这篇写下IKEv1的一些概念,包含DM-V-P-N和GET-V-P-N的配置
IKEv2也就是Flex-V-P-N之后再写
第一部分: IKEv1概念
主要说下控制层面,SA与SADB
这里直接抄教主以前的笔记:
SADB:在SADB里的每一个条目决定了一个特定SA的参数,当一个IPSec SA被创建,SADB更新所有关于这个SA的参数。当一个inbound的IPsec packet抵达,SADB基于outer ip header的destination address,SPI和ESP header,检查数据库以获得相应的SA,然后用这个SA的相关参数处理这个inbound ipsec packet。
而对于outbound IPSec packets 处理的相关参数是由SPD相关联的SA来获取的。
既:SAD security association data来处理inbound流量,SPD处理outbound流量。
SADB的9大部分:
- sequence number: 32-bit value provided in the ESP or AH header
- sequence number overflow: when sequence number is over 2^32
- anti-replay window: used to determin if an inbound IPSec packet is a replayed packet
- SA lifetime
- modes: transport or tunnel
- AH alogorithm
- ESP authentication algorithm
- ESP encryption algorithm
- Path MTU
IKEv1理论
IKE主要负责建立和维护IKE SA和IPsec SA。这里主要介绍main mode,因为aggressive mode的EZ×××已经淘汰了。
main mode 一共有6个包,以下链接讲的非常清楚
http://www.omnisecu.com/tcpip/ikev1-main-aggressive-and-quick-mode-message-exchanges.php
message 1 2: 协商SA payload,proposal payload, transform payload
message 3 4: diffie-hellman group,实际上配置时候的group number,并且计算密钥
message 5 6: 建立双向的IKEv1 sa
PFS:perfect forward secrecy
在ipsec里,PFS是通过ipsec sa协商阶段重新进行一次DH交换来实现的。
第二部分: DM-V-P-N
把DM-V-P-N打通,练习下证书的玩法。
DM×××和IGP部分
R1 hub:
