官方提供了三种安装方式
minikubeMinikube
是一个工具,可以在本地快速运行一个单点的Kubernetes,仅用于尝试Kubernetes或日常开发的用户使用。部署地址:https://kubernetes.io/docs/setup/minikube/
kubeadmKubeadm
也是一个工具,提供kubeadm init和kubeadm join,用于快速部署Kubernetes集群。部署地址:https://kubernetes.io/docs/reference/setup-tools/kubeadm/kubeadm/
二进制包推荐
从官方下载发行版的二进制包,手动部署每个组件,组成Kubernetes集群。下载地址:https://github.com/kubernetes/kubernetes/releases
我们选择二进制包安装
一、规划服务器
| 主机 | ip | 作用 |
|---|---|---|
| master 01 | 192.168.13.134 | master01节点 |
| master 02 | 192.168.13.135 | master01节点 |
| etcd 01 | 192.168.13.134 | 数据库01节点 |
| etcd 02 | 192.168.13.135 | 数据库02节点 |
| etcd 03 | 192.168.13.136 | 数据库03节点 |
| node01 | 192.168.13.134 | node01节点 |
| node02 | 192.168.13.135 | node02节点 |
| node03 | 192.168.13.136 | node03节点 |
| slb01 | 192.168.13.134 | 负载均衡主节点 |
| slb02 | 192.168.13.135 | 负载均衡备节点 |
生产环境双master高可用,数据库最少三台,奇数增加。node节点最少五个,可以用云服务器SLB进行负载均衡,也可以使用nginx+keepa高可用。
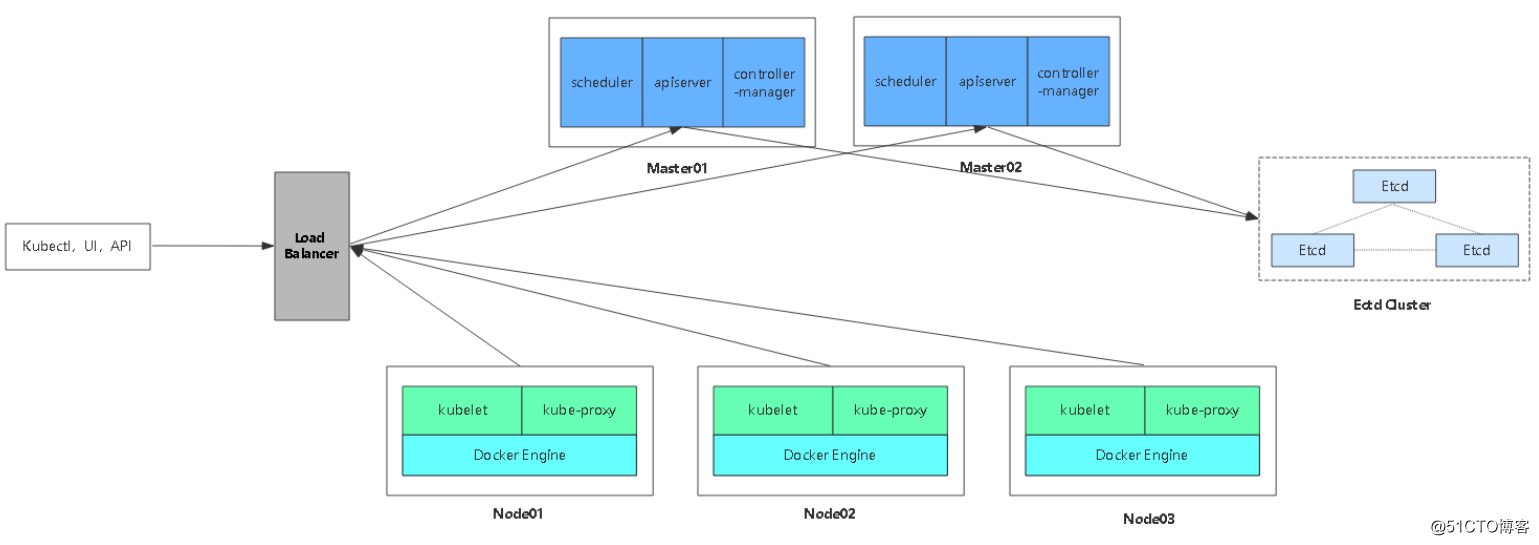
1.1、部署Etcd集群
1.1.1、生成Etcd SSL自签证书
使用cfssl来生成自签证书,先下载cfssl工具

curl -L https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 -o /usr/local/bin/cfssl
curl -L https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 -o /usr/local/bin/cfssljson
curl -L https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64 -o /usr/local/bin/cfssl-certinfo
chmod +x /usr/local/bin/cfssl /usr/local/bin/cfssljson /usr/local/bin/cfssl-certinfo
创建以下三个文件,用来生成证书
# cat ca-config.json
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"www": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
# cat ca-csr.json
{
"CN": "etcd CA",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Beijing",
"ST": "Beijing"
}
]
}
# cat server-csr.json
{
"CN": "etcd",
"hosts": [
"192.168.13.134",
"192.168.13.135",
"192.168.13.136"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "BeiJing",
"ST": "BeiJing"
}
]
}生成证书
cfssl gencert -initca ca-csr.json | cfssljson -bare ca -
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=www server-csr.json | cfssljson -bare server
# ls *pem
ca-key.pem ca.pem server-key.pem server.pem
1.1.2、部署Etcd集群
二进制包下载地址:https://github.com/etcd-io/etcd/releases
以下部署步骤在规划的三个etcd节点操作一样,唯一不同的是etcd配置文件中的服务器IP要写当前的
解压二进制包:
# mkdir /opt/etcd/{bin,cfg,ssl} -p
# tar zxvf etcd-v3.2.12-linux-amd64.tar.gz
# mv etcd-v3.2.12-linux-amd64/{etcd,etcdctl} /opt/etcd/bin/创建etcd配置文件
# cat /opt/etcd/cfg/etcd
#[Member]
ETCD_NAME="etcd01"
ETCD_DATA_DIR="/var/lib/etcd/default.etcd"
ETCD_LISTEN_PEER_URLS="https://192.168.13.134:2380" #本机ip地址,server端口
