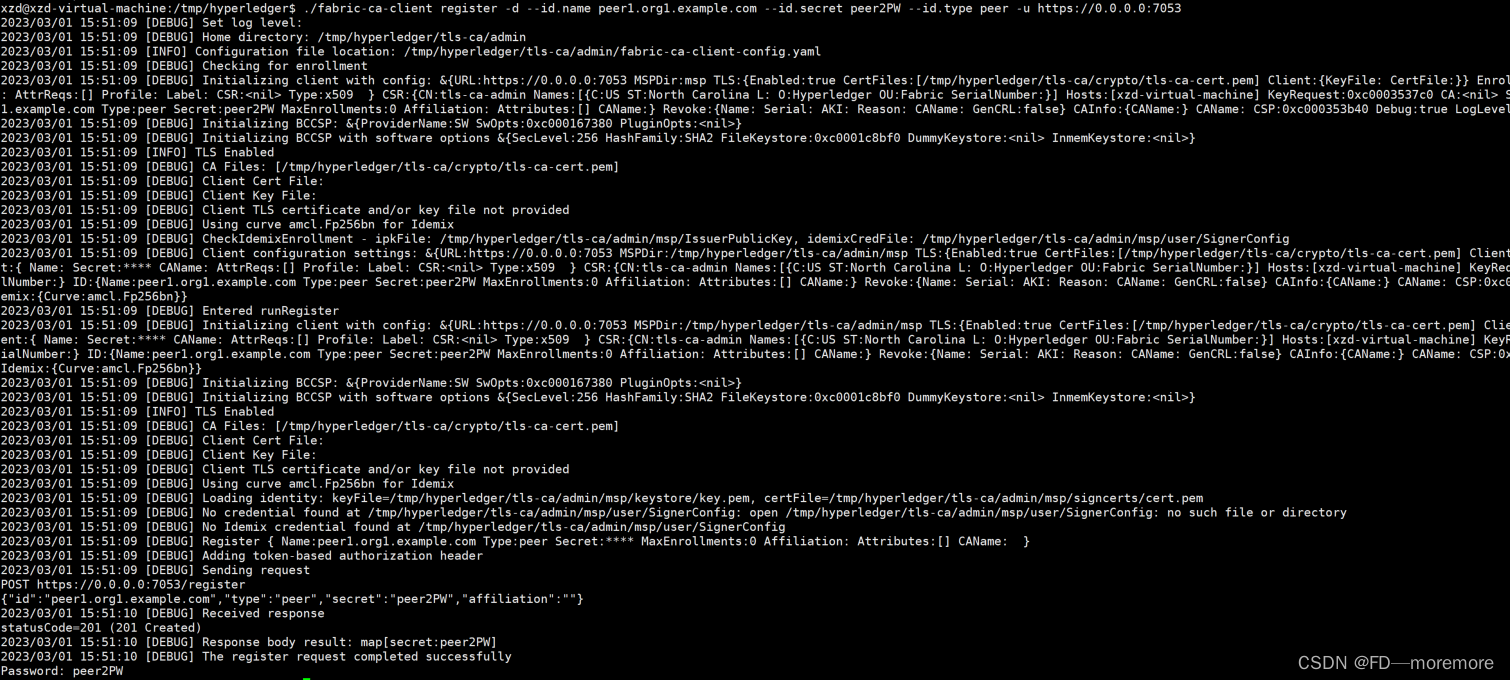
./fabric-ca-client register -d --id.name peer0.org1.example.com --id.secret peer1PW --id.type peer -u https://0.0.0.0:7053
./fabric-ca-client register -d --id.name peer1.org1.example.com --id.secret peer2PW --id.type peer -u https://0.0.0.0:7053
结果如下:
然后我们你可以打开fabric-ca-tls的数据库上查看:
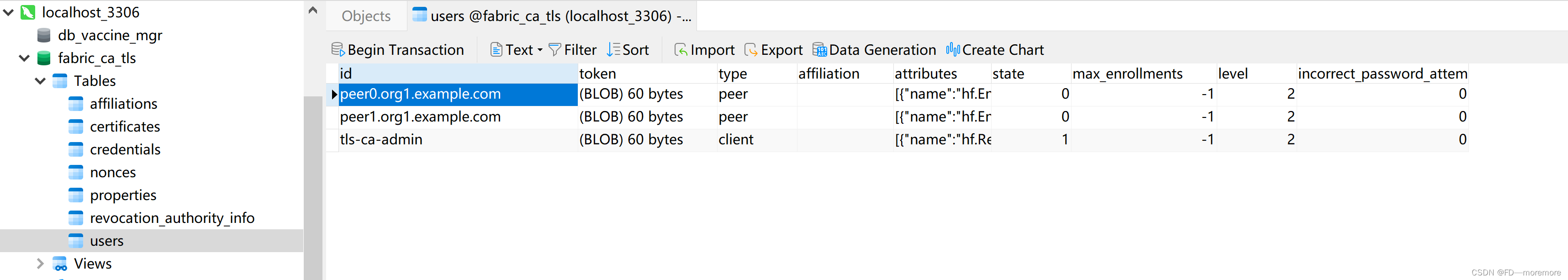
发现peer0.org1.example.com和peer1.org1.example.com已经注册成功了,他们的类型是peer。
2、注册机构2的两个peer节点:
./fabric-ca-client register -d --id.name peer0.org2.example.com --id.secret peer1PW --id.type peer -u https://0.0.0.0:7053
./fabric-ca-client register -d --id.name peer1.org2.example.com --id.secret peer2PW --id.type peer -u https://0.0.0.0:7053
3、注册机构0的三个orderer节点
./fabric-ca-client register -d --id.name orderer0.example.com --id.secret ordererPW --id.type orderer -u https://0.0.0.0:7053
./fabric-ca-client register -d --id.name orderer1.example.com --id.secret ordererPW --id.type orderer -u https://0.0.0.0:7053
./fabric-ca-client register -d --id.name orderer2.example.com --id.secret ordererPW --id.type orderer -u https://0.0.0.0:7053
结果如下:

2.4 注册orderer节点和org0的管理员
1、register orderer1 节点 & org0 管理员
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org0/ca/crypto/ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org0/ca/admin
./fabric-ca-client enroll -d -u https://rca-org0-admin:[email protected]:7054
./fabric-ca-client register -d --id.name orderer0.example.com --id.secret ordererpw --id.type orderer -u https://0.0.0.0:7054
./fabric-ca-client register -d --id.name admin-org0 --id.secret org0adminpw --id.type admin --id.attrs "hf.Registrar.Roles=*,hf.Registrar.DelegateRoles=*,hf.AffiliationMgr=true,hf.Registrar.Attributes=*,hf.Revoker=true,hf.GenCRL=true,admin=true:ecert" -u https://0.0.0.0:7054
结果如下:
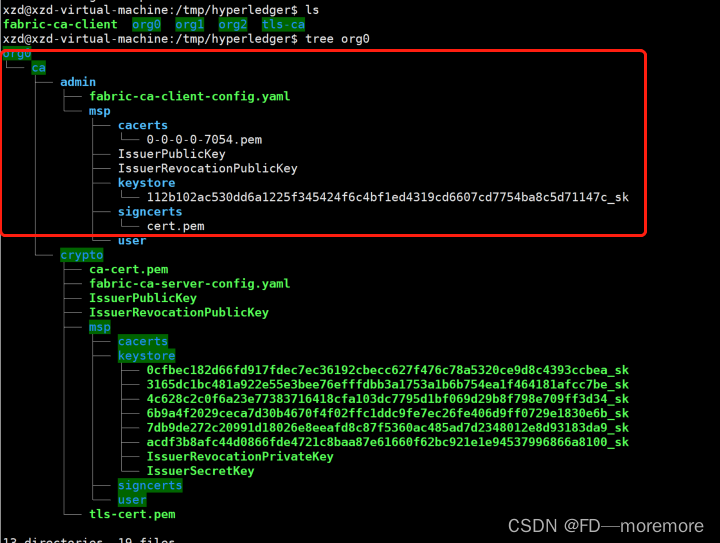
2、register orderer2 节点
./fabric-ca-client register -d --id.name orderer1.example.com --id.secret ordererpw --id.type orderer -u https://0.0.0.0:7054
3、register orderer3 节点
./fabric-ca-client register -d --id.name orderer2.example.com --id.secret ordererpw --id.type orderer -u https://0.0.0.0:7054
结果如下:

2.5 注册org1的peer节点和登记org1的管理员
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org1/ca/crypto/ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org1/ca/admin
./fabric-ca-client enroll -d -u https://rca-org1-admin:[email protected]:7055
./fabric-ca-client register -d --id.name peer0.org1.example.com --id.secret peer1PW --id.type peer -u https://0.0.0.0:7055
./fabric-ca-client register -d --id.name peer1.org1.example.com --id.secret peer2PW --id.type peer -u https://0.0.0.0:7055
./fabric-ca-client register -d --id.name admin-org1 --id.secret org1AdminPW --id.type admin --id.attrs "hf.Registrar.Roles=*,hf.Registrar.DelegateRoles=*,hf.AffiliationMgr=true,hf.Registrar.Attributes=*,hf.Revoker=true,hf.GenCRL=true,admin=true:ecert" -u https://0.0.0.0:7055
./fabric-ca-client register -d --id.name user-org1 --id.secret org1UserPW --id.type user -u https://0.0.0.0:7055结果如下:

2.6 注册org2的peer节点和登记org2的管理员
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org2/ca/crypto/ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org2/ca/admin
./fabric-ca-client enroll -d -u https://rca-org2-admin:[email protected]:7056
./fabric-ca-client register -d --id.name peer0.org2.example.com --id.secret peer1PW --id.type peer -u https://0.0.0.0:7056
./fabric-ca-client register -d --id.name peer1.org2.example.com --id.secret peer2PW --id.type peer -u https://0.0.0.0:7056
./fabric-ca-client register -d --id.name admin-org2 --id.secret org2AdminPW --id.type admin --id.attrs "hf.Registrar.Roles=*,hf.Registrar.DelegateRoles=*,hf.AffiliationMgr=true,hf.Registrar.Attributes=*,hf.Revoker=true,hf.GenCRL=true,admin=true:ecert" -u https://0.0.0.0:7056
./fabric-ca-client register -d --id.name user-org2 --id.secret org2UserPW --id.type user -u https://0.0.0.0:7056
结果如下:

2.7 登记org1中peer节点的证书
1、enroll org1的peer0的ECert证书
里面的peer1是第一个peer2的意思,即peer0.org1.example.com
mkdir -p org1/peer1/assets/ca/ && cp org1/ca/crypto/ca-cert.pem org1/peer1/assets/ca/org1-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org1/peer1
