转载自:https://blog.csdn.net/yyfzy/article/details/46798965
在之前的文章“通过OpenSSL解码X509证书文件”里,讲述了如何使用OpenSSL将证书文件解码,得到证书上下文结构体X509的方法。下面我们接着讲述如何通过证书上下文结构体X509,获得想要的证书项。本文先讲述如何获取证书的基本项,后面还有文章介绍如何获取证书的扩展项。
下面的代码,都是假定已经通过解码证书文件、得到了证书上下文结构体X509。至于如何使用OpenSSL解码证书文件、得到证书上下文结构体X509,请阅读之前的文章。
首先,我们看看关于证书结构体X509定义:
-
struct x509_st
-
{
-
X509_CINF *cert_info;
-
X509_ALGOR *sig_alg;
-
ASN1_BIT_STRING *signature;
-
int valid;
-
int references;
-
char *name;
-
CRYPTO_EX_DATA ex_data;
-
/* These contain copies of various extension values */
-
long ex_pathlen;
-
long ex_pcpathlen;
-
unsigned long ex_flags;
-
unsigned long ex_kusage;
-
unsigned long ex_xkusage;
-
unsigned long ex_nscert;
-
ASN1_OCTET_STRING *skid;
-
AUTHORITY_KEYID *akid;
-
X509_POLICY_CACHE *policy_cache;
-
STACK_OF(DIST_POINT) *crldp;
-
STACK_OF(GENERAL_NAME) *altname;
-
NAME_CONSTRAINTS *nc;
-
-
STACK_OF(IPAddressFamily) *rfc3779_addr;
-
struct ASIdentifiers_st *rfc3779_asid;
-
-
-
unsigned char sha1_hash[SHA_DIGEST_LENGTH];
-
-
X509_CERT_AUX *aux;
-
} /* X509 */;
-
-
typedef struct x509_cinf_st
-
{
-
ASN1_INTEGER *version; /* [ 0 ] default of v1 */
-
ASN1_INTEGER *serialNumber;
-
X509_ALGOR *signature;
-
X509_NAME *issuer;
-
X509_VAL *validity;
-
X509_NAME *subject;
-
X509_PUBKEY *key;
-
ASN1_BIT_STRING *issuerUID; /* [ 1 ] optional in v2 */
-
ASN1_BIT_STRING *subjectUID; /* [ 2 ] optional in v2 */
-
STACK_OF(X509_EXTENSION) *extensions; /* [ 3 ] optional in v3 */
-
ASN1_ENCODING enc;
-
} X509_CINF;
一、版本号
通过解码证书文件,得到证书结构体m_pX509之后,可以通过函数X509_get_version()获取证书的版本。具体代码如下:
-
int ver = X509_get_version(m_pX509);
-
switch(ver)
-
{
-
case 0: //V1
-
//...
-
break;
-
case 1: //V2
-
//...
-
break;
-
case 2: //V3
-
//...
-
break;
-
default:
-
//Error!
