1. Background introduction
Information system security is to protect various types of data resources in information systems from unauthorized access (including viewing, adding, modifying, deleting) and ensuring data integrity, confidentiality and availability. In the current development context of the Internet of Everything, information security is particularly important. As an important part of information security, access control can not only authenticate users' identities when accessing information systems, but also control users' access rights to information in a fine-grained manner. As the basic software of the information system, the database is responsible for data storage. To ensure the integrity, confidentiality and availability of information, strict access control is required.
The following is an excerpt of part of the content. Click on the video to view the full version.
2. Introduction to access control model
Access control core functions and elements
The core functions of access control: identity authentication and resource access control, which are embodied in the following four aspects: allowing legitimate subjects to enter the protected system; prohibiting illegal subjects from entering the protected system; allowing legitimate subjects to access protected resources Perform authorized access; prohibit unauthorized access by legitimate subjects to protected resources.
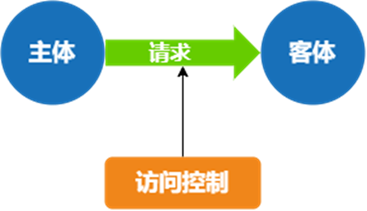
The three elements of access control are: subject, object and control policy:
- Subject, the entity requesting access to resources, which can be a system user, process or device, etc.;
- Object, the resource entity being accessed, can be a file or database object, etc.;
- A control strategy is a collection of attributes, which can be read, written, or executed.
Identity authentication
1. Password-based identity authentication uses username and password for identity authentication. Most information systems will use this method.
2. Certificate-based identity authentication uses signed certificates for identity authentication. The most commonly used is TLS (Transport Layer Security, Transport Layer Security Protocol) certificate. This method can not only verify the legality of the certificate, but also verify the information combining the certificate and the system. The legality verification of a certificate generally requires verification of the certificate's validity (the certificate is within the validity period) and credibility (the certificate chain is trustworthy). The information combined with the system is generally Common Name and is related to the system user's information.
3. Identity authentication based on three-party authentication center In information systems with complex business or many subsystems, it is necessary to use a unified authentication center for identity authentication. Commonly used unified identity authentication architectures include LDAP, Radius, GSSAPI, etc. There are many specific implementations of GSSAPI, such as KerberosV5, NTLM and SPNEGO.
4. Biometric-based identity authentication is based on each user’s unique biometric characteristics, including fingerprints, voice, facial recognition, iris, handwriting, hand shape, palm prints, etc.
5. Identity authentication based on hardware devices uses hardware devices bound to the identity, such as ID cards, IC cards, etc.
6. OTP (One-Time-Password) is a password that is only used once during the identity authentication process. Once a password is used, the password becomes invalid immediately and cannot be reused. OTP is generally not used independently and needs to be combined with other authentication methods and used in 2FA or MFA scenarios to enhance the security of identity authentication.
7. The identity authentication configuration based on HBA (Host-Based Authentication) configures the identity authentication method and authentication parameters of the specified access type, specified access resources, specified sources, specified users, thereby achieving flexible configuration of the identity authentication method.
3. Resource access control
Access control model development history
Information security With the development of informatization, access control models are also constantly evolving. The earliest ones were MAC (Mandatory Access Control, mandatory access control) and DAC (Discretionary Access Control, discretionary access control), and later IBAC (Identity-Based Access Control, identity-based access control) and ACL (Access Control Lists, access control lists) appeared ).
With the development of information systems, the popular RBAC (Role-Based Access Control, role-based access control) has emerged, and based on this, ABAC (Attribute-Based Access Control, attribute-based access control) has been developed. In some fields, especially the database field, LBAC (Label-Based Access Control) has been developed and used.
Introduction to access control model
1. MAC MAC, mandatory access control. The mandatory aspect of MAC is that permissions are managed by dedicated administrators. In the confidentiality field with relatively high security requirements, MAC has built an access control model around MLS (Multi-Level Security, multi-level security). The MLS was originally conceived as a concentric circle with multiple layers of access control, with higher levels of security toward the center.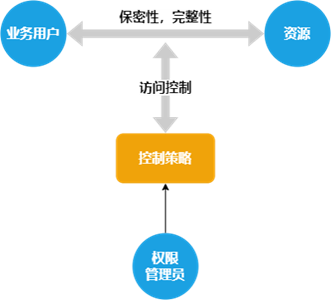
2. DAC DAC, autonomous access control. The autonomy of DAC is reflected in the fact that users can selectively share their resources with other users according to their own wishes.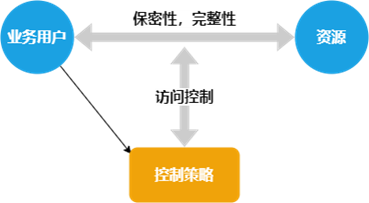
3. ACL/IBAC ACL, access control list. An ACL is a data structure, usually directly associated with a resource (such as a file, database record, or network resource), that lists the users with access rights and their access permissions (such as read, write, execute, etc.). An ACL usually consists of a set of rules (that is, ACL entries). Each ACL entry defines an access control policy, including allowing or denying specific types of access requests.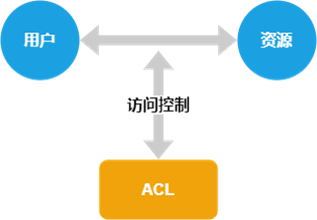
IBAC, identity-based access control. IBAC authorizes users to access resources based on their identity (such as username or user ID). Directly associating access rights with an individual's identity is one of the most intuitive methods of access control. IBAC places more emphasis on the role of user identity and controls access rights through identity information. The IBAC model realizes the association between users and permissions by associating the user's identity information with the access permissions of resources. The core of IBAC is the use of ACLs to define which users can access which resources.
