端口扫描
二、三、四层发现的目的就是发现存活的IP,在存活的IP上面,展开进一步的扫描,及端口扫描,发现存活主机上存在着哪些开放的端口,端口后面就对应着各种各样的应用程序,应用程序的漏洞都是通过端口体现出来的,所以,扫描端口为我们后续的攻击提供更大的攻击面。
- 端口对应网络服务及应用端程序;
- 服务端程序的漏洞通过端口攻入;
- 发现开放的端口;
- 更具体的攻击面;
1. UDP端口扫描
基于端口的扫描,都是针对存活的主机而言的,使用UDP端口扫描时,如果端口开放,则目标系统不响应(可能产生误判),如果端口不开放,则目标系统会响应端口不可达,代表该端口没有开放;
(1)scapy
- 端口关闭:ICMP port-unreachable;
- 端口开放:没有回包;
root@root:~# scapy
WARNING: No route found for IPv6 destination :: (no default route?)
INFO: Can't import python ecdsa lib. Disabled certificate manipulation tools
Welcome to Scapy (2.3.3)
>>> a=sr1(IP(dst="192.168.37.128")/UDP(dport=53),timeout=1,verbose=0)
>>> a.display() #报错是因为端口开放,没有回包
Traceback (most recent call last):
File "<console>", line 1, in <module>
AttributeError: 'NoneType' object has no attribute 'display'
>>> a=sr1(IP(dst="192.168.37.128")/UDP(dport=90),timeout=1,verbose=0)
>>> a.display() #目标主机的该端口没有开放
###[ IP ]###
version= 4L
ihl= 5L
tos= 0x0
len= 56
id= 3342
flags=
frag= 0L
ttl= 128
proto= icmp
chksum= 0x6163
src= 192.168.37.128
dst= 192.168.37.131
\options\
###[ ICMP ]###
type= dest-unreach
code= port-unreachable
chksum= 0xc96a
reserved= 0
length= 0
nexthopmtu= 0
###[ IP in ICMP ]###
version= 4L
ihl= 5L
tos= 0x0
len= 28
id= 1
flags=
frag= 0L
ttl= 64
proto= udp
chksum= 0xae7c
src= 192.168.37.131
dst= 192.168.37.128
\options\
###[ UDP in ICMP ]###
sport= domain
dport= 90
len= 8
chksum= 0x32fb
通过抓包查看发的两个包的过程:


使用脚本的方式实现扫描多个端口:UDP_scapy.py
#!/usr/bin/python
#Author:橘子女侠
#该脚本用于实现扫描多个端口
from scapy.all import*
import time
import sys
if len( sys.argv ) !=4:
print "Example - ./udp_scan.py 1.1.1.1 1 100"
sys.exit()
ip=sys.argv[1]
start=int(sys.argv[2])
end=int(sys.argv[3])
for port in range(start,end+1):
a=sr1(IP(dst=ip)/UDP(dport=port),timeout=5,verbose=0)
time.sleep(1) #防止因扫描过快,造成误判
if a==None:
print(port)
else:
pass结果如下:并使用Wireshark抓包查看
root@root:~# ./UDP_scapy.py 192.168.37.128 1 150
53
88
123
137
138

(2)Nmap
root@root:~# nmap -sU 192.168.7.128
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 18:30 CST
Nmap scan report for bogon (192.168.7.128)
Host is up (0.00075s latency).
All 1000 scanned ports on bogon (192.168.7.128) are open|filtered
Nmap done: 1 IP address (1 host up) scanned in 4.90 seconds
root@root:~# nmap -sU 192.168.7.128 -p 53
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 18:31 CST
Nmap scan report for bogon (192.168.7.128)
Host is up (0.00085s latency).
PORT STATE SERVICE
53/udp open|filtered domain
Nmap done: 1 IP address (1 host up) scanned in 0.32 seconds
root@root:~# nmap -iL IP.txt -sU -p 1-100
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 18:32 CST
Nmap scan report for bogon (192.168.37.2)
Host is up (0.000082s latency).
Not shown: 99 open|filtered ports
PORT STATE SERVICE
53/udp open domain
MAC Address: 00:50:56:E8:E0:56 (VMware)
Nmap scan report for bogon (192.168.37.128)
Host is up (0.0035s latency).
Not shown: 98 closed ports
PORT STATE SERVICE
53/udp open domain
88/udp open|filtered kerberos-sec
MAC Address: 00:0C:29:3B:24:57 (VMware)
Nmap scan report for bogon (192.168.37.131)
Host is up (0.0000050s latency).
