一、实验目的
- 熟悉ipsec vpn 的应用场景
- 掌握ipsec vpn 的配置方法
想要华为数通配套实验拓扑和配置笔记的朋友们点赞+关注,评论区留下邮箱发给你!
二、实验拓扑
实验拓扑如图所示:

三、实验步骤
(1)如图所示配置IP地址
PC1的配置
PC1的配置如图所示:

PC2的配置
PC2的IP地址的配置如图所示:

AR1的配置
<Huawei>system-view
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname AR1
[AR1]interface g0/0/0
[AR1-GigabitEthernet0/0/0]ip address 192.168.1.254 24
[AR1-GigabitEthernet0/0/0]quit
[AR1]interface g0/0/1
[AR1-GigabitEthernet0/0/1]ip address 172.16.1.254 24
[AR1-GigabitEthernet0/0/1]quit
[AR1]interface g0/0/2
[AR1-GigabitEthernet0/0/2]ip address 12.1.1.1 24
[AR1-GigabitEthernet0/0/2]quit
R2的配置
<Huawei>system-view
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname AR2
[AR2]interface g0/0/2
[AR2-GigabitEthernet0/0/2]ip address 12.1.1.2 24
[AR2-GigabitEthernet0/0/2]quit
[AR2]interface g0/0/0
[AR2-GigabitEthernet0/0/0]ip address 23.1.1.2 24
[AR2-GigabitEthernet0/0/0]quit
[AR2]interface LoopBack 0
[AR2-LoopBack0]ip address 2.2.2.2 32
[AR2-LoopBack0]quit
R3的配置
<Huawei>system-view
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname AR3
[AR3]interface g0/0/0
[AR3-GigabitEthernet0/0/0]ip address 23.1.1.3 24
[AR3-GigabitEthernet0/0/0]quit
[AR3]interface g0/0/1
[AR3-GigabitEthernet0/0/1]ip address 192.168.2.254 24
[AR3-GigabitEthernet0/0/1]quit
[AR3]interface g0/0/2
[AR3-GigabitEthernet0/0/2]ip address 172.16.2.254 24
[AR3-GigabitEthernet0/0/2]quit
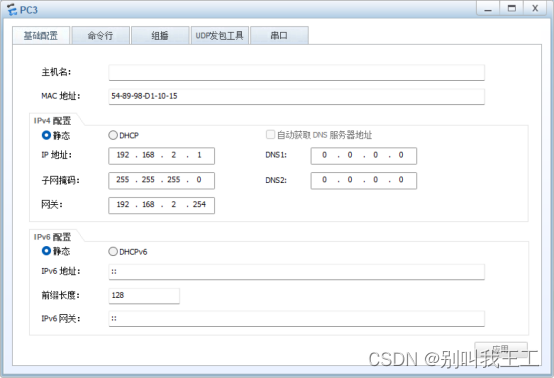
PC3的配置
PC3的IP地址如图所示:
PC4的配置
PC4的IP地址如图所示:

