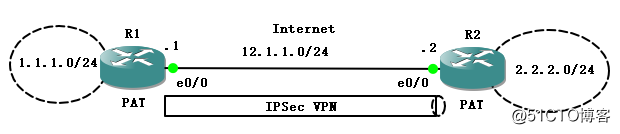
1、测试拓扑:
2、相关说明:
实际的网络情况中,Site1和Site2之间要建立IPSec VPN,已让 Site后面的内网网段互通。但是实际的情况往往也有访问internet的需求,所以一般会有NAT的情况,例如这里的情况和一般的NAT-T不一样。做VPN的设备和NAT的设备一样。
3、相关配置:
R1:
crypto isakmp policy 10
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 12.1.1.2
!
!
crypto ipsec transform-set Trans esp-3des esp-md5-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 12.1.1.2
set transform-set Trans
match address vpn
!
!
!
!
interface Loopback0
ip address 1.1.1.1 255.255.255.0
ip nat inside
ip virtual-reassembly
!
interface Ethernet0/0
ip address 12.1.1.1 255.255.255.0
ip nat outside
ip virtual-reassembly
half-duplex
crypto map cisco
!
ip route 2.2.2.0 255.255.255.0 12.1.1.2 >>>>这条静态路由,是为了让流量撞上VPN触发流量
!
!
ip nat inside source list nat interface Ethernet0/0 overload
!
!
ip access-list extended nat
deny ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255 >>>>这里是为了不让1.1.1.1访问2.2.2.2的流量撞上NAT
permit ip any any
ip access-list extended vpn
permit ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255
R2:
crypto isakmp policy 10
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 12.1.1.1
!
!
crypto ipsec transform-set Trans esp-3des esp-md5-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 12.1.1.1
set transform-set Trans
match address vpn
!
!
!
!
interface Loopback0
ip address 2.2.2.2 255.255.255.0
ip nat outside
ip virtual-reassembly
!
interface Ethernet0/0
ip address 12.1.1.2 255.255.255.0
half-duplex
crypto map cisco
!
ip route 1.1.1.0 255.255.255.0 12.1.1.1
!
!
ip nat inside source list nat interface Ethernet0/0 overload
!
!
ip access-list extended nat
deny ip 2.2.2.0 0.0.0.255 1.1.1.0 0.0.0.255
permit ip any any
ip access-list extended vpn
permit ip 2.2.2.0 0.0.0.255 1.1.1.0 0.0.0.255
触发VPN:
R1#ping 2.2.2.2 so 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 32/44/48 ms
4、分析建立过程:
第一阶段:
*Mar 1 04:49:24.886: ISAKMP (0:0): received packet from 12.1.1.1 dport 500 sport 500 Global (N) NEW SA
*Mar 1 04:49:24.886: ISAKMP: Created a peer struct for 12.1.1.1, peer port 500
*Mar 1 04:49:24.886: ISAKMP: New peer created peer = 0x64F66BC4 peer_handle = 0x80000007
*Mar 1 04:49:24.890: ISAKMP: Locking peer struct 0x64F66BC4, IKE refcount 1 for crypto_isakmp_process_block
*Mar 1 04:49:24.890: ISAKMP: local port 500, remote port 500
*Mar 1 04:49:24.890: insert sa successfully sa = 646DD604
*Mar 1 04:49:24.894: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 1 04:49:24.894: ISAKMP:(0:0:N/A:0):Old State = IKE_READY New State = IKE_R_MM1
*Mar 1 04:49:24.898: ISAKMP:(0:0:N/A:0): processing SA payload. message ID = 0
*Mar 1 04:49:24.898: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 1 04:49:24.898: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 1 04:49:24.902: ISAKMP (0:0): vendor ID is NAT-T v7
*Mar 1 04:49:24.902: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 1 04:49:24.902: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 157 mismatch
*Mar 1 04:49:24.902: ISAKMP:(0:0:N/A:0): vendor ID is NAT-T v3
*Mar 1 04:49:24.906: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 1 04:49:24.906: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 123 mismatch
*Mar 1 04:49:24.906: ISAKMP:(0:0:N/A:0): vendor ID is NAT-T v2
*Mar 1 04:49:24.906: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 12.1.1.1
*Mar 1 04:49:24.910: ISAKMP:(0:0:N/A:0): local preshared key found
*Mar 1 04:49:24.910: ISAKMP : Scanning profiles for xauth ...