Not shown: 99 closed ports
PORT STATE SERVICE
68/udp open|filtered dhcpc
Nmap done: 5 IP addresses (3 hosts up) scanned in 8.34 seconds
2. TCP端口扫描
- TCP是基于连接的协议;
- TCP扫描可以分为隐蔽扫描、僵尸扫描、全连接扫描;
- 所有的TCP扫描方式都是基于三次握手的变化来判断目标端口的状态;
隐蔽端口扫描
(1) 隐蔽端口扫描——scapy
1.1> SYN——SYN/ACK——ACK #目标端口开放
SYN——RST/ACK #目标端口不开放
root@root:~# scapy
WARNING: No route found for IPv6 destination :: (no default route?)
INFO: Can't import python ecdsa lib. Disabled certificate manipulation tools
Welcome to Scapy (2.3.3)
>>> a=sr1(IP(dst="192.168.37.128")/TCP(dport=80),timeout=1,verbose=0)
>>> a.display()
###[ IP ]###
version= 4L
ihl= 5L
tos= 0x0
len= 44
id= 3882
flags= DF
frag= 0L
ttl= 128
proto= tcp
chksum= 0x1f4e
src= 192.168.37.128
dst= 192.168.37.131
\options\
###[ TCP ]###
sport= http
dport= ftp_data
seq= 3859315704
ack= 1
dataofs= 6L
reserved= 0L
flags= SA
window= 8192
chksum= 0x495c
urgptr= 0
options= [('MSS', 1460)]
###[ Padding ]###
load= '\x00\x00'
>>> a=sr1(IP(dst="192.168.37.128")/TCP(dport=90),timeout=1,verbose=0)
>>> a.display()
###[ IP ]###
version= 4L
ihl= 5L
tos= 0x0
len= 40
id= 3956
flags= DF
frag= 0L
ttl= 128
proto= tcp
chksum= 0x1f08
src= 192.168.37.128
dst= 192.168.37.131
\options\
###[ TCP ]###
sport= 90
dport= ftp_data
seq= 0
ack= 1
dataofs= 5L
reserved= 0L
flags= RA
window= 0
chksum= 0xe30d
urgptr= 0
options= {}
###[ Padding ]###
load= '\x00\x00\x00\x00\x00\x00'
使用Wireshark抓包查看:
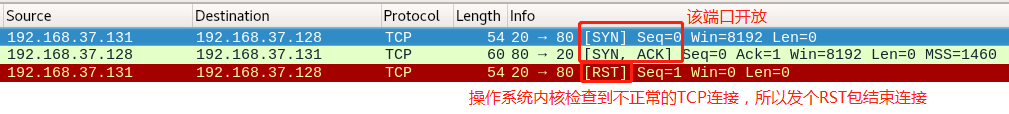

1.2>使用脚本实现 :syn_scan.py
#!/usr/bin/python
#Author:橘子女侠
#该脚本用户实现扫描目标主机中开放的TCP端口
from scapy.all import*
import sys
if len( sys.argv ) !=4:
print "Example - ./syn_scan.py 1.1.1.1 1 100"
sys.exit()
ip = str(sys.argv[1])
start = int(sys.argv[2])
end = int(sys.argv[3])
for port in range(start,end+1):
a=sr1(IP(dst=ip)/TCP(dport=port),timeout=0.1,verbose=0)
if a ==None:
pass
else:
if int(a[TCP].flags)==18: #SYN+ACK值为18
print (port)
else:
pass
结果如下:并使用Wireshark抓包查看
root@root:~# chmod +x syn_scan.py
root@root:~# ./syn_scan.py 192.168.37.128 1 150
25
53
80
88
110
135
139
143

针对脚本中为什么int(a[TCP].flags)==18,是因为SYN——>2,ACK——>16;
Transmission Control Protocol, Src Port: 25, Dst Port: 20, Seq: 0, Ack: 1, Len: 0
Source Port: 25
Destination Port: 20
[Stream index: 24]
[TCP Segment Len: 0]
Sequence number: 0 (relative sequence number)
Acknowledgment number: 1 (relative ack number)
0110 .... = Header Length: 24 bytes (6)
Flags: 0x012 (SYN, ACK)
000. .... .... = Reserved: Not set
...0 .... .... = Nonce: Not set
.... 0... .... = Congestion Window Reduced (CWR): Not set
.... .0.. .... = ECN-Echo: Not set
.... ..0. .... = Urgent: Not set
.... ...1 .... = Acknowledgment: Set #2^4=16
.... .... 0... = Push: Not set
.... .... .0.. = Reset: Not set
.... .... ..1. = Syn: Set #2^1=2
.... .... ...0 = Fin: Not set #2^0=1
[TCP Flags: ·······A··S·]
Window size value: 8192
[Calculated window size: 8192]
Checksum: 0xfd4f [unverified]
[Checksum Status: Unverified]
Urgent pointer: 0
Options: (4 bytes), Maximum segment size
TCP Option - Maximum segment size: 1460 bytes
Kind: Maximum Segment Size (2)
Length: 4
MSS Value: 1460
[SEQ/ACK analysis]
[This is an ACK to the segment in frame: 55]
[The RTT to ACK the segment was: 0.000445714 seconds]
(2)隐蔽端口扫描——nmap
root@root:~# nmap 192.168.37.128 -p1-100 #扫描1-100端口,默认-sS
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 15:34 CST
Nmap scan report for bogon (192.168.37.128)
Host is up (0.014s latency).
