sherlock
附件是一本书的内容,发现其中有些字母莫名地大写

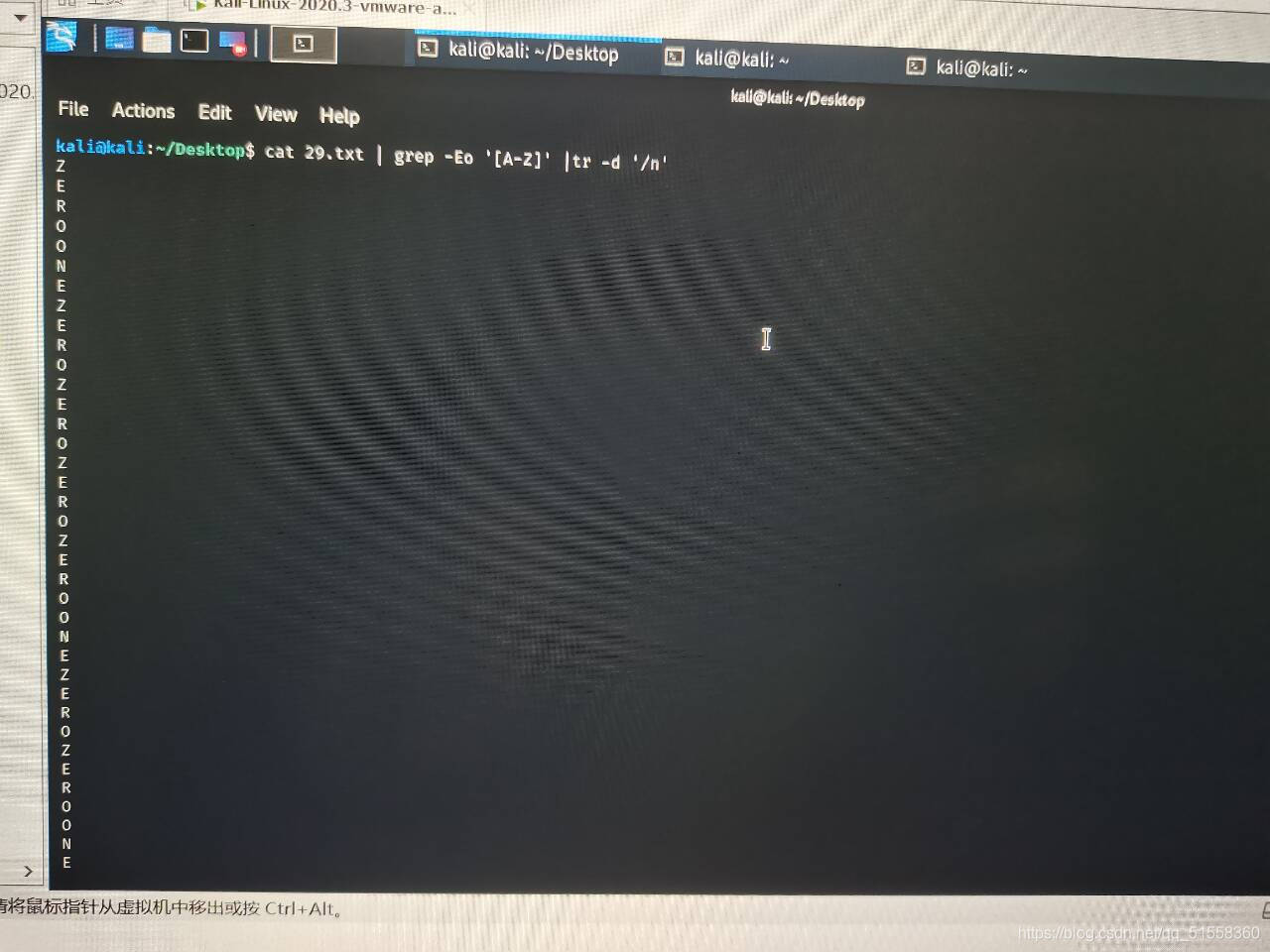
利用命令cat 文件名 | grep -Eo ‘[A-Z]’ |tr -d '\n’将大写字母提取出来
cat 29.txt | grep -Eo '[A-Z]' |tr -d '\n'
(语言为Linux的bash)
或者用脚本:
#include <iostream>
#include <fstream>
using namespace std;
int main()
{
fstream infile;
infile.open("29.txt");
char ch;
while (!infile.eof())
{
infile.get(ch);
if (ch >= 'A' && ch < 'Z')
cout << ch;
}
infile.close();
return 0;
}
得:
ZEROONEZEROZEROZEROZEROONEZEROZEROONEZEROZEROONEZEROZEROONEZEROONEZEROONEZEROONEZEROZEROZEROONEZEROONEZEROZEROONEONEZEROONEZEROZEROZEROZEROONEONEZEROONEZEROONEZEROONEZEROZEROZEROONEZEROZEROZEROONEONEZEROZEROONEONEONEONEZEROONEONEZEROONEONEZEROONEZEROZEROZEROZEROZEROONEONEZEROZEROZEROONEZEROONEONEZEROZEROONEZEROZEROZEROZEROONEONEZEROZEROONEONEZEROONEZEROONEONEONEONEONEZEROZEROONEONEZEROZEROZEROONEZEROONEONEZEROONEONEONEZEROZEROONEZEROONEONEONEONEONEZEROONEONEONEZEROZEROZEROZEROZEROONEONEZEROONEONEZEROZEROZEROZEROONEONEZEROONEZEROZEROZEROZEROONEONEZEROZEROZEROONEZEROONEONEZEROONEONEONEZEROZEROONEZEROONEONEONEONEONEZEROZEROONEONEZEROONEZEROONEZEROZEROONEONEZEROZEROZEROONEZEROZEROONEONEZEROONEONEONEZEROZEROONEONEZEROZEROONEONEZEROONEONEONEONEONEZEROONE
是英文的0和1,哈哈哈。将ZERO用0替代,ONE用1替代(在虚拟机用^C命令即可替换)
得:
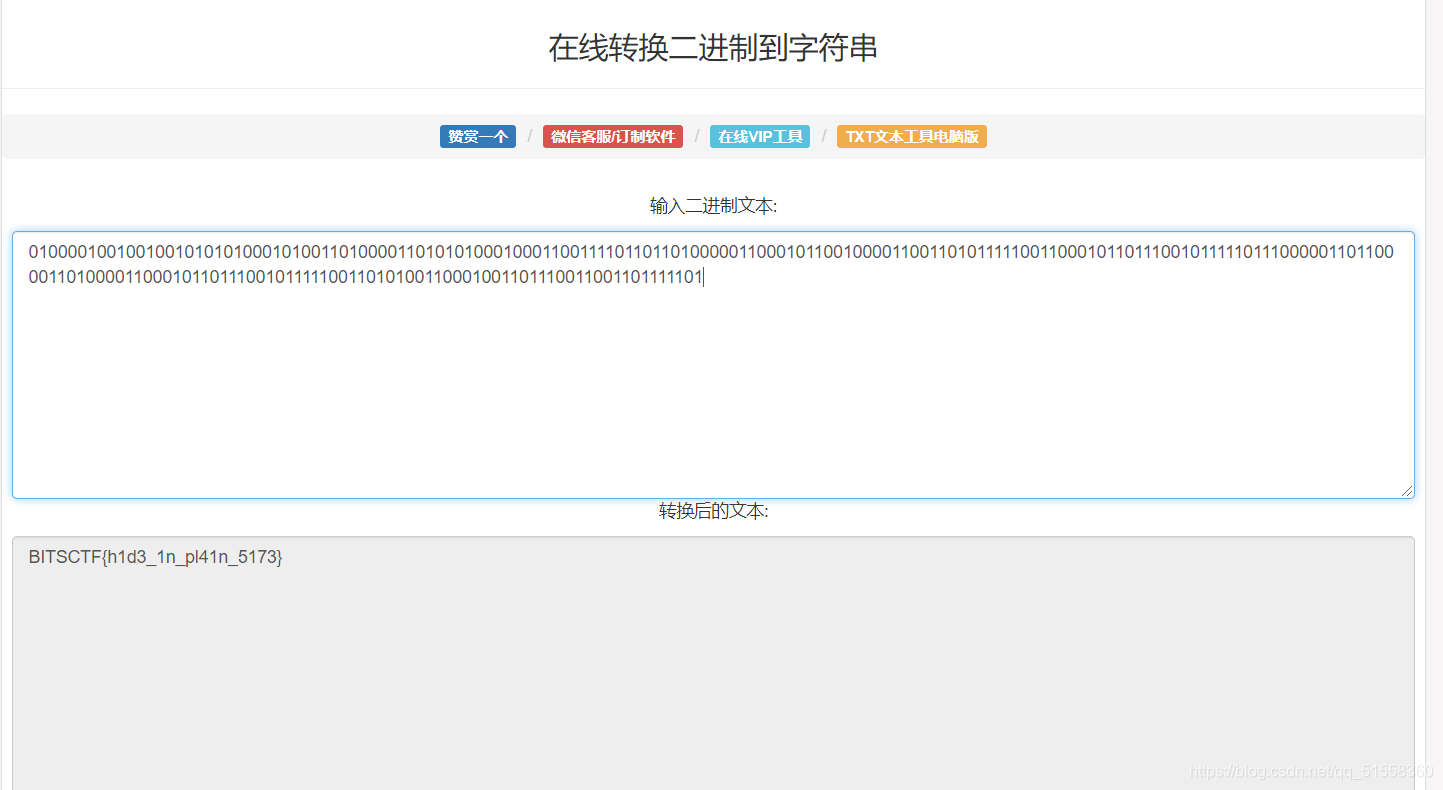
010000100100100101010100010100110100001101010100010001100111101101101000001100010110010000110011010111110011000101101110010111110111000001101100001101000011000101101110010111110011010100110001001101110011001101111101
然后再转换:
补充知识:
用法: grep [选项]… 模式 [文件]…
-E, --extended-regexp <模式> 是扩展正则表达式
-o, --only-matching 只显示行中非空匹配部分
[] #匹配一个指定范围内的字符,如’[Gg]rep’匹配Grep和grep。