*Mar 1 04:49:24.910: ISAKMP:(0:0:N/A:0):Checking ISAKMP transform 1 against priority 10 policy >>>检查我们配置的isakmp policy 10
*Mar 1 04:49:24.910: ISAKMP: encryption 3DES-CBC
*Mar 1 04:49:24.910: ISAKMP: hash SHA
*Mar 1 04:49:24.914: ISAKMP: default group 2
*Mar 1 04:49:24.914: ISAKMP: auth pre-share
*Mar 1 04:49:24.914: ISAKMP: life type in seconds
*Mar 1 04:49:24.914: ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x80
*Mar 1 04:49:24.914: ISAKMP:(0:0:N/A:0):atts are acceptable. Next payload is 0
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 1 04:49:24.946: ISAKMP (0:134217729): vendor ID is NAT-T v7
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1): vendor ID seems Unity/DPD but major 157 mismatch
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1): vendor ID is NAT-T v3
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1): vendor ID seems Unity/DPD but major 123 mismatch
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1): vendor ID is NAT-T v2
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM1 New State = IKE_R_MM1
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1): constructed NAT-T vendor-07 ID
*Mar 1 04:49:24.946: ISAKMP:(0:1:SW:1): sending packet to 12.1.1.1 my_port 500 peer_port 500 (R) MM_SA_SETUP
*Mar 1 04:49:24.950: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 1 04:49:24.950: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM1 New State = IKE_R_MM2
*Mar 1 04:49:25.046: ISAKMP (0:134217729): received packet from 12.1.1.1 dport 500 sport 500 Global (R) MM_SA_SETUP
*Mar 1 04:49:25.046: ISAKMP:(0:1:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 1 04:49:25.050: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM2 New State = IKE_R_MM3
*Mar 1 04:49:25.054: ISAKMP:(0:1:SW:1): processing KE payload. message ID = 0
*Mar 1 04:49:25.086: ISAKMP:(0:1:SW:1): processing NONCE payload. message ID = 0
*Mar 1 04:49:25.086: ISAKMP:(0:1:SW:1):found peer pre-shared key matching 12.1.1.1
*Mar 1 04:49:25.090: ISAKMP:(0:1:SW:1):SKEYID state generated
*Mar 1 04:49:25.090: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 04:49:25.090: ISAKMP:(0:1:SW:1): vendor ID is Unity
*Mar 1 04:49:25.094: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 04:49:25.094: ISAKMP:(0:1:SW:1): vendor ID is DPD
*Mar 1 04:49:25.094: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 04:49:25.094: ISAKMP:(0:1:SW:1): speaking to another IOS box!
*Mar 1 04:49:25.098: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 1 04:49:25.098: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM3 New State = IKE_R_MM3
*Mar 1 04:49:25.102: ISAKMP:(0:1:SW:1): sending packet to 12.1.1.1 my_port 500 peer_port 500 (R) MM_KEY_EXCH
*Mar 1 04:49:25.102: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 1 04:49:25.102: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM3 New State = IKE_R_MM4
*Mar 1 04:49:25.154: ISAKMP (0:134217729): received packet from 12.1.1.1 dport 500 sport 500 Global (R) MM_KEY_EXCH
*Mar 1 04:49:25.158: ISAKMP:(0:1:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 1 04:49:25.158: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM4 New State = IKE_R_MM5
*Mar 1 04:49:25.162: ISAKMP:(0:1:SW:1): processing ID payload. message ID = 0
*Mar 1 04:49:25.166: ISAKMP (0:134217729): ID payload
next-payload : 8
type : 1
address : 12.1.1.1
protocol : 17
port : 500
length : 12
*Mar 1 04:49:25.166: ISAKMP:(0:1:SW:1):: peer matches *none* of the profiles
*Mar 1 04:49:25.166: ISAKMP:(0:1:SW:1): processing HASH payload. message ID = 0
*Mar 1 04:49:25.170: ISAKMP:(0:1:SW:1): processing NOTIFY INITIAL_CONTACT protocol 1
spi 0, message ID = 0, sa = 646DD604
*Mar 1 04:49:25.170: ISAKMP:(0:1:SW:1):SA authentication status:
authenticated
*Mar 1 04:49:25.174: ISAKMP:(0:1:SW:1): Process initial contact,
bring down existing phase 1 and 2 SA's with local 12.1.1.2 remote 12.1.1.1 remote port 500
*Mar 1 04:49:25.174: ISAKMP:(0:1:SW:1):SA authentication status:
authenticated
*Mar 1 04:49:25.178: ISAKMP:(0:1:SW:1):SA has been authenticated with 12.1.1.1
*Mar 1 04:49:25.178: ISAKMP: Trying to insert a peer 12.1.1.2/12.1.1.1/500/, and inserted successfully 64F66BC4.