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org1/peer1/assets/ca/org1-ca-cert.pem
export FABRIC_CA_CLIENT_MSPDIR=msp
./fabric-ca-client enroll -d -u https://peer0.org1.example.com:[email protected]:7055
更改一下私钥的名字:(为了以后方便,省的改后端代码)
# 更改私钥文件名称
mv org1/peer1/msp/keystore/c7d42da1c3c9c988afc1a10e3ce954c76d0e76a3bda51fced0b21ba2c07cda6a_sk org1/peer1/msp/keystore/priv_sk
mkdir -p org1/peer1/msp/admincerts/2、enroll org1的peer0的TLS证书
注意:这里的端口号应该使用tls容器设置的端口号,过程中要传递tls证书
mkdir -p org1/peer1/assets/tls-ca/ && cp tls-ca/crypto/tls-ca-cert.pem org1/peer1/assets/tls-ca/tls-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org1/peer1
export FABRIC_CA_CLIENT_MSPDIR=tls-msp
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org1/peer1/assets/tls-ca/tls-ca-cert.pem
./fabric-ca-client enroll -d -u https://peer0.org1.example.com:[email protected]:7053 --enrollment.profile tls --csr.hosts peer0.org1.example.com
# 将 keystore 路径下的文件改名为 key.pem
mv org1/peer1/tls-msp/keystore/37babaf3fa116fdb0e0840b0084a7e5a1a762c0e62ac0662c68c9ac90935ba22_sk org1/peer1/tls-msp/keystore/key.pem
3、Enroll Org1 Peer2 ECert 证书
mkdir -p org1/peer2/assets/ca/ && cp org1/ca/crypto/ca-cert.pem org1/peer2/assets/ca/org1-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org1/peer2
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org1/peer2/assets/ca/org1-ca-cert.pem
export FABRIC_CA_CLIENT_MSPDIR=msp
./fabric-ca-client enroll -d -u https://peer1.org1.example.com:[email protected]:7055
# 修改私钥文件名称
mv org1/peer2/msp/keystore/719d48ca8b4ca174bebbc57ca470575cf6ccfd67d3879ad599890c5a75f84e16_sk org1/peer2/msp/keystore/priv_sk
mkdir -p org1/peer2/msp/admincerts/
4、Enroll Org1 Peer1 TLS 证书
mkdir -p org1/peer2/assets/tls-ca/ && cp tls-ca/crypto/tls-ca-cert.pem org1/peer2/assets/tls-ca/tls-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org1/peer2
export FABRIC_CA_CLIENT_MSPDIR=tls-msp
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org1/peer2/assets/tls-ca/tls-ca-cert.pem
./fabric-ca-client enroll -d -u https://peer1.org1.example.com:[email protected]:7053 --enrollment.profile tls --csr.hosts peer1.org1.example.com
# 将 keystore 路径下的文件改名为 key.pem
mv org1/peer2/tls-msp/keystore/b8ddcf900e66be9e1c5e4fd8989da9c684f772f2a144cef6af7e2eaf84bcad78_sk org1/peer2/tls-msp/keystore/key.pem
5、Enroll Org1’s Admin
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org1/admin
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org1/peer1/assets/ca/org1-ca-cert.pem
export FABRIC_CA_CLIENT_MSPDIR=msp
./fabric-ca-client enroll -d -u https://admin-org1:[email protected]:7055
mv /tmp/hyperledger/org1/admin/msp/keystore/05680a630bee4237da33db6b7446647890772773b7d51ab12ada1039f46dec96_sk /tmp/hyperledger/org1/admin/msp/keystore/priv_sk
cp /tmp/hyperledger/org1/admin/msp/signcerts/cert.pem /tmp/hyperledger/org1/peer1/msp/admincerts/org1-admin-cert.pem
cp /tmp/hyperledger/org1/admin/msp/signcerts/cert.pem /tmp/hyperledger/org1/peer2/msp/admincerts/org1-admin-cert.pem2.8 登记org2中peer节点的证书
1、Enroll Org2 Peer1 ECert 证书
mkdir -p org2/peer1/assets/ca/ && cp org2/ca/crypto/ca-cert.pem org2/peer1/assets/ca/org2-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org2/peer1
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org2/peer1/assets/ca/org2-ca-cert.pem
export FABRIC_CA_CLIENT_MSPDIR=msp
./fabric-ca-client enroll -d -u https://peer0.org2.example.com:[email protected]:7056
# 修改私钥文件名称
mv org2/peer1/msp/keystore/99810fa9833aa697f35e0bdedbabdb66fb00e7ae9a9c065d4e5f6f95e3173b3f_sk org2/peer1/msp/keystore/priv_sk
2、Enroll Org2 Peer1 TLS 证书
mkdir org2/peer1/assets/tls-ca/ && cp tls-ca/crypto/tls-ca-cert.pem org2/peer1/assets/tls-ca/tls-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org2/peer1
export FABRIC_CA_CLIENT_MSPDIR=tls-msp
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org2/peer1/assets/tls-ca/tls-ca-cert.pem
./fabric-ca-client enroll -d -u https://peer0.org2.example.com:[email protected]:7053 --enrollment.profile tls --csr.hosts peer0.org2.example.com
# 修改私钥文件名称
mv org2/peer1/tls-msp/keystore/5dc8a6a72dd4fecb940f2ddd11d8316639438f751a0bf88a22edcdbc7c3b8b24_sk org2/peer1/tls-msp/keystore/key.pem3、Enroll Org2 Peer2 ECert 证书