用法:tr [选项]… SET1 [SET2]
-d, --delete delete characters in SET1, do not translate
#删除SET1中的字符,不进行翻译
\n 换行
cr3-what-is-this-encryption
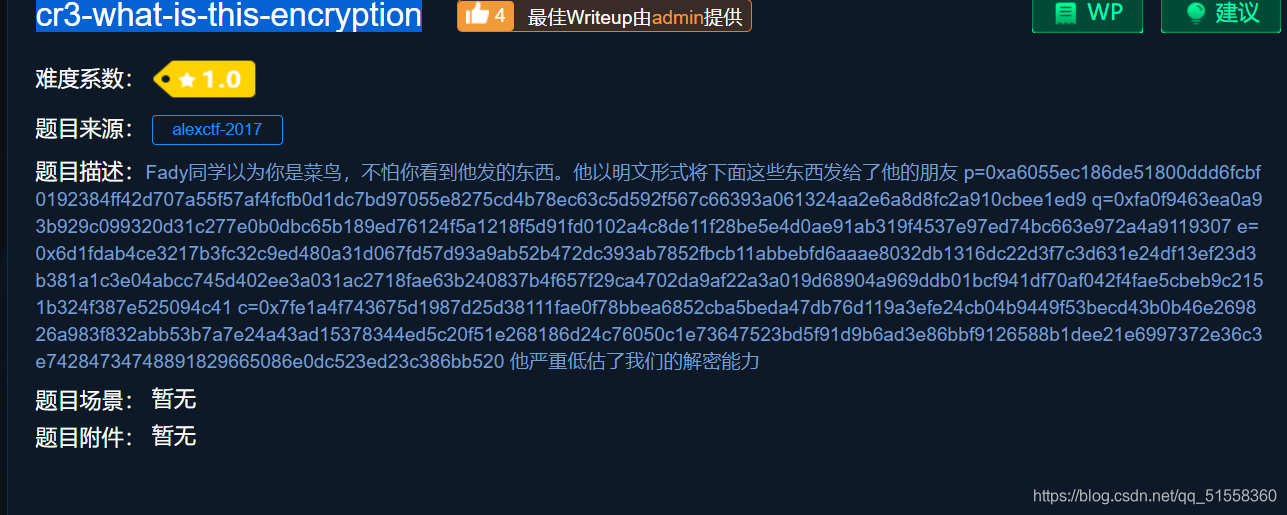
看到题目中的p,q,e,就想到了RSA加密
大致思路:
先把p,q,e转成十进制,再根据公式求出n,d,m
n=p*q
φ(N) = (p-1)(q-1)
e * d % φ(N) = 1(d是私钥,e是公钥)
m=c^ d mod n (m是明文)
import libnum
from Crypto.Util.number import long_to_bytes
q = int("0xa6055ec186de51800ddd6fcbf0192384ff42d707a55f57af4fcfb0d1dc7bd97055e8275cd4b78ec63c5d592f567c66393a061324aa2e6a8d8fc2a910cbee1ed9",16)
