1. Computer hardware composition:
Arithmetic units, controllers, storage, input devices, output devices (and interconnection devices: buses and interfaces)
-
Calculator: Complete arithmetic and logic operations. Arithmetic operations: addition, subtraction, multiplication, division, etc. Logical operations: AND, OR, NOT, shift, etc. Basic structure: ALU, registers, connection paths.
-
Controller: Generates control signals with time stamps. (Form of control signal: level signal and pulse signal)
-
Memory: store the original program, original data, and intermediate results of calculation

2. Standards for measuring computers:
Machine word length (in bytes as the basic unit: byte), storage capacity, and computing speed
1KB = 2^10B
1MB = 2^20B
1GB = 2^30B
1TB = 2^40B
1Byte = 8bit
3. Original code, inverse code, complement code and shift code
Machine number, true value: A number and its sign are encoded in the machine with 0 and 1, and the value of the number itself is called the true value of the machine number.
Inverse code: For a positive number, the form of its inverse code is the same as that of the original code; for a negative number, the inverse code needs to invert the value part of the original code. (symbol: positive number 0, negative number 1)
Frame shift: For positive numbers. The form of its complement code is the same as that of the original code; for negative numbers, the complement code adds 1 to the last bit of its inverse code (the number of digits changes). (symbol: positive number 0, negative number 1)
For integers only: [x+y] complement = [x] complement + [y] complement; [xy] complement = [x] complement + [-y] complement
[y] Complement→[-y] Complement: together with the sign bit, bitwise inversion, add 1 to the last bit
Code shift: unchanged for positive numbers, bitwise inversion for negative numbers, plus 1 at the end (symbol: positive 1, negative 0)
If [x] shift > [y] shift, then x > y
4. Overflow problem:
Overflow: refers to the phenomenon that the operation result exceeds the numerical range that the machine can represent;
Conditions for overflow to occur:
-
Overflow may occur when adding numbers of the same sign or subtracting numbers of different signs
-
The same number's complement addition, the sign bit of the result is opposite to the added number
-
Different sign complement subtraction, the sign bit of the result is the same as the subtrahend
5. Data verification code:
-
Parity check code (only error detection)
-
Hamming code (with error detection and error correction capabilities)
-
Cyclic redundancy check code (with strong error detection and error correction capabilities)
6. Representation of floating point numbers:

7. Memory classification:
- Classification by storage medium: semiconductor memory, magnetic surface memory, optical surface memory
- Classified by access mode: random read-write memory RAM, read-only memory ROM, sequential access memory SAM, direct access memory DAM
- Classification according to the preservation of information: permanent memory, non-permanent memory
- Classified according to the role in the computer: main memory, cache memory, auxiliary memory
The storage principle of SRAM: record 0 and 1 information according to the two stable states of two bistable flip-flops
The storage principle of DRAM: record 0/1 information according to the presence or absence of charge on the capacitor
Addressing mode: addressing by word and addressing by byte
Number of address pins = number of log2 storage units
Number of data pins = number of bits per storage unit
Storage extension: word extension, bit extension, segment extension
Three ways to refresh: centralized refresh, decentralized refresh, asynchronous refresh
Magnetic surface memory:
- Write (electromagnetic conversion): use the pulse current in the write coil to convert the value into different remanence states in the magnetic storage unit
- Read (magnetoelectric conversion): through the read coil, the residual magnetic state of the memory cell is converted into an electrical signal output
Magnetic recording method:
- return to zero
- non-return-to-zero
- Phasing system
- FM
Calculations related to hard disk storage:
The three-level structure has two levels:
- Cache-main memory level
- Main memory-auxiliary storage level: solve the problem of insufficient main memory capacity;
- Cache-Main Storage-Auxiliary Storage
Cache solves the mismatch between CPU and main memory;
Cache-main memory mechanism address mapping method:
- direct mapping
- fully connected map
- group associative mapping
Calculation of hit rate:
8. I/O interface and I/O process control
1. The main factors that affect the way I/O devices are connected to the host:
- The influence of peripheral operating speed
- Influence of data transmission form (parallel transmission, serial transmission)
- The impact of data communication synchronization mode: 1. Synchronous communication: the sending end and the receiving end have a unified clock; 2. Asynchronous communication: there is no unified clock between the sending end and the receiving end, and the response method is adopted;
- The impact of the type of information transmitted: 1. Device address information; 2. Data; 3. Device status information; 4. Control information;
- CPU controls I/O devices: 1. Program direct control; 2. Program query control; 3. Program interrupt control; 4. Direct memory access (DMA)
2. Function of I/O interface:
- Device Selection