int tun 0
ip add 192.168.100.1 255.255.255.0
tunnel source gi2
tunnel mode gre multipoint
ip nhrp map multicast dynamic
ip nhrp redirect
ip nhrp network-id 100
ip nhrp authentication cisco123
R2 spoke:
int tu 0
ip add 192.168.100.2 255.255.255.0
tunnel source gi1
tunnel mode gre multipoint
ip nhrp map 192.168.100.1 54.109.1.2
ip nhrp map multicast 54.109.1.2
ip nhrp shortcut
ip nhrp nhs 192.168.100.1
ip nhrp network-id 100
ip nhrp authentication cisco123
R3 spoke:
int tu 0
ip add 192.168.100.3 255.255.255.0
tunnel source gi1
tunnel mode gre multipoint
ip nhrp map 192.168.100.1 54.109.1.2
ip nhrp map multicast 54.109.1.2
ip nhrp shurtcut
ip nhrp nhs 192.168.100.1
ip nhrp network-id 100
ip nhrp authentication cisco123
R4 spoke:
int tu 0
ip add 192.168.100.4 255.255.255.0
tunnel source gi1
tunnel mode gre multipoint
ip nhrp map 192.168.100.1 54.109.1.2
ip nhrp map multicast 54.109.1.2
ip nhrp shortcut
ip nhrp nhs 192.168.100.1
ip nhrp network-id 100
ip nhrp authentication cisco123
IGP:
router eigrp 10
network 192.168.100.0 0.0.0.255
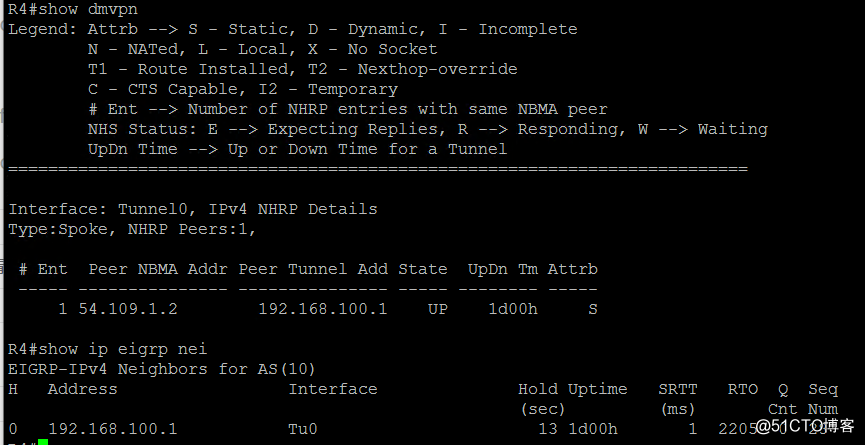
验证:
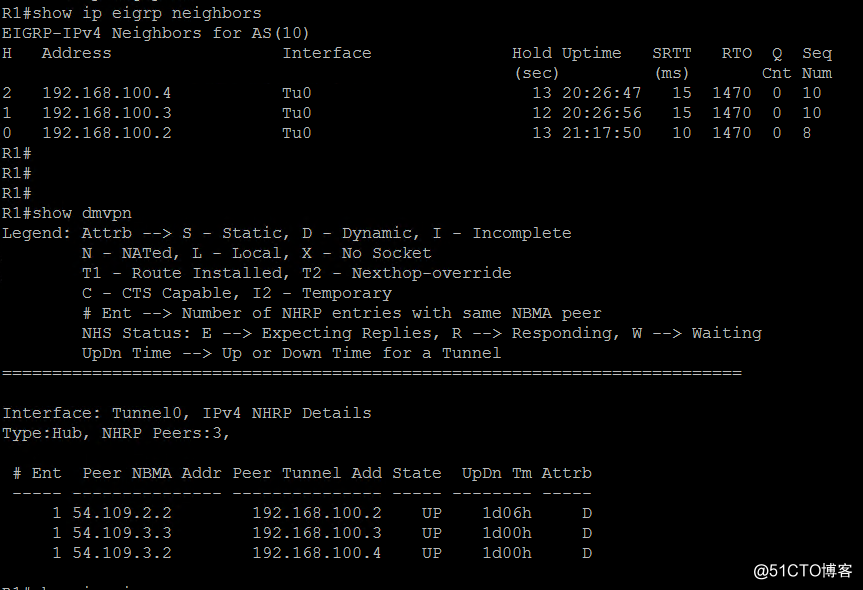
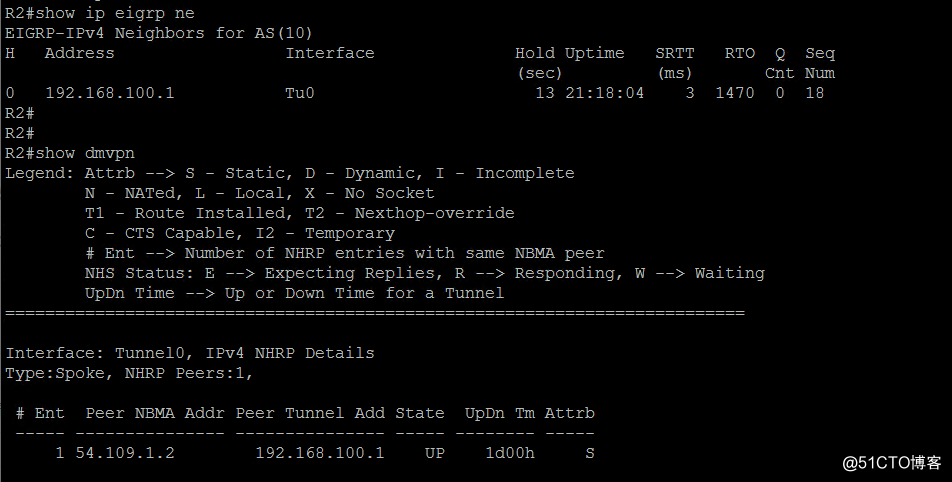
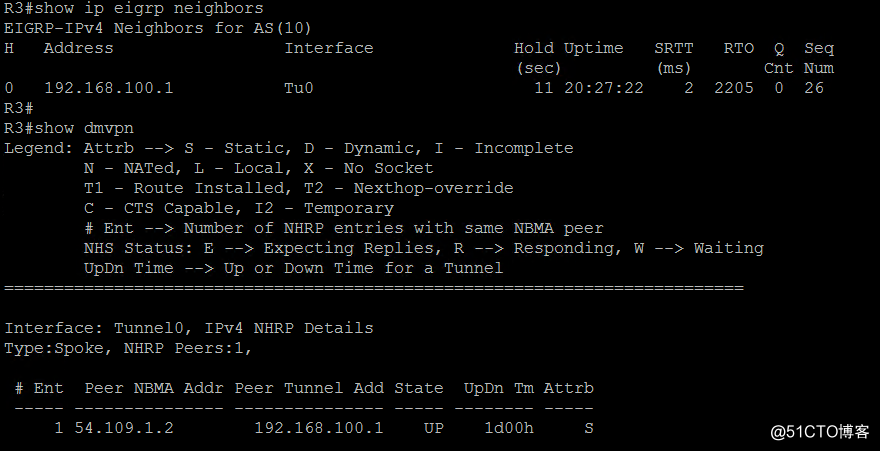
show dm***
show ip eigrp neighbor
