版权声明:转载声明来源,请勿用于商业用途! https://blog.csdn.net/qq_27180763/article/details/83788880
SQL约束攻击环境搭建
MYSQL:
表结构:
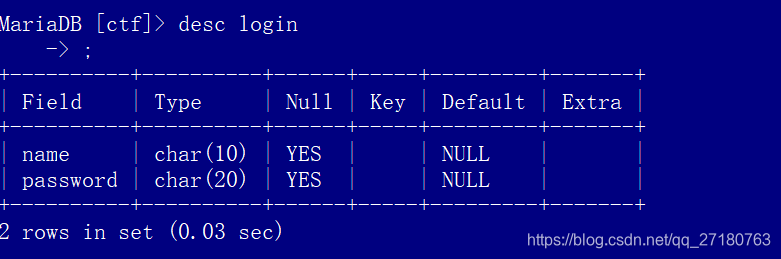
创建表命令:create table ctf(name char(10),password char(20));
表内数据:
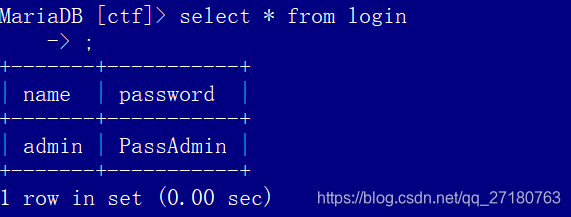
插入命令:insert into ctf values(‘admin’,‘PassAdmin’);
PHP
LOGIN页面:
<html>
<head><title>登陆系统</title></head>
<body>
<center>
<h1>欢迎来到登陆系统!</h1>
<h3>第一个注册的用户为:admin</h3>
</center>
<form action="./login.php" method="post">
<center><input type="text" name="username" placeholder="请输入用户名"></center>
<center><input type="text" name="password" placeholder="请输入密码" ></center>
<center><input type="submit" name="submit"></center>
</form>
<center><a href="./register.php">没有账号点这里!!!</a><br><br></center>
</body>
</html>
<?php
if(isset($_POST['submit'])){
$username = $_POST['username'];
if($username == 'admin'){
echo "<center>admin已被禁用!</center>";
exit(0);
}
$password = $_POST['password'];
try{
$db = new PD('mysql:host=7fp9co9h.2326.dnstoo.com:5505;dbname=czlgj','czlgj_f','Wa360218171');
}catch(PDOException $e){
echo $e;
}
$query = "select * from login where name = ? and password = ?;";
$sql = $db -> prepare($query);
$sql->execute(array($username,$password));
$arr = $sql->fetchAll();
$arr[0][0] = str_replace(' ','',$arr[0][0]);
echo "<center>当前用户为:".$arr[0][0]."</center><br>";
if(!empty($arr) && trim($arr[0][0] == 'admin'))
{
echo "GJCTF{RandLpsxQQQ}";
exit(0);
}else if(!empty($arr)){
echo "<center>登陆成功。然并卵。</center>";
exit(0);
}else{
echo "登陆失败。";
exit(0);
}
}
?>
注册界面:
<html>
<head><title>注册</title></head>