(2)配置网络连通性
AR1的配置
[AR1]ip route-static 0.0.0.0 0.0.0.0 12.1.1.2
AR3的配置
[AR3]ip route-static 0.0.0.0 0.0.0.0 23.1.1.2
(3)配置IPSEC VPN
第一步:定义感兴趣的流量
AR1的配置
[AR1]acl 3000
[AR1-acl-adv-3000]rule 10 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
[AR1-acl-adv-3000]quit
AR3的配置
[AR3]acl 3000
[AR3-acl-adv-3000]rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
[AR3-acl-adv-3000]quit
【技术要点】
满足ACL的流量才能走VPN
第二步:设置提议
AR1的配置
[AR1]ipsec proposal 1
[AR1-ipsec-proposal-1]quit
AR3的配置
[AR3]ipsec proposal 1
[AR3-ipsec-proposal-1]quit
在AR1上查看提议
[AR1]display ipsec proposal //查看IPSEC VPN 提议
Number of proposals: 1 //编号为1
IPSec proposal name: 1 //名字为1
Encapsulation mode: Tunnel //封装模式为隧道
Transform : esp-new //封装为ESP
ESP protocol : Authentication MD5-HMAC-96 //认证模式为MD5
Encryption DES //加密用DES
【技术要点】
1、默认模式
2、两边的提议要一样
第三步:设置安全策略
AR1的配置
[AR1]ipsec policy hcip 1 manual
[AR1-ipsec-policy-manual-hcip-1]security acl 3000
[AR1-ipsec-policy-manual-hcip-1]proposal 1
[AR1-ipsec-policy-manual-hcip-1]tunnel local 12.1.1.1
[AR1-ipsec-policy-manual-hcip-1]tunnel remote 23.1.1.3
[AR1-ipsec-policy-manual-hcip-1]sa spi outbound esp 1234
[AR1-ipsec-policy-manual-hcip-1]sa spi inbound esp 4321
[AR1-ipsec-policy-manual-hcip-1]sa string-key inbound esp simple lwljh
[AR1-ipsec-policy-manual-hcip-1]sa string-key outbound esp simple lwljh
AR3的配置
[AR3]ipsec policy hcip 1 manual
[AR3-ipsec-policy-manual-hcip-1]security acl 3000
[AR3-ipsec-policy-manual-hcip-1]proposal 1
[AR3-ipsec-policy-manual-hcip-1]tunnel local 23.1.1.3
[AR3-ipsec-policy-manual-hcip-1]tunnel remote 12.1.1.1
[AR3-ipsec-policy-manual-hcip-1]sa spi outbound esp 4321
[AR3-ipsec-policy-manual-hcip-1]sa spi inbound esp 1234
[AR3-ipsec-policy-manual-hcip-1]sa string-key inbound esp simple lwljh
[AR3-ipsec-policy-manual-hcip-1]sa string-key outbound esp simple lwljh
[AR3-ipsec-policy-manual-hcip-1]quit
查看策略
[AR1]display ipsec policy //查看IPSEC的策略
===========================================
IPSec policy group: "hcip"
Using interface:
==========================================
Sequence number: 1
Security data flow: 3000
Tunnel local address: 12.1.1.1
Tunnel remote address: 23.1.1.3
Qos pre-classify: Disable
Proposal name:1
Inbound AH setting:
AH SPI:
AH string-key:
AH authentication hex key:
Inbound ESP setting:
ESP SPI: 4321 (0x10e1)
ESP string-key: lwljh
ESP encryption hex key:
ESP authentication hex key:
Outbound AH setting:
AH SPI:
AH string-key:
AH authentication hex key:
Outbound ESP setting:
ESP SPI: 1234 (0x4d2)
ESP string-key: lwljh
ESP encryption hex key:
ESP authentication hex key:
第四步:在接口下调用
AR1的配置
[AR1]interface g0/0/2
[AR1-GigabitEthernet0/0/2]ipsec policy hcip
[AR1-GigabitEthernet0/0/2]quit
AR2的配置
[AR3]interface g0/0/0
[AR3-GigabitEthernet0/0/0]ipsec policy hcip
[AR3-GigabitEthernet0/0/0]quit
想要华为数通配套实验拓扑和配置笔记的朋友们点赞+关注,评论区留下邮箱发给你!
四、实验调试
(1)在PC1访问PC3
在PC1上访问192.168.2.1,配置如图所示:

(2)在AR1的g0/0/2抓包
抓包截图如图12-10所示:
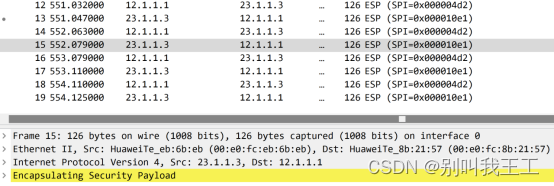
通过以上输出可以看到,数据都加密了。
想要华为数通配套实验拓扑和配置笔记的朋友们点赞+关注,评论区留下邮箱发给你!