准备
k8s各组件版本对应关系: https://github.com/kubernetes/kubernetes/blob/master/build/dependencies.yaml
192.168.220.100 vip-ha
192.168.220.128 k8s-master01 h1
192.168.220.129 k8s-master02 h2
192.168.220.130 k8s-master03 h3
192.168.220.132 k8s-node01 h5
192.168.220.133 k8s-node02 h6
k8s service-net 10.96.0.0/12
k8s pod-net 172.168.0.0/12
[root@h1 k8s]# uname -a
Linux h1 6.2.2-1.el7.elrepo.x86_64 #1 SMP PREEMPT_DYNAMIC Thu Mar 2 15:47:32 EST 2023 x86_64 x86_64 x86_64 GNU/Linux
一、基础环境
tar -zxvf kubernetes-server-linux-amd64.tar.gz --strip-components=3 -C /usr/local/bin kubernetes/server/bin/kube{
let,ctl,-apiserver,-controller-manager,-scheduler,-proxy}
tar -zxvf etcd-v3.5.6-linux-amd64.tar.gz --strip-components=1 -C /usr/local/bin etcd-v3.5.6-linux-amd64/etcd{
,ctl}
for i in {
h1,h2,h3};
> do scp -r /usr/local/bin/* $i:/usr/local/bin
> for n in {
h5,h6}
> do scp -r /usr/local/bin/kube{
let,-proxy} $n:/usr/local/bin/;
> done
> done
CN(Common Name): etcd/kube-apiserver从证书中提取该字段作为请求的用户名 (User Name);浏览器使用该字段验证网站是否合法,一般写的是域名。
O(Organization): etcd/kube-apiserver 从证书中提取该字段作为请求用户所属的组 (Group);
这两个参数在后面的kubernetes启用RBAC模式中很重要,因为需要设置kubelet、admin等角色权限
C(Country): 国家
ST(State): 州,省
L(Locality): 地区,城市
O(Organization Name): 组织名称,公司名称
OU(Organization Unit Name): 组织单位名称,公司部门
cat > etcd-ca-csr.json << EOF
{
"CN": "etcd",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Beijing",
"L": "Beijing",
"O": "etcd",
"OU": "Etcd Security"
}
],
"ca": {
"expiry": "876000h"
}
}
EOF
cfssl gencert -initca etcd-ca-csr.json | cfssljson -bare /etc/etcd/ssl/etcd-ca
创建ca-config.json
ca-config.json: 可以定义多个 profiles,分别指定不同的过期时间、使用场景等参数;后续在签名证书时使用某个 profile;此实例只有一个kubernetes模板。
signing: 表示该证书可用于签名其它证书;生成的 ca.pem 证书中 CA=TRUE;
server auth: 表示client可以用该CA对server提供的证书进行验证;
client auth: 表示server可以用该CA对client提供的证书进行验证;
cat > ca-config.json << EOF
{
"signing": {
"default": {
"expiry": "876000h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "876000h"
}
}
}
}
EOF
etcd-csr.json (hosts可以预留,方便扩展)
cat > etcd-csr.json << EOF
{
"CN": "etcd",
"hosts": [
"127.0.0.1",
"k8s-master01",
"k8s-master02",
"k8s-master03",
"192.168.220.128",
"192.168.220.129",
"192.168.220.130"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Beijing",
"L": "Beijing",
"O": "etcd",
"OU": "Etcd Security"
}
]
}
EOF
cfssl gencert -ca=/etc/etcd/ssl/etcd-ca.pem -config=ca-config.json -ca-key=/etc/etcd/ssl/etcd-ca-key.pem -profile=kubernetes etcd-csr.json | cfssljson -bare /etc/etcd/ssl/etcd
三台:github.com containerd 1,7,3 amd64
tar xf tar -C /
critcl images
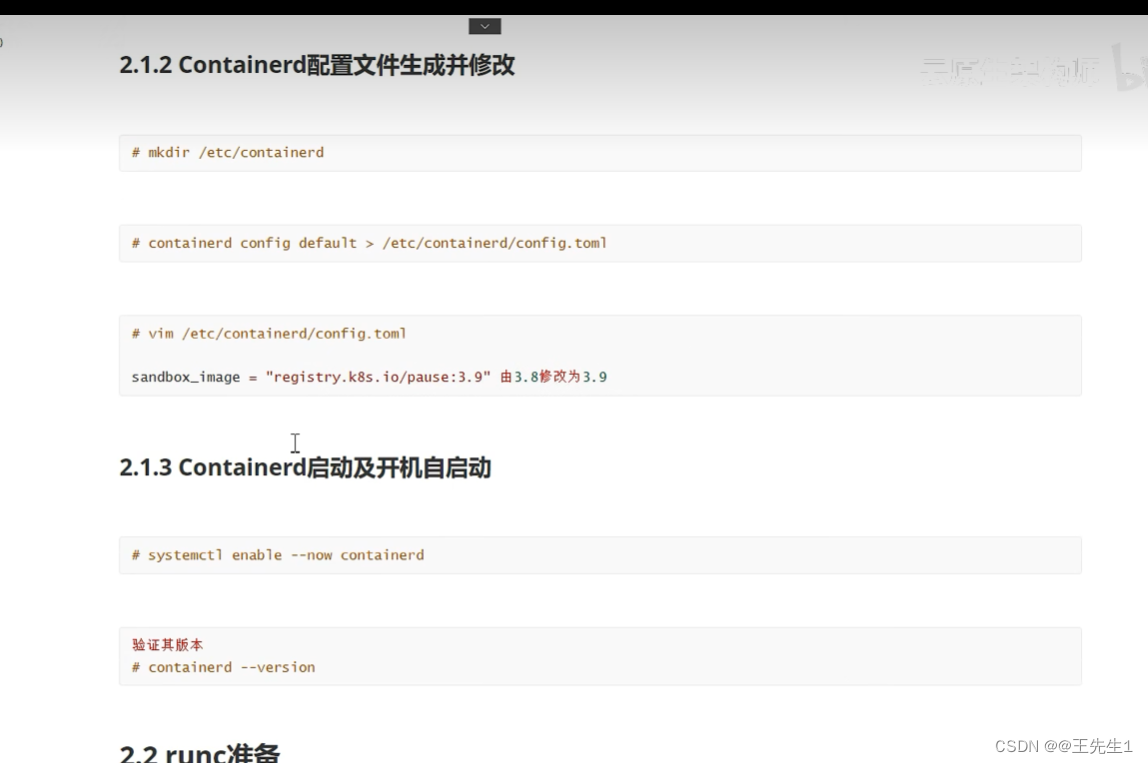
runc 1.1.9
libseccomp-2.5.4库文件准备 yum gperf安装包
./configure
make
make install
find / -name “libseccomp.so”
which runc
runc.amd64 download 替换
chmod +x
rm -rf “which runc”
mv