- Data buffering and latching
- Data format conversion
- Signal characteristic matching
- Accept the control commands of the CPU and monitor the working status of the peripherals
3. Addressing of I/O ports:
- Unified addressing of I/O port address and memory address
- independent addressing
4. Save the breakpoint and protect the scene
breakpoint: the value in the program counter;
Field: the value in the current program register
5. Five stages of program interruption:
- interrupt request
- interrupt arbitration
- interrupt response
- interrupt handling
- interrupt return
6. The solution to the conflict between the DMA controller and the CPU shared memory
- CPU pauses access to memory
- The DMA controller alternates with the CPU to access memory
- cycle stealing
7. DMA transfer process:
- preprocessing
- data transmission
- Post-processing
9. Bus
1. Three basic characteristics of the bus: sharing, time sharing, and specification (mechanical specification, electrical specification, functional specification, time specification)
2. Bus classification:
- Classified according to the nature of the signal transmitted by the bus: 1. Address bus; 2. Data bus; 3. Control bus;
- Classified according to the location of the bus: 1. Internal bus (on-chip bus and off-chip bus) 2. External bus (referring to the bus interfaced with peripheral devices)
- Classified according to the main components connected by the bus in the system: 1. Storage bus; 2. DMA bus; 3. System bus; 4. I/O bus; 5. Local bus;
3. The structure of the bus:
- Single bus structure;
- Dual bus structure;
- Three bus structure;
4. The basic transmission process of signals in the bus
- request bus
- bus arbitration
- destination addressing
- Information transfer
- error detection
5. Bus contention and arbitration
Two methods of conflict resolution: static method and dynamic method;
Dynamic method: the arbitration and arbitration logic in the bus control mechanism will determine which module uses the bus according to certain arbitration principles;
Dynamic arbitration is divided into two types: centralized control and distributed control;
There are three priority arbitration methods for centralized control:
- chain query
- Counter timing query method
- independent request method
6. Bus communication
- Synchronous communication (master and slave have a common clock)
- Asynchronous communication (does not rely on a time standard based on a common clock, forming a "request-response" approach)
- Semi-synchronous communication (synchronized with system clock)
- split communication
10. Controller logic
1. Instruction: A command that requires the computer to complete a certain basic operation; it consists of two parts: the operation code and the address code.
2. Divide instructions into 4 types according to the number of addresses:
- 3 address instruction;
- 2 address instruction;
- 1 address instruction
- 0 address instruction;


You can use fixed-length opcodes or variable-length opcodes;
3. Instruction addressing mode:
- Sequential addressing (the address of the next instruction is provided by the program counter PC)
- Jump addressing (the address of the next instruction is provided by the address code of the program control instruction)
4. Data addressing mode: (formal address D: the address in the address code field in the instruction; effective address EA: the real address of the operand)
- Immediate addressing: the address field of the instruction indicates not the address of the operand, but the operand itself;
- Immediate addressing: The address field in the instruction directly indicates the address of the operand in memory; EA=(D); parentheses indicate the content to be fetched
- Indirect addressing: What is taken out of the memory by the address code is not the operand, but the address of the operand;
- Register addressing: EA = R number;
- Register indirect addressing: EA = (R); parentheses indicate the content
- Index addressing: EA = D + index register;
- Base addressing: EA = D + base register;
- Relative addressing: EA = D + (special register PC);
- stack addressing
- implicit addressing
5. RISC: Simplified Instruction Computer System; CISC: Complex Instruction Computer System;
These are two different ways of designing the instruction system at present.
6. Instruction system design, the basic content to be considered mainly includes:
- action list;
- type of data;
- instruction format;
- register;
- addressing mode;
Design principles: completeness; effectiveness; regularity; compatibility.
7. The main memory and functions of the CPU
① Instruction Register (IR): Stores the instruction currently being executed
② Program Counter (PC): Stores the address of the next instruction to be executed
③ Data Buffer Register (MDR): Stores the address to be stored Memory or data read from memory
④ Address Register (MAR): Store the address of the memory unit to be accessed
⑤ Program Status Word Register (PSW): Store various status information during program running
⑥ Accumulator (AC): Stores an operand or result of an arithmetic or logical operation
8. CPU function:
- command control (controller)
- Operational Control (Controller)
- Time Control (Controller)
- Data processing (calculator)
9. CPU tasks:
- fetch instruction
- analysis instruction
- execute command
10. Instruction cycle flow chart:
For example: "ADD R2, R0" instruction completed (R0) + (R2) → R0; (assuming the address of the instruction has been put into PC).


