碰到 Sqlserver 服务器 有时候重启服务器没启动(或者由于某些情况下停止服务了)
所以,弄个每天定时检查启动sqlserver代理服务
做法:使用 window任务计划 + bat
材料:Sqlserver2014 + win10 64位家庭版
1.bat :(感谢:https://blog.csdn.net/kk185800961/article/details/43816319)
@echo off
for /f "skip=3 tokens=4" %%i in ('sc query SQLSERVERAGENT') do set "zt=%%i" &goto :next
:next
if /i "%zt%"=="RUNNING" (
echo "SQL Server 代理 (MSSQLSERVER) 服务在运行。"
) else (
echo "SQL Server 代理 (MSSQLSERVER) 服务处理停止状态,准备启动……"
net start SQLSERVERAGENT
ping /n 3 127.1>nul
)
#pause>nul
之后,有个问题,执行这个,必须需要 管理员
所以,需要在 bat 前面 加上(感谢:https://zhidao.baidu.com/question/649678679924639445.html):
net session >nul 2>&1
if not "%errorLevel%" == "0" (
echo Oops: This tools must run with administrator permissions!
echo it will popup the UAC dialog, please click [Yes] to continue.
echo Set UAC = CreateObject^("Shell.Application"^) > "%temp%\getadmin.vbs"
echo UAC.ShellExecute "%~s0", "%*", "", "runas", 1 >> "%temp%\getadmin.vbs"
"%temp%\getadmin.vbs"
exit /b 2
)
所以 这个bat 的 内容为:
net session >nul 2>&1
if not "%errorLevel%" == "0" (
echo Oops: This tools must run with administrator permissions!
echo it will popup the UAC dialog, please click [Yes] to continue.
echo Set UAC = CreateObject^("Shell.Application"^) > "%temp%\getadmin.vbs"
echo UAC.ShellExecute "%~s0", "%*", "", "runas", 1 >> "%temp%\getadmin.vbs"
"%temp%\getadmin.vbs"
exit /b 2
)
@echo off
for /f "skip=3 tokens=4" %%i in ('sc query SQLSERVERAGENT') do set "zt=%%i" &goto :next
:next
if /i "%zt%"=="RUNNING" (
echo "SQL Server 代理 (MSSQLSERVER) 服务在运行。"
) else (
echo "SQL Server 代理 (MSSQLSERVER) 服务处理停止状态,准备启动……"
net start SQLSERVERAGENT
ping /n 3 127.1>nul
)
#pause>nul
之后,给要执行的文件 赋予User权限
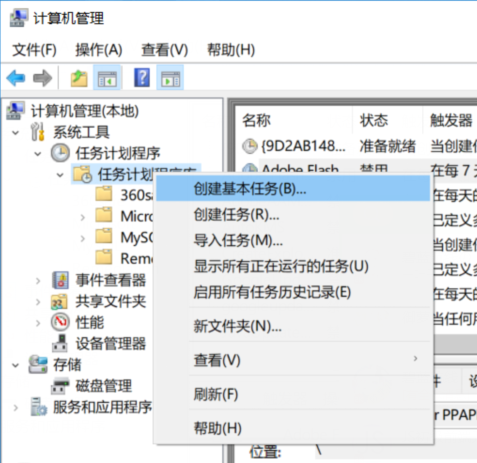
2.winow计划(感谢:https://jingyan.baidu.com/article/9989c746210d2bf649ecfe5a.html)
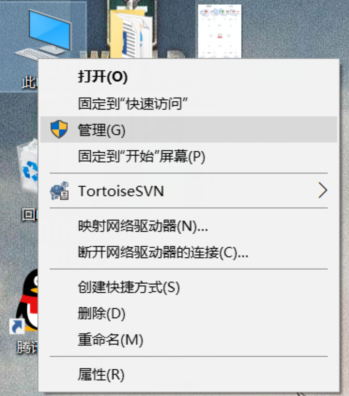
右击=》“我的电脑”=》“管理”=》“系统工具”=》“任务计划程序库”=》“创建基本任务”=》....(后续自行操作--偷懒)
参考:https://blog.csdn.net/kk185800961/article/details/43816319
https://jingyan.baidu.com/article/9989c746210d2bf649ecfe5a.html
https://zhidao.baidu.com/question/649678679924639445.html