Hub as CA:
ip http server
crypto key generate rsa modu 1024 label dm***-key exportable
crypto pki trustpoint CA
revocation-check url
rsakeypair dm***-key
crypto pki certificate CA
issuer-name CN:Hub.securitylab.net
grant auto
database level complete
database url nvram:
R1
crypto key genertae rsa modu 1024 label dm***-key exportable
crypto pki trustpoint CA
enrollment url http://10.10.10.10:80
rsakeypair dm***-key
crypto pki authenticate CA
crypto pki enroll CA
R2
crypto key generate rsa modul 1024 label dm-key exportable
crypto pki trustpoint CA
enrollment url http://10.10.10.10:80
rsakeypair dm-key
crypto pki authenticate CA
crypto pki enroll CA
R3
crypto key generate rsa modul 1024 label dm-key exportable
crypto pki trustpoint CA
enrollment url http://10.10.10.10:80
rsakeypair dm-key
crypto pki authenticate CA
crypto pki enroll CA
R4
crypto key generate rsa modu 1024 label dm-key exportable
crypto pki trustpoint CA
enrollment url http://10.10.10.10:80
rsakeypair dm-key
crypto pki authenticate CA
crypto pki enroll CA
Encryption
R1~R4
crypto isakmp policy 10
encryption aes
group 5
crypto ipsec transform-set TS esp-aes esp-sha-hmac
mode transport
crypto ipsec profile DM×××
set transform-set TS
int tunnel 0