11. The basic composition of the microcontroller:
- Control memory CM (used to store microprograms that implement all instruction systems, it is a read-only memory)
- Microinstruction register (holds microinstructions fetched from control memory)
- Micro-address transfer logic (automatically complete the task of modifying the micro-address, equivalent to a PC)
Micro-command: the control command issued by the control unit to the execution unit;
Microinstructions: a set of microinstructions to realize certain operation functions;
Microinstructions are divided into two parts: micro-opcode and micro-address;
Coding method: direct coding method, field direct coding method, mixed coding method;
Microinstruction format: horizontal type; vertical type.
Digression
Many people who are new to the computer industry or graduates of computer-related majors have encountered obstacles everywhere due to lack of practical experience. Let's look at two sets of data:
-
The 2023 national college graduates are expected to reach 11.58 million, and the employment situation is severe;
-
According to the data released by the National Network Security Publicity Week, by 2027, the shortage of network security personnel in my country will reach 3.27 million.
On the one hand, the employment situation of fresh graduates is severe every year, and on the other hand, there is a gap of one million cyber security talents.
On June 9, the 2023 edition of the Employment Blue Book of MyCOS Research (including the 2023 Employment Report for Undergraduates in China and the Employment Report for Higher Vocational Students in China in 2023) was officially released.
Top 10 Majors with Higher Monthly Salary for 2022 College Graduates
The monthly income of undergraduate computer science majors and higher vocational automation majors is relatively high. The monthly income of the 2022 class of undergraduate computer science and higher vocational automation majors is 6,863 yuan and 5,339 yuan, respectively. Among them, the starting salary of undergraduate computer majors is basically the same as that of the 2021 class, and the monthly income of higher vocational automation majors has increased significantly. The 2022 class of overtaking railway transportation majors (5295 yuan) ranks first.
Specifically, depending on the major, the major with a higher monthly income for undergraduates in 2022 is information security (7579 yuan). Compared with the class of 2018, undergraduate majors related to artificial intelligence, such as electronic science and technology, automation, performed well, and their starting salaries increased by 19% compared with five years ago. Although data science and big data technology are newly added majors in recent years, they have performed well, and have ranked among the top three majors with higher monthly income half a year after graduation for the 2022 class of undergraduates. The only humanities and social science major that entered the top 10 undergraduate high-paying list five years ago-French has dropped out of the top 10.

