上一篇文章讲了如何在centos7下自制高版本的openssh-server的rpm包(高版本的rpm包没有镜像站提供,所以只好自己制作啦)
文章地址:Linux|编译最新版的openssh-server-9.3的rpm包(一)_晚风_END的博客-CSDN博客
那么,这些rpm包如何使用呢?
一,
相关rpm包下载地址:
链接:https://pan.baidu.com/s/1tlCKx9v-xK1kJ1Qv-f4DIA?pwd=open
提取码:open
--来自百度网盘超级会员V5的分享
压缩包内容如下:
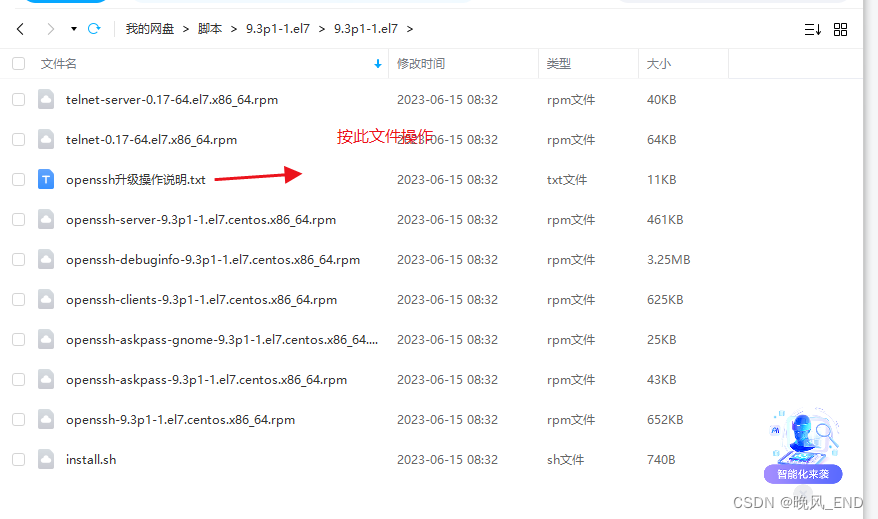
二,
部署文件
!!!!!本文档适用于centos7以及redhat7 版本的操作系统,其它操作系统不可使用!!!!!!!
升级openssh的具体步骤如下:
一,
升级前的检查工作
检查sshd的版本
sshd -V
该命令输出sshd服务的版本,确认是低于9.3版本,符合升级条件。
示例如下:
[root@EULER2 ~]# ssh -V
OpenSSH_7.4p1, OpenSSL 1.0.2k-fips 26 Jan 2017
[root@EULER2 ~]# sshd -V
unknown option -- V
OpenSSH_7.4p1, OpenSSL 1.0.2k-fips 26 Jan 2017
usage: sshd [-46DdeiqTt] [-C connection_spec] [-c host_cert_file]
[-E log_file] [-f config_file] [-g login_grace_time]
[-h host_key_file] [-o option] [-p port] [-u len]
可以看到ssh客户端和服务端版本都较低,是符合升级条件的。
检查系统的版本
示例如下:
[root@EULER2 ~]# cat /etc/redhat-release
EulerOS release 2.0 (SP5)
可以看到,系统是欧拉2.0,等于是centos7,符合升级条件。
二,
将9.3p1-1.el7 这个文件夹上传到待升级sshd服务的服务器上
备份/etc/pam.d/sshd 这个文件,具体命令如下:
[root@EULER2 ~]# cd 9.3p1-1.el7/
[root@EULER2 9.3p1-1.el7]# cp /etc/pam.d/sshd{,.bak}
###说明:有的版本不同,可能没有sshd文件,备份带有sshd的文件即可,
三,
为了防止sshd升级失败导致sshd彻底不可用的极端情况,需要安装telnet-server作为备份远程连接手段。
安装telnet目录下的文件,telnet\telnet-server-0.17-64.el7.x86_64.rpm
具体命令的示例为:
[root@EULER2 ~]# rpm -ivh telnet-server-0.17-64.el7.x86_64.rpm
warning: telnet-server-0.17-64.el7.x86_64.rpm: Header V3 RSA/SHA256 Signature, key ID f4a80eb5: NOKEY
Preparing... ################################# [100%]
Updating / installing...