tunnel protection ipsec profile DM×××
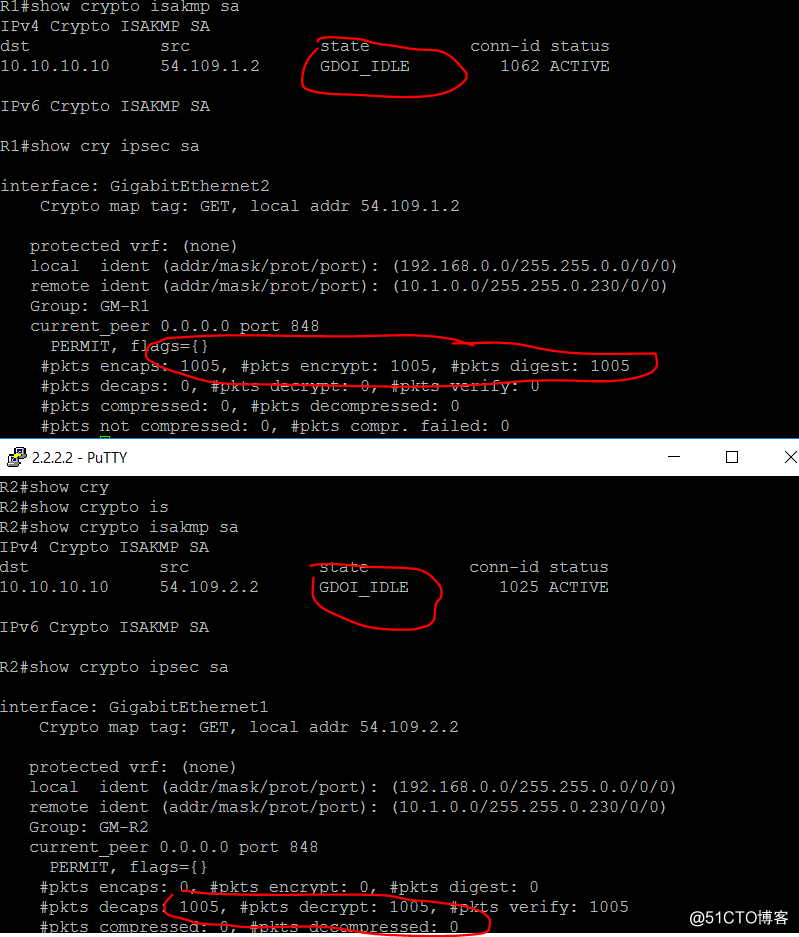
show crypto isakmp sa
show crypto ipsec sa
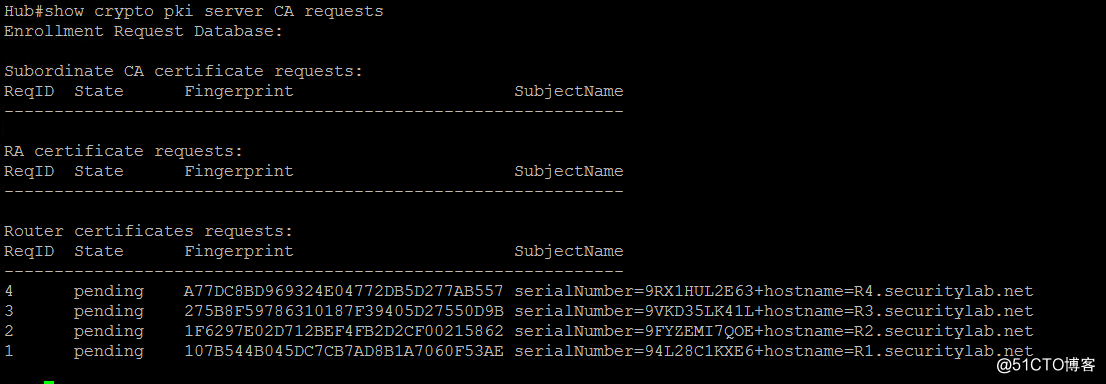
如果pki server不是grant auto的,需要手动grant
在客户端认证和注册之后,使用以下命令查看
show crypto pki certificates
show crypto pki server CA requests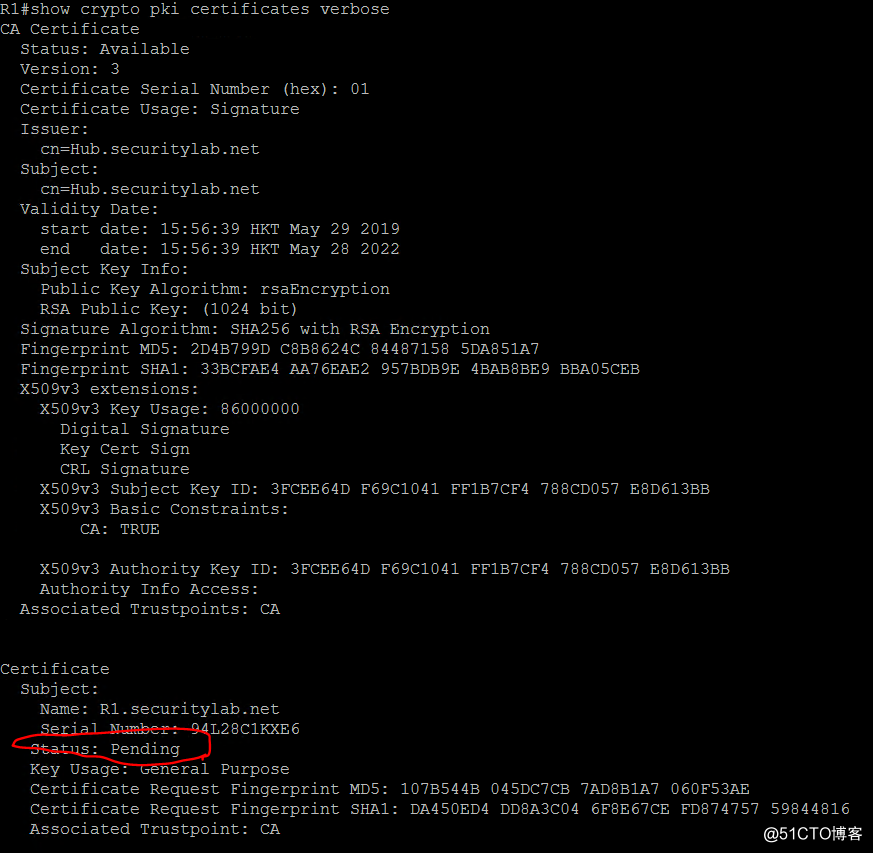
需要等待一会时间才能生效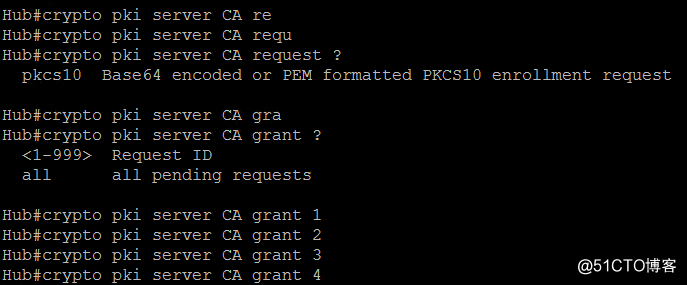
第三部分: GET_V_P_N
GET-V-P-N的功能不用多说了,就是给已有的连接的链路加密。优点有,收敛性不错,不需要隧道级的封装,QoS和组播的支持优秀。
组件:
1 GDOI:group domain of intepretation 用于组成员和组控制器(group controller)之间建立安全关联SA。实现安全的group内通讯,UDP 848,实际上等于一个“phase 2”ipsec 机制。
2 Group Controller/Key Server(GCKS)组维护策略,创建和维护key的的路由器。当一个Group Member注册的时候,Key server也会在密钥超时前更新密钥。
两种key
TEK:Traffic Encryption Key,纯粹用来加密流量。
KEK:Key Encryption Key, 用来加密更新密钥信息,每一个组成员也用它来解密Key Server发送过来的更新密钥信息。(Rekey)
- Group Member:在KS上注册,并且在KS上获取IPSec SA。Group member在KS上注册并且提供一个Group ID,并且从KS获取用于这个group的安全策略和密钥。
概念实在太多,工作中能用的机会也少,直接贴个讲个最好的文档
https://community.cisco.com/t5/security-documents/get***/ta-p/3114998
唯一需要注意的是,rekey的方式有组播和单播两种,在配置中使用前者,一定需要把组播打开。
在我的topology里面,我用尝试用Hub作为Key Server,R1,R2,R3,R4作为group member转发数据。
Key Server
密钥服务器配置非常复杂,总结起来一共五步
- crypto key generate modu 2048 label GET-key exportable//生成密钥对
- crypto isakmp policy 20 //定义phase 1策略,和对应的地址以及口令