*Mar 1 04:49:25.178: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 1 04:49:25.182: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM5 New State = IKE_R_MM5
*Mar 1 04:49:25.182: IPSEC(key_engine): got a queue event with 1 kei messages
*Mar 1 04:49:25.186: ISAKMP:(0:1:SW:1):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
*Mar 1 04:49:25.186: ISAKMP (0:134217729): ID payload
next-payload : 8
type : 1
address : 12.1.1.2
protocol : 17
port : 500
length : 12
*Mar 1 04:49:25.190: ISAKMP:(0:1:SW:1):Total payload length: 12
*Mar 1 04:49:25.194: ISAKMP:(0:1:SW:1): sending packet to 12.1.1.1 my_port 500 peer_port 500 (R) MM_KEY_EXCH
*Mar 1 04:49:25.198: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 1 04:49:25.198: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM5 New State = IKE_P1_COMPLETE
*Mar 1 04:49:25.202: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
*Mar 1 04:49:25.202: ISAKMP:(0:1:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
第二阶段:
*Mar 1 04:49:25.266: ISAKMP (0:134217729): received packet from 12.1.1.1 dport 500 sport 500 Global (R) QM_IDLE
*Mar 1 04:49:25.266: ISAKMP: set new node 1812581365 to QM_IDLE
*Mar 1 04:49:25.270: ISAKMP:(0:1:SW:1): processing HASH payload. message ID = 1812581365
*Mar 1 04:49:25.274: ISAKMP:(0:1:SW:1): processing SA payload. message ID = 1812581365
*Mar 1 04:49:25.274: ISAKMP:(0:1:SW:1):Checking IPSec proposal 1
*Mar 1 04:49:25.274: ISAKMP: transform 1, ESP_3DES
*Mar 1 04:49:25.274: ISAKMP: attributes in transform:
*Mar 1 04:49:25.274: ISAKMP: encaps is 1 (Tunnel)
*Mar 1 04:49:25.278: ISAKMP: SA life type in seconds
*Mar 1 04:49:25.278: ISAKMP: SA life duration (basic) of 3600
*Mar 1 04:49:25.278: ISAKMP: SA life type in kilobytes
*Mar 1 04:49:25.278: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
*Mar 1 04:49:25.278: ISAKMP: authenticator is HMAC-MD5
*Mar 1 04:49:25.282: ISAKMP:(0:1:SW:1):atts are acceptable.