mkdir -p org2/peer2/assets/ca/ && cp org2/ca/crypto/ca-cert.pem org2/peer2/assets/ca/org2-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org2/peer2
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org2/peer2/assets/ca/org2-ca-cert.pem
export FABRIC_CA_CLIENT_MSPDIR=msp
./fabric-ca-client enroll -d -u https://peer1.org2.example.com:[email protected]:7056
# 修改私钥文件名称
mv org2/peer2/msp/keystore/1ecea1bcb5e65fa5f7e1e55b3ecdfa65c02833de0a83f3bbfbedb0ea2bf94fb2_sk org2/peer2/msp/keystore/priv_sk4、Enroll Org2 Peer2 TLS 证书
mkdir -p org2/peer2/assets/tls-ca/ && cp tls-ca/crypto/tls-ca-cert.pem org2/peer2/assets/tls-ca/tls-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org2/peer2
export FABRIC_CA_CLIENT_MSPDIR=tls-msp
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org2/peer2/assets/tls-ca/tls-ca-cert.pem
./fabric-ca-client enroll -d -u https://peer1.org2.example.com:[email protected]:7053 --enrollment.profile tls --csr.hosts peer1.org2.example.com
# 修改私钥文件名称
mv org2/peer2/tls-msp/keystore/ab08fb99a61ab4b72bdbc08ea1be72483665f8bb6d7ed25dcf9efce7190fc1d4_sk org2/peer2/tls-msp/keystore/key.pem5、Enroll Org2’s Admin
mkdir -p org2/peer1/msp/admincerts
mkdir -p org2/peer2/msp/admincerts
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org2/admin
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org2/peer1/assets/ca/org2-ca-cert.pem
export FABRIC_CA_CLIENT_MSPDIR=msp
./fabric-ca-client enroll -d -u https://admin-org2:[email protected]:7056
cp org2/admin/msp/signcerts/cert.pem org2/peer1/msp/admincerts/org2-admin-cert.pem
cp org2/admin/msp/signcerts/cert.pem org2/peer2/msp/admincerts/org2-admin-cert.pem
mv org2/admin/msp/keystore/1534e670f0e43226fd0c3ba8204305c2283c10376e9deee72f81245ada9db05d_sk org2/admin/msp/keystore/priv_sk2.9 登记org0中orderer节点的证书
1、Enroll Orderer1 ECert 证书
mkdir -p org0/orderer1/assets/ca/ && cp org0/ca/crypto/ca-cert.pem org0/orderer1/assets/ca/org0-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org0/orderer1
export FABRIC_CA_CLIENT_MSPDIR=msp
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org0/orderer1/assets/ca/org0-ca-cert.pem
./fabric-ca-client enroll -d -u https://orderer0.example.com:[email protected]:7054
mv org0/orderer1/msp/keystore/568c077c8f0a3bc4e35a9294f87063e64ae9974190a6abe5ccd9f6872f33e1ab_sk org0/orderer1/msp/keystore/priv_sk2、Enroll Orderer1 TLS 证书
mkdir -p org0/orderer1/assets/tls-ca/ && cp tls-ca/crypto/tls-ca-cert.pem org0/orderer1/assets/tls-ca/tls-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org0/orderer1
export FABRIC_CA_CLIENT_MSPDIR=tls-msp
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org0/orderer1/assets/tls-ca/tls-ca-cert.pem
./fabric-ca-client enroll -d -u https://orderer0.example.com:[email protected]:7053 --enrollment.profile tls --csr.hosts 'orderer0.example.com,orderer0,192.168.235.130'
mv org0/orderer1/tls-msp/keystore/84f00c20de8393a0e5f817f0d6418c676ae38cc626a15ed69f8ba2a5050fc6bb_sk org0/orderer1/tls-msp/keystore/key.pem3、Enroll Orderer2 ECert 证书
mkdir -p org0/orderer2/assets/ca/ && cp org0/ca/crypto/ca-cert.pem org0/orderer2/assets/ca/org0-ca-cert.pem
export FABRIC_CA_CLIENT_MSPDIR=msp
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org0/orderer2
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org0/orderer2/assets/ca/org0-ca-cert.pem
./fabric-ca-client enroll -d -u https://orderer1.example.com:[email protected]:7054
mv org0/orderer2/msp/keystore/934954c7fa4431d1be86d92e3c2033646fbd4c6478ecfde799300990396af07a_sk org0/orderer2/msp/keystore/priv_sk4、Enroll Orderer2 TLS 证书
mkdir -p org0/orderer2/assets/tls-ca/ && cp tls-ca/crypto/tls-ca-cert.pem org0/orderer2/assets/tls-ca/tls-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org0/orderer2
export FABRIC_CA_CLIENT_MSPDIR=tls-msp
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org0/orderer2/assets/tls-ca/tls-ca-cert.pem
./fabric-ca-client enroll -d -u https://orderer1.example.com:[email protected]:7053 --enrollment.profile tls --csr.hosts 'orderer1.example.com,orderer1,192.168.235.130'
