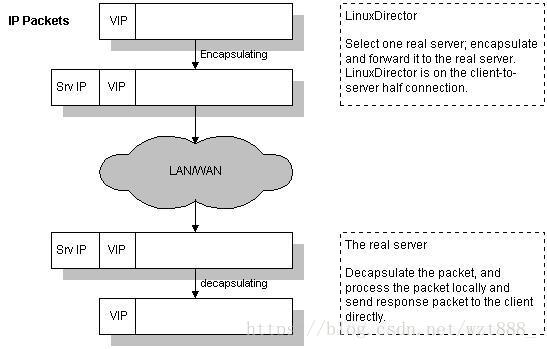
有关lvs的相关知识可以去查看之前写的DR模型
VS/TUN的体系结构如图所示,各个服务器将VIP地址配置在自己的IP隧道设备上。
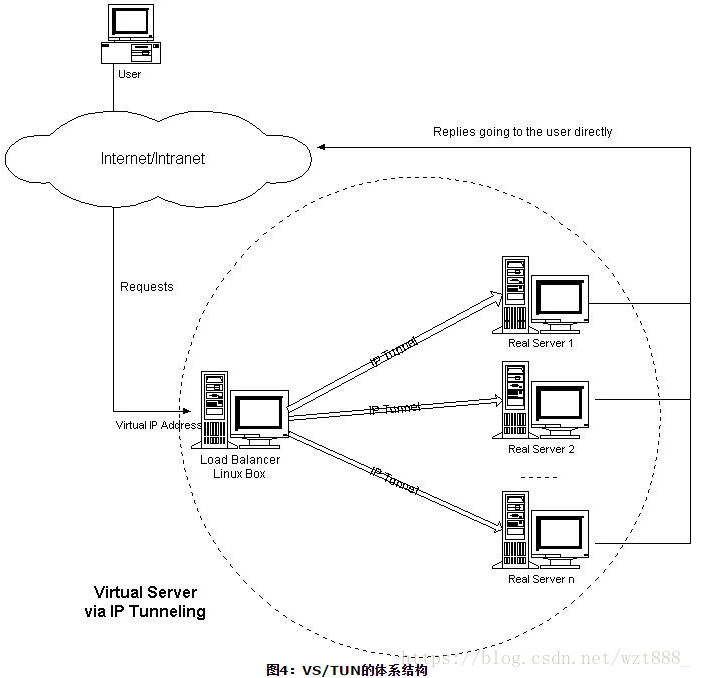
VS/TUN模式的工作原理:
(1)IP隧道技术又称为IP封装技术,它可以将带有源和目标IP地址的数据报文使用新的源和目标IP进行第二次封装,这样这个报文就可以发送到一个指定的目标主机上;
(2)VS/TUN模式下,调度器和后端服务器组之间使用IP隧道技术。当客户端发送的请求(CIP-->VIP)被director接收后,director修改该报文,加上IP隧道两端的IP地址作为新的源和目标地址,并将请求转发给后端被选中的一个目标;
(3)当后端服务器接收到报文后,首先解封报文得到原有的CIP-->VIP,该后端服务器发现自身的tun接口上配置了VIP,因此接受该数据包。
(4)当请求处理完成后,结果将不会重新交给director,而是直接返回给客户端;在后端服务器返回给客户端数据包时,由于使用的是普通网卡接口,根据一般的路由条目,源IP地址将是该网卡接口上的地址,例如是RIP。因此,要让响应数据包的源IP为VIP,必须添加一条特殊的路由条目,明确指定该路由的源地址是VIP。
采用VS/TUN模式时的基本属性和要求:
(1)Real Server的RIP和director的DIP不用处于同一物理网络中,且RIP必须可以和公网通信。也就是说集群节点可以跨互联网实现。
(2)real server的 tun接口上需要配置VIP地址,以便接收director转发过来的数据包,以及作为响应报文的源IP。
(3)director给realserver时需要借助隧道,隧道外层的IP头部的源IP是DIP,目标IP是RIP。而realsever响应给客户端的IP头部是根据隧道内层的IP头分析得到的,源IP是VIP,目标IP是CIP。这样客户端就无法区分这个VIP到底是director的还是服务器组中的。
(4)需要添加一条特殊的路由条目,使得后端服务器返回响应给客户端时的源IP为VIP。
(5)director只处理入站请求,响应请求由realserver完成。
一般来说,VS/TUN模式会用来负载调度缓存服务器组,这些缓存服务器一般放置在不同网络环境,可以就近返回数据给客户端。在请求对象不能在Cache服务器本地命中的情况下,Cache服务器要向源服务器发请求,将结果取回,最后将结果返回给客户。
#在server2上:
[root@server2 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 52:54:00:d3:bc:cf brd ff:ff:ff:ff:ff:ff
inet 172.25.44.2/24 brd 172.25.44.255 scope global eth0
inet6 fe80::5054:ff:fed3:bccf/64 scope link
valid_lft forever preferred_lft forever
[root@server2 ~]# modprobe ipip #自动加载ipip隧道模块
[root@server2 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 52:54:00:d3:bc:cf brd ff:ff:ff:ff:ff:ff
inet 172.25.44.2/24 brd 172.25.44.255 scope global eth0
inet6 fe80::5054:ff:fed3:bccf/64 scope link
valid_lft forever preferred_lft forever
3: tunl0: <NOARP> mtu 1480 qdisc noop state DOWN #显示出来隧道接口
link/ipip 0.0.0.0 brd 0.0.0.0
[root@server2 ~]# ip addr add 172.25.44.100/24 dev tunl0
[root@server2 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 52:54:00:d3:bc:cf brd ff:ff:ff:ff:ff:ff
inet 172.25.44.2/24 brd 172.25.44.255 scope global eth0
inet6 fe80::5054:ff:fed3:bccf/64 scope link
valid_lft forever preferred_lft forever
3: tunl0: <NOARP> mtu 1480 qdisc noop state DOWN
link/ipip 0.0.0.0 brd 0.0.0.0
inet 172.25.44.100/24 scope global tunl0
[root@server2 ~]# ip link set up tunl0
