1.访问控制
- 在location段修改以下配置
location / {
allow 192.168.225.129/32; //允许访问
deny 192.168.225.130/32; //拒绝访问
root html;
index index.html index.htm;
}
验证
//在192.168.225.129上访问192.168.225.128
[root@localhost ~]# curl 192.168.225.128
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
body {
width: 35em;
margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif;
}
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
//再到192.168.225.130上访问192.168.225.128
[root@localhost ~]# curl 192.168.225.128
<html>
<head><title>403 Forbidden</title></head>
<body bgcolor="white">
<center><h1>403 Forbidden</h1></center>
<hr><center>nginx/1.14.0</center>
</body>
</html>
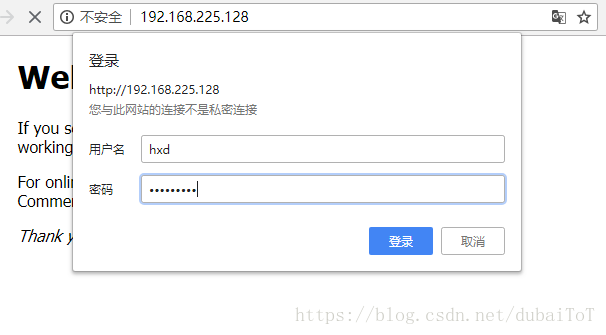
- 安装htpasswd命令,并生成用户和密码
[root@hxdserver ~]# yum -y install httpd-tools
[root@hxdserver ~]# touch /usr/local/nginx/pass
[root@hxdserver ~]# htpasswd -c -m /usr/local/nginx/pass hxd
New password:
Re-type new password:
Adding password for user hxd
[root@hxdserver ~]# cat /usr/local/nginx/pass
hxd:$apr1$Hi6M8UsP$e/SxFgGkizk0te.Xcfxvl.
[root@hxdserver ~]# vim /usr/local/nginx/conf/nginx.conf
//修改如下配置
location / {
auth_basic "hello";//欢迎信息
auth_basic_user_file "/usr/local/nginx/pass"; //放置用户密码的文件
root html;
index index.html index.htm;
}
[root@hxdserver ~]# nginx -t
nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful
[root@hxdserver ~]# nginx -s reload
验证
- 配置证书
- 192.168.225.129(CA)
生成一对密钥
[root@localhost CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus //生成密钥
...............................................+++
......................................................................................................................+++
e is 65537 (0x10001)
[root@localhost CA]# openssl rsa -in private/cakey.pem -pubout //提取公钥
writing RSA key
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAyGJz+7lnD3VAXUSRlRzb
c7RhQ3nUu5aSp2un4hpxzvuNmRNb+bCS+vB3x8Lp7ovTbCWbGh491sQ1SP1Dm/8w
3LLRJOcqyh8GMI+Z1XXQaEkJqNpf2rtHcahVSl28x/XYu/NEbVTIHQKDkB8qxZ36
QREfErnRwgp0CFQji9b5vpZuxv2X4e1C6NxHlDO5o38OflGAhgeAWw66gy7wMiRn
Tg2bURcEIIpx5AouYCjuHYHtRgx1eHHjc7tElhv067vp/PLnblv3z6Jl9vF7awtk
sGO3NNvIkKSG80hkKuoq+USbiAgaI7koZgCLAOznflTq8RxiBQQIwNlDbQsgdh82
PQIDAQAB
-----END PUBLIC KEY-----
[root@localhost CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 7
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN //国家
State or Province Name (full name) []:HB //省
Locality Name (eg, city) [Default City]:WH //市
Organization Name (eg, company) [Default Company Ltd]:www.hxd.com //公司域名
Organizational Unit Name (eg, section) []:www.hxd.com //公司域名
Common Name (eg, your name or your server's hostname) []:www.hxd.com
Email Address []:[email protected] //邮件
- 192.168.225.128(nginx服务器)
[root@hxdserver ~]# cd /usr/local/nginx/
[root@hxdserver nginx]# mkdir ssl
[root@hxdserver nginx]# cd ssl
[root@hxdserver ssl]# (umask 077;openssl genrsa -out nginx.key 2048)
Generating RSA private key, 2048 bit long modulus
.............................................+++
...........................+++
e is 65537 (0x10001)
[root@hxdserver ssl]# openssl req -new -key nginx.key -days 7 -out nginx.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:www.hxd.com
Organizational Unit Name (eg, section) []:www.hxd.com
Common Name (eg, your name or your server's hostname) []:nginx
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:nginx
[root@hxdserver ssl]# scp nginx.csr [email protected]:/root
The authenticity of host '192.168.225.129 (192.168.225.129)' can't be established.