1:telnet-server-1:0.17-64.el7 ################################# [100%]
[root@EULER2 ~]# systemctl start telnet.socket &&systemctl status telnet.socket
● telnet.socket - Telnet Server Activation Socket
Loaded: loaded (/usr/lib/systemd/system/telnet.socket; disabled; vendor preset: disabled)
Active: active (listening) since Thu 2023-06-08 01:07:44 CST; 19ms ago
Docs: man:telnetd(8)
Listen: [::]:23 (Stream)
Accepted: 0; Connected: 0
Jun 08 01:07:44 EULER2 systemd[1]: Listening on Telnet Server Activation Socket.、
###假设遇到了极端情况,服务器的sshd服务彻底不可用,此时可用telnet远程登陆到服务器进行修复工作。
四,
正式安装sshd服务
命令运行示例如下(在rpm包所在目录执行安装脚本):
[root@EULER2 9.3p1-1.el7]# bash install.sh
Loaded plugins: fastestmirror
Examining openssh-server-9.3p1-1.el7.centos.x86_64.rpm: openssh-server-9.3p1-1.el7.centos.x86_64
Marking openssh-server-9.3p1-1.el7.centos.x86_64.rpm as an update to openssh-server-7.4p1-16.h10.eulerosv2r7.x86_64
Examining openssh-clients-9.3p1-1.el7.centos.x86_64.rpm: openssh-clients-9.3p1-1.el7.centos.x86_64
Marking openssh-clients-9.3p1-1.el7.centos.x86_64.rpm as an update to openssh-clients-7.4p1-16.h10.eulerosv2r7.x86_64
Examining openssh-9.3p1-1.el7.centos.x86_64.rpm: openssh-9.3p1-1.el7.centos.x86_64
Marking openssh-9.3p1-1.el7.centos.x86_64.rpm as an update to openssh-7.4p1-16.h10.eulerosv2r7.x86_64
Resolving Dependencies
--> Running transaction check
---> Package openssh.x86_64 0:7.4p1-16.h10.eulerosv2r7 will be updated
---> Package openssh.x86_64 0:9.3p1-1.el7.centos will be an update
---> Package openssh-clients.x86_64 0:7.4p1-16.h10.eulerosv2r7 will be updated
---> Package openssh-clients.x86_64 0:9.3p1-1.el7.centos will be an update
---> Package openssh-server.x86_64 0:7.4p1-16.h10.eulerosv2r7 will be updated
---> Package openssh-server.x86_64 0:9.3p1-1.el7.centos will be an update
--> Finished Dependency Resolution
Dependencies Resolved
=================================================================================================================
Package Arch Version Repository Size
=================================================================================================================
Updating:
openssh x86_64 9.3p1-1.el7.centos /openssh-9.3p1-1.el7.centos.x86_64 3.0 M
openssh-clients x86_64 9.3p1-1.el7.centos /openssh-clients-9.3p1-1.el7.centos.x86_64 2.4 M
openssh-server x86_64 9.3p1-1.el7.centos /openssh-server-9.3p1-1.el7.centos.x86_64 1.1 M
Transaction Summary
=================================================================================================================
Upgrade 3 Packages
Total size: 6.5 M
Downloading packages:
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Warning: RPMDB altered outside of yum.
Updating : openssh-9.3p1-1.el7.centos.x86_64 1/6
Updating : openssh-clients-9.3p1-1.el7.centos.x86_64 2/6
warning: /etc/ssh/ssh_config created as /etc/ssh/ssh_config.rpmnew
Updating : openssh-server-9.3p1-1.el7.centos.x86_64 3/6
warning: /etc/ssh/sshd_config created as /etc/ssh/sshd_config.rpmnew
Cleanup : openssh-server-7.4p1-16.h10.eulerosv2r7.x86_64 4/6
Cleanup : openssh-clients-7.4p1-16.h10.eulerosv2r7.x86_64 5/6
Cleanup : openssh-7.4p1-16.h10.eulerosv2r7.x86_64 6/6
Verifying : openssh-clients-9.3p1-1.el7.centos.x86_64 1/6
Verifying : openssh-9.3p1-1.el7.centos.x86_64 2/6
Verifying : openssh-server-9.3p1-1.el7.centos.x86_64 3/6
Verifying : openssh-server-7.4p1-16.h10.eulerosv2r7.x86_64 4/6
Verifying : openssh-clients-7.4p1-16.h10.eulerosv2r7.x86_64 5/6
Verifying : openssh-7.4p1-16.h10.eulerosv2r7.x86_64 6/6
Updated:
openssh.x86_64 0:9.3p1-1.el7.centos openssh-clients.x86_64 0:9.3p1-1.el7.centos
openssh-server.x86_64 0:9.3p1-1.el7.centos
Complete!
