1. 引言
Standford大学Dan Boneh等人2003年论文《A Survey of Two Signature Aggregation Techniques》。
针对的场景主要为:
Given
signatures on
distinct messages from
distinct users, it is possible to aggregate all these signatures into a single signature.
This single signature (and all
original messages) will convince any verifier that the
users signed the
original messages (i.e., for
, user
signed message number
).
实际应用有:
- in a Public Key Infrastructure (PKI) of depth , user signatures are accompanied by a chain of certificates. The chain contains signatures by Certificate Authorities (CAs) on distinct certificates.
- in the Secure BGP protocol (SBGP) each router receves a list of signatures attesting to a certain path of length in the network. A router signs its own segment in the path and forwards the resulting list of signatures to the next router. The number of signatures in routing messages is linear in the length of the path.
以上两种应用场景,都将受益于a method for compressing the list of signatures on distinct messages issued by distinct parties. 而aggregate signature可实现这样的compression压缩。
1.1 aggregate signature与multisignature的关系
multisignature是多个用户对 同一消息 进行签名,最终结果为a single signature。
而aggregate signature 是需要combine signatures on distinct messages into an aggregate。
本论文中,主要调查了2套签名方案:
- general aggregation: short signature scheme of Boneh, Lynn, and Shacham.
- sequential aggregation: Micali, Ohta, and Reyzin的multisignature scheme——built from any trapdoor permutation.
假设 个users的公私钥对分别为 ,User 希望签名的消息为 。
2. General aggregate signatures
在general aggregate signature机制中,user
对它的消息
生成签名
。
将
个不同的签名
通过a public aggregation algorithm来压缩为a single signature
。同时存在aggregate verification algorithm,根据
,来验证aggregate signature是否有效。
aggregation algorithm和aggregate verification algorithm:
- aggregation algorithm:输入为signatures on respective messages under respective public keys 。输出为a single aggregate signature 。
- aggregate verification algorithm:输入为an aggregate signature ,messages 以及public keys ,验证 is a valid aggregate signature on the given messages under the given keys。
an aggregate signature可提供non-repudiation不可抵赖性at once on many different messages by many users。
general aggregate signature之所以为general,是因为public aggregation algorithm可由任何人执行,且不需要与签名者进行交互。
Boneh, Lynn, and Shacham等人2003年论文《Aggregate and verifiably encrypted signatures from bilinear maps》中利用bilinear maps form algebraic geometry 实现了a general aggregate signature scheme。
2.1 Bilinear Maps
general aggregate signature的底层数学基础主要有:
- Gap Diffie-Hellman groups:arise from a separation between Computational Diffie-Hellman and Decision Diffie-Hellman;
- bilinear groups:arise from the presence of a bilinear map, a function with certain properties。
Consider a multiplicative cyclic group of prime order , with generator 。
- Computational Diffie-Hellman(CDH):Given ,计算 。CDH assumption是指计算 为computationally infeasible。
- Decision Diffie-Hellman(DDH):Given , decide whether equals . Tuples of this form—— ——are termed Diffie-Hellman tuple。DDH assumption是指在不知道的 或者 的情况下,很难判断 是否等于 。【但是,参见2.2.2节,借助bilinear group 可使DDH assumption不成立。】(参见博客 基于Sigma protocol实现的零知识证明protocol集锦 2.7节 Inequality of discrete logs中,若知道witness 或 ,则可判断 是否成立。)
2.1.1 GDH Groups (Gap Diffie-Hellman groups)
对于大多数的cyclic group
来说,如subgroups of
,CDH和DDH assumption均成立。
但是,on certain elliptic-curve groups【如存在bilinear map的groups】,DDH problem is easy to solve, whereas CDH is believed hard [6,22]. CDH assumption成立而DDH assumption不成立的groups 称为 Gap Diffie-Hellman (GDH) groups。
2.1.2 Bilinear groups
目前,the only known examples of GDH groups have additional structure, namely, a bilinear map.
