Algorithms
160. Intersection of Two Linked Lists
Write a program to find the node at which the intersection of two singly linked lists begins.
For example, the following two linked lists:
begin to intersect at node c1.
Example 1:
Input: intersectVal = 8, listA = [4,1,8,4,5], listB = [5,0,1,8,4,5], skipA = 2, skipB = 3
Output: Reference of the node with value = 8
Input Explanation: The intersected node's value is 8 (note that this must not be 0 if the two lists intersect). From the head of A, it reads as [4,1,8,4,5]. From the head of B, it reads as [5,0,1,8,4,5]. There are 2 nodes before the intersected node in A; There are 3 nodes before the intersected node in B.
Solution 1—— leetcode上的思路:listNodeA和listNodeB循环两遍,如果相等,则说明有重合的链表,如果没有循环两遍没有中止,那就没有重合的链表。
/**
* Definition for singly-linked list.
* public class ListNode {
* int val;
* ListNode next;
* ListNode(int x) {
* val = x;
* next = null;
* }
* }
*/
public class Solution {
public ListNode getIntersectionNode(ListNode headA, ListNode headB) {
//boundary check
if(headA == null || headB == null) return null;
ListNode a = headA;
ListNode b = headB;
//if a & b have different len, then we will stop the loop after second iteration
while( a != b){
//for the end of first iteration, we just reset the pointer to the head of another linkedlist
a = a == null? headB : a.next;
b = b == null? headA : b.next;
}
return a;
}
}
Review
Why I’m The Best Programmer In The World
1、Nobody is really smart enough to program computers.
2、The way you focus your intelligence is more important than how much intelligence you have.
3、The more humble you are,the faster you’ll improve.
4、it’s not our job to be better than anyone else;we just need to be better than we were a year ago.
Tips
网络知识基础协议——应用层:http和https。
1、http请求的格式
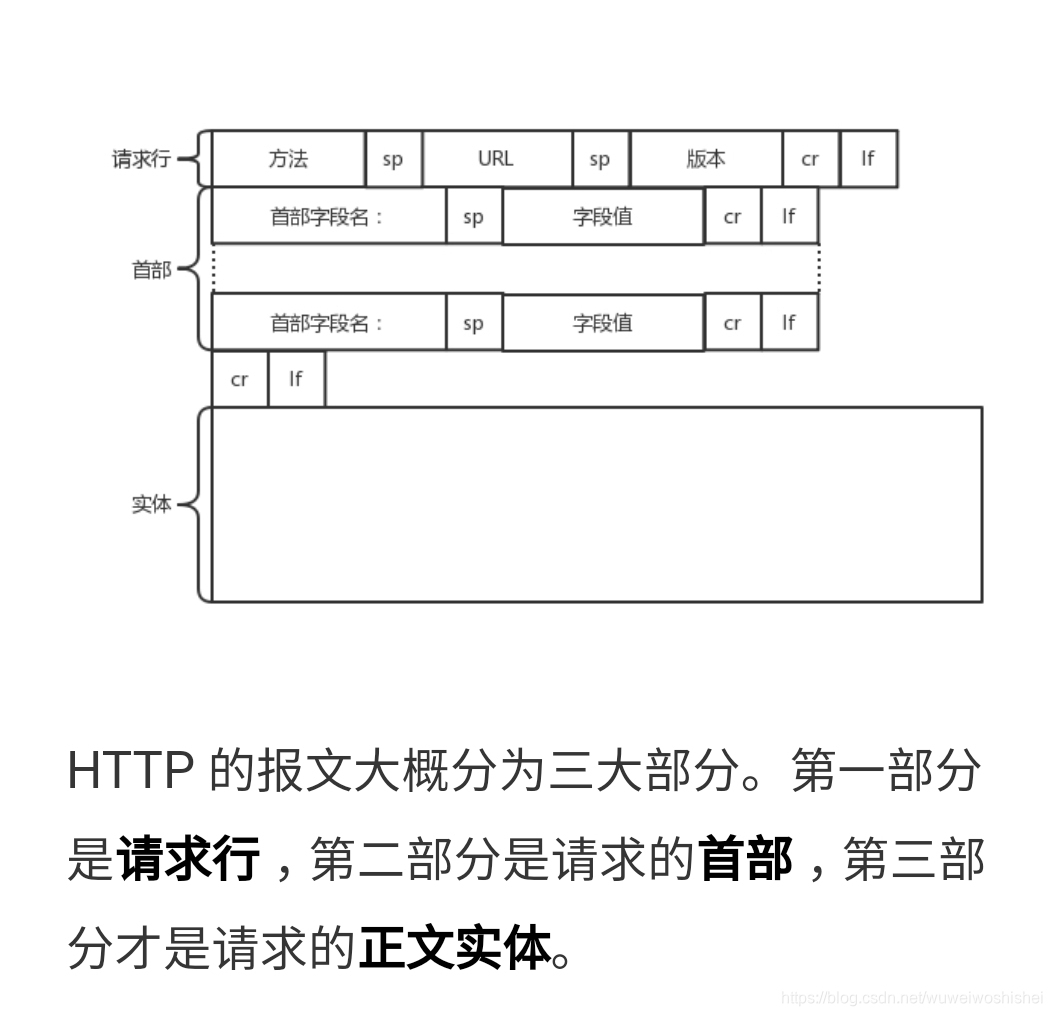
2、https的加密通信
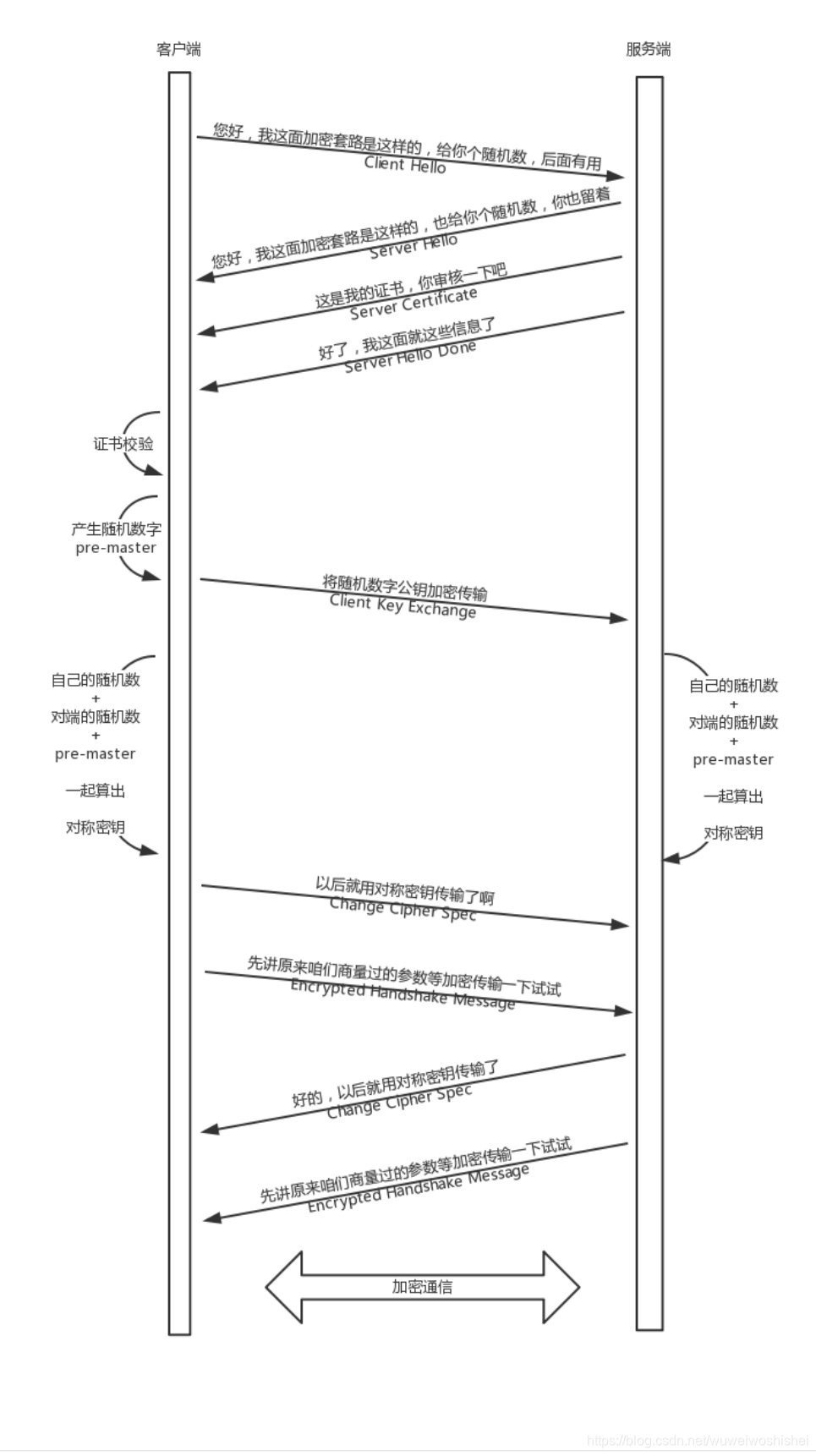
3、重放和篡改:通过Timestamp和Nonce随机数保证唯一,如果服务器多次收到相同的Timestamp和Nonce,则视为无效,可以防止重放攻击。签名可以保证信息的不可篡改性,如果改了用签名算法解出来,就对不上了,可以丢弃了。