ECDSA key fingerprint is SHA256:Y7vZS5XBplS7QSCZD8jVqIOx/EOr2hATD+05juJnWyc.
ECDSA key fingerprint is MD5:f2:5b:29:bc:55:53:95:ea:81:c7:4c:36:80:e3:5d:99.
Are you sure you want to continue connecting (yes/no)? 1^Hyes
Please type 'yes' or 'no': yes
Warning: Permanently added '192.168.225.129' (ECDSA) to the list of known hosts.
[email protected]'s password: //将证书发送给CA签署
nginx.csr 100% 1090 1.3MB/s 00:00
- 192.168.225.129
[root@localhost CA]# openssl x509 -text -in cacert.pem //读取公钥的内容
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
8c:3b:e9:6d:58:0a:71:b2
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=HB, L=WH, O=www.hxd.com, OU=www.hxd.com, CN=www.hxd.com/[email protected]
Validity
Not Before: Oct 25 03:06:56 2018 GMT
Not After : Nov 1 03:06:56 2018 GMT
Subject: C=CN, ST=HB, L=WH, O=www.hxd.com, OU=www.hxd.com, CN=www.hxd.com/[email protected]
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:c8:62:73:fb:b9:67:0f:75:40:5d:44:91:95:1c:
db:73:b4:61:43:79:d4:bb:96:92:a7:6b:a7:e2:1a:
71:ce:fb:8d:99:13:5b:f9:b0:92:fa:f0:77:c7:c2:
e9:ee:8b:d3:6c:25:9b:1a:1e:3d:d6:c4:35:48:fd:
43:9b:ff:30:dc:b2:d1:24:e7:2a:ca:1f:06:30:8f:
99:d5:75:d0:68:49:09:a8:da:5f:da:bb:47:71:a8:
55:4a:5d:bc:c7:f5:d8:bb:f3:44:6d:54:c8:1d:02:
83:90:1f:2a:c5:9d:fa:41:11:1f:12:b9:d1:c2:0a:
74:08:54:23:8b:d6:f9:be:96:6e:c6:fd:97:e1:ed:
42:e8:dc:47:94:33:b9:a3:7f:0e:7e:51:80:86:07:
80:5b:0e:ba:83:2e:f0:32:24:67:4e:0d:9b:51:17:
04:20:8a:71:e4:0a:2e:60:28:ee:1d:81:ed:46:0c:
75:78:71:e3:73:bb:44:96:1b:f4:eb:bb:e9:fc:f2:
e7:6e:5b:f7:cf:a2:65:f6:f1:7b:6b:0b:64:b0:63:
b7:34:db:c8:90:a4:86:f3:48:64:2a:ea:2a:f9:44:
9b:88:08:1a:23:b9:28:66:00:8b:00:ec:e7:7e:54:
ea:f1:1c:62:05:04:08:c0:d9:43:6d:0b:20:76:1f:
36:3d
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
CD:94:FD:1D:0D:AA:38:BC:F0:DD:5C:9C:AD:C6:42:DE:13:F0:33:B9
X509v3 Authority Key Identifier:
keyid:CD:94:FD:1D:0D:AA:38:BC:F0:DD:5C:9C:AD:C6:42:DE:13:F0:33:B9
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
37:62:0c:06:d6:97:ac:fc:47:6d:b0:38:d3:aa:14:7a:94:77:
b2:ff:e6:1a:21:9c:ed:89:db:cd:bd:c6:e1:cd:46:fd:ff:16:
8d:ff:46:27:a1:12:8b:03:81:90:52:38:9c:78:3c:d2:96:a7:
15:b6:c8:bd:ca:cb:ae:75:10:8c:ab:3a:fe:a6:94:31:47:f3:
84:d3:8c:0f:be:92:55:1d:1b:b2:e8:7c:68:3f:dc:80:5f:3b:
b5:7e:89:06:b1:ba:ea:8e:0e:a4:e8:48:63:7a:30:c9:27:5f:
5c:35:64:18:69:e0:a6:8d:f7:1a:ec:44:91:c0:65:3e:de:c4:
aa:48:cd:b0:9a:f6:ce:9d:d6:21:74:7d:9c:6d:59:43:a4:65:
8b:a3:f7:e2:dc:fe:30:d2:ee:8a:a6:24:34:14:cd:34:93:55:
a5:27:35:63:48:9e:c4:af:48:7d:c4:8e:79:10:59:11:24:ac:
