**描述:利用非对称加密算法,实现两台主机之间可以免密码直接登录
,如下图:**

整个实验的原理如下图:
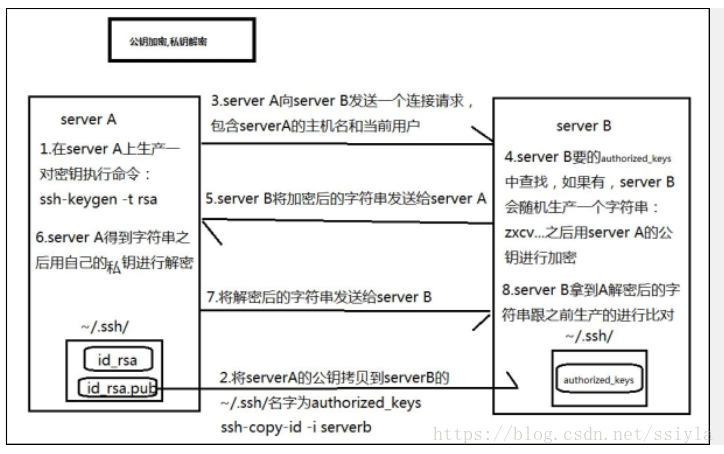
具体步骤如下:
- 1、先准备好实验需要的环境(两台虚拟机–A:192.168.72.73,B:192.168.72.23),此时,我们远程登录主机B,必须输入主机B的密码以后才可以成功登录,如下:
[root@server-140 .ssh]# ssh 192.168.72.23
root@192.168.72.23's password:
Last login: Sun Sep 9 15:40:44 2018 from 192.168.72.73
[root@server-23 ~]# - 2、有些时候为了方便快速,我们并不想总是输入密码,现在可以利用上我们的非对称加密算法了 执行ssh-keygen -t rsa, 然后一路回车,就可以生成公钥和私钥对了
[root@server-23 ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:nlrLZB+BVgkuypbsKaaySggvW4ANLtzjn7Fwn029B4Q root@server-23
The key's randomart image is:
+---[RSA 2048]----+
| . |
| . . . |
|. . . + |
|+o.o o . E . |
|=o.o* S o |
|+o.o.. o ..o |
|o.=ooo *.... |
|o* .+ =*+o ... |
|B. +.oo.... |
+----[SHA256]-----+
进入/root/.ssh查看公钥和私钥是否生成
[root@server-23 ~]# cd /root/.ssh/
[root@server-23 ~/.ssh]# ll
总用量 16
-rw-r--r-- 1 root root 397 9月 9 15:42 authorized_keys
-rw------- 1 root root 1679 9月 9 15:50 id_rsa
-rw-r--r-- 1 root root 396 9月 9 15:50 id_rsa.pub
-rw-r--r-- 1 root root 350 9月 8 13:24 known_hosts
注:id_rsa为私钥,id_rsa.pub是公钥- 3、下一步就是把公钥的内容拷贝给主机B下/root/.ssh/authorized_keys,authorized_keys如果不存在,自己建立就行
- 我是用Xshell登录的,就直接手动复制过去了,如果是用虚拟机的,也可以选择远程拷贝Scp
[root@server-23 ~/.ssh]# ll
总用量 16
-rw-r--r-- 1 root root 847 9月 9 16:00 authorized_keys- 4、操作成功后,就可以直接在主机A登录主机B了
[root@server-23 ~/.ssh]# ssh 192.168.72.23
The authenticity of host '192.168.72.23 (192.168.72.23)' can't be established.
ECDSA key fingerprint is SHA256:OMFX56Bo/D68z1hPiIv/CmYFiICWnDaayJfx7XGfnAI.
ECDSA key fingerprint is MD5:ab:59:6a:61:b8:c0:4a:98:71:3e:7f:20:1f:ff:02:ae.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.72.23' (ECDSA) to the list of known hosts.
Last login: Sun Sep 9 15:45:29 2018 from 192.168.72.73
[root@server-23 ~]# exit
登出
Connection to 192.168.72.23 closed.
[root@server-23 ~/.ssh]# ssh 192.168.72.23
Last login: Sun Sep 9 16:01:27 2018 from 192.168.72.23
注:只有第一次登录时需要确认,以后就可以免密码直接登录了那我们的ssh的免密码登录就成功了,以后需要输入密码的操作都可以不用输入密码了,除了ssh,还有如Scp,rsync等
但是需要我们注意的是,复制公钥的时候要保证两边的公钥完全相同,有一点不同,就无法实现免密码登录,所以,要细心哟!!!
如果有什么不同意见或者疑问,欢迎留言!