Amazon VPC is the networking layer for Amazon Elastic Compute Cloud (Amazon EC2), and it allows you to build your own virtual network within AWS.
An Amazon VPC address range may be as large as /16 (65,536 available addresses) or as small as /28 (16 available addresses)
An Amazon VPC consists of the following components:
Subnets
Route tables
Dynamic Host Configuration Protocol (DHCP) option sets
Security groups
Network Access Control Lists (ACLs)
An Amazon VPC has the following optional components:
Internet Gateways (IGWs)
Elastic IP (EIP) addresses
Elastic Network Interfaces (ENIs)
Endpoints
Peering
Network Address Translation (NATs) instances and NAT gateways
Virtual Private Gateway (VPG), Customer Gateways (CGWs), and Virtual Private Networks (VPNs)
Subnets
subnet is a segment of an Amazon VPC’s IP address range where you can launch Amazon EC2 instances。.
The smallest subnet that you can create is a /28 (16 IP addresses).
AWS reserves the first four IP addresses and the last IP address of every subnet for internal networking purposes. //考点
Subnets reside within one Availability Zone and cannot span zones.so remember that one subnet equals one Availability Zone.
Subnets can be classified as public, private, or VPN-only.
Default Amazon VPCs contain one public subnet in every Availability Zone within the region,with a netmask of /20.
Route Tables
A route table is a logical construct within an Amazon VPC that contains a set of rules (called routes) that are applied to the subnet and used to determine where network traffic is directed.
Each route table contains a default route called the local route, which enables
communication within the Amazon VPC,and this route cannot be modified or removed.
Internet Gateways
An Internet Gateway (IGW) is a horizontally scaled, redundant, and highly available Amazon VPC component that allows communication between instances in your Amazon VPC and the Internet.
Dynamic Host Configuration Protocol (DHCP) Option Sets
Dynamic Host Configuration Protocol (DHCP) provides a standard for passing configuration information to hosts on a TCP/IP network.
You can configure the following values within a DHCP option set:
domain-name-servers
domain-name
ntp-servers
netbios-name-servers
netbios-node-type
Every Amazon VPC must have only one DHCP option set assigned to it.
Elastic IP Addresses (EIPs)
AWS maintains a pool of public IP addresses in each region and makes them available for you to associate to resources within your Amazon VPCs.
You must first allocate an EIP for use within a VPC and then assign it to an instance.
EIPs are specific to a region (that is, an EIP in one region cannot be assigned to an instance within an Amazon VPC in a different region).
There is a one-to-one relationship between network interfaces and EIPs.
You can move EIPs from one instance to another, either in the same Amazon VPC or a different Amazon VPC within the same region.
EIPs remain associated with your AWS account until you explicitly release them.
There are charges for EIPs allocated to your account, even when they are not associated with a resource.
Elastic Network Interfaces (ENIs)
An Elastic Network Interface (ENI) is a virtual network interface that you can attach to an instance in an Amazon VPC.
They can have one public IP address and multiple private IP addresses.
If there are multiple private IP addresses, one of them is primary.
Assigning a second network interface to an instance via an ENI allows it to be dual-homed (have network presence in different subnets).
Endpoints
An Amazon VPC endpoint enables you to create a private connection between your Amazon VPC and another AWS service without requiring access over the Internet or through a NAT instance,VPN connection, or AWS Direct Connect.
Peering
An Amazon VPC peering connection is a networking connection between two Amazon VPCs that enables instances in either Amazon VPC to communicate with each other as if they are within the same network.
You cannot create a peering connection between Amazon VPCs that have matching or overlapping CIDR blocks.
You cannot create a peering connection between Amazon VPCs in different regions.
Amazon VPC peering connections do not support transitive routing.
You cannot have more than one peering connection between the same two Amazon VPCs at the same time.