p = int("0xfa0f9463ea0a93b929c099320d31c277e0b0dbc65b189ed76124f5a1218f5d91fd0102a4c8de11f28be5e4d0ae91ab319f4537e97ed74bc663e972a4a9119307",16)
e = int("0x6d1fdab4ce3217b3fc32c9ed480a31d067fd57d93a9ab52b472dc393ab7852fbcb11abbebfd6aaae8032db1316dc22d3f7c3d631e24df13ef23d3b381a1c3e04abcc745d402ee3a031ac2718fae63b240837b4f657f29ca4702da9af22a3a019d68904a969ddb01bcf941df70af042f4fae5cbeb9c2151b324f387e525094c41",16)
c = 0x7fe1a4f743675d1987d25d38111fae0f78bbea6852cba5beda47db76d119a3efe24cb04b9449f53becd43b0b46e269826a983f832abb53b7a7e24a43ad15378344ed5c20f51e268186d24c76050c1e73647523bd5f91d9b6ad3e86bbf9126588b1dee21e6997372e36c3e74284734748891829665086e0dc523ed23c386bb520
n = q*p
d = libnum.invmod(e, (p - 1) * (q - 1))
m = pow(c, d, n) # m 的十进制形式
string = long_to_bytes(m) # m明文
print(string) # 结果为 b‘ m ’ 的形式
flag_in_your_hand
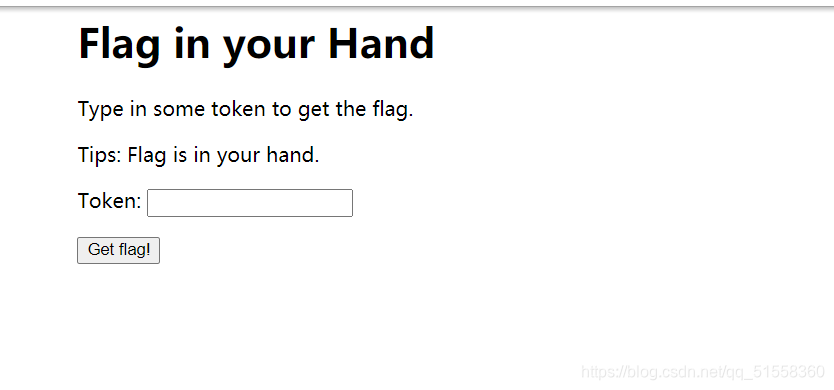
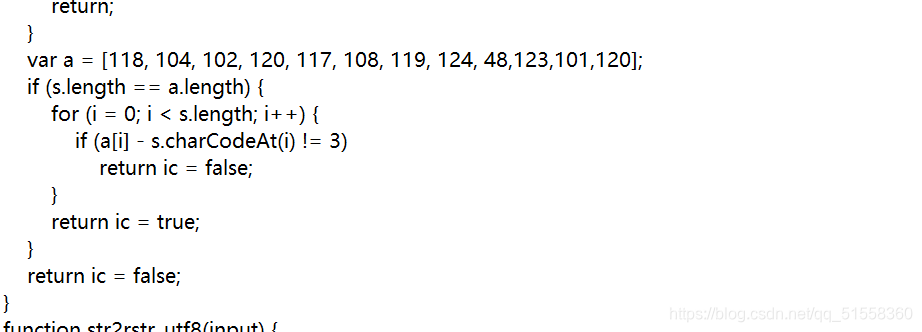
数组a 尝试用ASCII码转换解出
115 101 99 117 114 105 116 121 45 120 98 117
security
告诉你个秘密
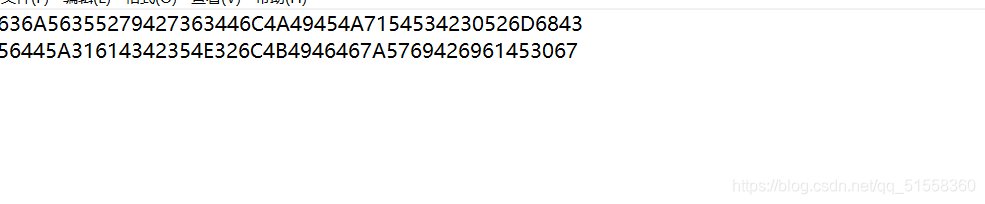
一看是十六进制,先转成ASCII码
cjV5RyBscDlJIEJqTSB0RmhCVDZ1aCB5N2lKIFFzWiBiaE0g
看样子像base64加密。我们试着base64解密。