"There is no national security without cybersecurity". At present, network security has been elevated to the height of national strategy and has become one of the most important factors affecting national security and social stability.
Characteristics of the network security industry
1. The employment salary is very high, and the salary rises quickly. In 2021, Liepin.com released the highest employment salary in the network security industry, which is 337,700 yuan per capita!
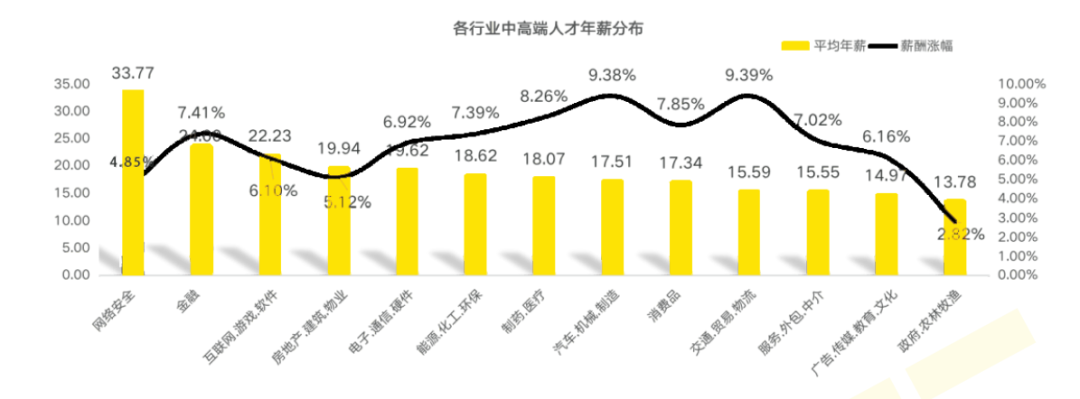
2. There is a large talent gap and many employment opportunities
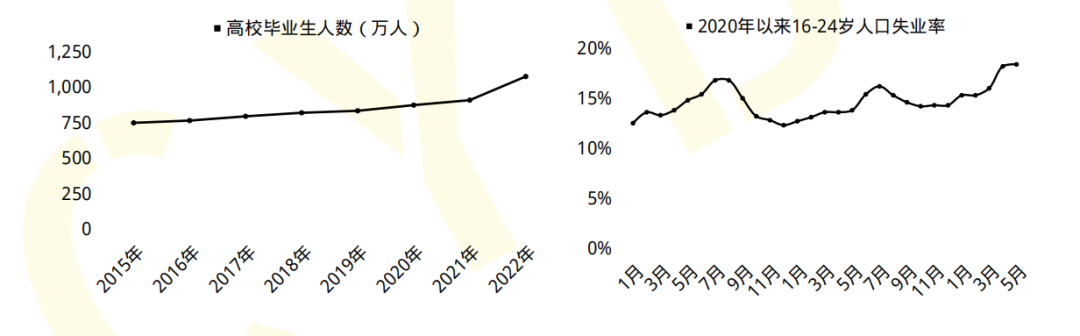
On September 18, 2019, the official website of the "Central People's Government of the People's Republic of China" published: my country needs 1.4 million cyberspace security talents, but schools across the country train less than 1.5 million people each year. Liepin.com's "Cyber Security Report for the First Half of 2021" predicts that the demand for cyber security talents will be 3 million in 2027, and there are only 100,000 employees currently engaged in the cyber security industry.
There is a lot of room for development in the industry, and there are many jobs
Since the establishment of the network security industry, dozens of new network security industry positions have been added: network security experts, network security analysts, security consultants, network security engineers, security architects, security operation and maintenance engineers, penetration engineers, information security management Data Security Engineer, Network Security Operations Engineer, Network Security Emergency Response Engineer, Data Appraiser, Network Security Product Manager, Network Security Service Engineer, Network Security Trainer, Network Security Auditor, Threat Intelligence Analysis Engineer, Disaster Recovery Professional , Actual combat offensive and defensive professionals...
Great career potential
The network security major has strong technical characteristics, especially mastering the core network architecture and security technology in the work, which has an irreplaceable competitive advantage in career development.
With the continuous improvement of personal ability, the professional value of the work will also increase with the enrichment of one's own experience and the maturity of project operation, and the appreciation space is bullish all the way, which is the main reason why it is popular with everyone.
To some extent, in the field of network security, just like the doctor profession, the older you are, the more popular you become. Because the technology becomes more mature, the work will naturally be valued, and promotion and salary increase are a matter of course.
Hacking & Cyber Security How to Learn
Today, as long as you give my article a thumbs-up, I will share my private collection of online security learning materials with you for free, so let’s see what is there.
1. Learning Roadmap
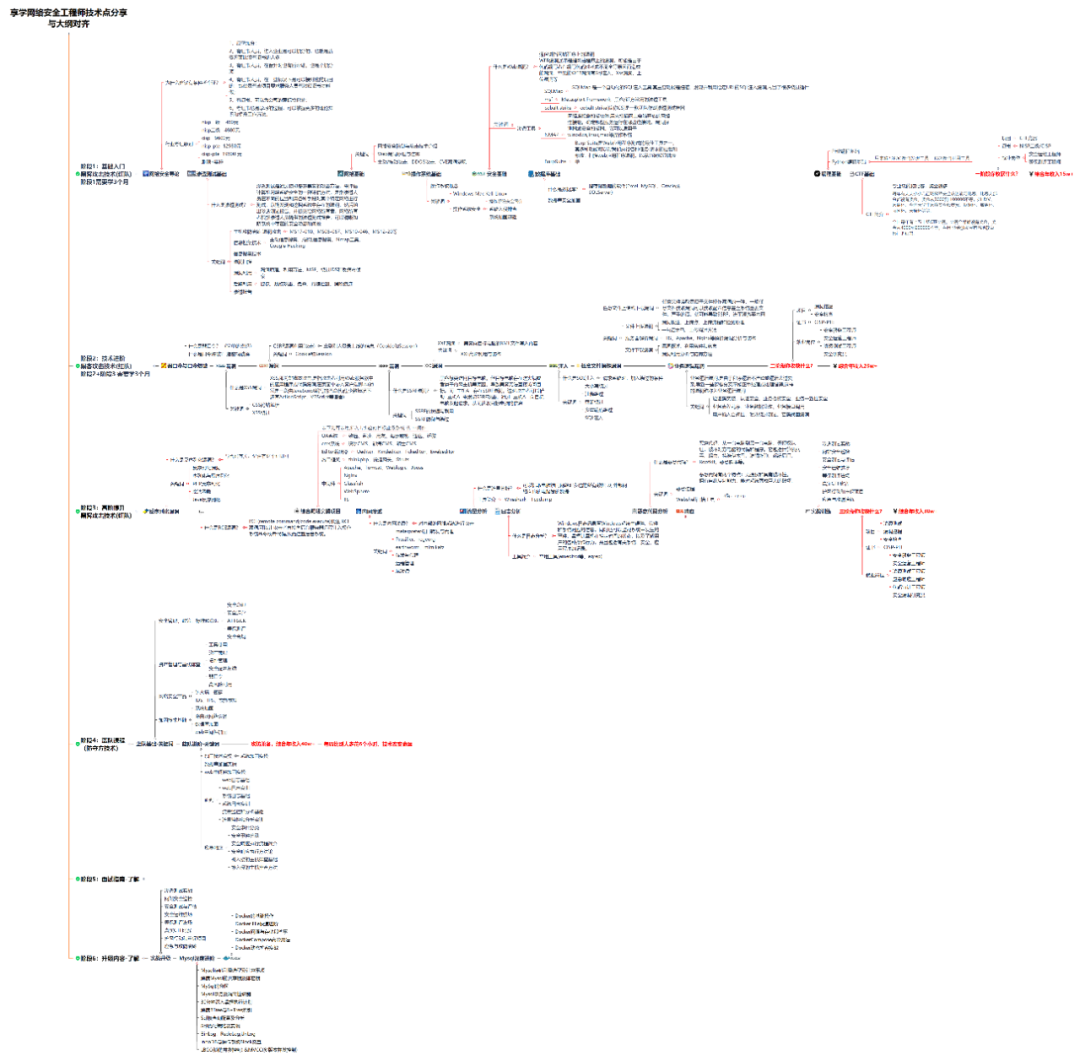
There are also many things to learn in attack and defense. I have written all the specific things to learn in the roadmap above. If you can learn them, you will have no problem getting a job or taking private jobs.