*Mar 1 04:49:25.282: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 12.1.1.2, remote= 12.1.1.1,
local_proxy= 2.2.2.0/255.255.255.0/0/0 (type=4),
remote_proxy= 1.1.1.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac (Tunnel),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x2
*Mar 1 04:49:25.286: Crypto mapdb : proxy_match
src addr : 2.2.2.0
dst addr : 1.1.1.0
protocol : 0
src port : 0
dst port : 0
*Mar 1 04:49:25.290: ISAKMP:(0:1:SW:1): processing NONCE payload. message ID = 1812581365
*Mar 1 04:49:25.290: ISAKMP:(0:1:SW:1): processing ID payload. message ID = 1812581365
*Mar 1 04:49:25.290: ISAKMP:(0:1:SW:1): processing ID payload. message ID = 1812581365
*Mar 1 04:49:25.290: ISAKMP:(0:1:SW:1): asking for 1 spis from ipsec
*Mar 1 04:49:25.290: ISAKMP:(0:1:SW:1):Node 1812581365, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
*Mar 1 04:49:25.290: ISAKMP:(0:1:SW:1):Old State = IKE_QM_READY New State = IKE_QM_SPI_STARVE
*Mar 1 04:49:25.290: IPSEC(key_engine): got a queue event with 1 kei messages
*Mar 1 04:49:25.290: IPSEC(spi_response): getting spi 2345636103 for SA
from 12.1.1.2 to 12.1.1.1 for prot 3
*Mar 1 04:49:25.290: ISAKMP: received ke message (2/1)
*Mar 1 04:49:25.290: ISAKMP: Locking peer struct 0x64F66BC4, IPSEC refcount 1 for for stuff_ke
*Mar 1 04:49:25.290: ISAKMP:(0:1:SW:1): Creating IPSec SAs
*Mar 1 04:49:25.290: inbound SA from 12.1.1.1 to 12.1.1.2 (f/i) 0/ 0
(proxy 1.1.1.0 to 2.2.2.0)
*Mar 1 04:49:25.290: has spi 0x8BCF9107 and conn_id 0 and flags 2
*Mar 1 04:49:25.290: lifetime of 3600 seconds
*Mar 1 04:49:25.290: lifetime of 4608000 kilobytes
*Mar 1 04:49:25.290: has client flags 0x0
*Mar 1 04:49:25.290: outbound SA from 12.1.1.2 to 12.1.1.1 (f/i) 0/0
(proxy 2.2.2.0 to 1.1.1.0)
*Mar 1 04:49:25.290: has spi 685105074 and conn_id 0 and flags A
*Mar 1 04:49:25.290: lifetime of 3600 seconds
*Mar 1 04:49:25.290: lifetime of 4608000 kilobytes
*Mar 1 04:49:25.290: has client flags 0x0
*Mar 1 04:49:25.290: ISAKMP:(0:1:SW:1): sending packet to 12.1.1.1 my_port 500 peer_port 500 (R) QM_IDLE
*Mar 1 04:49:25.290: ISAKMP:(0:1:SW:1):Node 1812581365, Input = IKE_MESG_FROM_IPSEC, IKE_SPI_REPLY
*Mar 1 04:49:25.294: ISAKMP:(0:1:SW:1):Old State = IKE_QM_SPI_STARVE New State = IKE_QM_R_QM2
*Mar 1 04:49:25.294: IPSEC(key_engine): got a queue event with 2 kei messages
*Mar 1 04:49:25.298: IPSEC(initialize_sas): ,
(key eng. msg.) INBOUND local= 12.1.1.2, remote= 12.1.1.1,
local_proxy= 2.2.2.0/255.255.255.0/0/0 (type=4),
remote_proxy= 1.1.1.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x8BCF9107(2345636103), conn_id= 0, keysize= 0, flags= 0x2
*Mar 1 04:49:25.302: IPSEC(initialize_sas): ,
(key eng. msg.) OUTBOUND local= 12.1.1.2, remote= 12.1.1.1,
local_proxy= 2.2.2.0/255.255.255.0/0/0 (type=4),
remote_proxy= 1.1.1.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x28D5DFB2(685105074), conn_id= 0, keysize= 0, flags= 0xA
*Mar 1 04:49:25.306: Crypto mapdb : proxy_match
src addr : 2.2.2.0
dst addr : 1.1.1.0
protocol : 0
src port : 0
dst port : 0
*Mar 1 04:49:25.306: IPSEC(crypto_ipsec_sa_find_ident_head): reconnecting with the same proxies and 12.1.1.1
*Mar 1 04:49:25.306: IPSec: Flow_switching Allocated flow for sibling 8000000B
*Mar 1 04:49:25.310: IPSEC(policy_db_add_ident): src 2.2.2.0, dest 1.1.1.0, dest_port 0
*Mar 1 04:49:25.310: ISAKMP: Locking peer struct 0x64F66BC4, IPSEC refcount 2 for from create_transforms
*Mar 1 04:49:25.310: IPSEC(create_sa): sa created,
(sa) sa_dest= 12.1.1.2, sa_proto= 50,
sa_spi= 0x8BCF9107(2345636103),
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 2003
*Mar 1 04:49:25.314: IPSEC(create_sa): sa created,
(sa) sa_dest= 12.1.1.1, sa_proto= 50,
sa_spi= 0x28D5DFB2(685105074),
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 2002
*Mar 1 04:49:25.314: ISAKMP: Unlocking IPSEC struct 0x64F66BC4 from create_transforms, count 1
*Mar 1 04:49:25.374: ISAKMP (0:134217729): received packet from 12.1.1.1 dport 500 sport 500 Global (R) QM_IDLE
*Mar 1 04:49:25.378: ISAKMP:(0:1:SW:1):deleting node 1812581365 error FALSE reason "QM done (await)"
*Mar 1 04:49:25.378: ISAKMP:(0:1:SW:1):Node 1812581365, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
*Mar 1 04:49:25.382: ISAKMP:(0:1:SW:1):Old State = IKE_QM_R_QM2 New State = IKE_QM_PHASE2_COMPLETE
*Mar 1 04:49:25.382: IPSEC(key_engine): got a queue event with 1 kei messages
*Mar 1 04:49:25.386: IPSEC(key_engine_enable_outbound): rec'd enable notify from ISAKMP
*Mar 1 04:49:25.386: IPSEC(key_engine_enable_outbound): enable SA with spi 685105074/50
5、报文抓取:【在R2的E0/0抓取的报文】
主模式1-6个包,快速模式1-3个包
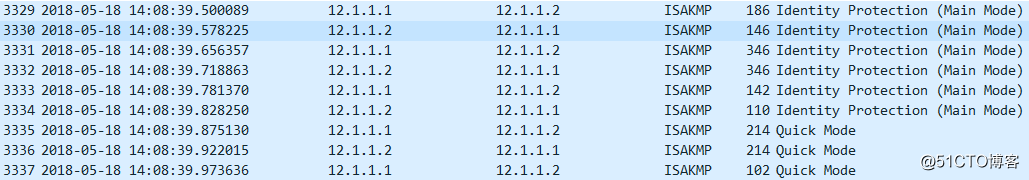
第一个报文SA内容:R1-R2交互crypto isakmp policy 10配置的加密,校验,DH组等参数。
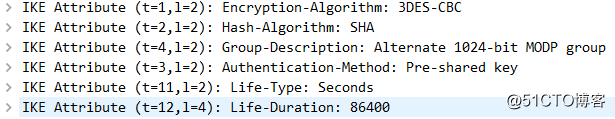
第二个报文SA内容:R2-R1,1-2个包中的这些信息一致
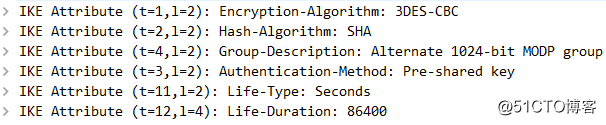
第三个报文Key Exchange、Vendor ID【CISCO-UNITY;DPD;XAUTH】、NAT-Discovery:R1-R2,主要交互密钥资源,以便为5-6包提供安全算法所需密钥
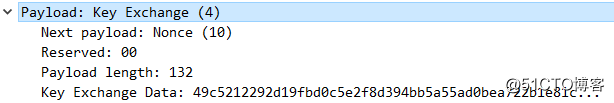
第四个报文:R2-R1,格式内容和第三个报文一样
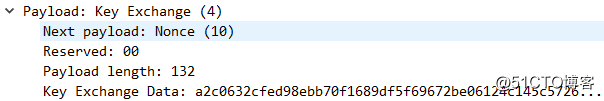
第五个报文:R1-R2,传递的是加密的数据,5-6报文都是在加密的环境中传输的
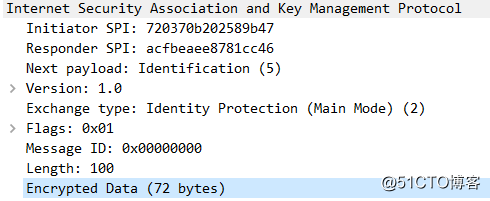
第六个报文:R2-R1
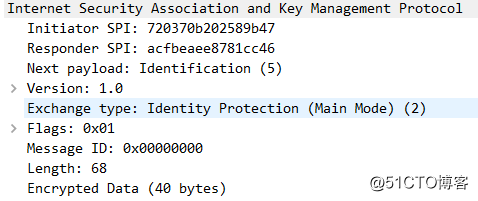
快速模式的1-3个报文【R1-R2,R2-R1,R1-R2】
QM-1:
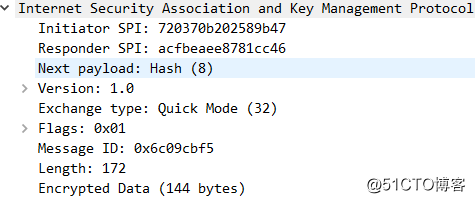
QM-2:
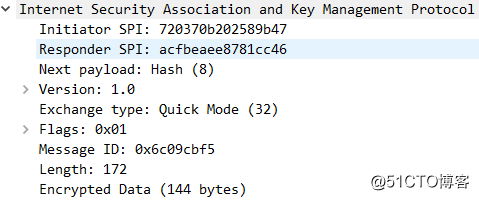
QM-3:
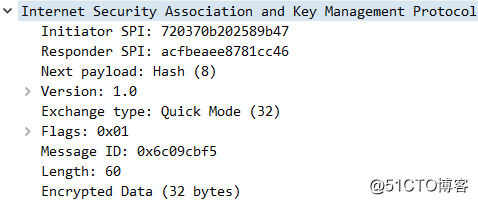
6、我们验证一下建立后的情况
R1#sho crypto engine connections active
ID Interface IP-Address State Algorithm Encrypt Decrypt
2 Ethernet0/0 12.1.1.1 set HMAC_SHA+3DES_56_C 0 0
2001 Ethernet0/0 12.1.1.1 set 3DES+MD5 4 0
2004 Ethernet0/0 12.1.1.1 set 3DES+MD5 0 4
R1#show crypto isakmp sa
dst src state conn-id slot status
12.1.1.2 12.1.1.1 QM_IDLE 2 0 ACTIVE
R1#show crypto ipsec sa
interface: Ethernet0/0
Crypto map tag: cisco, local addr 12.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (2.2.2.0/255.255.255.0/0/0)
current_peer 12.1.1.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 12.1.1.1, remote crypto endpt.: 12.1.1.2
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0x50B82D9A(1354247578)
inbound esp sas:
spi: 0x777B0338(2004550456)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2004, flow_id: SW:4, crypto map: cisco
sa timing: remaining key lifetime (k/sec): (4391758/3437)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x50B82D9A(1354247578)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: cisco
sa timing: remaining key lifetime (k/sec): (4391758/3436)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
ACl匹配情况:
R1#sho access-lists
Extended IP access list nat
10 deny ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255 (5 matches)
20 permit ip any any (2 matches)
Extended IP access list vpn
10 permit ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255 (9 matches)
可以ping公网上的地址:
R1#ping 12.1.1.2 so lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 12.1.1.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/22/32 ms
R1#sho acce
R1#sho access-l
R1#sho access-lists
Extended IP access list nat
10 deny ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255 (5 matches)
20 permit ip any any (3 matches) >>>>匹配了一个去做NAT
Extended IP access list vpn
10 permit ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255 (9 matches)
R1#sho
R1#show ip nat tr
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 12.1.1.1:23 1.1.1.1:23 12.1.1.2:23 12.1.1.2:23