mv org0/orderer2/tls-msp/keystore/468adfca64821fb18467e4c69c744a129cc983c8b216c135972185ed61b6fbee_sk org0/orderer2/tls-msp/keystore/key.pem5、Enroll Orderer3 ECert 证书
mkdir -p org0/orderer3/assets/ca/ && cp org0/ca/crypto/ca-cert.pem org0/orderer3/assets/ca/org0-ca-cert.pem
export FABRIC_CA_CLIENT_MSPDIR=msp
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org0/orderer3
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org0/orderer3/assets/ca/org0-ca-cert.pem
./fabric-ca-client enroll -d -u https://orderer2.example.com:[email protected]:7054
mv org0/orderer3/msp/keystore/4b27550ee9eb1b40c05526e4bce2064a95baec5547be7ee694bd3cf48e7322ce_sk org0/orderer3/msp/keystore/priv_sk6、Enroll Orderer3 TLS 证书
mkdir -p org0/orderer3/assets/tls-ca/ && cp tls-ca/crypto/tls-ca-cert.pem org0/orderer3/assets/tls-ca/tls-ca-cert.pem
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org0/orderer3
export FABRIC_CA_CLIENT_MSPDIR=tls-msp
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org0/orderer3/assets/tls-ca/tls-ca-cert.pem
./fabric-ca-client enroll -d -u https://orderer2.example.com:[email protected]:7053 --enrollment.profile tls --csr.hosts 'orderer2.example.com,orderer2,192.168.235.130'
mv org0/orderer3/tls-msp/keystore/17294e44bc5ba90b7d4c09d8fa5bee6acecebf2a8feb752290831f7627284042_sk org0/orderer3/tls-msp/keystore/key.pem
7、Enroll Org0’s Admin
export FABRIC_CA_CLIENT_HOME=/tmp/hyperledger/org0/admin
export FABRIC_CA_CLIENT_TLS_CERTFILES=/tmp/hyperledger/org0/ca/crypto/ca-cert.pem
export FABRIC_CA_CLIENT_MSPDIR=msp
./fabric-ca-client enroll -d -u https://admin-org0:[email protected]:7054
mv /tmp/hyperledger/org0/admin/msp/keystore/9febcf800d108cac5f56efa82e99eefbd17907ebc0171e89447038cb01ee51c0_sk /tmp/hyperledger/org0/admin/msp/keystore/priv_sk
mkdir /tmp/hyperledger/org0/orderer1/msp/admincerts && cp /tmp/hyperledger/org0/admin/msp/signcerts/cert.pem /tmp/hyperledger/org0/orderer1/msp/admincerts/orderer-admin-cert.pem
mkdir /tmp/hyperledger/org0/orderer2/msp/admincerts && cp /tmp/hyperledger/org0/admin/msp/signcerts/cert.pem /tmp/hyperledger/org0/orderer2/msp/admincerts/orderer-admin-cert.pem
mkdir /tmp/hyperledger/org0/orderer3/msp/admincerts && cp /tmp/hyperledger/org0/admin/msp/signcerts/cert.pem /tmp/hyperledger/org0/orderer3/msp/admincerts/orderer-admin-cert.pem
到了此刻所有的证书文件都生成完毕。
三、构建 本地Orderer MSP 结构
上面已经将所有的证书文件都生成了,现在我们需要将文件目录结构弄得和官方的bin文件夹中cryptogen文件生成的文件夹一样。
3.1 Orderer 1 Local MSP
mkdir -p crypto-config/ordererOrganizations/example.com/orderers/orderer0.example.com/msp
mkdir -p crypto-config/ordererOrganizations/example.com/orderers/orderer0.example.com/tls
# TLS 私钥
cp org0/orderer1/tls-msp/keystore/key.pem crypto-config/ordererOrganizations/example.com/orderers/orderer0.example.com/tls/server.key
# TLS 签名证书
cp org0/orderer1/tls-msp/signcerts/cert.pem crypto-config/ordererOrganizations/example.com/orderers/orderer0.example.com/tls/server.crt
# TLS 根证书
cp org0/orderer1/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/ordererOrganizations/example.com/orderers/orderer0.example.com/tls/ca.crt
cp -r org0/orderer1/msp/ crypto-config/ordererOrganizations/example.com/orderers/orderer0.example.com/
mv crypto-config/ordererOrganizations/example.com/orderers/orderer0.example.com/msp/cacerts/0-0-0-0-7054.pem crypto-config/ordererOrganizations/example.com/orderers/orderer0.example.com/msp/cacerts/ca.example.com-cert.pem
mkdir -p crypto-config/ordererOrganizations/example.com/orderers/orderer0.example.com/msp/tlscacerts && cp org0/orderer1/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/ordererOrganizations/example.com/orderers/orderer0.example.com/msp/tlscacerts/tlsca.example.com-cert.pem
# 编写 config.yaml 文件
vim crypto-config/ordererOrganizations/example.com/orderers/orderer0.example.com/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: orderer
3.2 Orderer 2 Local MSP
mkdir -p crypto-config/ordererOrganizations/example.com/orderers/orderer1.example.com/msp
mkdir -p crypto-config/ordererOrganizations/example.com/orderers/orderer1.example.com/tls
# TLS 私钥
cp org0/orderer2/tls-msp/keystore/key.pem crypto-config/ordererOrganizations/example.com/orderers/orderer1.example.com/tls/server.key
