1.ipsec VPN安全策略配置流程图
1)定义需要保护的数据流(acl)
2)配置IKE安全提议(IKE proposal)
Encryption-algorithrm加密算法
Authentication-method认证方法
Authentication-algorithrm认证算法
Integrity-algorithrm完整性算法
DH 秘钥交换算法
3)配置IKE对等体(IKE peer)
4)配置ipsec安全提议(ipsec proposal)
ESP Encryption-algorithrm 使用ESP安全协议以及加密算法
ESP Authentication-algorithrm 使用ESP安全协议以及认证算法
AH Authentication-algorithrm 使用Aha协议以及。。。
Encapsulation-mode 封装模型 tunnel(隧道) 传输
5)配置ipsec安全策略(ipsec policy)
6)应用ipsec安全策略
2.实验站点到站点(site to site)
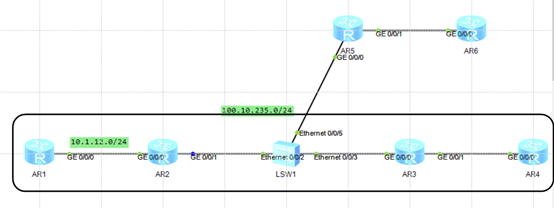
底层链路通过ospf实现站点到站点部署:
R1:
interface GigabitEthernet0/0/0
ip address 10.1.12.1 24
ospf 1
area 0
network 10.1.12.0 0.0.0.255
R2:
interface GigabitEthernet0/0/0
ip address 10.1.12.2 24
interface GigabitEthernet0/0/1
ip address 100.10.235.2 24
ospf 1
area 0
network 10.1.12.0 0.0.0.255
network 100.10.235.0 0.0.0.255
R3:
interface GigabitEthernet0/0/0
ip address 100.10.235.3 24
interface GigabitEthernet0/0/1
ip address 10.1.34.3 24
ospf 1
area 0
network 10.1.34.0 0.0.0.255
network 100.10.235.0 0.0.0.255
R4:
interface GigabitEthernet0/0/0
ip address 10.1.34.4 24
ospf 1
area 0
network 10.1.34.0 0.0.0.255
R1:
acl number 3000
rule 5 permit ip source 10.1.12.0 0.0.0.255 destination 10.1.34.0 0.0.0.255
q
ipsec proposal tran
q
ike proposal 1
q
ike peer r3 v1
pre-shared-key simple huawei
remote-address 100.10.235.3
q
ipsec policy s2s 10 isakmp
security acl 3000
ike-peer r3
proposal tran
int g0/0/1
ipsec policy s2s
R3:
acl number 3000
rule 5 permit ip source 10.1.34.0 0.0.0.255 destination 10.1.12.0 0.0.0.255
q
ipsec proposal tran
q
ike proposal 1
q
ike peer r2 v1
pre-shared-key simple huawei
remote-address 100.10.235.2
q
ipsec policy s2s 10 isakmp
security acl 3000
ike-peer r2
proposal tran
q
int g0/0/0
ipsec policy s2s
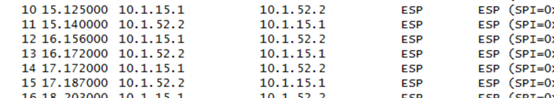
抓包分析数据加密

通过unr逆向解析实现站点到站点部署:
在上述实验基础上分别在R2,R3上做如下操作:
ospf
area 0
undo net 100.0.235.0 0.0.0.255
ipsec policy s2s 10 isakmp
route inject dynamic
在出接口重新调用ipsec policy s2s
ospf 1
import-route unr
利用防火墙实现站点到站点:
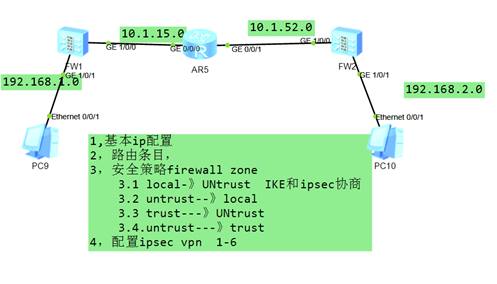
1,基本IP地址照图配置
注意:配置每个接口的区域
例如:FW1: firewall zone trust
add interface g1/0/1
firewall zone untrust
add interface g1/0/0
FW2: firewall zone trust
add interface g1/0/1
firewall zone untrust
add interface g1/0/0
2.路由条目
FW1:ip route-static 0.0.0.0 0 10.1.15.5 让防火墙将数据传递给R5进行转发
FW2:ip route-static 0.0.0.0 0 10.1.52.5 让防火墙将数据传递给R5进行转发
或者写具体的IP地址
FW1: IP route-static 192.168.2.0 24 10.1.15.5
IP route-static 10.1.52.0 24 10.1.15.5
FW2: IP route-static 192.168.1.0 24 10.1.52.5
IP route-static 10.1.15.0 24 10.1.52.5
3.FW1的安全策略
FW1:
security-policy
rule name policy1
source-zone local
destination-zone untrust
source-address 10.1.15.1 32
destination-address 10.1.52.2 32
action permit
quit
rule name policy2
source-zone untrust
destination-zone local
source-address 10.1.52.2 32
destination-address 10.1.15.1 32
action permit
rule name poilcy3
source-zone trust
destination-zone untrust
source-address 192.168.1.0 24
destination-address 192.168.2.0 24
action permit
rule name policy4
source-zone untrust
destination-zone trust
source-address 192.168.2.0 24
destination-address 192.168.1.0 24
action permit
4.ipsec vpn ---FW1上面操作
acl number 3000
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
#
ipsec proposal ip_p
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike peer fw2
pre-shared-key huawei@123
remote-address 10.1.52.2
#
ipsec policy fw2fw 10 isakmp
security acl 3000
ike-peer fw2
proposal ip_p
route inject dynamic
#
int g1/0/0
ipsec policy fw2fw
FW2:
security-policy
rule name policy1
source-zone local
destination-zone untrust
source-address 10.1.52.2 32
destination-address 10.1.15.1 32
action permit
q
rule name policy2
source-zone untrust
destination-zone local
source-address 10.1.15.1 32
destination-address 10.1.52.2 32
action permit
q
rule name policy3
source-zone trust
destination-zone untrust
source-address 192.168.2.0 24
destination-address 192.168.1.0 24
action permit
q
rule name policy4
source-zone untrust
destination-zone trust
source-address 192.168.1.0 24
destination-address 192.168.2.0 24
action permit
q
acl number 3000
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
#
ipsec proposal ip_p
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike peer fw1
pre-shared-key huawei@123
remote-address 10.1.15.1
#
ipsec policy fw2fw 10 isakmp
security acl 3000
ike-peer fw1
proposal ip_p
route inject dynamic
#
int g1/0/0
ipsec policy fw2fw
最后:测试PC之间可以ping通,抓包,公网之中可以看到ESP报文