r5yG lp9I BjM tFhBT6uh y7iJ QsZ bhM
得到七段字符,在键盘上发现每段字符包围着一个字母,这些字母就是flag了
TONGYUAN
Broadcast
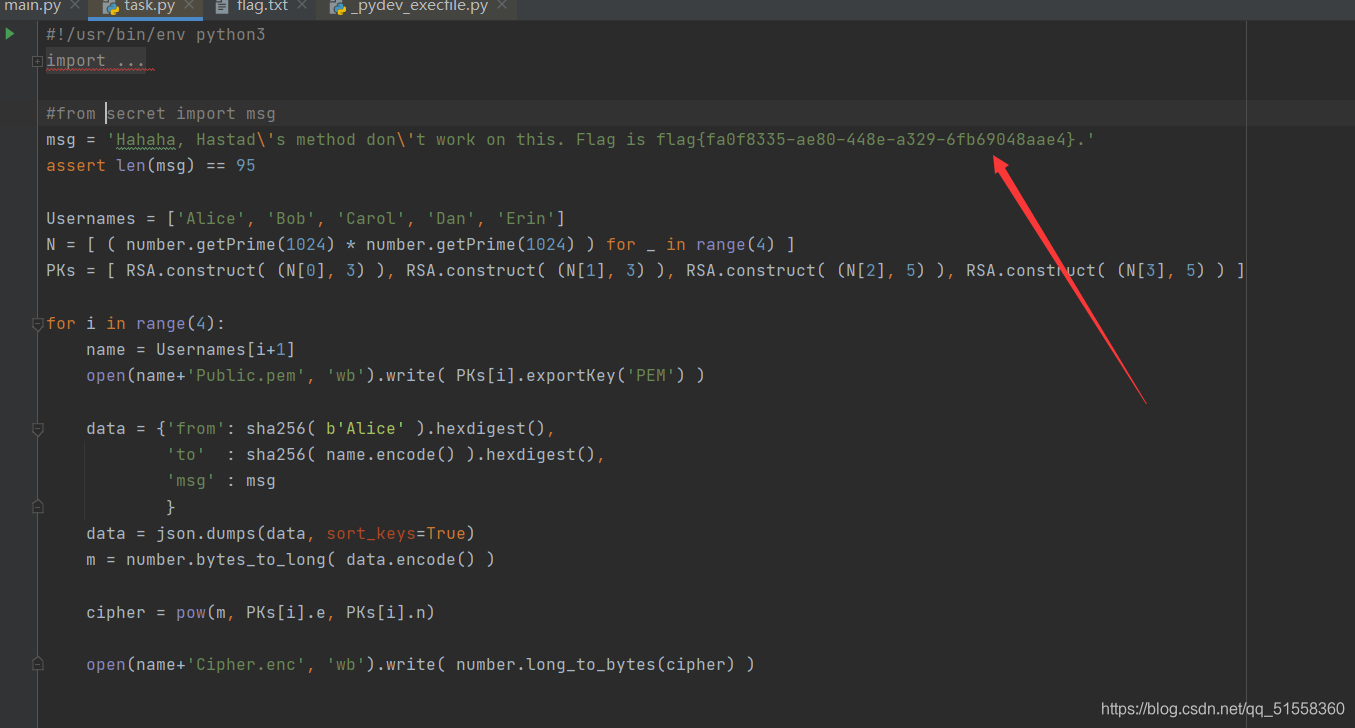
直接把flag写在代码里了
工业协议分析2
用wireshark打开pcapng文件,发现存在大量UDP流量包,大部分UDP流量包的长度相同,只有一些长度的UDP流量包仅出现过一次,猜测它们可能有异常。
查看这些流量包,发现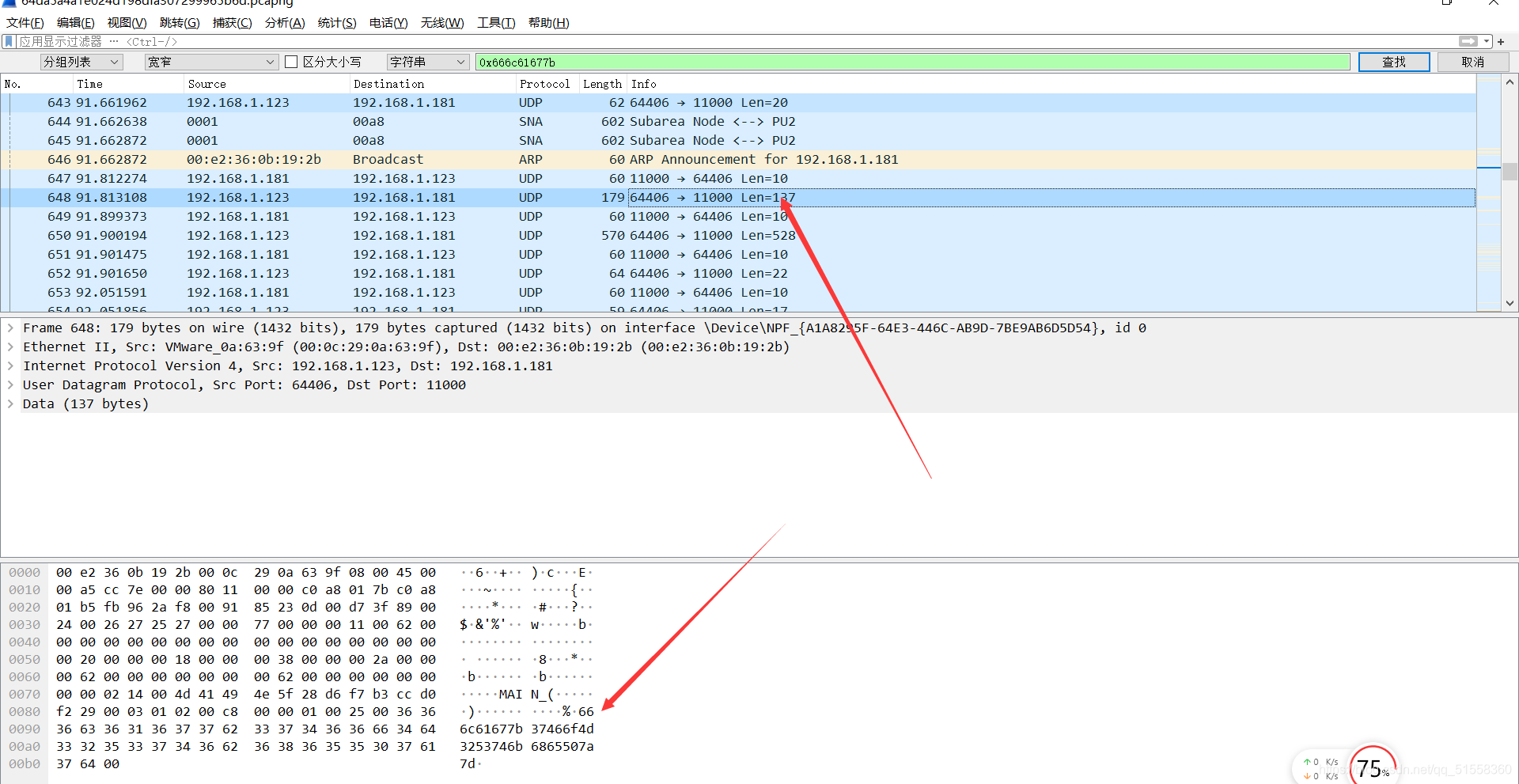
将该字符串提取出来:
666c61677b37466f4d3253746b6865507a7d
发现最大不超过F,猜测是16进制,将其转成字符串,得到flag:

你猜猜
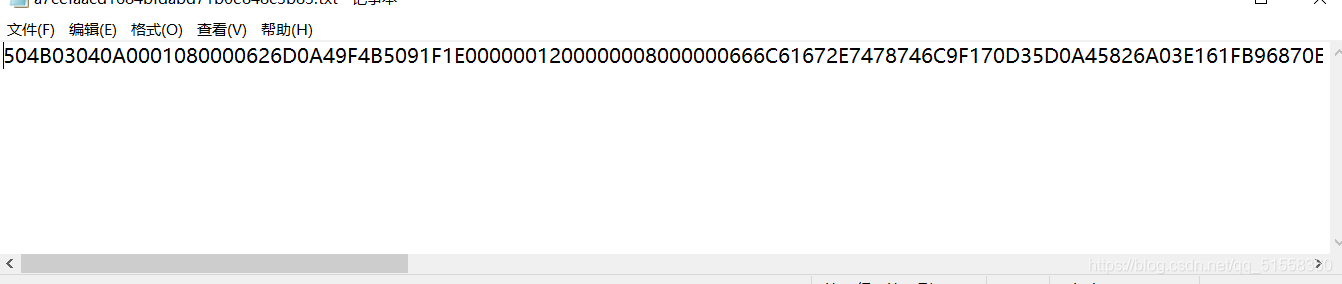
拿到文件后,发现是504B0304开头的。这是zip文件头,打开winhex,将那段16进制复制进去,选择ASCⅠⅠ HEX
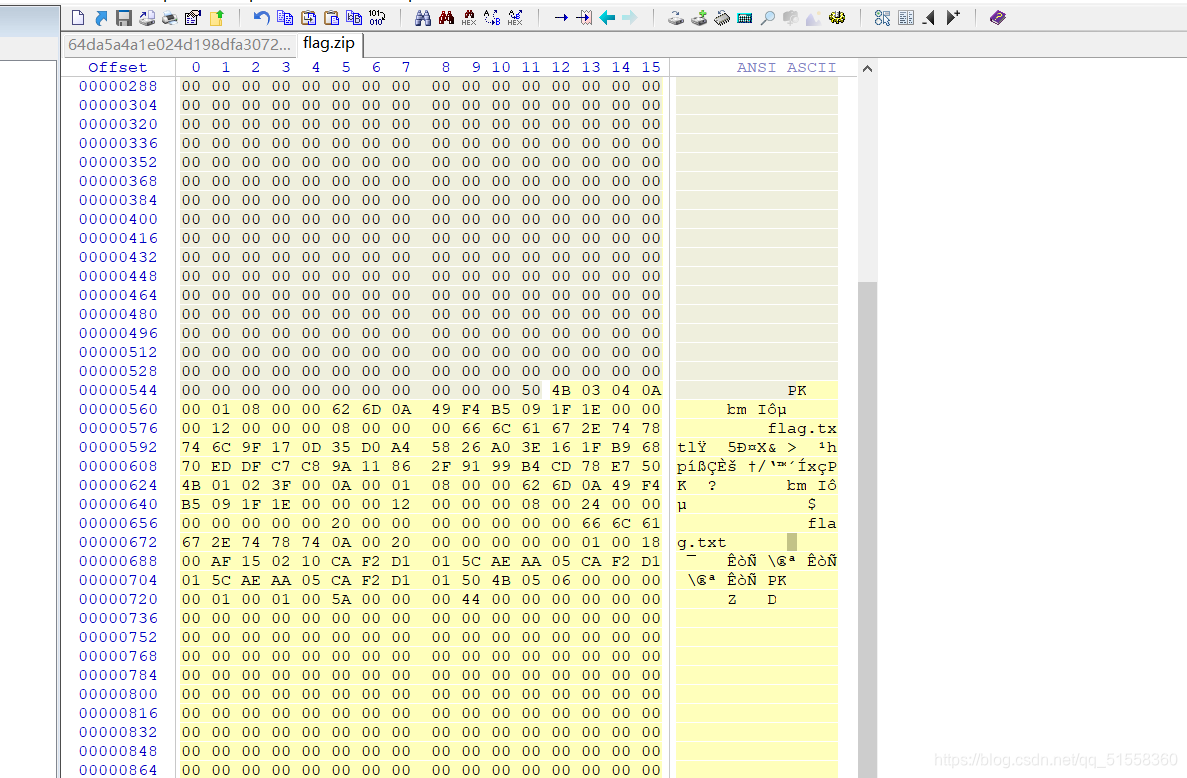
保存该文件得到一个压缩包flag.zip。打开后发现有密码。