[root@server2 ~]# ip addr add 172.25.44.100/24 dev eth0
[root@server2 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 52:54:00:d3:bc:cf brd ff:ff:ff:ff:ff:ff
inet 172.25.44.2/24 brd 172.25.44.255 scope global eth0
inet 172.25.44.100/24 scope global secondary eth0 #VIP添加成功
inet6 fe80::5054:ff:fed3:bccf/64 scope link
valid_lft forever preferred_lft forever
3: tunl0: <NOARP> mtu 1480 qdisc noop state UNKNOWN #链接成功
link/ipip 0.0.0.0 brd 0.0.0.0
inet 172.25.44.100/24 scope global tunl0
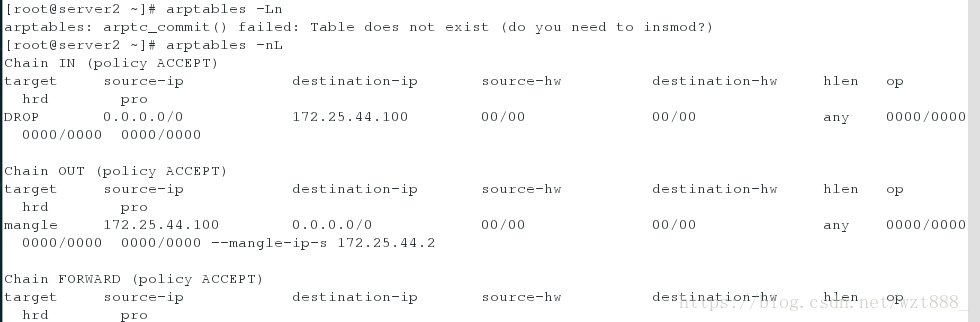
[root@server2 ~]# arptables -nL #查看arp策略
Chain IN (policy ACCEPT)
target source-ip destination-ip source-hw destination-hw hlen op hrd pro
Chain OUT (policy ACCEPT)
target source-ip destination-ip source-hw destination-hw hlen op hrd pro
Chain FORWARD (policy ACCEPT)
target source-ip destination-ip source-hw destination-hw hlen op hrd pro
[root@server2 ~]# arptables -A IN -d 172.25.44.100 -j DROP #关闭arp响应
[root@server2 ~]# arptables -A OUT -s 172.25.44.100 -j mangle --mangle-ip-s 172.25.44.2
[root@server2 ~]# /etc/init.d/arptables_jf save
Saving current rules to /etc/sysconfig/arptables: [ OK ]
[root@server2 ~]# arptables -nL
Chain IN (policy ACCEPT)
target source-ip destination-ip source-hw destination-hw hlen op hrd pro
DROP 0.0.0.0/0 172.25.44.100 00/00 00/00 any 0000/0000 0000/0000 0000/0000 #策略添加成功
Chain OUT (policy ACCEPT)
target source-ip destination-ip source-hw destination-hw hlen op hrd pro
mangle 172.25.44.100 0.0.0.0/0 00/00 00/00 any 0000/0000 0000/0000 0000/0000 --mangle-ip-s 172.25.44.2
Chain FORWARD (policy ACCEPT)
target source-ip destination-ip source-hw destination-hw hlen op hrd pro
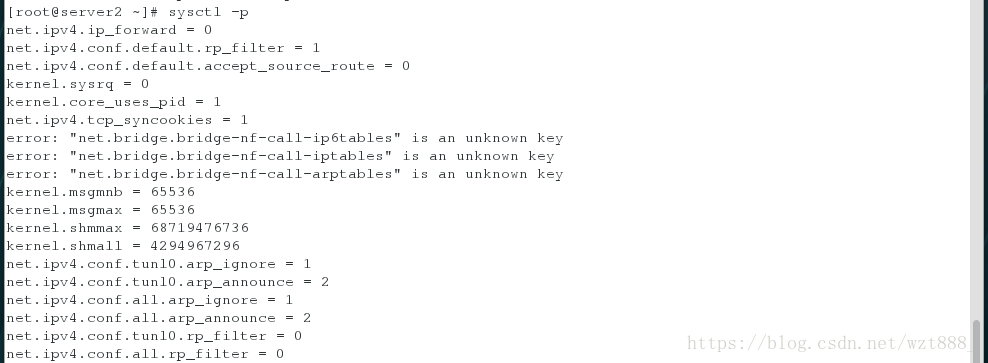
[root@server2 ~]# vim /etc/sysctl.conf # 关闭ARP转发,永久生效
#添加以下内容
kernel.shmall = 4294967296
net.ipv4.conf.tunl0.arp_ignore = 1
net.ipv4.conf.tunl0.arp_announce = 2
net.ipv4.conf.all.arg_ignore = 1
net.ipv4.conf.all_announce =2
net.ipv4.conf.tunl0.rp_filter = 0
net.ipv4.conf.all.rp_filter = 0
[root@server2 ~]# sysctl -p #加载文件内容
net.ipv4.ip_forward = 0
net.ipv4.conf.default.rp_filter = 1
net.ipv4.conf.default.accept_source_route = 0
kernel.sysrq = 0
kernel.core_uses_pid = 1
net.ipv4.tcp_syncookies = 1