ETCD_LISTEN_CLIENT_URLS="https://192.168.13.134:2379" #本机ip地址,数据库端口
#[Clustering]
ETCD_INITIAL_ADVERTISE_PEER_URLS="https://192.168.13.134:2380"
ETCD_ADVERTISE_CLIENT_URLS="https://192.168.13.134:2379"
ETCD_INITIAL_CLUSTER="etcd01=https://192.168.13.134:2380,etcd02=https://192.168.13.135:2380,etcd03=https://192.168.13.136:2380"
ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"
ETCD_INITIAL_CLUSTER_STATE="new"• ETCD_NAME #节点名称
• ETCD_DATA_DIR #数据目录
• ETCD_LISTEN_PEER_URLS #集群通信监听地址
• ETCD_LISTEN_CLIENT_URLS #客户端访问监听地址
• ETCD_INITIAL_ADVERTISE_PEER_URLS #集群通告地址
• ETCD_ADVERTISE_CLIENT_URLS #客户端通告地址
• ETCD_INITIAL_CLUSTER #集群节点地址
• ETCD_INITIAL_CLUSTER_TOKEN #集群Token
• ETCD_INITIAL_CLUSTER_STATE 加入#集群的当前状态,new是新集群,existing表示加入已有集群
systemd管理etcd:
# cat /usr/lib/systemd/system/etcd.service
[Unit]
Description=Etcd Server
After=network.target
After=network-online.target
Wants=network-online.target
[Service]
Type=notify
EnvironmentFile=/opt/etcd/cfg/etcd
ExecStart=/opt/etcd/bin/etcd \
--name=${ETCD_NAME} \
--data-dir=${ETCD_DATA_DIR} \
--listen-peer-urls=${ETCD_LISTEN_PEER_URLS} \
--listen-client-urls=${ETCD_LISTEN_CLIENT_URLS},http://127.0.0.1:2379 \
--advertise-client-urls=${ETCD_ADVERTISE_CLIENT_URLS} \
--initial-advertise-peer-urls=${ETCD_INITIAL_ADVERTISE_PEER_URLS} \
--initial-cluster=${ETCD_INITIAL_CLUSTER} \
--initial-cluster-token=${ETCD_INITIAL_CLUSTER_TOKEN} \
--initial-cluster-state=new \
--cert-file=/opt/etcd/ssl/server.pem \
--key-file=/opt/etcd/ssl/server-key.pem \
--peer-cert-file=/opt/etcd/ssl/server.pem \
--peer-key-file=/opt/etcd/ssl/server-key.pem \
--trusted-ca-file=/opt/etcd/ssl/ca.pem \
--peer-trusted-ca-file=/opt/etcd/ssl/ca.pem
Restart=on-failure
LimitNOFILE=65536
[Install]
WantedBy=multi-user.target
**把刚才生成的证书拷贝到配置文件中的位置:**
# cp ca*pem server*pem /opt/etcd/ssl注意:将完整的一份Etcd目录,复制到其他两个etcd服务器,只需修改ip地址即可
最后启动三台etcd
# systemctl start etcd
# systemctl enable etcd检查健康状态
[root@k8s-matser01 k8s]# /opt/etcd/bin/etcdctl --ca-file=/opt/etcd/ssl/ca.pem --cert-file=/opt/etcd/ssl/server.pem --key-file=/opt/etcd/ssl/server-key.pem --endpoints="https://192.168.13.134:2379,https://192.168.13.135:2379,https://192.168.13.136:2379" cluster-health
出现如下输出,表示etcd集群完成
member 98d5f0d49711f89d is healthy: got healthy result from https://192.168.13.135:2379
member b37efb70492212de is healthy: got healthy result from https://192.168.13.136:2379
member ffd0c8087276f422 is healthy: got healthy result from https://192.168.13.134:2379
cluster is healthy