# TLS 签名证书
cp org0/orderer2/tls-msp/signcerts/cert.pem crypto-config/ordererOrganizations/example.com/orderers/orderer1.example.com/tls/server.crt
# TLS 根证书
cp org0/orderer2/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/ordererOrganizations/example.com/orderers/orderer1.example.com/tls/ca.crt
# MSP
cp -r org0/orderer2/msp/ crypto-config/ordererOrganizations/example.com/orderers/orderer1.example.com/
mv crypto-config/ordererOrganizations/example.com/orderers/orderer1.example.com/msp/cacerts/0-0-0-0-7054.pem crypto-config/ordererOrganizations/example.com/orderers/orderer1.example.com/msp/cacerts/ca.example.com-cert.pem
mkdir -p crypto-config/ordererOrganizations/example.com/orderers/orderer1.example.com/msp/tlscacerts && cp org0/orderer2/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/ordererOrganizations/example.com/orderers/orderer1.example.com/msp/tlscacerts/tlsca.example.com-cert.pem
# 编写 config.yaml 文件
vim crypto-config/ordererOrganizations/example.com/orderers/orderer1.example.com/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: orderer3.3 Orderer 3 Local MSP
mkdir -p crypto-config/ordererOrganizations/example.com/orderers/orderer2.example.com/msp
mkdir -p crypto-config/ordererOrganizations/example.com/orderers/orderer2.example.com/tls
# TLS 私钥
cp org0/orderer3/tls-msp/keystore/key.pem crypto-config/ordererOrganizations/example.com/orderers/orderer2.example.com/tls/server.key
# TLS 签名证书
cp org0/orderer3/tls-msp/signcerts/cert.pem crypto-config/ordererOrganizations/example.com/orderers/orderer2.example.com/tls/server.crt
# TLS 根证书
cp org0/orderer3/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/ordererOrganizations/example.com/orderers/orderer2.example.com/tls/ca.crt
# MSP
cp -r org0/orderer3/msp/ crypto-config/ordererOrganizations/example.com/orderers/orderer2.example.com/
mv crypto-config/ordererOrganizations/example.com/orderers/orderer2.example.com/msp/cacerts/0-0-0-0-7054.pem crypto-config/ordererOrganizations/example.com/orderers/orderer2.example.com/msp/cacerts/ca.example.com-cert.pem
mkdir -p crypto-config/ordererOrganizations/example.com/orderers/orderer2.example.com/msp/tlscacerts && cp org0/orderer3/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/ordererOrganizations/example.com/orderers/orderer2.example.com/msp/tlscacerts/tlsca.example.com-cert.pem
# 编写 config.yaml 文件
vim crypto-config/ordererOrganizations/example.com/orderers/orderer2.example.com/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: orderer4、crypto-config/ordererOrganizations/example.com/msp/
mkdir -p crypto-config/ordererOrganizations/example.com/msp/admincerts
mkdir -p crypto-config/ordererOrganizations/example.com/msp/cacerts
mkdir -p crypto-config/ordererOrganizations/example.com/msp/tlscacerts
cp org0/orderer1/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/ordererOrganizations/example.com/msp/tlscacerts/tlsca.example.com-cert.pem
cp org0/orderer1/msp/cacerts/0-0-0-0-7054.pem crypto-config/ordererOrganizations/example.com/msp/cacerts/ca.example.com-cert.pem
cp /tmp/hyperledger/org0/admin/msp/signcerts/cert.pem crypto-config/ordererOrganizations/example.com/msp/admincerts/orderer-admin-cert.pem
# 编写 config.yaml 文件
vim crypto-config/ordererOrganizations/example.com/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: orderer四、构建 Org1 Peer 本地 MSP 结构
4.1 Org1 Peer1 Local MSP
mkdir -p crypto-config/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/ && cp -r org1/peer1/msp/ crypto-config/peerOrganizations/org1.example.com/peers/peer0.org1.example.com
mkdir -p crypto-config/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/tls
cp org1/peer1/tls-msp/signcerts/cert.pem crypto-config/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/tls/server.crt
cp org1/peer1/tls-msp/keystore/key.pem crypto-config/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/tls/server.key
cp org1/peer1/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/tls/ca.crt
mv crypto-config/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/msp/cacerts/0-0-0-0-7055.pem crypto-config/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/msp/cacerts/ca.example.com-cert.pem