A bilinear map is a map
,其中
为another multiplicative cyclic group of prime order
。具有如下属性:
- Computable可计算性:即存在有效的算法用于计算 ,for all 。
- Bilinear:对于所有的 , 成立。
- Non-degenerate:即 。
以上属性还可衍生为:【参见Boneh, Lynn, and Shacham等人2003年论文《Aggregate and verifiably encrypted signatures from bilinear maps》】
- for any , 成立。
- for any , 成立。
任何拥有map (满足如上属性)且CDH assumption成立的group,都可称为bilinear group。
bilinear map
可用于解决DDH问题,如已知
有:
从而使得DDH assumption不成立。
结论为:
若group
为bilinear group,则
也为GDH group。
假设
为an elliptic curve,设置
为 a subgroup (of prime order
) of the curve’s group of points
。
On certain cuves, the Weil pairing和modified Tate pairing可生成a bilinear map
,其中group
为a subgroup of
,
为a security multiplier that depends on the curve and on the group
。
multiplier
的取值需要权衡efficiency和security。
值越小,bilinear map的运算越快;而
值越大,则安全系数更高,the more difficult is the CDH problem on
。
目前的CDH algorithms on
require solving the discrete logarithm problem either in the generic group
(of order
) or in the finite field
。
MNT 家族curves具有large subgroups with security multiplier ,可满足要求。
2.2 BLS Signature Scheme
(可参见博客 ECDSA VS Schnorr signature VS BLS signature 第3节内容。)
BLS short signature scheme works in any Gap Diffie-Hellman group ,同时额外需要a hash function from the message space onto the group 。
假设
为a GDH group of prime order
,with a hash function
(可被认为是a random oracle)。
任何string可都被前面,BLS signature为 a single element of
,整个BLS signature的流程如下:
- Key Generation:选择随机数 ,计算 。公钥为 ,私钥为 。
- Signing:输入为私钥 和消息 ,计算 。BLS签名为 。
- Verification:输入为公钥 ,消息 以及a signature ,计算 ,验证 为a valid Diffie-Hellman tuple。(其实即是验证 是否成立。)
Its security against existential forgery under a chosen message attack can be shown based on the CDH assumption in [6].
BLS签名 ,可只取 坐标表示(BLS remains valid and secure even if only the x-coordinate of every signature point is transimitted.)。
对于MNT curve (with
) over a 170-bit field, BLS签名的长度为170bits,同时provide security comparable to that of 1024-bit RSA或者是320-bit DSA。
BLS signatures are half the size of DSA with comparable security。
BLS signature可扩展为threshold signature, multisignature以及blind signature。
2.3 Bilinear Aggregate Signatures
bilinear aggregate signature要求group 为a bilinear group,而仅仅为general GDH group是不够的。
bilinear aggregate signature中引入了a random oracle hash function,输入为a string和an element of : 。
bilinear aggregate signature可支持general aggregation,可允许任何人来combine pre-existing signatures into an aggregate,对aggregated elements的顺序无要求,如果确实需要的话,可在待签名消息上附加index numbers。
Bilinear Aggregate Signatures在BLS Signature Scheme的基础上,增加了Aggregation和Aggregate Verification算法:
- Key Generation:选择随机数 ,计算 。公钥为 ,私钥为 。
- Signing:输入为私钥 、消息 和公钥 ,计算 。BLS签名为 。
- Verification:输入为公钥 ,消息 以及a signature ,计算 ,验证 为a valid Diffie-Hellman tuple。(其实即是验证 是否成立。)
- Aggregation:Arbitrarily assign to each user whose signature will be aggregated an index , ranging from to . Each user provides a signature on a message of her choice. 计算 。The aggregate signature is 。
- Aggregation Verification:输入为an aggregate signature for a set of users indexed as before,original messages and public keys 。计算 for ,验证 是否成立。(根据2.1.2节衍生属性可知其应成立。)
Bilinear Aggregate Signatures的安全性:当仅仅知道messages,public keys和the aggregate signature 时,从 中恢复各个单独的signatures 为hard。其安全性等价为CDH assumption,详细可参见Coron等人2003年论文《k-element aggregate extraction assumption is equivalent to the Diffie-Hellman assumption》。
Bilinear Aggregate Signatures支持incremental aggregation,即:
已知一个基于消息
under public keys
的aggregate signature
。
- 增加一个签名 (on a message M_{n+1} under public key ) 可以aggregate为: 。
- 若 中的某个signature 已知,则可从aggregate中移除: 。
3. Sequential aggregate signature
在sequential aggregation signature机制中,signature aggregation仅能在签名过程中实现。每个签名者依次在current aggregate的基础上添加自己的签名。在aggregate signature中有明确的顺序要求,签名者之间在aggregation过程中must communicate with each other。
sequential aggregation signature是分层构建的,像洋葱依样,第一各签名aggregate后在最里层。基本流程为:
- User 1 signs to obtain ;
- User 2 then combines and to obtain ;(aggregate和签名操作是在一起进行的。)
- The final signature binds user to for all 。
sequential aggregation signature的最终长度与ordinary signature的长度一样。
可基于类似RSA的homomorphic trapdoor permutation来实现sequential aggregate signature。
Micali, Ohta, and Reyzin 1999年论文《Provable subgroup signatures》(手稿,未发表)中的multisignature scheme可实现sequential aggregate signature,且Shacham 在其2003年论文《Sequential aggregate signatures from trapdoor homomorphic permutations》中进行了分析。
尽管general aggregation is more powerful than sequential aggregation,但是sequential aggregation可基于标准的primitives如RSA等来构建。
general aggregation和sequential aggregation均可用于compressing signatures in a certificate chain。
3.1 Trapdoor Homomorphic Permutations
sequential aggregation signature是基于trapdoor homomorphic permutation构建的。
permutation family
定义:
a collection of permutations of some domain
. 每个
中的permutation均有a description
。Anyone given a description
can evaluate the corresponding permutation。
permutation family 具有one-way属性,即给定permutation description , it’s infeasible to invert the corresponding permutation.