encryption 3des
authentication pre-share
crypto isakmp key 0 cisco123 address 0.0.0.0 0.0.0.0 - ip access-list extended GET-Traffic //定义感兴趣流
permit ip 10.1.0.0 0.0.255.255 192.168.0.0 0.0.255.255
permit ip 192.168.0.0 0.0.255.255 10.1.0.0 0.0.255.25
permit ip 10.1.0.0 0.0.255.255 172.16.0.0 0.0.255.255
permit ip 172.16.0.0 0.0.255.255 10.1.0.0 0.0.255.255
permit ip 172.16.0.0 0.0.255.255 192.168.0.0 0.0.255.255
permit ip 192.168.0.0 0.0.255.255 172.16.0.0 0.0.255.255 - crypto ipsec transform-set GET-TS esp-aes esp-hmac-sha //GET-V-P-N肯定使用tunnel模式
crypto ipsec profile
set transform-set GET-TS - 最复杂难记的key server配置
crypto gdoi group KS
identity number 666
server local
address ipv4 10.10.10.10
rekey authentication mypubkey GET-key
rekey transport unicast
sa ipsec 1
profile GET-TS
replay time window-size 3
组成员比较简单了
crypto isakmp policy 20
encryption 3des
authentication pre-share
crypto isakmp key 0 cisco123 address 0.0.0.0 0.0.0.0
crypto gdoi group GM
identity number 666
server address 10.10.10.10
crypto map GET 10 gdoi
set group GM
int gi 2
crypto map GET
验证命令
KS: show crypto gdoi ks member
GM:show crypto gdoi
有几个注意事项,默认的rekey模式是组播,(但我个人认为这就和OTV一样,说组播好处一大堆,实际部署的时候如果是为了加密MPLS链路就歇菜,因为支持组播的mpls线路很贵还不一定有,内网的交换机之间的Trunk链路,我为啥不用MacSec?)