# 编写 config.yaml 文件
vim crypto-config/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: orderer4.2 Org1 Peer2 Local MSP
mkdir -p crypto-config/peerOrganizations/org1.example.com/peers/peer1.org1.example.com/ && cp -r org1/peer2/msp/ crypto-config/peerOrganizations/org1.example.com/peers/peer1.org1.example.com/
mkdir -p crypto-config/peerOrganizations/org1.example.com/peers/peer1.org1.example.com/tls
cp org1/peer2/tls-msp/signcerts/cert.pem crypto-config/peerOrganizations/org1.example.com/peers/peer1.org1.example.com/tls/server.crt
cp org1/peer2/tls-msp/keystore/key.pem crypto-config/peerOrganizations/org1.example.com/peers/peer1.org1.example.com/tls/server.key
cp org1/peer2/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/peerOrganizations/org1.example.com/peers/peer1.org1.example.com/tls/ca.crt
mv crypto-config/peerOrganizations/org1.example.com/peers/peer1.org1.example.com/msp/cacerts/0-0-0-0-7055.pem crypto-config/peerOrganizations/org1.example.com/peers/peer1.org1.example.com/msp/cacerts/ca.example.com-cert.pem
# 编写 config.yaml 文件
vim crypto-config/peerOrganizations/org1.example.com/peers/peer1.org1.example.com/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: orderer4.3 crypto-config/peerOrganizations/org1.example.com/msp
mkdir -p crypto-config/peerOrganizations/org1.example.com/msp/admincerts
mkdir -p crypto-config/peerOrganizations/org1.example.com/msp/cacerts
mkdir -p crypto-config/peerOrganizations/org1.example.com/msp/tlscacerts
cp org1/admin/msp/cacerts/0-0-0-0-7055.pem crypto-config/peerOrganizations/org1.example.com/msp/cacerts/ca.org1.example.com-cert.pem
cp org1/peer1/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/peerOrganizations/org1.example.com/msp/tlscacerts/tlsca.org1.example.com-cert.pem
cp /tmp/hyperledger/org1/admin/msp/signcerts/cert.pem crypto-config/peerOrganizations/org1.example.com/msp/admincerts/org1-admin-cert.pem
# 编写 config.yaml 文件
vim crypto-config/peerOrganizations/org1.example.com/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.org1.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.org1.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.org1.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.org1.example.com-cert.pem
OrganizationalUnitIdentifier: orderer4.4 crypto-config/peerOrganizations/org1.example.com/users
mkdir -p crypto-config/peerOrganizations/org1.example.com/users/[email protected]
cp -r org1/admin/msp/ crypto-config/peerOrganizations/org1.example.com/users/[email protected]
mkdir -p crypto-config/peerOrganizations/org1.example.com/users/Admin\@org1.example.com/msp/admincerts
cp /tmp/hyperledger/org1/admin/msp/signcerts/cert.pem crypto-config/peerOrganizations/org1.example.com/users/Admin\@org1.example.com/msp/admincerts/org1-admin-cert.pem
mkdir -p crypto-config/peerOrganizations/org1.example.com/users/Admin\@org1.example.com/msp/tlscacerts
cp org1/peer1/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/peerOrganizations/org1.example.com/users/Admin\@org1.example.com/msp/tlscacerts/tlsca.org1.example.com-cert.pem
mv crypto-config/peerOrganizations/org1.example.com/users/[email protected]/msp/cacerts/0-0-0-0-7055.pem crypto-config/peerOrganizations/org1.example.com/users/[email protected]/msp/cacerts/ca.example.com-cert.pem
# 编写 config.yaml 文件
vim crypto-config/peerOrganizations/org1.example.com/users/[email protected]/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: orderer五、构建 Org2 Peer 本地 MSP 结构
5.1 Org2 Peer1 Local MSP
mkdir -p crypto-config/peerOrganizations/org2.example.com/peers/peer0.org2.example.com/ && cp -r org2/peer1/msp/ crypto-config/peerOrganizations/org2.example.com/peers/peer0.org2.example.com
mkdir -p crypto-config/peerOrganizations/org2.example.com/peers/peer0.org2.example.com/tls
cp org2/peer1/tls-msp/signcerts/cert.pem crypto-config/peerOrganizations/org2.example.com/peers/peer0.org2.example.com/tls/server.crt
cp org2/peer1/tls-msp/keystore/key.pem crypto-config/peerOrganizations/org2.example.com/peers/peer0.org2.example.com/tls/server.key
