Firewalld
安全 OSI
物理层
数据链路层
网络层
传输层
会话层
表示层
应用层
-----------------------------------------------------------------------------------------
硬件安全 机柜锁
网络安全 iptables firewalld selinux
服务安全 更新有漏洞的版本 nginx mysql redis
系统安全 没有公网ip,修改ssh默认端口号,禁用root远程登录。
-----------------------------------------------------------------------------------------
云环境:
网络 高防DDOS、安全组
系统 SSH安全、权限控制、更新补丁、安骑士、堡垒机
web SSL、WAF、云安全中心
数据 备份 敏感数据保护
服务 mysql redis ..... 所有主机都没有公网IP, 大大的降低被攻击的风险
web SSL、WAF --> SQL注入漏洞、XSS跨站、网站挂马、页面被篡改、蠕虫等黑客
数据 备份
-----------------------------------------------------------------------------------------
第三方软件 硬件防火墙 waf防火墙 防DDOS攻击 漏洞注入 SQL注入
安全狗
知道创宇
牛盾云
-----------------------------------------------------------------------------------------
物理环境:
硬件 (电源被拔 UPS 网线被拔(打标签))
网络 (硬件防火墙 软件防火墙(Friewalld/Iptables(规则限制)))
系统 (SSH安全 权限控制)
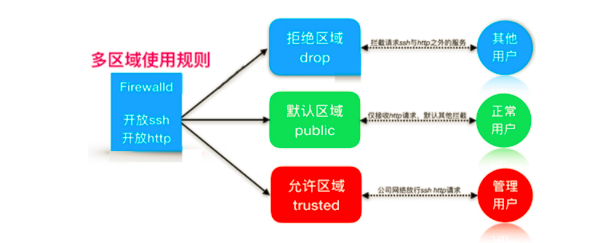
- Firewalld基本概述
规则:默认是从外部访问内部是拒绝的,从内部访问外部,默认是允许的。
Firewalld底层使用的就是iptables
Firewalld 多了个zone的概念 区域
trusted 允许所有的数据包流入与流出
home 拒绝流入的流量,除非与流出的流量相关;而如果流量与ssh、mdns、ipp-client、amba-client与dhcpv6-client服务相关,则允许流量
internal 等同于home区域
work 拒绝流入的流量,除非与流出的流量数相关;而如果流量与ssh、ipp-client与dhcpv6-client服务相关,则允许流量
public 拒绝流入的流量,除非与流出的流量相关;而如果流量与ssh、dhcpv6-client服务相关,则允许流量
external 拒绝流入的流量,除非与流出的流量相关;而如果流量与ssh服务相关,则允许流量
dmz 拒绝流入的流量,除非与流出的流量相关;而如果流量与ssh服务相关,则允许流量
block 拒绝流入的流量,除非与流出的流量相关
drop 拒绝流入的流量,除非与流出的流量相关
[root@web01 ~]# systemctl start firewalld
[root@web01 ~]# systemctl enable firewalld
禁用iptables
[root@web01 ~]# systemctl mask iptables
Created symlink from /etc/systemd/system/iptables.service to /dev/null.
[root@web01 ~]# systemctl mask ip6tables
Created symlink from /etc/systemd/system/ip6tables.service to /dev/null.
[root@web01 ~]#
白名单
trusted 允许所有的数据包流入与流出
public 拒绝流入的流量,除非与流出的流量相关;而如果流量与ssh、dhcpv6-client服务相关,则允许流量
drop 拒绝流入的流量,除非与流出的流量相关
- 区域管理
使用firewalld多个区域规则结合,调整默认public区域拒绝所有流量,但如果来源IP是10.0.0.1/24则允许。
显示所有的zone
[root@web01 ~]# firewall-cmd --get-zones
block dmz drop external home internal public trusted work
详细的显示所有zone的默认规则
[root@web01 ~]# firewall-cmd --list-all-zones
block
target: %%REJECT%%
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
显示当前默认的zone
[root@web01 ~]# firewall-cmd --get-default-zone
public
显示默认区域的规则
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
设置默认的区域
[root@web01 ~]# firewall-cmd --set-default-zone=trusted
success
查看默认的区域
[root@web01 ~]# firewall-cmd --get-default-zone
trusted
显示当前活动的区域及接口
[root@web01 ~]# firewall-cmd --get-active-zone
public
interfaces: eth0 eth1
添加一个新的zone
[root@web01 ~]# firewall-cmd --new-zone=test --permanent
success
查看所有的zone
[root@web01 ~]# firewall-cmd --get-zones
block dmz drop external home internal public trusted work
重启firewalld的设置规则
[root@web01 ~]# firewall-cmd --reload
success
查看所有的zone
[root@web01 ~]# firewall-cmd --get-zones
block dmz drop external home internal public test trusted work
删除zone
[root@web01 ~]# firewall-cmd --delete-zone=test --permanent
success
[root@web01 ~]# firewall-cmd --get-zones
block dmz drop external home internal public test trusted work
[root@web01 ~]# firewall-cmd --reload
success
[root@web01 ~]# firewall-cmd --get-zones
block dmz drop external home internal public trusted work
使用Firewalld中各个区域规则结合,当前默认区域拒绝所有的流量,但如果来源IP是10.0.0.0/24网段则允许。
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
移除ssh和dhcp的服务
[root@web01 ~]# firewall-cmd --remove-service={ssh,dhcpv6-client}
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services:
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
设置来源ip属于10.0.0.0/24网段的ip允许所有
[root@web01 ~]# firewall-cmd --add-source=10.0.0.0/24 --zone=trusted