配置openssh
PasswordAuthentication yes
PermitRootLogin yes
Port 10022
UseDNS no
Banner /etc/issue
setenforce: SELinux is disabled
修改/etc/ssh/sshd_config 文件,PermitRootLogin yes Port 10022 PasswordAuthentication yes
确认以上内容在该配置文件内
查看服务状态,假如有如下报错:
[root@EULER2 9.3p1-1.el7]# systemctl status sshd
● sshd.service - SYSV: OpenSSH server daemon
Loaded: loaded (/etc/rc.d/init.d/sshd; bad; vendor preset: enabled)
Active: active (running) since Thu 2023-06-08 01:10:47 CST; 6min ago
Docs: man:systemd-sysv-generator(8)
Process: 5282 ExecStart=/etc/rc.d/init.d/sshd start (code=exited, status=0/SUCCESS)
Main PID: 5290 (sshd)
CGroup: /system.slice/system-hostos.slice/sshd.service
└─5290 sshd: /usr/sbin/sshd [listener] 0 of 10-100 startups
Jun 08 01:13:24 EULER2 sshd[7451]: rexec line 146: Deprecated option RSAAuthentication
Jun 08 01:13:24 EULER2 sshd[7451]: rexec line 148: Deprecated option RhostsRSAAuthentication
Jun 08 01:13:24 EULER2 sshd[7451]: Connection from 192.168.76.1 port 53799 on 192.168.76.12 port 22
Jun 08 01:13:25 EULER2 sshd[7451]: reprocess config line 146: Deprecated option RSAAuthentication
Jun 08 01:13:25 EULER2 sshd[7451]: reprocess config line 148: Deprecated option RhostsRSAAuthentication
Jun 08 01:13:25 EULER2 sshd[7451]: PAM unable to dlopen(/usr/lib64/security/pam_stack.so): /usr/lib64/sec...ctory
Jun 08 01:13:25 EULER2 sshd[7451]: PAM adding faulty module: /usr/lib64/security/pam_stack.so
Jun 08 01:13:25 EULER2 sshd[7451]: Failed password for root from 192.168.76.1 port 53799 ssh2
Jun 08 01:13:28 EULER2 sshd[7451]: error: Received disconnect from 192.168.76.1 port 53799:0: [preauth]
Jun 08 01:13:28 EULER2 sshd[7451]: Disconnected from authenticating user root 192.168.76.1 port 53799 [preauth]
恢复使用旧的密码校验插件配置文件:
[root@EULER2 9.3p1-1.el7]# mv /etc/pam.d/sshd /opt/
[root@EULER2 9.3p1-1.el7]# mv /etc/pam.d/sshd.bak /etc/pam.d/sshd
重启sshd服务并再次查看服务状态:
[root@EULER2 9.3p1-1.el7]# systemctl restart sshd
[root@EULER2 9.3p1-1.el7]# systemctl status sshd
● sshd.service - SYSV: OpenSSH server daemon
Loaded: loaded (/etc/rc.d/init.d/sshd; bad; vendor preset: enabled)
Active: active (running) since Thu 2023-06-08 01:17:10 CST; 1s ago
Docs: man:systemd-sysv-generator(8)
Process: 10506 ExecStop=/etc/rc.d/init.d/sshd stop (code=exited, status=0/SUCCESS)
Process: 10513 ExecStart=/etc/rc.d/init.d/sshd start (code=exited, status=0/SUCCESS)
Main PID: 10520 (sshd)
CGroup: /system.slice/system-hostos.slice/sshd.service
└─10520 sshd: /usr/sbin/sshd [listener] 0 of 10-100 startups
Jun 08 01:17:10 EULER2 systemd[1]: Starting SYSV: OpenSSH server daemon...