cp org2/peer1/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/peerOrganizations/org2.example.com/peers/peer0.org2.example.com/tls/ca.crt
mv crypto-config/peerOrganizations/org2.example.com/peers/peer0.org2.example.com/msp/cacerts/0-0-0-0-7056.pem crypto-config/peerOrganizations/org2.example.com/peers/peer0.org2.example.com/msp/cacerts/ca.example.com-cert.pem
# 编写 config.yaml 文件
vim crypto-config/peerOrganizations/org2.example.com/peers/peer0.org2.example.com/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: orderer5.2 Org2 Peer2 Local MSP
mkdir -p crypto-config/peerOrganizations/org2.example.com/peers/peer1.org2.example.com/ && cp -r org2/peer2/msp/ crypto-config/peerOrganizations/org2.example.com/peers/peer1.org2.example.com/
mkdir -p crypto-config/peerOrganizations/org2.example.com/peers/peer1.org2.example.com/tls
cp org2/peer2/tls-msp/signcerts/cert.pem crypto-config/peerOrganizations/org2.example.com/peers/peer1.org2.example.com/tls/server.crt
cp org2/peer2/tls-msp/keystore/key.pem crypto-config/peerOrganizations/org2.example.com/peers/peer1.org2.example.com/tls/server.key
cp org2/peer2/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/peerOrganizations/org2.example.com/peers/peer1.org2.example.com/tls/ca.crt
mv crypto-config/peerOrganizations/org2.example.com/peers/peer1.org2.example.com/msp/cacerts/0-0-0-0-7056.pem crypto-config/peerOrganizations/org2.example.com/peers/peer1.org2.example.com/msp/cacerts/ca.example.com-cert.pem
# 编写 config.yaml 文件
vim crypto-config/peerOrganizations/org2.example.com/peers/peer1.org2.example.com/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: orderer5.3 crypto-config/peerOrganizations/org2.example.com/msp
mkdir -p crypto-config/peerOrganizations/org2.example.com/msp/admincerts
mkdir -p crypto-config/peerOrganizations/org2.example.com/msp/cacerts
mkdir -p crypto-config/peerOrganizations/org2.example.com/msp/tlscacerts
cp org2/admin/msp/cacerts/0-0-0-0-7056.pem crypto-config/peerOrganizations/org2.example.com/msp/cacerts/ca.org2.example.com-cert.pem
cp org2/peer1/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/peerOrganizations/org2.example.com/msp/tlscacerts/tlsca.org2.example.com-cert.pem
cp /tmp/hyperledger/org2/admin/msp/signcerts/cert.pem crypto-config/peerOrganizations/org2.example.com/msp/admincerts/org2-admin-cert.pem
# 编写 config.yaml 文件
vim crypto-config/peerOrganizations/org2.example.com/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.org2.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.org2.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.org2.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.org2.example.com-cert.pem
OrganizationalUnitIdentifier: orderer5.4 crypto-config/peerOrganizations/org2.example.com/users
mkdir -p crypto-config/peerOrganizations/org2.example.com/users/[email protected]
cp -r org2/admin/msp/ crypto-config/peerOrganizations/org2.example.com/users/[email protected]
mkdir -p crypto-config/peerOrganizations/org2.example.com/users/Admin\@org2.example.com/msp/admincerts
cp /tmp/hyperledger/org2/admin/msp/signcerts/cert.pem crypto-config/peerOrganizations/org2.example.com/users/Admin\@org2.example.com/msp/admincerts/org2-admin-cert.pem
mkdir -p crypto-config/peerOrganizations/org2.example.com/users/Admin\@org2.example.com/msp/tlscacerts
cp org2/peer1/tls-msp/tlscacerts/tls-0-0-0-0-7053.pem crypto-config/peerOrganizations/org2.example.com/users/Admin\@org2.example.com/msp/tlscacerts/tlsca.org2.example.com-cert.pem
mv crypto-config/peerOrganizations/org2.example.com/users/[email protected]/msp/cacerts/0-0-0-0-7056.pem crypto-config/peerOrganizations/org2.example.com/users/[email protected]/msp/cacerts/ca.example.com-cert.pem
# 编写 config.yaml 文件
vim crypto-config/peerOrganizations/org2.example.com/users/[email protected]/msp/config.yaml
NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/ca.example.com-cert.pem
OrganizationalUnitIdentifier: orderer最后查看一下结果:
tree crypto-config/crypto-config/
├── ordererOrganizations
│ └── example.com
│ ├── msp
│ │ ├── admincerts
│ │ │ └── orderer-admin-cert.pem
│ │ ├── cacerts
│ │ │ └── ca.example.com-cert.pem
│ │ ├── config.yaml