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services:
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
[root@web01 ~]# firewall-cmd --get-active-zone
public
interfaces: eth0 eth1
trusted
sources: 10.0.0.0/24
[root@web01 ~]# firewall-cmd --reload #重启服务之后,临时生效的失效
success
[root@web01 ~]# firewall-cmd --get-active-zone
public
interfaces: eth0 eth1
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
拒绝10.0.0.0/24网段的所有服务
[root@web01 ~]# firewall-cmd --add-source=10.0.0.0/24 --zone=drop
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
[root@web01 ~]# firewall-cmd --get-active-zone
drop
sources: 10.0.0.0/24
public
interfaces: eth0 eth1
- 防火墙服务管理
添加一个服务
[root@web01 ~]# firewall-cmd --add-service=http
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh dhcpv6-client http
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
移除一个服务
[root@web01 ~]# firewall-cmd --remove-service=dhcpv6-client
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh http
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
只显示当前允许的通过的服务
[root@web01 ~]# firewall-cmd --list-services
ssh http
添加多个服务
[root@web01 ~]# firewall-cmd --add-service={https,mysql,redis}
success
[root@web01 ~]# firewall-cmd --list-services
ssh http https mysql redis
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh http https mysql redis
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
移除多个服务
[root@web01 ~]# firewall-cmd --remove-service={http,https,mysql,redis}
success
[root@web01 ~]# firewall-cmd --list-services
ssh
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
显示所有预定义的服务
[root@web01 ~]# firewall-cmd --get-services
RH-Satellite-6 amanda-client amanda-k5-client bacula bacula-client bgp bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc ceph ceph-mon cfengine condor-collector ctdb dhcp dhcpv6 dhcpv6-client dns docker-registry docker-swarm dropbox-lansync elasticsearch freeipa-ldap freeipa-ldaps freeipa-replication freeipa-trust ftp ganglia-client ganglia-master git gre high-availability http https imap imaps ipp ipp-client ipsec irc ircs iscsi-target jenkins kadmin kerberos kibana klogin kpasswd kprop kshell ldap ldaps libvirt libvirt-tls managesieve mdns minidlna mongodb mosh mountd ms-wbt mssql murmur mysql nfs nfs3 nmea-0183 nrpe ntp openvpn ovirt-imageio ovirt-storageconsole ovirt-vmconsole pmcd pmproxy pmwebapi pmwebapis pop3 pop3s postgresql privoxy proxy-dhcp ptp pulseaudio puppetmaster quassel radius redis rpc-bind rsh rsyncd samba samba-client sane sip sips smtp smtp-submission smtps snmp snmptrap spideroak-lansync squid ssh syncthing syncthing-gui synergy syslog syslog-tls telnet tftp tftp-client tinc tor-socks transmission-client upnp-client vdsm vnc-server wbem-https xmpp-bosh xmpp-client xmpp-local xmpp-server zabbix-agent zabbix-server
参数 zone区域相关指令 作用
--get-default-zone 查询默认的区域名称
--set-default-zone=
<区域名称>
设置默认的区域,使其永久生效
--get-active-zones 显示当前正在使用的区域与网卡名称
--get-zones 显示总共可用的区域
--new-zone= 新增区域
--delete-zone= 删除区域
--get-services 显示预先定义的服务
--add-service=
<服务名>
设置默认区域允许该服务的流量
--remove-service=
<服务名>
设置默认区域不再允许该服务的流量
--list-services 显示默认区域允许的服务
Port端口相关指令
--add-port=
<端口号 协议>
设置默认区域允许该端口的流量
--remove-port=
<端口号 协议>
设置默认区域不再允许该端口的流量
--list-port 显示默认区域允许的端口
Interface网卡相关指令
--get-zone-of-interface=
<网卡名称>
查看接口在哪个区域
--add-interface=
<网卡名称>
将源自该网卡的所有流量都导向某个指定区域
--remove-interface=
<网卡名称>
删除接口
地址源相关命令
--add-source= 添加来源地址
--remove-source= 移除来源地址
其他相关指令
--list-all 显示当前区域的网卡配置参数、资源、端口以及服务等信息
--reload 让"永久生效"的配置规则立即生效,并覆盖当前的配置规则
--panic-on 阻断一切网络连接
--panic-off 恢复网络连接
- 防火墙端口管理
添加一个端口
