RPC调用的大坑:变量要定义var,调用的方法名不要用大写的字母!!!return,send的拼写
先通过Fdex2进行脱壳,将脱壳后后的dex导出到电脑用JADX进行分析
大坑:手机导出dex到电脑要先将文件cope到sdcard目录下
cp com.tianyancha.skyeye7500600.dex /sdcard
adb pull sdcard/com.tianyancha.skyeye7500600.dex E:/for_cd
fiddler抓包,发现有变化的请求参数tyc-hi和Authorization
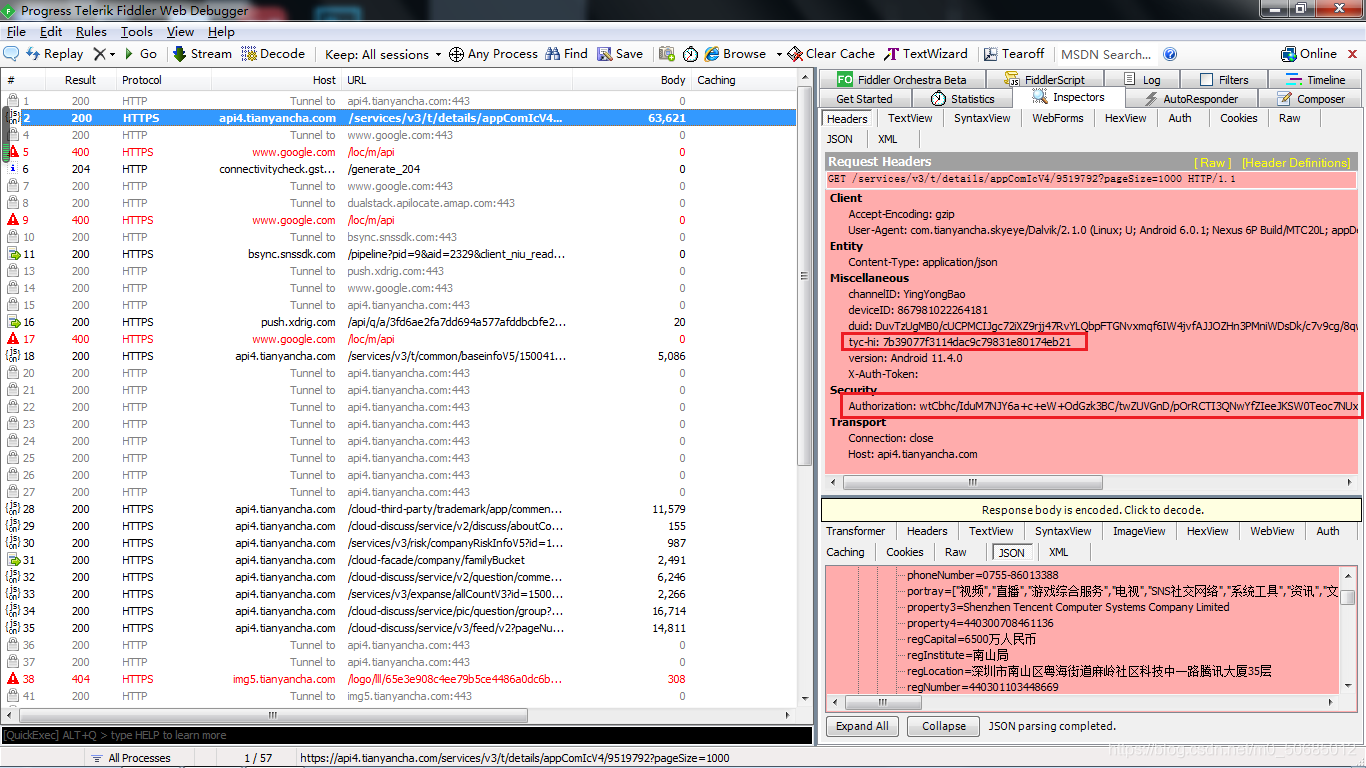
JADX打开脱壳后的dex文件进行分析
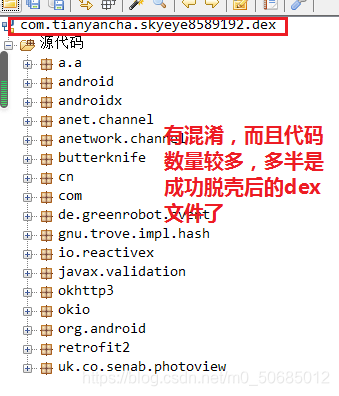
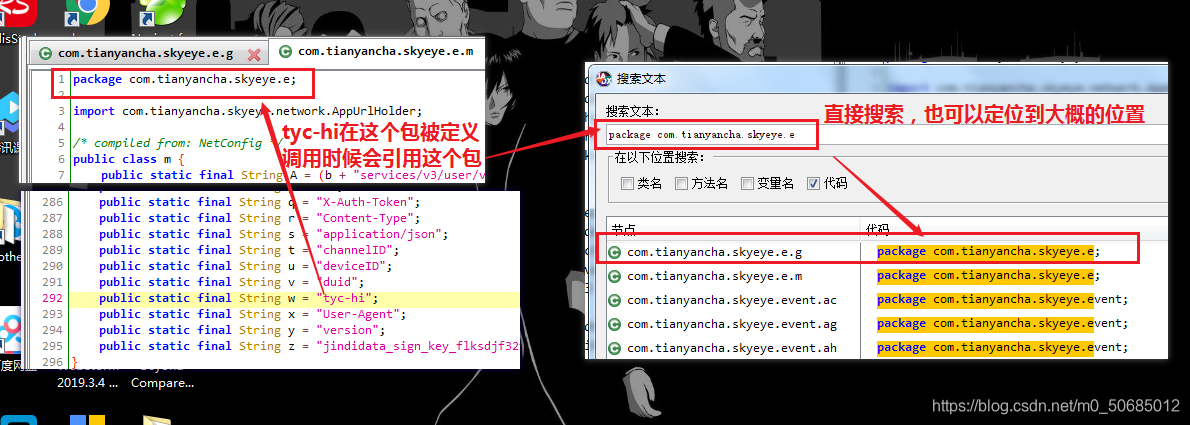
首先直接上技巧搜索大法
- 首先直接搜tyc-hi
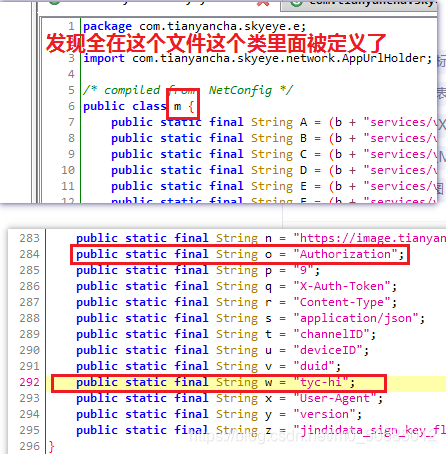
- 搜索
.w
.w =
.w,
m.w
# 可疑位置
m.w,
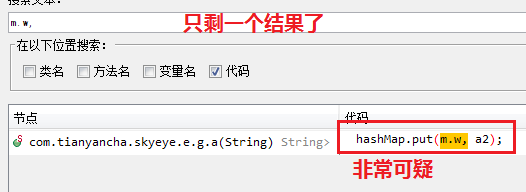
我的有趣的搜索方法
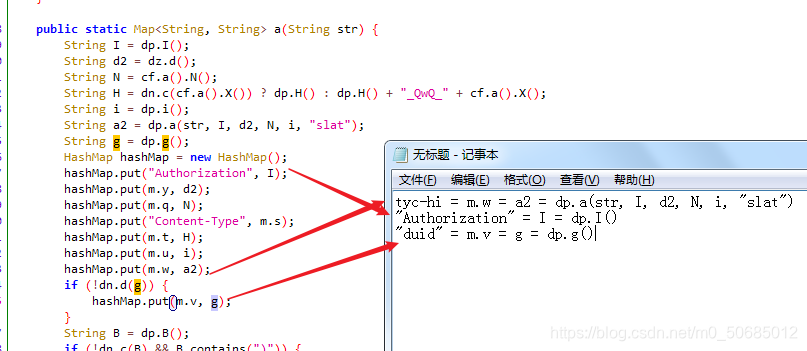
捋一下关系
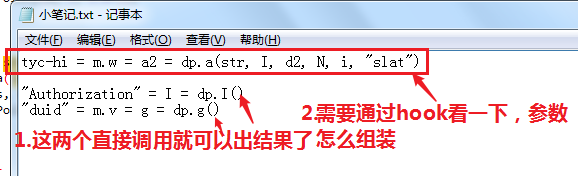
hook传入的参数
import codecs
import frida
import os
import sys
# 大坑 变量要定义var
# return,send的拼写
def on_message(message, data):
if message['type'] == 'send':
print(message['payload'])
elif message['type'] == 'error':
print(message['stack'])
def adbforward():
os.system("adb forward tcp:27042 tcp:27042")
os.system("adb forward tcp:27043 tcp:27043")
# 先通过hook了解传入的参数情况,然后再rpc
hook_code = '''
Java.perform(
function(){
var dp = Java.use('com.tianyancha.skyeye.utils.dp');