permutation family
具有trapdoor属性,若每个description
都有相应的trapdoor
使得it’s easy to invert the permutation corresponding to
with
,而infeasible without
。
trapdoor permutation family肯定是one-way的。
permutation family
主要由Generate,Evaluate和Invert算法组成:
- Generate:输出description of a permutation along with the corresponding trapdoor 。
- Evaluate :输入为description 和a value ,输出为 , 为the image of under the permutation。
- Invert:输入为description ,trapdoor 和a value ,输出为the preimage of under the permutation。
以上算法需满足: be a permutation of for all ,而 hold for all and for all 。
trapdoor permutation具有homomorphic属性,若在group内满足:若
,则有
。
可将Generate算法的输出理解为a probability distribution
on permutations,表示为
,其中
对应为the permutation
,而
为the inverse permutation
。
permutation family 中的每个permutation可对应different domain 。
3.2 Full-domain signatures
Full-domain signatures scheme中引入了一个random-oracle hash function 。该hash函数可maps bit strings into the entire domain (rather than some subset of )。
Full-domain signatures算法流程为:
- Key Generation:对于特定用户,选择随机 。该用户的公钥为 ,私钥为 。
- Signing:对于特定用户,输入为私钥 ,message ,计算 ,其中 ,计算 。The signature is 。
- Verification:输入为特定用户的公钥 ,message 和a signature ,计算 ,验证 是否成立。
即,用户通过 来签名,通过判断 来验签。
若 为a trapdoor permutation family,则对当前已存在的existential forgery under a chosen message attack是安全的;若 同时具有Homomorphic属性,则其security reduction将更有效。
3.3 Sequential Aggregate Signatures
Sequential Aggregate Signatures是基于具有homomorphic属性trapdoor permutation的full-domain hash signature scheme构建的。
以下Sequential Aggregate Signatures scheme是基于Micali, Ohta, and Reyzin 1999年论文《Provable subgroup signatures》(手稿,未发表)中的multisignature scheme来实现的。
论文中用到的向量基本定义如下:
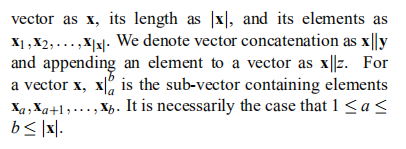
Sequential Aggregate Signatures算法流程为:
- Key Generation:对于特定用户,选择随机 。该用户的公钥为 ,私钥为 。
- Aggregate Signing:输入为私钥
,待签名message
以及a sequential aggregate signature
on a vector of messages
under a vector of public keys
。 No key may appear twice in
,同时要求vectors
和
的长度应该相同。当
时,
值必须为1(即the unit of
)。
计算 ,其中 ,计算 。The sequential aggregate signature is 。 - Aggregate Verification:输入为a sequential aggregate signature on messages under public keys ,其中 。验证时,首先设置 ,然后 for ,依次计算 ,验证 是否等于 。
以
理念表示的话,sequential aggregate signature可表示为:
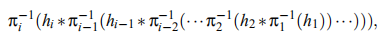
其中
。
若 为homomorphic trapdoor permutation family,则 trapdoor sequential aggregate signature scheme也是安全的。同时认为,只要forger没有获取到所有的私钥(如有1个私钥是安全的),则该forger无法frame the remaining honest user。
3.4 Aggregating with RSA
RSA算法可参见博客 密码学算法——RSA。
具体为:
- , 为2个large primes。
- ,其中 为私钥, 为公钥。
- 为a permutation on , 为其inverse。
难点在于,两个用户无法共享相同的modulus
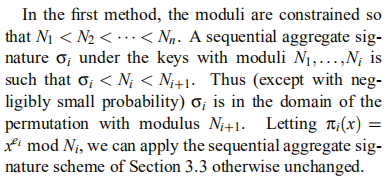
,有2种方法来解决:
(假设
个用户的moduli分别为
,要求这些moduli具有接近的size,即
,假设
为所有
中的最小值。The hash function
maps into the set
,对于无法map进去的,可iterating the hash(参见Bellare and Rogaway 1993论文《A paradigm for designing efficient protocols》第4章方法)。)
- 第一种方法:约束
。
- 第二种方法:对moduli无约束。
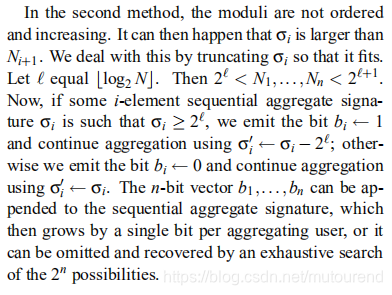
第一种方法对signing keys的选择限制更多。而第二种方法生成的aggregate signatures grow by one bit per signature。两种方法都不再是full-domain hash signature schemes,但是由于所有的moduli具有几乎相同的size, Coron的partial-domain hash anayasis [9]可适用。