-
break;
-
}
二、序列号
同样,有了m_pX509之后,调用函数X509_get_serialNumber()即可获得证书的序列号。只是该函数返回的是ASN1_INTEGER类型,需要转换后才能是我们平常看到的十六进制表示的序列号。具体实现函数如下:
-
ULONG COpenSSLCertificate::get_SN(LPSTR lptcSN, ULONG *pulLen)
-
{
-
ULONG ulRet = CERT_ERR_OK;
-
ASN1_INTEGER *asn1_i = NULL;
-
BIGNUM *bignum = NULL;
-
char *serial = NULL;
-
-
if (!m_pX509)
-
{
-
return CERT_ERR_INVILIDCALL;
-
}
-
if (!pulLen)
-
{
-
return CERT_ERR_INVALIDPARAM;
-
}
-
asn1_i = X509_get_serialNumber(m_pX509);
-
bignum = ASN1_INTEGER_to_BN(asn1_i, NULL);
-
if (bignum == NULL)
-
{
-
ulRet = CERT_ERR_FAILED;
-
goto FREE_MEMORY;
-
}
-
serial = BN_bn2hex(bignum);
-
if (serial == NULL)
-
{
-
ulRet = CERT_ERR_FAILED;
-
goto FREE_MEMORY;
-
}
-
BN_free(bignum);
-
if (!lptcSN)
-
{
-
*pulLen = strlen(serial) + 1;
-
ulRet = CERT_ERR_OK;
-
goto FREE_MEMORY;
-
}
-
if (*pulLen < strlen(serial) + 1)
-
{
-
ulRet = CERT_ERR_BUFFER_TOO_SMALL;
-
goto FREE_MEMORY;
-
}
-
strcpy_s(lptcSN, *pulLen, serial);
-
*pulLen = strlen(serial);
-
FREE_MEMORY:
-
OPENSSL_free(serial);
-
return ulRet;
-
}
三、公钥算法(证书算法)
要想获取证书公钥算法,需要先调用函数X509_get_pubkey()得到公钥属性结构体,然后通过type字段来判断公钥的算法类型。具体实现函数如下:
-
ULONG COpenSSLCertificate::get_KeyType(ULONG* pulType)
-
{
-
EVP_PKEY *pk = NULL;
-
stack_st_X509* chain = NULL;
-
X509_EXTENSION *pex = NULL;
-
-
if (!m_pX509)
-
{
-
return CERT_ERR_INVILIDCALL;
-
}
-
if (!pulType)
-
{
-
return CERT_ERR_INVALIDPARAM;
-
}
-
-
pk = X509_get_pubkey(m_pX509);
-
if (!pk)
-
{
-
return CERT_ERR_FAILED;
-
}
-
-
if (EVP_PKEY_RSA == pk->type)
-
{
-
*pulType = CERT_KEY_ALG_RSA;
-
}
-
else if (EVP_PKEY_EC == pk->type)
-
{
-
*pulType = CERT_KEY_ALG_ECC;
-
}
-
else if (EVP_PKEY_DSA == pk->type)
-
{
-
*pulType = CERT_KEY_ALG_DSA;
-
}
-
else if (EVP_PKEY_DH == pk->type)
-
{
-
*pulType = CERT_KEY_ALG_DH;
-
}
-
else
-
{
-
return CERT_KEY_ALG_UNKNOWN;
-
}
-
-
return CERT_ERR_OK;
-
}
四、证书用途
证书从用途来分,分为“签名证书”和“加密证书”两大类。“签名证书”的公钥用来验证签名,而“加密证书”的公钥则用来加密数据。我们可以通过调用X509中的ex_kusage字段来判断证书的用途,具体函数实现如下:
-
ULONG COpenSSLCertificate::get_KeyUsage(ULONG* lpUsage)
-
{
-
ULONG lKeyUsage = 0;
-
-
if (!m_pX509)
-
{
-
return CERT_ERR_INVILIDCALL;
-
}
-
if (!lpUsage)
-
{
-
return CERT_ERR_INVALIDPARAM;
-
}
-
-
*lpUsage = CERT_USAGE_UNKNOWN;
-
-
//X509_check_ca() MUST be called!