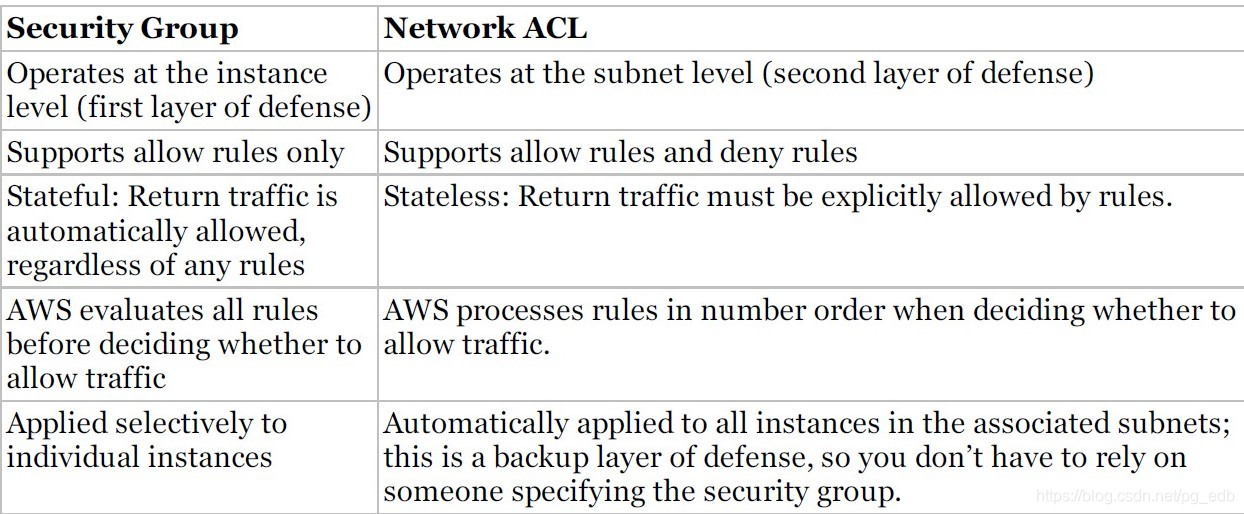
Security Groups
A security group is a virtual stateful firewall that controls inbound and outbound network traffic to AWS resources and Amazon EC2 instances.
All Amazon EC2 instances must be launched into a security group.
If a security group is not specified at launch, then the instance
will be launched into the default security group for the Amazon VPC. The default security group allows communication between all resources within the security group, allows all outbound traffic, and denies all other traffic. You may change the rules for the default security group, but you may not delete the default security group.
You can create up to 500 security groups for each Amazon VPC.
You can add up to 50 inbound and 50 outbound rules to each security group. If you need to apply more than 100 rules to an instance, you can associate up to five security groups with each network interface.
You can specify allow rules, but not deny rules. This is an important difference between security groups and ACLs.
You can specify separate rules for inbound and outbound traffic.
By default, no inbound traffic is allowed until you add inbound rules to the security group.
By default, new security groups have an outbound rule that allows all outbound traffic.
You can remove the rule and add outbound rules that allow specific outbound traffic only.
Security groups are stateful. This means that responses to allowed inbound traffic are allowed to flow outbound regardless of outbound rules and vice versa. This is an important difference between security groups and network ACLs.
Instances associated with the same security group can’t talk to each other unless you add rules allowing it (with the exception being the default security group).
You can change the security groups with which an instance is associated after launch,and the changes will take effect immediately.
Network Access Control Lists (ACLs)
A network access control list (ACL) is another layer of security that acts as a stateless firewall on a subnet level.
When you create a custom network ACL, its initial configuration will deny all inbound and outbound traffic until you create rules that allow otherwise.
Overall, every subnet must be associated with a network ACL.
Comparison of Security Groups and Network ACLs
Network Address Translation (NAT) Instances and NAT Gateways
AWS provides NAT instances and NAT gateways to allow instances deployed in private subnets to gain Internet access.
NAT Instance
A network address translation (NAT) instance is an Amazon Linux Amazon Machine Image (AMI) that is designed to accept traffic from instances within a private subnet, translate the source IP address to the public IP address of the NAT instance, and forward the traffic to the IGW.
NAT Gateway
NAT gateway is an Amazon managed resource that is designed to operate just like a NAT instance, but it is simpler to manage and highly available within an Availability Zone.
Virtual Private Gateways (VPGs), Customer Gateways (CGWs), and Virtual Private Networks (VPNs)
You can connect an existing data center to Amazon VPC using either hardware or software VPN connections, which will make Amazon VPC an extension of the data center. Amazon VPC offers two ways to connect a corporate network to a VPC: VPG and CGW.
A virtual private gateway (VPG) is the virtual private network (VPN) concentrator on the AWS side of the VPN connection between the two networks. A customer gateway (CGW) represents a physical device or a software application on the customer’s side of the VPN connection.
The VPN connection consists of two Internet Protocol Security (IPSec) tunnels for higher availability to the Amazon VPC.
You must specify the type of routing that you plan to use when you create a VPN connection.
If the CGW supports Border Gateway Protocol (BGP), then configure the VPN connection for dynamic routing. Otherwise, configure the connections for static routing. If you will be using static routing, you must enter the routes for your network that should be communicated to the VPG. Routes will be propagated to the Amazon VPC to allow your resources to route
network traffic back to the corporate network through the VGW and across the VPN tunnel.
The VPG is the AWS end of the VPN tunnel.
The CGW is a hardware or software application on the customer’s side of the VPN tunnel.
You must initiate the VPN tunnel from the CGW to the VPG.
VPGs support both dynamic routing with BGP and static routing.
The VPN connection consists of two tunnels for higher availability to the VPC.