2. Video Tutorial
Although there are many learning resources on the Internet, they are basically incomplete. This is a video tutorial on cyber security recorded by myself. I have a supporting video explanation for every knowledge point in the above roadmap.
The content covers the study of network security law, network security operation and other guarantee assessment, penetration testing basics, detailed explanation of vulnerabilities, basic computer knowledge, etc., which are all learning contents that must be known when getting started with network security.
(It’s all packed into one piece and cannot be unfolded one by one. There are more than 300 episodes in total)
Due to limited space, only part of the information is shown, you need to click the link below to get it
CSDN spree: "Hacker & Network Security Introduction & Advanced Learning Resource Pack" free sharing
3. Technical documents and e-books
The technical documents are also compiled by myself, including my experience and technical points of participating in large-scale network security operations, CTF and SRC vulnerability mining. There are also more than 200 e-books. Due to the sensitivity of the content, I will not show them one by one.
Due to limited space, only part of the information is shown, you need to click the link below to get it
CSDN spree: "Hacker & Network Security Introduction & Advanced Learning Resource Pack" free sharing
4. Toolkit, interview questions and source code
"If you want to do a good job, you must first sharpen your tools." I have summarized dozens of the most popular hacking tools for everyone. The scope of coverage mainly focuses on information collection, Android hacking tools, automation tools, phishing, etc. Interested students should not miss it.
There is also the source code of the case and the corresponding toolkit mentioned in my video, which can be taken away if needed.
Due to limited space, only part of the information is shown, you need to click the link below to get it
CSDN spree: "Hacker & Network Security Introduction & Advanced Learning Resource Pack" free sharing
Finally, there are interview questions about Internet security that I have sorted out in the past few years. If you are looking for a job in Internet security, they will definitely help you a lot.
These questions are often encountered in interviews with Sangfor, Qi Anxin, Tencent or other major companies. If you have good questions or good insights, please share them.
Reference analysis: Sangfor official website, Qi Anxin official website, Freebuf, csdn, etc.
Content features: clear organization, including graphic representation, which is easier to understand.
Summary of content: Including intranet, operating system, protocol, penetration test, security service, vulnerability, injection, XSS, CSRF, SSRF, file upload, file download, file inclusion, XXE, logic vulnerability, tool, SQLmap, NMAP, BP, MSF…
Due to limited space, only part of the information is shown, you need to click the link below to get it
CSDN spree: "Hacker & Network Security Introduction & Advanced Learning Resource Pack" free sharing