4. RBAC RBAC, role-based access control. RBAC is the most widely used access control model in current information systems. The core concept of RBAC is that permissions are associated with roles, and users are assigned to the appropriate roles. A role is a user collection on one side and a permissions collection on the other. It acts as an intermediary that combines user collections and permissions collections. 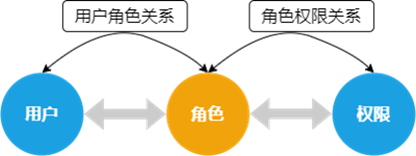 In the open source field, RBAC's famous open source frameworks include Spring Security and Apache Shiro.
In the open source field, RBAC's famous open source frameworks include Spring Security and Apache Shiro.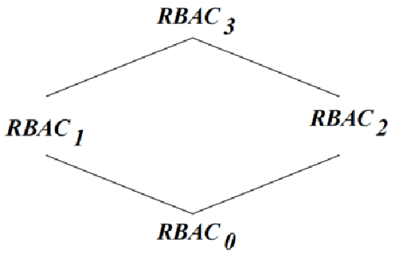
In practice, RBAC has gradually developed four reference models based on different application scenarios: • RBAC0: basic model, the minimum requirement for any system claiming to support RBAC; • RBAC1: advanced model, based on RBAC0, adding roles Hierarchy function. A role can be a member of a role, or it can inherit permissions from its parent; • RBAC2: Advanced model, based on RBAC0, adds the function of separation of duties to avoid conflicts of interest caused by users having too many permissions. Common separation of duties include static mutually exclusive roles, runtime mutually exclusive roles, cardinality constraints (total number of roles), prerequisite constraints, etc.; • RBAC3: Advanced model, based on RBAC0, combines the advantages of RBAC1 and RBAC2.
5. ABAC ABAC, attribute-based access control. ABAC uses the attributes of related entities as the basis for authorization, and makes authorization judgments by dynamically calculating whether one or a group of attributes satisfies certain conditions.
ABAC's access control policy: Users with u attributes are allowed/forbidden to perform operations with o attributes on resources with d object attributes under c attribute conditions (u, c, d, o are random examples). Therefore, the core of ABAC is 4 types of entity attributes: User attributes, attributes possessed by users, such as age, department, position, etc.; Environmental attributes, environmental condition factors of access control, such as current time, time allowed to access, and subclasses allowed to access. Network, etc.; Resource attributes, attributes possessed by resources, such as file type, data sensitivity, etc.; Operation attributes, allowed operation types, such as read, write, execute, etc.
ABAC can achieve very flexible permission control and can theoretically meet almost all types of access control needs.
6. LBAC LBAC, label-based access control. In LBAC, users and data are assigned labels, and comparisons are made based on the labels to determine whether the user can access the data. The relationship between users, data and tags can be described by the following diagram. Data labels: specify the sensitivity of data rows; User labels: provide appropriate authorization for users; Access mediation between users and data depends on the user's labels.