Not shown: 96 closed ports
PORT STATE SERVICE
25/tcp open smtp
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
MAC Address: 00:0C:29:3B:24:57 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.68 seconds
root@root:~# nmap -sS 192.168.37.128 -p1-100
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 15:37 CST
Nmap scan report for bogon (192.168.37.128)
Host is up (0.00027s latency).
Not shown: 96 closed ports
PORT STATE SERVICE
25/tcp open smtp
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
MAC Address: 00:0C:29:3B:24:57 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.22 seconds
root@root:~# nmap -sS 192.168.37.128 -p 80,88,53,22,25 #扫描指定的端口
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 15:37 CST
Nmap scan report for bogon (192.168.37.128)
Host is up (0.00022s latency).
PORT STATE SERVICE
22/tcp closed ssh
25/tcp open smtp
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
MAC Address: 00:0C:29:3B:24:57 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.11 seconds
root@root:~# nmap -sS -iL IP.txt -p 80,88,53,22 #扫描指定的IP地址列表和端口
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 15:40 CST
Nmap scan report for bogon (192.168.37.2)
Host is up (0.0015s latency).
PORT STATE SERVICE
22/tcp closed ssh
53/tcp open domain
80/tcp closed http
88/tcp closed kerberos-sec
MAC Address: 00:50:56:E8:E0:56 (VMware)
Nmap scan report for bogon (192.168.37.128)
Host is up (0.00034s latency).
PORT STATE SERVICE
22/tcp closed ssh
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
MAC Address: 00:0C:29:3B:24:57 (VMware)
Nmap scan report for bogon (192.168.37.131)
Host is up (0.000029s latency).
PORT STATE SERVICE
22/tcp closed ssh
53/tcp closed domain
80/tcp closed http
88/tcp closed kerberos-sec
Nmap done: 5 IP addresses (3 hosts up) scanned in 1.61 seconds
(3)隐蔽端口扫描——hping3
root@root:~# hping3 192.168.37.128 --scan 1-100 -S #-S:SYN包
Scanning 192.168.37.128 (192.168.37.128), port 1-100
100 ports to scan, use -V to see all the replies
+----+-----------+---------+---+-----+-----+-----+
|port| serv name | flags |ttl| id | win | len |
+----+-----------+---------+---+-----+-----+-----+
25 smtp : .S..A... 128 49411 8192 46
53 domain : .S..A... 128 56579 8192 46
80 http : .S..A... 128 63491 8192 46
88 kerberos : .S..A... 128 4 8192 46
All replies received. Done.
Not responding ports:
root@root:~# hping3 192.168.37.128 --scan 22,25,80 -S
Scanning 192.168.37.128 (192.168.37.128), port 22,25,80
3 ports to scan, use -V to see all the replies
+----+-----------+---------+---+-----+-----+-----+
|port| serv name | flags |ttl| id | win | len |
+----+-----------+---------+---+-----+-----+-----+
80 http : .S..A... 128 12548 8192 46
25 smtp : .S..A... 128 13060 8192 46
All replies received. Done.