02:68:47:c6:21:88:91:c9:07:d4:71:08:d7:97:21:5b:b6:4f:
94:ac:16:16:d2:10:b5:88:aa:d5:d6:50:20:4c:95:4a:7e:2b:
13:0e:37:fa:af:8e:50:03:0d:86:1d:60:12:af:ba:3f:01:81:
30:f9:6d:bb:12:79:e6:3a:79:7e:37:e4:bf:75:30:d7:e9:5f:
86:a1:98:9a
-----BEGIN CERTIFICATE-----
MIID1zCCAr+gAwIBAgIJAIw76W1YCnGyMA0GCSqGSIb3DQEBCwUAMIGBMQswCQYD
VQQGEwJDTjELMAkGA1UECAwCSEIxCzAJBgNVBAcMAldIMRQwEgYDVQQKDAt3d3cu
aHhkLmNvbTEUMBIGA1UECwwLd3d3Lmh4ZC5jb20xFDASBgNVBAMMC3d3dy5oeGQu
Y29tMRYwFAYJKoZIhvcNAQkBFgdhQGIuY29tMB4XDTE4MTAyNTAzMDY1NloXDTE4
MTEwMTAzMDY1NlowgYExCzAJBgNVBAYTAkNOMQswCQYDVQQIDAJIQjELMAkGA1UE
BwwCV0gxFDASBgNVBAoMC3d3dy5oeGQuY29tMRQwEgYDVQQLDAt3d3cuaHhkLmNv
bTEUMBIGA1UEAwwLd3d3Lmh4ZC5jb20xFjAUBgkqhkiG9w0BCQEWB2FAYi5jb20w
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDIYnP7uWcPdUBdRJGVHNtz
tGFDedS7lpKna6fiGnHO+42ZE1v5sJL68HfHwunui9NsJZsaHj3WxDVI/UOb/zDc
stEk5yrKHwYwj5nVddBoSQmo2l/au0dxqFVKXbzH9di780RtVMgdAoOQHyrFnfpB
ER8SudHCCnQIVCOL1vm+lm7G/Zfh7ULo3EeUM7mjfw5+UYCGB4BbDrqDLvAyJGdO
DZtRFwQginHkCi5gKO4dge1GDHV4ceNzu0SWG/Tru+n88uduW/fPomX28XtrC2Sw
Y7c028iQpIbzSGQq6ir5RJuICBojuShmAIsA7Od+VOrxHGIFBAjA2UNtCyB2HzY9
AgMBAAGjUDBOMB0GA1UdDgQWBBTNlP0dDao4vPDdXJytxkLeE/AzuTAfBgNVHSME
GDAWgBTNlP0dDao4vPDdXJytxkLeE/AzuTAMBgNVHRMEBTADAQH/MA0GCSqGSIb3
DQEBCwUAA4IBAQA3YgwG1pes/EdtsDjTqhR6lHey/+YaIZztidvNvcbhzUb9/xaN
/0YnoRKLA4GQUjiceDzSlqcVtsi9ysuudRCMqzr+ppQxR/OE04wPvpJVHRuy6Hxo
P9yAXzu1fokGsbrqjg6k6EhjejDJJ19cNWQYaeCmjfca7ESRwGU+3sSqSM2wmvbO
ndYhdH2cbVlDpGWLo/fi3P4w0u6KpiQ0FM00k1WlJzVjSJ7Er0h9xI55EFkRJKwC
aEfGIYiRyQfUcQjXlyFbtk+UrBYW0hC1iKrV1lAgTJVKfisTDjf6r45QAw2GHWAS
r7o/AYEw+W27EnnmOnl+N+S/dTDX6V+GoZia
-----END CERTIFICATE-----
[root@localhost CA]# touch index.txt && echo 01 > serial
[root@localhost CA]# openssl ca -in /root/nginx.csr -out nginx.crt -days 7 //生成7天的自签署证书
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Oct 25 03:10:18 2018 GMT
Not After : Nov 1 03:10:18 2018 GMT
Subject:
countryName = CN
stateOrProvinceName = HB
organizationName = www.hxd.com
organizationalUnitName = www.hxd.com
commonName = nginx
emailAddress = [email protected]
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
BC:B4:42:0C:3B:3A:01:C0:2D:F1:64:24:1B:F1:A5:B2:55:F4:8C:20
X509v3 Authority Key Identifier:
keyid:CD:94:FD:1D:0D:AA:38:BC:F0:DD:5C:9C:AD:C6:42:DE:13:F0:33:B9
Certificate is to be certified until Nov 1 03:10:18 2018 GMT (7 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@localhost CA]# scp nginx.crt [email protected]:/usr/local/nginx/ssl
The authenticity of host '192.168.225.128 (192.168.225.128)' can't be established.