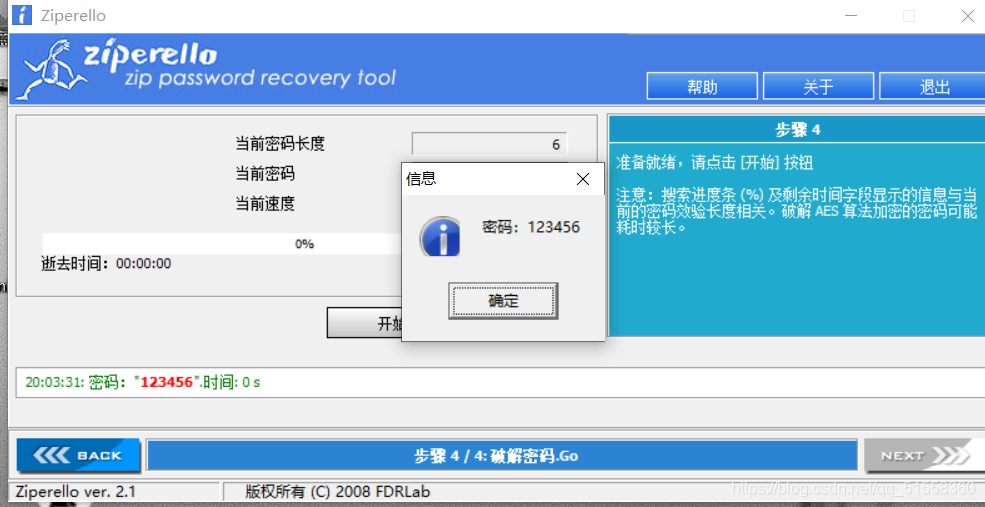
用Ziperello破解,得到密码为123456
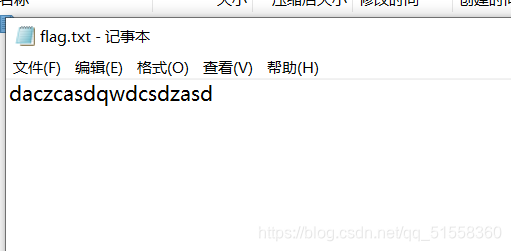
banana-princess
得到一个pdf
但是打不开
扔进winhex
发现开头是%CQS-1.5
而我拿一个正常的pdf是%PDF-1.7
形式完全一样啊,数字可以理解为版本号。那就思路来了,估计是进行了位移?尝试后发现: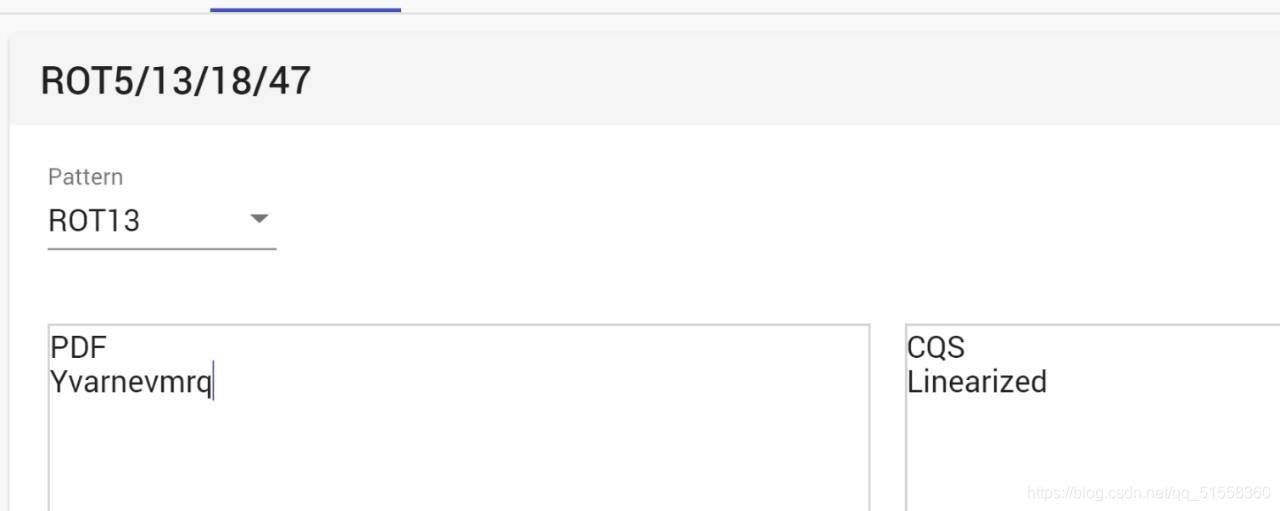
cat 1.pdf | tr 'A-Za-z' 'N-ZA-Mn-za-m' > 2.pdf
得到一个2.pdf

flag被遮掩了
用在线工具将pdf转成html 在线工具下载压缩包,解压
发现有两张照片,其中一张就含有flag

safer-than-rot13
解压得到 cry100文件,复制文件内容尝试进行 rot13解密,没发现什么
在尝试 词频分析,利用在线工具:https://quipqiup.com/

得到flag:no this is not crypto my dear
但格式搞了一会儿
要把空格改为下划线no_this_is_not_crypto_my_dear