Not responding ports:
#源地址欺骗,但是不知道扫描后的结果
root@root:~# hping3 -c 100 -S --spoof 192.168.37.130 -p ++1 192.168.37.128
HPING 192.168.37.128 (eth0 192.168.37.128): S set, 40 headers + 0 data bytes
--- 192.168.37.128 hping statistic ---
100 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms

全连接端口扫描
(1)全连接端口扫描(SYN、SYN+ACK、ACK)——scapy
scapy对全连接扫描比较困难,如果直接给目标系统发SYN,目标系统会回应一个SYN/ACK,这时候,操作系统内核会认为没建立完整的连接,会返回一个RST,断开TCP连接,此时,如果在向目标系统发送一个ACK,目标系统会回应RST;
若需要让操作系统不产生RST包,影响后续的操作,就需要添加一定的防火墙策略,讲操作系统系统内核产生的RST包drop掉;
使用策略:iptables -A OUTPUT -p tcp --tcp-flags RST RST -d 192.168.37.128 -j DROP
脚本:tcp_scan.py
#!/usr/bin/python
#Author:橘子女侠
#Time:2019/4/14
#该脚本用于与目标主机建立全连接的端口扫描
from scapy.all import *
SYN=IP(dst="192.168.37.128")/TCP(dport=80,flags="S")
print("-- SENT --" )
SYN.display()
print("\n\n-- REVEIED" )
response=sr1(SYN,timeout=1,verbose=0)
response.display()
if int(response[TCP].flags)==18:
print ("\n\n-- SENT --" )
A=IP(dst="192.168.37.128")/TCP(dport=80,flags="A",ack=(response[TCP].seq+1))
A.display()
response2=sr1(A,timeout=1,verbose=0)
else:
print ("SYN-ACK not returned")结果如下:并使用Wireshark抓包查看
root@root:~# ./tcp_scan.py
-- SENT --
###[ IP ]###
version = 4
ihl = None
tos = 0x0
len = None
id = 1
flags =
frag = 0
ttl = 64
proto = tcp
chksum = None
src = 192.168.37.131
dst = 192.168.37.128
\options \
###[ TCP ]###
sport = ftp_data
dport = http
seq = 0
ack = 0
dataofs = None
reserved = 0
flags = S
window = 8192
chksum = None
urgptr = 0
options = {}
-- REVEIED
###[ IP ]###
version = 4L
ihl = 5L
tos = 0x0
len = 44
id = 7450
flags = DF
frag = 0L
ttl = 128
proto = tcp
chksum = 0x115e
src = 192.168.37.128
dst = 192.168.37.131
\options \
###[ TCP ]###
sport = http
dport = ftp_data
seq = 3575793390
ack = 1
dataofs = 6L
reserved = 0L
flags = SA
window = 8192
chksum = 0x8f4c
urgptr = 0
options = [('MSS', 1460)]
###[ Padding ]###
load = '\x00\x00'
-- SENT --
###[ IP ]###
version = 4
ihl = None
tos = 0x0
len = None
id = 1
flags =
frag = 0
ttl = 64
proto = tcp
chksum = None
src = 192.168.37.131
dst = 192.168.37.128
\options \
###[ TCP ]###
sport = ftp_data
dport = http
seq = 0
ack = 3575793391
dataofs = None
reserved = 0
flags = A
window = 8192
chksum = None
urgptr = 0
options = {}

(2)全连接端口扫描——nmap
root@root:~# nmap -sT 192.168.37.128 -p 1-100 #扫描1-100端口
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 16:21 CST
Nmap scan report for bogon (192.168.37.128)
Host is up (0.00080s latency).
Not shown: 96 closed ports
PORT STATE SERVICE
25/tcp open smtp
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
MAC Address: 00:0C:29:3B:24:57 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.34 seconds
root@root:~# nmap -sT 192.168.37.128 -p 22,25,28,80 #扫描指定的端口
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 16:22 CST
Nmap scan report for bogon (192.168.37.128)
Host is up (0.00053s latency).
PORT STATE SERVICE
22/tcp closed ssh
25/tcp open smtp
28/tcp closed unknown
80/tcp open http
MAC Address: 00:0C:29:3B:24:57 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.24 seconds
root@root:~# nmap -sT 192.168.37.128 #扫描1000个常见端口
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 16:23 CST
Nmap scan report for bogon (192.168.37.128)
Host is up (0.00036s latency).
Not shown: 973 closed ports
PORT STATE SERVICE
25/tcp open smtp
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
110/tcp open pop3
135/tcp open msrpc
139/tcp open netbios-ssn
143/tcp open imap
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
465/tcp open smtps
593/tcp open http-rpc-epmap
636/tcp open ldapssl
993/tcp open imaps
995/tcp open pop3s
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3306/tcp open mysql
6000/tcp open X11
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49158/tcp open unknown
49167/tcp open unknown
MAC Address: 00:0C:29:3B:24:57 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.85 seconds
(3)全连接端口扫描——dmitry
- 功能简单,使用简便;
- 默认150个最常用的端口;
root@root:~# dmitry -p 192.168.37.128
Deepmagic Information Gathering Tool
"There be some deep magic going on"
HostIP:192.168.37.128
HostName:bogon
Gathered TCP Port information for 192.168.37.128
---------------------------------
Port State
25/tcp open
53/tcp open
80/tcp open
88/tcp open
110/tcp open
135/tcp open
139/tcp open
143/tcp open
Portscan Finished: Scanned 150 ports, 141 ports were in state closed
All scans completed, exiting
(4)全连接端口扫描——nc
root@root:~# nc -nv -w 1 -z 192.168.37.128 1-100
(UNKNOWN) [192.168.37.128] 88 (kerberos) open
(UNKNOWN) [192.168.37.128] 80 (http) open
(UNKNOWN) [192.168.37.128] 53 (domain) open
(UNKNOWN) [192.168.37.128] 25 (smtp) open