error: "net.bridge.bridge-nf-call-ip6tables" is an unknown key
error: "net.bridge.bridge-nf-call-iptables" is an unknown key
error: "net.bridge.bridge-nf-call-arptables" is an unknown key
kernel.msgmnb = 65536
kernel.msgmax = 65536
kernel.shmmax = 68719476736
kernel.shmall = 4294967296
net.ipv4.conf.tunl0.arp_ignore = 1
net.ipv4.conf.tunl0.arp_announce = 2
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.all.arp_announce = 2
net.ipv4.conf.tunl0.rp_filter = 0
net.ipv4.conf.all.rp_filter = 0
[root@server2 ~]# echo "0" > "/proc/sys/net/ipv4/ip_forward" #返回值默认是0,此功能就是关闭的
[root@server2 ~]#/etc/init.d/httpd start
#在server3上和server2进行相同的操作
#在server5(调度器)上:
##yum源的配置和之前NAT模式一样
[root@server5 ~]# modprobe ipip
[root@server5 ~]# ip addr add 172.25.44.100/24 dev eth0
[root@server5 network-scripts]# ip addr add 172.25.44.100/24 dev tunl0
[root@server5 network-scripts]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 52:54:00:eb:57:75 brd ff:ff:ff:ff:ff:ff
inet 172.25.44.3/24 brd 172.25.44.255 scope global eth0
inet 172.25.44.100/24 scope global secondary eth0
inet6 fe80::5054:ff:feeb:5775/64 scope link
valid_lft forever preferred_lft forever
3: tunl0: <NOARP> mtu 1480 qdisc noop state DOWN
link/ipip 0.0.0.0 brd 0.0.0.0
inet 172.25.44.100/24 scope global tunl0
[root@server5 network-scripts]# yum install ipvsadm-1.26-2.el6.x86_64 -y
[root@server5 network-scripts]# ipvsadm -l
IP Virtual Server version 1.2.1 (size=4194304)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
[root@server5 network-scripts]# ipvsadm -A -t 172.25.44.100:80 -s rr
[root@server5 network-scripts]# ipvsadm -a -t 172.25.44.100:80 -r 172.25.44.2:80 -i
[root@server5 network-scripts]# ipvsadm -a -t 172.25.44.100:80 -r 172.25.44.3:80 -i
[root@server5 network-scripts]# ipvsadm -l #策略添加成功
IP Virtual Server version 1.2.1 (size=4194304)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 172.25.44.100:http rr
-> server2:http Tunnel 1 0 0
-> server3:http Tunnel 1 0 0
#在真机上测试:
[root@foundation44 ~]# curl 172.25.44.100
bbs.westos.org - server3
[root@foundation44 ~]# curl 172.25.44.100
www.westos.org - server2
[root@foundation44 ~]# curl 172.25.44.100
bbs.westos.org - server3
[root@foundation44 ~]# curl 172.25.44.100
www.westos.org - server2