-
X509_check_ca(m_pX509);
-
lKeyUsage = m_pX509->ex_kusage;
-
if ((lKeyUsage & KU_DATA_ENCIPHERMENT) == KU_DATA_ENCIPHERMENT)
-
{
-
*lpUsage = CERT_USAGE_EXCH;<span style= "white-space:pre"> </span> //加密证书
-
}
-
else if ((lKeyUsage & KU_DIGITAL_SIGNATURE) == KU_DIGITAL_SIGNATURE)
-
{
-
*lpUsage = CERT_USAGE_SIGN;<span style= "white-space:pre"> </span> //签名证书
-
}
-
-
return CERT_ERR_OK;
-
}
五、签名算法
证书的签名算法,是指证书用来签名时使用的算法(包含HASH算法)。签名算法用结构体X509中sig_alg字段来表示,可以通过sig_alg的子字段algorithm返回签名算法对象,从而得到签名算法的Oid。首先,签名算法的Oid常见得定义如下:
-
/* Certificate siganture alg */
-
-
-
-
-
-
获取签名算法Oid的具体实现函数如下:
-
ULONG COpenSSLCertificate::get_SignatureAlgOid(LPSTR lpscOid, ULONG *pulLen)
-
{
-
char oid[ 128] = { 0};
-
ASN1_OBJECT* salg = NULL;
-
-
if (!m_pX509)
-
{
-
return CERT_ERR_INVILIDCALL;
-
}
-
if (!pulLen)
-
{
-
return CERT_ERR_INVALIDPARAM;
-
}
-
-
salg = m_pX509->sig_alg->algorithm;
-
OBJ_obj2txt(oid, 128, salg, 1);
-
if (!lpscOid)
-
{
-
*pulLen = strlen(oid) + 1;
-
return CERT_ERR_OK;
-
}
-
if (*pulLen < strlen(oid) + 1)
-
{
-
return CERT_ERR_BUFFER_TOO_SMALL;
-
}
-
-
strcpy_s(lpscOid, *pulLen, oid);
-
*pulLen = strlen(oid) + 1;
-
return CERT_ERR_OK;
-
}
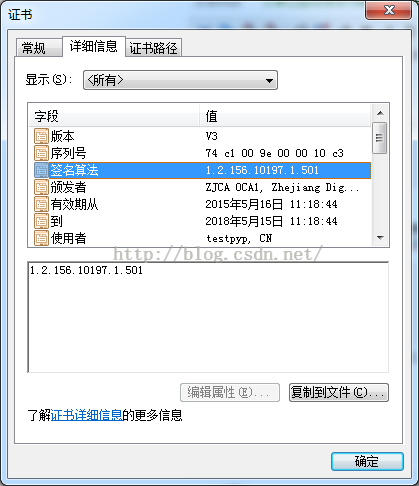
六、颁发者
关于颁发者,我们可以通过调用函数X509_get_issuer_name()获取属性。不过该函数返回的是X509_NAME类型,需要调用函数X509_NAME_get_text_by_NID()将其转化为ASCII字符形式。具体通过下面函数实现:
-
ULONG COpenSSLCertificate::get_Issuer(LPSTR lpValue, ULONG *pulLen)
-
{
-
int nNameLen = 512;
-
CHAR csCommonName[ 512] = { 0};
-
X509_NAME *pCommonName = NULL;
-
-
if (!m_pX509)
-
{
-
return CERT_ERR_INVILIDCALL;
-
}
-
if (!pulLen)
-
{
-
return CERT_ERR_INVALIDPARAM;
-
}
-
-
pCommonName = X509_get_issuer_name(m_pX509);
-
if (!pCommonName)
-
{
-
return CERT_ERR_FAILED;
-
}
-
nNameLen = X509_NAME_get_text_by_NID(pCommonName, NID_commonName, csCommonName, nNameLen);
-
if ( -1 == nNameLen)
-
{
-
return CERT_ERR_FAILED;
-
};
-
if (!lpValue)
-
{
-
*pulLen = nNameLen + 1;
-
return CERT_ERR_OK;
-
}
-
if (*pulLen < (ULONG)nNameLen + 1)
-
{
-
return CERT_ERR_BUFFER_TOO_SMALL;
-
}
-
-
strcpy_s(lpValue, *pulLen, csCommonName);
-
*pulLen = nNameLen;
-
return CERT_ERR_OK;
-
}
七、使用者
关于证书使用者,我们可以通过调用函数X509_get_subject_name)获取属性。同样,该函数返回的是X509_NAME类型,需要调用函数X509_NAME_get_text_by_NID()将其转化为ASCII字符形式。具体通过下面函数实现:
-
ULONG COpenSSLCertificate::get_SubjectName(LPSTR lpValue, ULONG *pulLen)
-
{
-
int iLen = 0;
-
int iSubNameLen = 0;
-
CHAR csSubName[ 1024] = { 0};
-
CHAR csBuf[ 256] = { 0};
-
X509_NAME *pSubName = NULL;
-
-
if (!m_pX509)
-
{
-
return CERT_ERR_INVILIDCALL;
-
}
-
if (!pulLen)
-
{
-
return CERT_ERR_INVALIDPARAM;
-
}
-
-
pSubName = X509_get_subject_name(m_pX509);
-
if (!pSubName)
-
{
-
return CERT_ERR_FAILED;
-
}
-
-
ZeroMemory(csBuf, 256);
-
iLen = X509_NAME_get_text_by_NID(pSubName, NID_countryName, csBuf, 256);
-
if (iLen > 0)
-
{
-
strcat_s(csSubName, 1024, "C=");
-
strcat_s(csSubName, 1024, csBuf);
-
strcat_s(csSubName, 1024, ", ");
-
}
-
-
ZeroMemory(csBuf, 256);
-
iLen = X509_NAME_get_text_by_NID(pSubName, NID_organizationName, csBuf, 256);
-
if (iLen > 0)
-
{
-
strcat_s(csSubName, 1024, "O=");
-
strcat_s(csSubName, 1024, csBuf);
-
strcat_s(csSubName, 1024, ", ");
-
}
-
-
ZeroMemory(csBuf, 256);
-
iLen = X509_NAME_get_text_by_NID(pSubName, NID_organizationalUnitName, csBuf, 256);
-
if (iLen > 0)
-
{
-
strcat_s(csSubName, 1024, "OU=");
-
strcat_s(csSubName, 1024, csBuf);
-
strcat_s(csSubName, 1024, ", ");
-
}
-
-
ZeroMemory(csBuf, 256);
-
iLen = X509_NAME_get_text_by_NID(pSubName, NID_commonName, csBuf, 256);
-
if (iLen > 0)
-
{
-
strcat_s(csSubName, 1024, "CN=");
-
strcat_s(csSubName, 1024, csBuf);
-
}
-
-
if (!lpValue)
-
{
-
*pulLen = strlen(csSubName) + 1;
-
return CERT_ERR_OK;
-
}
-
if (*pulLen < strlen(csSubName) + 1)
-
{
-
return CERT_ERR_BUFFER_TOO_SMALL;
-
}
-
-
strcpy_s(lpValue, *pulLen, csSubName);
-
*pulLen = strlen(csSubName);
-
return CERT_ERR_OK;
-
}
八、有效期限
要获取证书的有效期属性,需要通过调用函数X509_get_notBefore()和X509_get_notAfter()来实现。而且这两个函数返回的时间是time_t类型,需要转化为SYSTEMTIME类型。具体实现函数如下:
-
ULONG COpenSSLCertificate::get_ValidDate(SYSTEMTIME *ptmStart, SYSTEMTIME *ptmEnd)
-
{
-
int err = 0;
-
ASN1_TIME *start = NULL;
-
ASN1_TIME *end = NULL;
-
time_t ttStart = { 0};
-
time_t ttEnd = { 0};
-
LONGLONG nLLStart = 0;
-
LONGLONG nLLEnd = 0;
-
FILETIME ftStart = { 0};
-
FILETIME ftEnd = { 0};
-
-
if (!m_pX509)
-
{
-
return CERT_ERR_INVALIDPARAM;
-
}
-
-
start = X509_get_notBefore(m_pX509);
-
end = X509_get_notAfter(m_pX509);
-
-
ttStart = ASN1_TIME_get(start, &err);
-
ttEnd = ASN1_TIME_get(end, &err);
-
nLLStart = Int32x32To64(ttStart, 10000000) + 116444736000000000;
-
nLLEnd = Int32x32To64(ttEnd, 10000000) + 116444736000000000;
-
-
ftStart.dwLowDateTime = (DWORD)nLLStart;
-
ftStart.dwHighDateTime = (DWORD)(nLLStart >> 32);
-
ftEnd.dwLowDateTime = (DWORD)nLLEnd;
-
ftEnd.dwHighDateTime = (DWORD)(nLLEnd >> 32);
-
-
FileTimeToSystemTime(&ftStart, ptmStart);
-
FileTimeToSystemTime(&ftEnd, ptmEnd);
-
-
return 0;
-
}
至此,X509证书的基本项通过OpenSLL均已解析完毕!如需获取证书的扩展项或者公钥等数据,请关注后续博文。