4. Requirements of database standards on access control
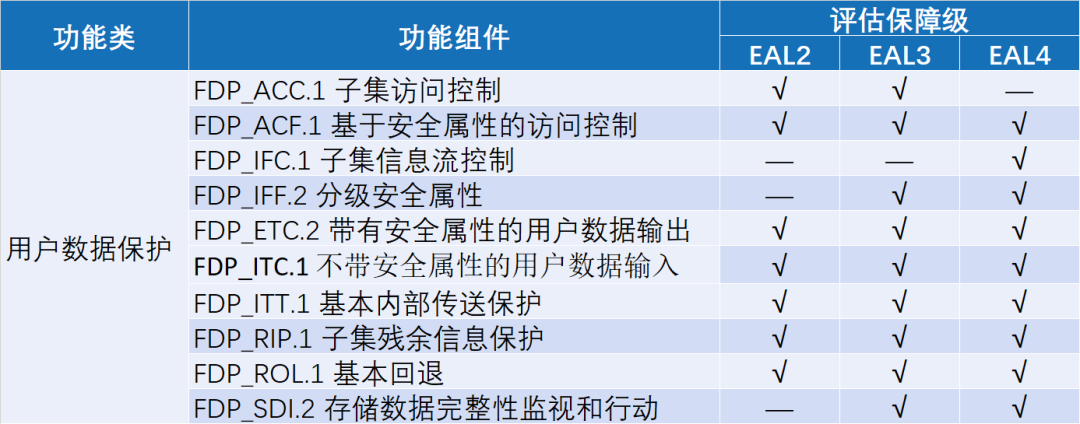
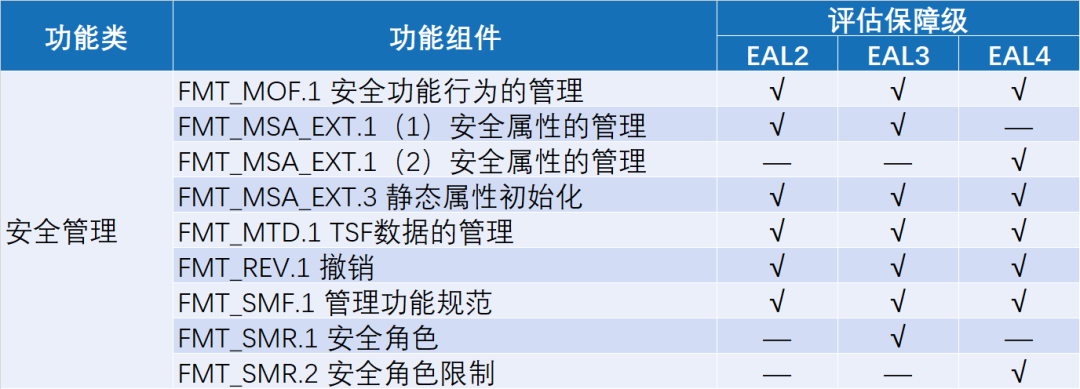
"GB/T 20273-2019 Information Security Technology - Security Technical Requirements for Database Management Systems", the requirements for access control mainly involve 27 functional components in three major functional categories.
User data protection
Identification and identification

Security management
5. KaiwuDB access control
KaiwuDB access control also includes two parts: identity authentication and access control.
KaiwuDB identity authentication
1. Password-based identity authentication KaiwuDB supports password-based identity authentication. User password security measures:
- Password storage encryption method (international algorithm and commercial secret algorithm)
- The password cannot contain the username and its reverse sequence
- Password minimum length limit
- Maximum password length limit
- Number of uppercase letters
- Number of lowercase letters
- Number of digits
- Special symbol digits
- Limit on the number of categories of characters included (uppercase letters, lowercase letters, numbers, special symbols)
2. Certificate-based identity authentication KaiwuDB supports identity authentication based on TLS certificates. The expiration time and certificate chain of the certificate can be verified, and the Common Name in the certificate and the user name in the database system can be verified.
3. Identity authentication based on three-party unified authentication KaiwuDB supports identity authentication based on three-party unified authentication and supports the GSSAPI authentication framework. The specific implementation is Kerberos V5 unified authentication.
4. 2FAK aiwuDB supports 2FA based on TLS certificate and password.
5. HBAK aiwuDB supports the configuration of specified access types, specified access resources, specified sources, specified user identity authentication methods and their authentication parameters, thereby enabling flexible configuration of identity authentication methods.
KaiwuDB access control
1. Access control list KaiwuDB supports access control lists to directly manage access control permissions for users and database objects.
2. RBACKaiwuDB supports the RBAC1 model, can perform access control based on roles, and supports role hierarchical management and permission inheritance.
3. LBACKaiwuDB supports LBAC access control and can perform access control based on tags. Labels currently support the Level component, which marks the user's permitted access level and the data's sensitivity level. Users can only access data with a lower sensitivity level than their permitted access level.
4. ABACKaiwuDB supports ABAC and can perform access control based on attributes. The user attributes supported by ABAC are:
- CREATEDB/NOCREATEDB: Allow/disable the user's CREATE DATABASE operation.
- CREATEROLE/NOCREATEROLE: Allow/disable the user's CREATE ROLE and CREATE USER operations.
- LOGIN/NOLOGIN: Allow/disable user login.
- FAILED_LOGIN_ATTEMPTS: The maximum number of failed login attempts allowed for a user. CONNECTION LIMIT: The maximum number of concurrent login connections allowed for users.
- VALID UNTIL: The user's password validity period. After the validity period, login is not allowed.
6. Future planning of KaiwuDB access control
1. Future planning for identity authentication
The future planning of identity authentication mainly plans to implement the following functions:
- 2FA/MFA: In addition to 2FA of user password and certificate, it supports more 2FA and MFA identity authentication, such as adding verification code, OTP, etc.
- Three-party unified authentication and identity authentication: In addition to Kerberos V5, it supports three-party unified authentication such as LDAP and Radius.
2. Future planning of access control
The future planning of access control mainly plans to implement the following functions: security role restrictions:
- Supports the RBAC3 model, including separation of duties functions, such as separation of three powers or separation of more roles and responsibilities.
- LBAC function enhancement: From the current Level component to LBAC including Level, Compartment and Group components, and on this basis, more fine-grained access control such as column level and row level can be implemented.