Key Server和Group member的identity number,IKE第一阶段的口令得匹配。
粘贴一些配置,和结果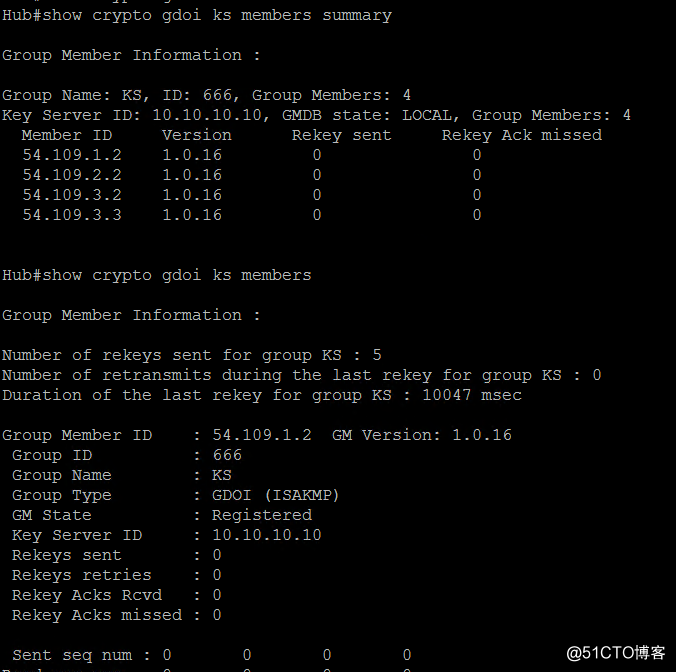
R1#show crypto gdoi
GROUP INFORMATION
Group Name : GM-R1
Group Identity : 666
Group Type : GDOI (ISAKMP)
Crypto Path : ipv4
Key Management Path : ipv4
Rekeys received : 0
IPSec SA Direction : Both
Group Server list : 10.10.10.10Group Member Information For Group GM-R1:
IPSec SA Direction : Both
ACL Received From KS : gdoi_group_GM-R1_temp_acl
Group member : 54.109.1.2 vrf: None
Local addr/port : 54.109.1.2/848
Remote addr/port : 10.10.10.10/848
fvrf/ivrf : None/None
Version : 1.0.16
Registration status : Registered
Registered with : 10.10.10.10
Re-registers in : 1610 sec
Succeeded registration: 1
Attempted registration: 1
Last rekey from : 0.0.0.0
Last rekey seq num : 0
Unicast rekey received: 0
Rekey ACKs sent : 0
Rekey Received : never
DP Error Monitoring : OFF
IPSEC init reg executed : 0
IPSEC init reg postponed : 0
Active TEK Number : 1
SA Track (OID/status) : disabled
allowable rekey cipher: any
allowable rekey hash : any
allowable transformtag: any ESP
Rekeys cumulative
Total received : 0
After latest register : 0
Rekey Acks sents : 0ACL Downloaded From KS 10.10.10.10:
access-list permit ip 10.1.0.0 0.0.255.255 192.168.0.0 0.0.255.255
access-list permit ip 192.168.0.0 0.0.255.255 10.1.0.0 0.0.255.25
access-list permit ip 10.1.0.0 0.0.255.255 172.16.0.0 0.0.255.255
access-list permit ip 172.16.0.0 0.0.255.255 10.1.0.0 0.0.255.255
access-list permit ip 172.16.0.0 0.0.255.255 192.168.0.0 0.0.255.255
access-list permit ip 192.168.0.0 0.0.255.255 172.16.0.0 0.0.255.255
KEK POLICY:
Rekey Transport Type : Unicast
Lifetime (secs) : 84605
Encrypt Algorithm : 3DES
Key Size : 192
Sig Hash Algorithm : HMAC_AUTH_SHA
Sig Key Length (bits) : 2352
TEK POLICY for the current KS-Policy ACEs Downloaded:
GigabitEthernet2:
IPsec SA:
spi: 0x451180FB(1158775035)
KGS: Disabled
transform: esp-aes esp-sha-hmac
sa timing:remaining key lifetime (sec): (1807)
Anti-Replay(Time Based) : 3 sec interval
tag method : disabled
alg key size: 16 (bytes)
sig key size: 20 (bytes)
encaps: ENCAPS_TUNNEL