ECDSA key fingerprint is SHA256:Pdsa5HfH0daA6UHMZn03MdcdupayO3PaI73KCb4Aqsc.
ECDSA key fingerprint is MD5:62:b6:4c:22:3b:3c:c6:de:36:71:11:03:aa:20:ea:a4.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.225.128' (ECDSA) to the list of known hosts.
[email protected]'s password: //将签署好的证书再发送给nginx服务器
nginx.crt 100% 4565 529.3KB/s 00:00
- 192.168.225.128(nginx服务器)
[root@hxdserver ssl]#
[root@hxdserver ssl]# ls
nginx.crt nginx.csr nginx.key
[root@hxdserver ssl]# vim /usr/local/nginx/conf/nginx.conf
server {
listen 443 ssl;
server_name localhost;
ssl_certificate /usr/local/nginx/ssl/nginx.crt;
ssl_certificate_key /usr/local/nginx/ssl/nginx.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root html;
index index.html index.htm;
}
[root@hxdserver ssl]# nginx -t
nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful
[root@hxdserver ssl]# nginx -s reload
验证
- 开启状态页面
修改配置文件
[root@hxdserver ~]# vim /usr/local/nginx/conf/nginx.conf
location /status {
stub_status on;
allow 192.168.0.0/16;
deny all;
}
[root@hxdserver ~]# nginx -t
nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful
[root@hxdserver ~]# nginx -s reload
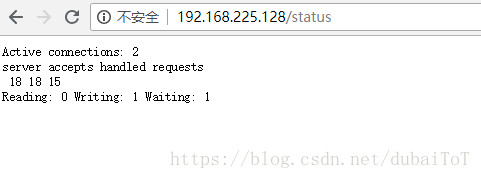
- 测试
- Active connections:当前所有处于打开状态的连接数
- accepts:总共处理了多少个连接
- handled:成功创建多少次握手
- requests:总共处理了多少个请求
- Reading:nginx读取到客户端的header信息数,表示正处于接受请求状态的连接数
- Writing:nginx返回给客户端的header信息数,表示请求已经接收完成,且正处于处理请求或发送响应的过程中的连接数
- Waiting:开启keep-alive的情况下,这个值等于active - (reading+writing),意思就是nginx已处理完正在等候下一次请求指令的驻留连接
rewrite重写url
[root@hxdserver ~]# vim /usr/local/nginx/conf/nginx.conf
location /aaa {
root /opt;
index index.html;
rewrite ^/aaa/(.*\.html) /bbb/$1 last; //将/aaa的url重写成/bbb的,接上last就会继续往后匹配,如果后面没有 那么将会访问/bbb下的网站
}
location /bbb {
root /opt;
index index.html index.htm;
rewrite ^/bbb/(.*\.html) /ccc/$1 break; //将/bbb的url重写成/ccc的,并停止匹配
}
[root@hxdserver opt]# mkdir /opt/{aaa,bbb,ccc}
[root@hxdserver opt]# ls
aaa bbb ccc
[root@hxdserver opt]# echo 'xixi' > /opt/aaa/a.html
[root@hxdserver opt]# echo 'haha' > /opt/bbb/a.html
[root@hxdserver opt]# echo 'xiha' > /opt/ccc/a.html
[root@hxdserver opt]# cd
[root@hxdserver ~]# nginx -t
nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful
[root@hxdserver ~]# nginx -s reload
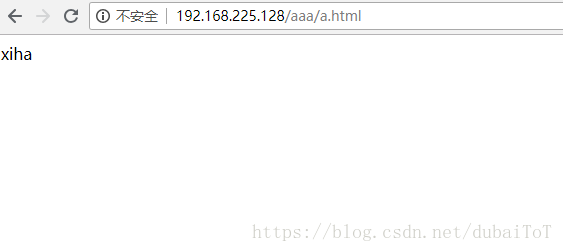
验证访问192.168.225.128/aaa/a.html
重写后访问到的是ccc/a.html,而不是aaa/a.html