版权声明:本文为博主原创文章,未经博主允许不得转载。 https://blog.csdn.net/BlueEffie/article/details/53224773
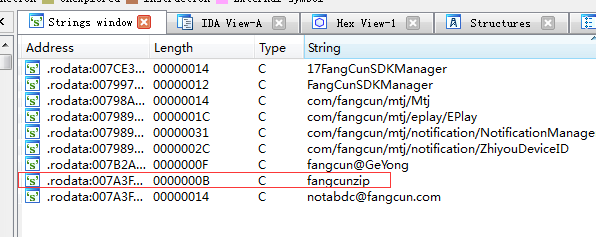
0x00 先用WinHex看看魔天记的资源文件
我们发现有些资源的文件头前面都加了“fangcunzip” 姑且理解为加密的标识
0x01 在IDA中反汇编\lib\armeabi\libgame.so文件,分析一下,搜索一下字符串“fangcunzip”
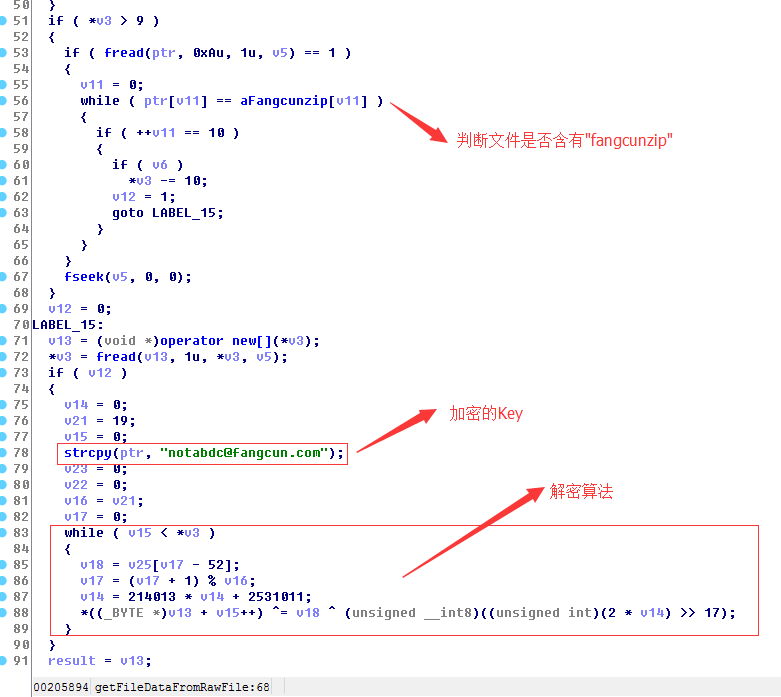
双击进入“fangcunzip”所对应的地址,按F5看看伪代码
经过上面的分析后,发现其实解密很简单 就是异或+右移运算
0x02 分析完 那就直接上代码解析资源(C# 代码片段)
private void ReadFile(FileInfo f)
{
FileStream inStream = new FileStream(f.FullName, FileMode.Open, FileAccess.ReadWrite);
byte[] bytes = new byte[inStream.Length];
inStream.Read(bytes, 0, bytes.Length);
inStream.Close();
if (Encoding.Default.GetString(bytes).Contains("fangcunzip"))
{
byte[] resBytes = new byte[bytes.Length - 0xA];
Array.Copy(bytes, 0xA, resBytes, 0, resBytes.Length);
byte[] decryptBytes = DecryptData(resBytes);
OutResFile(decryptBytes, f.FullName);
}
}
private byte[] DecryptData(Byte[] bytes)
{
string key = "[email protected]";
byte[] keyBytes = Encoding.Default.GetBytes(key);
int shrKey = 0;
for (int i = 0; i < bytes.Length; i++)
{
byte xorKey = keyBytes[i % keyBytes.Length];
shrKey = 0x343FD * shrKey + 0x269EC3;
bytes[i] = (byte)(bytes[i] ^ (xorKey ^ ((2 * shrKey) >> 17)));
}
return bytes;
}
资源提取源码
链接:http://pan.baidu.com/s/1nuKidHR 密码:6ic3