Preface to the article
Sometimes when we are doing penetration testing, we will find that the target website allows uploading PDF files and supports online preview of PDF files. However, many similar websites will directly parse the PDF by calling the system IE browser. At this time, if we are in the PDF Insert executable malicious XSS code. When the user previews it online, the malicious XSS can be triggered and steal user cookies and other data information or perform malicious operations. In this article, we mainly introduce how to construct malicious XSS code in PDF and implement it by uploading PDF. XSS attack
Construction process
Step 1: Download and install "Swift PDF Editor"

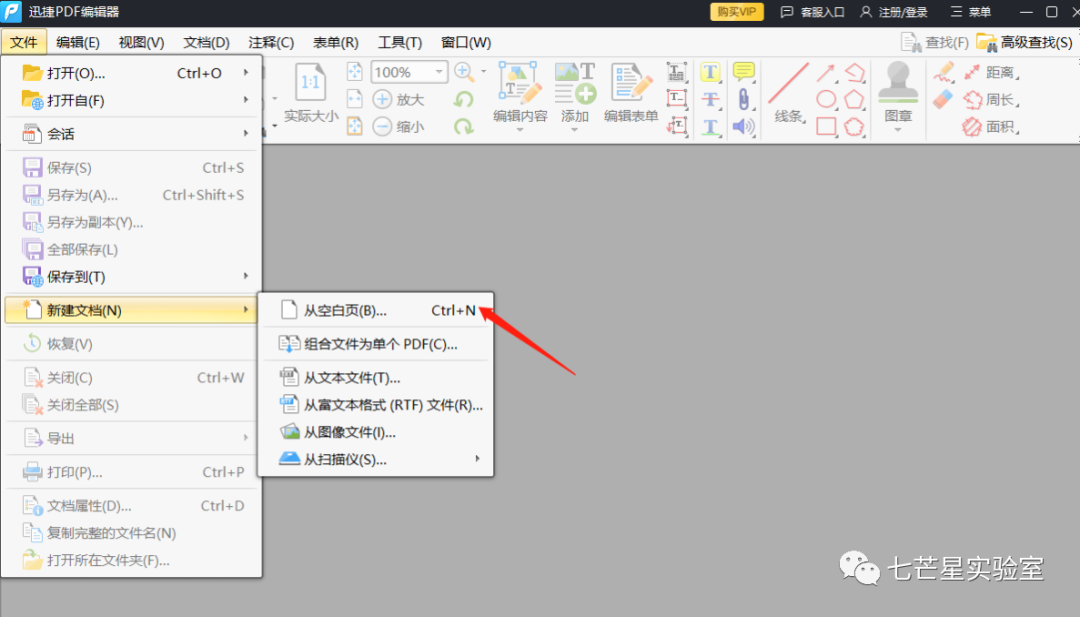
Step 2: Create PDF file
Step 2: Click the "Page" label on the left, select the corresponding page thumbnail, and then select the "Page Properties" command from the options drop-down menu

Step 3: Click the "Action" tab in the "Page Properties" dialog box, then select the "Run JavaScript" command from the "Select Action" drop-down menu, and then click the [Add] button to pop up the JavaScript editor dialog box

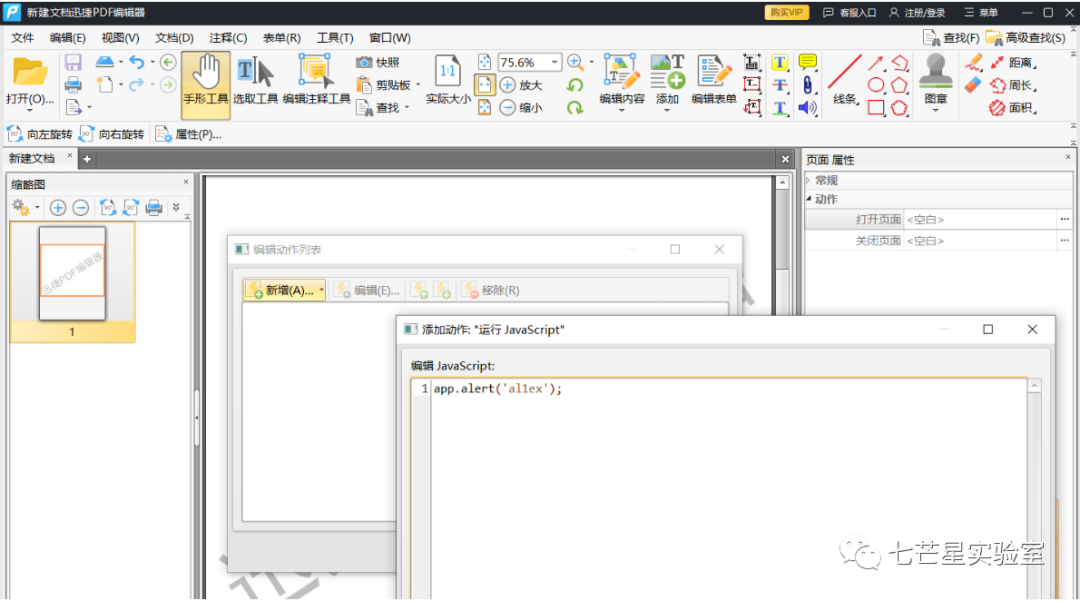
Step 4: Save the document and open it with a browser later

Skill development
We can embed the PDF file into the web page and try it out
<html><body><object data="test.pdf" width="100%" heigh="100%"type="application/pdf"></object></body></html>
Fix
As a website administrator or developer, you can choose to force the browser to download PDF files instead of providing online browsing or modifying the header and related properties of the web server configuration. You can also use a third-party plug-in to parse PDF without using Chrome's own PDF parsing. , https://github.com/adobe-type-tools/cmap-resources