现在的服务器(一般是堡垒机)为了保证安全,通常会采用双认证+防火墙的形式。双身份认证就是通过你所知道再加上你所能拥有的这二个要素组合到一起才能发挥作用的身份认证系统。双认证是一种采用时间同步技术的系统,采用了基于时间、事件和密钥三变量而产生的一次性密码来代替传统的静态密码。每个动态密码卡都有一个唯一的密钥,该密钥同时存放在服务器端,每次认证时动态密码卡与服务器分别根据同样的密钥,同样的随机参数(时间、事件)和同样的算法计算了认证的动态密码,从而确保密码的一致性,从而实现了用户的认证。
google-authenticator+ssh 密码方式
1.在服务上编译安装 google-authenticator
git clone https://github.com/google/google-authenticator-libpam.git
./bootstrap.sh
./configure
make
sudo make install执行./bootstrap.sh如果有报错,可能是缺少相关的库导致的,可能需要yum -y install autoconf automake libtool等
2.在/etc/pam.d/sshd的第一行添加
auth required pam_google_authenticator.so3.修改/etc/ssh/sshd_config 开启 ChallengeResponseAuthentication
ChallengeResponseAuthentication yes4.设置服务器,切换到需要启用 google-authenticator 的用户执行google-authenticator
$ google-authenticator
Do you want authentication tokens to be time-based (y/n) y
https://www.google.com//chart?chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/jolestar@xxxxx%3Fsecret%xxxxxxxx
Your new secret key is: xxxxxx
Your verification code is xxxxx
Your emergency scratch codes are:
xxxxxxxx
Do you want me to update your "/home/jolestar/.google_authenticator" file (y/n) y
# 禁止同一个token被多个人使用
Do you want to disallow multiple uses of the same authentication
token? This restricts you to one login about every 30s, but it increases
your chances to notice or even prevent man-in-the-middle attacks (y/n) y
#是否需要延长过期时间,默认是30秒,但允许提前和延后一个段,所以过期时间是1分钟30秒。
By default, tokens are good for 30 seconds and in order to compensate for
possible time-skew between the client and the server, we allow an extra
token before and after the current time. If you experience problems with poor
time synchronization, you can increase the window from its default
size of 1:30min to about 4min. Do you want to do so (y/n) n
#是否启用频次限制
If the computer that you are logging into isn't hardened against brute-force
login attempts, you can enable rate-limiting for the authentication module.
By default, this limits attackers to no more than 3 login attempts every 30s.
Do you want to enable rate-limiting (y/n) y5.重启sshd服务
期间碰到一个问题,查看/var/log/secure 发现 cannot open shared object file ,做以下链接即可:
ln -s /usr/local/lib/security/pam_google_authenticator.so /lib64/security/pam_google_authenticator.so
6.测试登录
[root@testos7 jackzou]# ssh [email protected]
Verification code:
Password:
Last login: Wed Mar 29 15:28:00 2017 from 10.21.252.85
[root@smokeping ~]# exit
configure: error: Unable to find the PAM library or the PAM header files yum
yum install pam-develgoogle-authenticator+ ssh key的方式
基本方法和ssh 密码方式差不多,/etc/pam.d/sshd 和 /etc/ssh/sshd_config 有几个地方修改下即可。
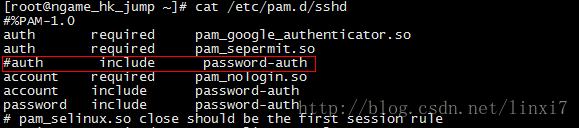
把password注释掉

RequiredAuthentications2 publickey,keyboard-interactive
PasswordAuthentication no
重启sshd即可。
官方文档 https://github.com/google/google-authenticator-libpam
参考:http://jolestar.com/two-step-ssh-with-google-authenticator/
http://www.cnblogs.com/hanyifeng/p/5516053.html