Jun 08 01:17:10 EULER2 sshd[10513]: Starting sshd:/etc/ssh/sshd_config line 146: Deprecated option RSAAut...ation
Jun 08 01:17:10 EULER2 sshd[10513]: /etc/ssh/sshd_config line 148: Deprecated option RhostsRSAAuthentication
Jun 08 01:17:10 EULER2 sshd[10520]: Server listening on :: port 22.
Jun 08 01:17:10 EULER2 sshd[10520]: Server listening on 0.0.0.0 port 22.
Jun 08 01:17:10 EULER2 sshd[10513]: [ OK ]
Jun 08 01:17:10 EULER2 systemd[1]: Started SYSV: OpenSSH server daemon.
Hint: Some lines were ellipsized, use -l to show in full.
五,
测试流程
#####注意,原ssh连接窗口不能关!!!!!!!!!!!!!!!!!!
新增xshell窗口,如能正确登陆,表明sshd服务功能正常。
查看ssh和sshd的版本:
[root@EULER2 ~]# ssh -V
OpenSSH_9.3p1, OpenSSL 1.0.2k-fips 26 Jan 2017
[root@EULER2 ~]# sshd -V
OpenSSH_9.3, OpenSSL 1.0.2k-fips 26 Jan 2017
查看sshd服务的状态:
示例代码如下:
[root@EULER2 ~]# systemctl status sshd
● sshd.service - SYSV: OpenSSH server daemon
Loaded: loaded (/etc/rc.d/init.d/sshd; bad; vendor preset: enabled)
Active: active (running) since Thu 2023-06-08 01:17:10 CST; 6min ago
Docs: man:systemd-sysv-generator(8)
Process: 10506 ExecStop=/etc/rc.d/init.d/sshd stop (code=exited, status=0/SUCCESS)
Process: 10513 ExecStart=/etc/rc.d/init.d/sshd start (code=exited, status=0/SUCCESS)
Main PID: 10520 (sshd)
CGroup: /system.slice/system-hostos.slice/sshd.service
└─10520 sshd: /usr/sbin/sshd [listener] 0 of 10-100 startups
Jun 08 01:17:10 EULER2 sshd[10520]: Server listening on :: port 22.
Jun 08 01:17:10 EULER2 sshd[10520]: Server listening on 0.0.0.0 port 22.
Jun 08 01:17:10 EULER2 sshd[10513]: [ OK ]
Jun 08 01:17:10 EULER2 systemd[1]: Started SYSV: OpenSSH server daemon.
Jun 08 01:19:56 EULER2 sshd[12747]: rexec line 146: Deprecated option RSAAuthentication
Jun 08 01:19:56 EULER2 sshd[12747]: rexec line 148: Deprecated option RhostsRSAAuthentication
Jun 08 01:19:56 EULER2 sshd[12747]: Connection from 192.168.76.1 port 53852 on 192.168.76.12 port 22
Jun 08 01:19:57 EULER2 sshd[12747]: reprocess config line 146: Deprecated option RSAAuthentication
Jun 08 01:19:57 EULER2 sshd[12747]: reprocess config line 148: Deprecated option RhostsRSAAuthentication
Jun 08 01:19:57 EULER2 sshd[12747]: Accepted password for root from 192.168.76.1 port 53852 ssh2
表明此次sshd升级成功!!!!
停止telnet服务:
[root@EULER2 ~]# systemctl stop telnet.socket
清理相关安装文件,本次升级完成。
补充:
切记@@@@@@~~~~~~~~~~~~~~切记!!!!!!!!!!!!!!!!!!!!!
telnet默认是不可以root用户登陆的,需要做一下设置,编辑/etc/securetty 将以后可能用到的tty终端名称写入就可以了
pts/0
pts/1
pts/2
pts/3
pts/4
pts/5
pts/6
pts/7
pts/8
pts/9