[root@web01 ~]# firewall-cmd --add-port=80/tcp
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh dhcpv6-client
ports: 80/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
显示所有允许的端口及协议
[root@web01 ~]# firewall-cmd --list-ports
80/tcp
添加多个端口
[root@web01 ~]# firewall-cmd --add-port={443/tcp,6379/tcp}
success
[root@web01 ~]# firewall-cmd --list-ports
80/tcp 443/tcp 6379/tcp
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh dhcpv6-client
ports: 80/tcp 443/tcp 6379/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
[root@web01 ~]# firewall-cmd --list-ports
80/tcp 443/tcp 6379/tcp
移除一个端口
[root@web01 ~]# firewall-cmd --remove-port=6379/tcp
success
[root@web01 ~]# firewall-cmd --list-ports
80/tcp 443/tcp
移除多个端口
[root@web01 ~]# firewall-cmd --remove-port={80/tcp,443/tcp}
success
[root@web01 ~]# firewall-cmd --list-ports
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
- 接口管理
查看接口在哪个zone下面
[root@web01 ~]# firewall-cmd --get-zone-of-interface=eth0
public
[root@web01 ~]# firewall-cmd --get-zone-of-interface=eth1
public
移除eth1接口
[root@web01 ~]# firewall-cmd --remove-interface=eth1
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
添加一个接口
[root@web01 ~]# firewall-cmd --add-interface=eth0
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
[root@web01 ~]# firewall-cmd --get-zone-of-interface=eth1
no zone
将接口跟zone进行相关联
[root@web01 ~]# firewall-cmd --change-interface=eth0 --zone=public
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
- 源地址管理
禁用一个ip地址的所有访问
[root@web01 ~]# firewall-cmd --add-source=10.0.0.8/32 --zone=drop
success
[root@web01 ~]# firewall-cmd --get-active-zone
drop
sources: 10.0.0.8/32
public
interfaces: eth0
禁用一个网段
[root@web01 ~]# firewall-cmd --add-source=10.0.0.0/24 --zone=drop
success
[root@web01 ~]# firewall-cmd --get-active-zone
drop
sources: 10.0.0.8/32 10.0.0.0/24
public
interfaces: eth0
允许一个ip地址访问所有
[root@web01 ~]# firewall-cmd --add-source=10.0.0.8/32 --zone=trusted
success
[root@web01 ~]# firewall-cmd --get-active-zone
public
interfaces: eth0
trusted
sources: 10.0.0.8/32
移除ip地址
[root@web01 ~]# firewall-cmd --remove-source=10.0.0.8/32 --zone=trusted
success
[root@web01 ~]# firewall-cmd --get-active-zone
public
interfaces: eth0
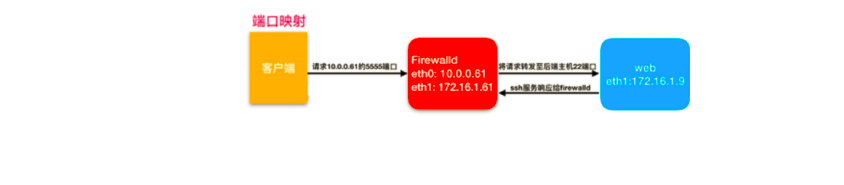
- 地址转发
firewall-cmd --permanent --zone=
<区域>
--add-forward-port=port=
<源端口号>
:proto=
<协议>
:toport=
<目标端口号>
:toaddr=
<目标ip地址>
开启地址映射
[root@web01 ~]# firewall-cmd --add-masquerade
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: yes
forward-ports:
source-ports:
icmp-blocks:
rich rules:
将本地的6666端口映射到后端的172.16.1.8的22端口
[root@web01 ~]# firewall-cmd --zone=public --add-forward-port=port=6666:proto=tcp:toport=22:toaddr=172.16.1.8
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: yes
forward-ports: port=6666:proto=tcp:toport=22:toaddr=172.16.1.8
source-ports:
icmp-blocks:
rich rules:
移除端口映射
[root@web01 ~]# firewall-cmd --remove-forward-port=port=6666:proto=tcp:toport=22:toaddr=172.16.1.8
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: ssh dhcpv6-client
ports:
protocols:
masquerade: yes
forward-ports:
source-ports:
icmp-blocks:
rich rules:
禁用一切网络
[root@web01 ~]# firewall-cmd --panic-on
关闭禁用的网络
[root@web01 ~]# firewall-cmd --panic-off
- 自定义服务名称
拷贝配置文件
[root@web01 ~]# cp /usr/lib/firewalld/services/http.xml /usr/lib/firewalld/services/oldboy.xml
编写配置文件
[root@web01 ~]# cat /usr/lib/firewalld/services/oldboy.xml
添加这个服务
[root@web01 ~]# firewall-cmd --add-service=oldboy
success
[root@web01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: ssh dhcpv6-client oldboy
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules: