1. What is a hacker?
Hackers generally refer to computer experts who focus on infiltration and stealing attack technology in IT technology. At this stage, hackers need to master far more than these.

2. Why learn hacking technology?
In fact, network information space security has become the fourth largest battlefield after sea, land and air. In addition to the game between countries, there are also obvious competitions between domestic enterprises and enterprises.
Network security hacking technology is one of the capabilities that both countries and enterprises are paying more and more attention to.
So if you are still considering whether to learn, my answer is: just learn, you are right
3. How to learn network security (hacking technology)?
Phase 1: Security Basics
Cybersecurity Industry and Regulations
Linux operating system
computer network
HTML PHP Mysql Python basics to practical mastery
Phase Two: Information Gathering
IP information collection
Domain name information collection
Server Information Collection
Web site information collection
Google hacking
Fofa Network Security Mapping
Phase Three: Web Security
SQL injection vulnerability
XSS
CSRF vulnerability
File Upload Vulnerability
file contains bug
SSRF vulnerability
XXE vulnerability
Remote Code Execution Vulnerabilities
Password Brute Force Cracking and Defense
Middleware Parsing Vulnerabilities
Deserialization Vulnerabilities
Stage Four: Penetration Tools
MSF
Cobalt strike
Burp suite
Nessus Appscea AWVS
Goby XRay
Sqlmap
Nmap
Kali
The fifth stage: actual combat digging
Vulnerability mining skills
Src
Cnvd
Crowdtest project
Recurrence of popular CVE vulnerabilities
Shooting Range Combat
Network Security (Hacking Technology) Learning Roadmap
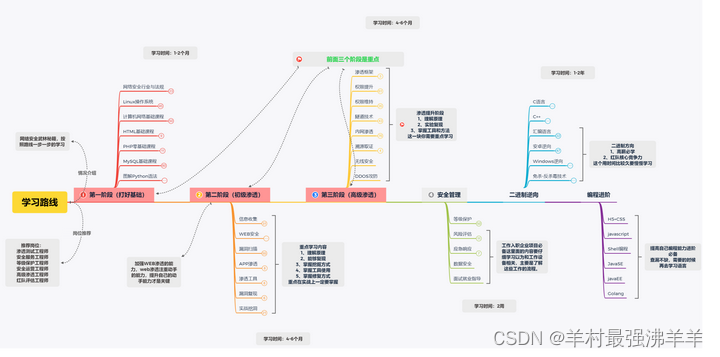
All knowledge point materials within the framework of the learning route - will be sent automatically after following the blogger !
 statement:
statement:
Pure technical teaching sharing! The purpose of this tutorial is to awaken everyone's attention to network security and take corresponding security measures to reduce the economic losses caused by network security, and not to bear criminal responsibility for all aspects of technology abuse.