<body>
<center><h1>欢迎来到注册页面</h1></center>
<center><h3>title:admin已被注册</h3></center>
<center>
<form action="./register.php" method="post">
<input type="text" name="username" placeholder="请输入用户名"><br><br>
<input type="text" name="password" placeholder="请输入密码"><br><br>
<input type="text" name="password2" placeholder="请再次输入密码"><br><br>
<input type="submit" name="submit" value="提交"><br><br>
</form>
</center>
</body>
</html>
<?php
if(!empty($_POST['submit']))
{
$username = addslashes(htmlspecialchars($_POST['username']));
$password = addslashes(htmlspecialchars($_POST['password']));
$password2 = addslashes(htmlspecialchars($_POST['password2']));
if($username == 'admin'){
echo "<script>alert('admin已被注册!');window.location.href='./register.php';</script>";
exit(0);
}
if($password !=$password2){
echo "<script>alert('请确保两次输入的密码相同。');window.location.href='./register.php';</script>";
exit(0);
}
try{
$db = new PDO('mysql:host=7fp9co9h.2326.dnstoo.com:5505;dbname=czlgj','czlgj_f','Wa360218171');
}catch (PDOException $e){
echo $e;
}
$sql = $db->prepare("insert into login values(?,?)");
$sql->execute(array($username,$password));
$number = $sql->rowCount();
if($number!=0){
echo "<script>alert('注册成功!');window.location.href='./login.php'</script>";
}else{
echo "<script>alert('注册失败!');window.location.href='./register.php';</script>";
}
}
?>
不过我自己搭了一个平台放在外网上了,有兴趣的可以上去看看。
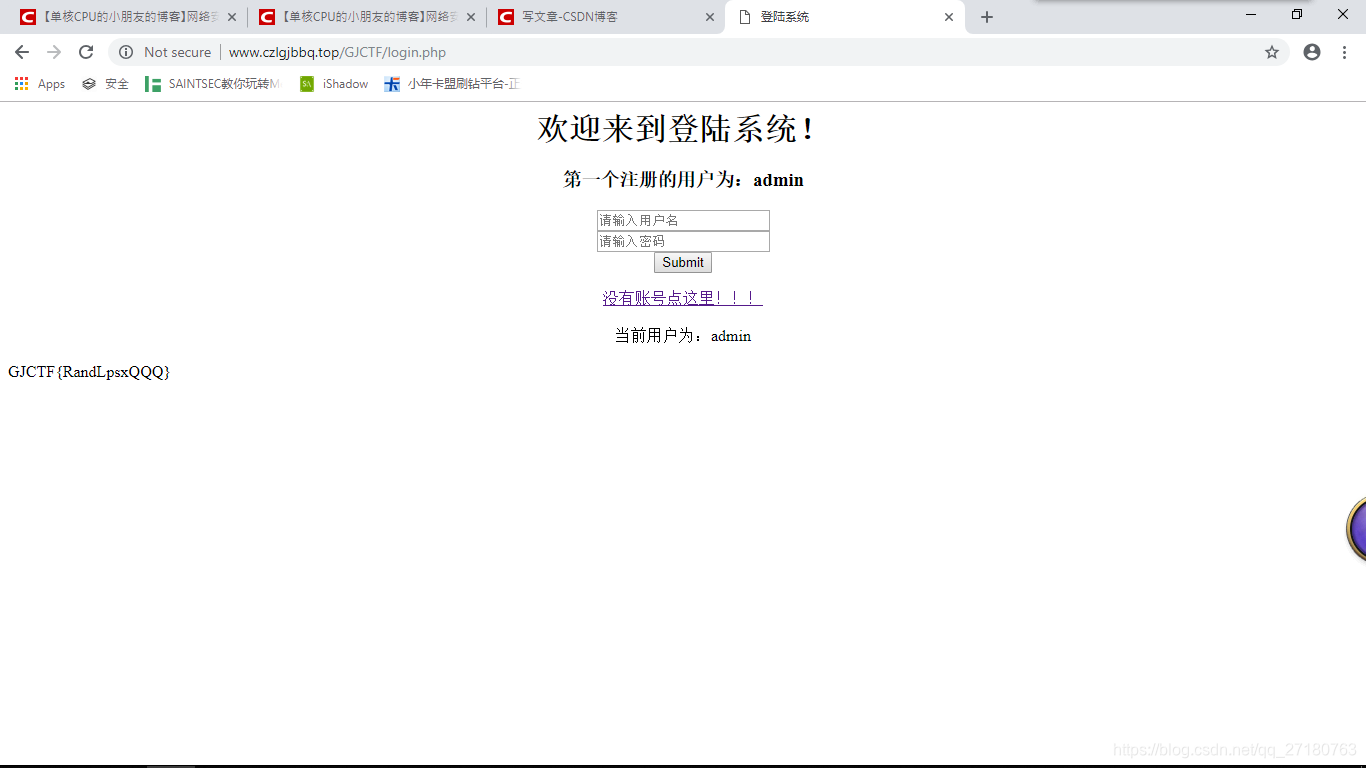
环境链接:http://www.czlgjbbq.top/GJCTF/login.php
攻击演示
用户名可以打很多的空格。密码随意。
登陆的时候直接登录,在数据库中会忽略用户名结尾的空格。所以就当成admin登陆了。所以就可以直接拿到flag了。