dp.a.overload('java.lang.String', 'java.lang.String', 'java.lang.String', 'java.lang.String', 'java.lang.String', 'java.lang.String').implementation = function(arg1,arg2,arg3,arg4,arg5,arg6){
send("dp.a.args")
send(arg1);
send(arg2);
send(arg3);
send(arg4);
send(arg5);
send(arg6);
var result_dp_a = this.a(arg1,arg2,arg3,arg4,arg5,arg6);
send('re:'+result_dp_a);
return result_dp_a
},
dp.I.implementation = function(){
var result_dp_I = this.I();
send("Authorization");
send(result_dp_I);
return result_dp_I;
},
dp.g.implementation = function(){
var result_dp_g = this.g();
send("duid");
send(result_dp_g);
return result_dp_g;
}
}
)
'''
# 这里的attach可以传int格式的pid
process = frida.get_usb_device().attach('com.tianyancha.skyeye')
script = process.create_script(hook_code)
script.on('message', on_message)
# 注入rpc代码
script.load()
sys.stdin.read()
# 启动rpc
# script.exports.MyAnalysis()
注意大坑:在js里的变量记得要var,还有return和send的拼写,以及send里面不要用,逗号拼接
可通过hook结果知道dp.a()中传入的参数组成
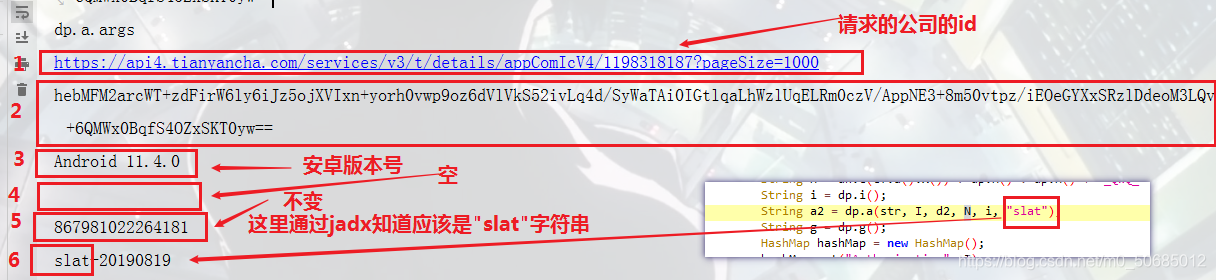
通过rpc调用返回参数字典,然后就可以后续调用组装请求了
import codecs
import frida
import os
import sys
# 大坑 变量要定义var,方法名不要用大写的字母!!!
# return,send的拼写
def on_message(message, data):
if message['type'] == 'send':
print(message['payload'])
elif message['type'] == 'error':
print(message['stack'])
def adbforward():
os.system("adb forward tcp:27042 tcp:27042")
os.system("adb forward tcp:27043 tcp:27043")
rpc_code = '''
rpc.exports = {
myanalysis:function(url,android){
var analysisresult = {"tyc-hi":"","Authorization":"","duid":"","deviceID":""};
Java.perform(
function(){
var dp = Java.use('com.tianyancha.skyeye.utils.dp');
var duid = dp.g();
var Authorization = dp.I();
analysisresult["Authorization"] = Authorization;
analysisresult["duid"] = duid;
var tyc = dp.a(url,Authorization,android,"","867981022264181","slat");
analysisresult["tyc-hi"] = tyc;
})
return analysisresult
}}
'''
# 这里的attach可以传int格式的pid
process = frida.get_usb_device().attach('com.tianyancha.skyeye')
script = process.create_script(rpc_code)
script.on('message', on_message)
# 注入rpc代码
script.load()
# 启动rpc
analysis_result = script.exports.myanalysis("https://api4.tianyancha.com/services/v3/t/common/baseinfoV5/150041670","Android 11.4.0")
print(analysis_result,'-analysis_result')
sys.stdin.read()