│ │ └── tlscacerts
│ │ └── tlsca.example.com-cert.pem
│ └── orderers
│ ├── orderer0.example.com
│ │ ├── msp
│ │ │ ├── admincerts
│ │ │ │ └── orderer-admin-cert.pem
│ │ │ ├── cacerts
│ │ │ │ └── ca.example.com-cert.pem
│ │ │ ├── config.yaml
│ │ │ ├── IssuerPublicKey
│ │ │ ├── IssuerRevocationPublicKey
│ │ │ ├── keystore
│ │ │ │ └── priv_sk
│ │ │ ├── signcerts
│ │ │ │ └── cert.pem
│ │ │ ├── tlscacerts
│ │ │ │ └── tlsca.example.com-cert.pem
│ │ │ └── user
│ │ └── tls
│ │ ├── ca.crt
│ │ ├── server.crt
│ │ └── server.key
│ ├── orderer1.example.com
│ │ ├── msp
│ │ │ ├── admincerts
│ │ │ │ └── orderer-admin-cert.pem
│ │ │ ├── cacerts
│ │ │ │ └── ca.example.com-cert.pem
│ │ │ ├── config.yaml
│ │ │ ├── IssuerPublicKey
│ │ │ ├── IssuerRevocationPublicKey
│ │ │ ├── keystore
│ │ │ │ └── priv_sk
│ │ │ ├── signcerts
│ │ │ │ └── cert.pem
│ │ │ ├── tlscacerts
│ │ │ │ └── tlsca.example.com-cert.pem
│ │ │ └── user
│ │ └── tls
│ │ ├── ca.crt
│ │ ├── server.crt
│ │ └── server.key
│ └── orderer2.example.com
│ ├── msp
│ │ ├── admincerts
│ │ │ └── orderer-admin-cert.pem
│ │ ├── cacerts
│ │ │ └── ca.example.com-cert.pem
│ │ ├── config.yaml
│ │ ├── IssuerPublicKey
│ │ ├── IssuerRevocationPublicKey
│ │ ├── keystore
│ │ │ └── priv_sk
│ │ ├── signcerts
│ │ │ └── cert.pem
│ │ ├── tlscacerts
│ │ │ └── tlsca.example.com-cert.pem
│ │ └── user
│ └── tls
│ ├── ca.crt
│ ├── server.crt
│ └── server.key
└── peerOrganizations
├── org1.example.com
│ ├── msp
│ │ ├── admincerts
│ │ │ └── org1-admin-cert.pem
│ │ ├── cacerts
│ │ │ └── ca.org1.example.com-cert.pem
│ │ ├── config.yaml
│ │ └── tlscacerts
│ │ └── tlsca.org1.example.com-cert.pem
│ ├── peers
│ │ ├── peer0.org1.example.com
│ │ │ ├── msp
│ │ │ │ ├── admincerts
│ │ │ │ │ └── org1-admin-cert.pem
│ │ │ │ ├── cacerts
│ │ │ │ │ └── ca.example.com-cert.pem
│ │ │ │ ├── config.yaml
│ │ │ │ ├── IssuerPublicKey
│ │ │ │ ├── IssuerRevocationPublicKey
│ │ │ │ ├── keystore
│ │ │ │ │ └── priv_sk
│ │ │ │ ├── signcerts
│ │ │ │ │ └── cert.pem
│ │ │ │ └── user
│ │ │ └── tls
│ │ │ ├── ca.crt
│ │ │ ├── server.crt
│ │ │ └── server.key
│ │ └── peer1.org1.example.com
│ │ ├── msp
│ │ │ ├── admincerts
│ │ │ │ └── org1-admin-cert.pem
│ │ │ ├── cacerts
│ │ │ │ └── ca.example.com-cert.pem
│ │ │ ├── config.yaml
│ │ │ ├── IssuerPublicKey
│ │ │ ├── IssuerRevocationPublicKey
│ │ │ ├── keystore
│ │ │ │ └── priv_sk
│ │ │ ├── signcerts
│ │ │ │ └── cert.pem
│ │ │ └── user
│ │ └── tls
│ │ ├── ca.crt
│ │ ├── server.crt
│ │ └── server.key
│ └── users
│ └── [email protected]
│ └── msp
│ ├── admincerts
│ │ └── org1-admin-cert.pem
│ ├── cacerts
│ │ └── ca.example.com-cert.pem
│ ├── config.yaml
│ ├── IssuerPublicKey
│ ├── IssuerRevocationPublicKey
│ ├── keystore
│ │ └── priv_sk
│ ├── signcerts
│ │ └── cert.pem
│ ├── tlscacerts
│ │ └── tlsca.org1.example.com-cert.pem
│ └── user
└── org2.example.com
├── msp
│ ├── admincerts
│ │ └── org2-admin-cert.pem
│ ├── cacerts
│ │ └── ca.org2.example.com-cert.pem
│ ├── config.yaml
│ └── tlscacerts
│ └── tlsca.org2.example.com-cert.pem
├── peers
│ ├── peer0.org2.example.com
│ │ ├── msp
│ │ │ ├── admincerts
│ │ │ │ └── org2-admin-cert.pem
│ │ │ ├── cacerts
│ │ │ │ └── ca.example.com-cert.pem
│ │ │ ├── config.yaml
│ │ │ ├── IssuerPublicKey
│ │ │ ├── IssuerRevocationPublicKey
│ │ │ ├── keystore
│ │ │ │ └── priv_sk
│ │ │ ├── signcerts
│ │ │ │ └── cert.pem
│ │ │ └── user
│ │ └── tls
│ │ ├── ca.crt
│ │ ├── server.crt
│ │ └── server.key
│ └── peer1.org2.example.com
│ ├── msp
│ │ ├── admincerts
│ │ │ └── org2-admin-cert.pem
│ │ ├── cacerts
│ │ │ └── ca.example.com-cert.pem
│ │ ├── config.yaml
│ │ ├── IssuerPublicKey
│ │ ├── IssuerRevocationPublicKey
│ │ ├── keystore
│ │ │ └── priv_sk
│ │ ├── signcerts
│ │ │ └── cert.pem
│ │ └── user
│ └── tls
│ ├── ca.crt
│ ├── server.crt
│ └── server.key
└── users
└── [email protected]
└── msp
├── admincerts
│ └── org2-admin-cert.pem
├── cacerts
│ └── ca.example.com-cert.pem
├── config.yaml
├── IssuerPublicKey
├── IssuerRevocationPublicKey
├── keystore
│ └── priv_sk
├── signcerts
│ └── cert.pem
├── tlscacerts
│ └── tlsca.org2.example.com-cert.pem
└── user
97 directories, 101 files
准备好 MSP 目录结构后就可以搭建 Fabric 网络了。
