0x01、实验环境
1、靶机:Metasploitable(192.168.97.140)
浏览器访问:http://192.168.97.140/dvwa
Username=admin
Password=password
2、攻击机:kali(192.168.97.129)
0x02、Httrack工具
1、Httrack:是一种专门针对Web服务器的一种工具
//其可以把站点下所有文件拷贝下来
2、httrack实战
例子1:
靶机:Metasploitable(192.168.97.140)
攻击机:kali(192.168.97.129)
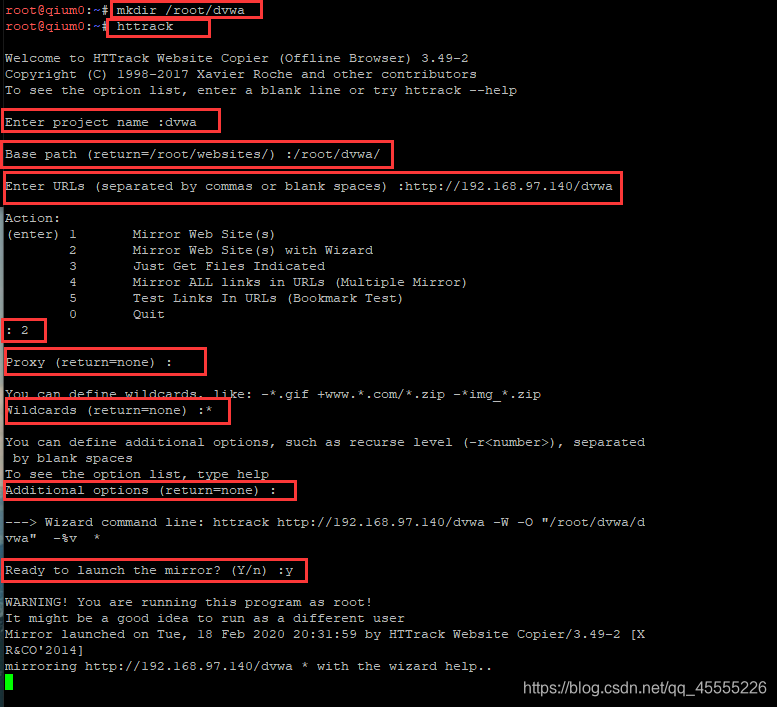
kali上:
mkdir /root/dvwa
#httrack
dvwa
http://192.168.97.140
2
回车
*
回车
y
如下图所示:

0x03、扫描工具Nikto
1、Nikto简介
①、Perl语言开发的开源web安全扫描器
②、用来搜索存在安全隐患的文件
③、扫描服务器配置漏洞
④、扫描Web Application层面的安全隐患
⑤、避免404误判:
很多服务器不遵守RFC标准,对于不存在的对象返回200响应码;
依据响应文件内容判断,不同扩展名的文件404响应内容不同;
去除时间信息后的内容取MD5值;
⑥、-no404:提高性能,但是存在误判;
2、nikto命令
man nikto //查看使用手册
nikto -list-plugins //查看插件
nikto //查看版本等信息
nikto -host //后可加url,可加ip、域名(d端口号)
nikto -evasion //使用LibWhisker中对IDS的躲避技术
①、随机URL编码(非UTF-8方式)
②、自选择路径
③、过早结束路径(/./)
④、优先考虑长随机字符串
⑤、参数欺骗
⑥、使用TAB作为命令的分隔符
⑦、使用变化的URL
⑧、使用Windows路径分隔符"\"
3、nikto实战
例子1:利用nikto扫描站点
靶机:Metasploitable(192.168.97.140:80)或(http://192.168.97.140/dvwa)
1、
# nikto -host http://192.168.97.140/dvwa
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.97.140
+ Target Hostname: 192.168.97.140
+ Target Port: 80
+ Start Time: 2020-02-18 20:42:42 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) DAV/2
+ Cookie PHPSESSID created without the httponly flag
+ Cookie security created without the httponly flag
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.10
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Root page / redirects to: login.php
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /dvwa/robots.txt, inode: 93164, size: 26, mtime: Tue Mar 16 13:56:22 2010
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-3268: /dvwa/config/: Directory indexing found.
+ /dvwa/config/: Configuration information may be available remotely.
+ OSVDB-12184: /dvwa/?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /dvwa/?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /dvwa/?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /dvwa/?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /dvwa/login/: This might be interesting...
+ OSVDB-3268: /dvwa/docs/: Directory indexing found.
+ OSVDB-3092: /dvwa/CHANGELOG.txt: A changelog was found.
+ /dvwa/login.php: Admin login page/section found.
+ /dvwa/?-s: PHP allows retrieval of the source code via the -s parameter, and may allow command execution. See http://www.kb.cert.org/vuls/id/520827
+ /dvwa/login.php?-s: PHP allows retrieval of the source code via the -s parameter, and may allow command execution. See http://www.kb.cert.org/vuls/id/520827
+ /dvwa/CHANGELOG.txt: Version number implies that there is a SQL Injection in Drupal 7, can be used for authentication bypass (Drupageddon: see https://www.sektioneins.de/advisories/advisory-012014-drupal-pre-auth-sql-injection-vulnerability.html).
+ 7914 requests: 0 error(s) and 25 item(s) reported on remote host
+ End Time: 2020-02-18 20:43:09 (GMT8) (27 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
2、
# nikto -host 192.168.97.140:80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.97.140
+ Target Hostname: 192.168.97.140
+ Target Port: 80
+ Start Time: 2020-02-18 20:43:53 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) DAV/2
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.10
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ /phpinfo.php: Output from the phpinfo() function was found.
+ OSVDB-3268: /doc/: Directory indexing found.
+ OSVDB-48: /doc/: The /doc/ directory is browsable. This may be /usr/doc.
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /phpMyAdmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ Server may leak inodes via ETags, header found with file /phpMyAdmin/ChangeLog, inode: 92462, size: 40540, mtime: Wed Dec 10 01:24:00 2008
+ OSVDB-3092: /phpMyAdmin/ChangeLog: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3268: /test/: Directory indexing found.
+ OSVDB-3092: /test/: This might be interesting...
+ OSVDB-3233: /phpinfo.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpMyAdmin/: phpMyAdmin directory found
+ OSVDB-3092: /phpMyAdmin/Documentation.html: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3092: /phpMyAdmin/README: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ 8726 requests: 0 error(s) and 27 item(s) reported on remote host
+ End Time: 2020-02-18 20:44:21 (GMT8) (28 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
3、
# nikto -host 192.168.97.140 -p 80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.97.140
+ Target Hostname: 192.168.97.140
+ Target Port: 80
+ Start Time: 2020-02-18 20:47:19 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) DAV/2
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.10
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ /phpinfo.php: Output from the phpinfo() function was found.
+ OSVDB-3268: /doc/: Directory indexing found.
+ OSVDB-48: /doc/: The /doc/ directory is browsable. This may be /usr/doc.
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /phpMyAdmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ Server may leak inodes via ETags, header found with file /phpMyAdmin/ChangeLog, inode: 92462, size: 40540, mtime: Wed Dec 10 01:24:00 2008
+ OSVDB-3092: /phpMyAdmin/ChangeLog: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3268: /test/: Directory indexing found.
+ OSVDB-3092: /test/: This might be interesting...
+ OSVDB-3233: /phpinfo.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpMyAdmin/: phpMyAdmin directory found
+ OSVDB-3092: /phpMyAdmin/Documentation.html: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3092: /phpMyAdmin/README: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ 8726 requests: 0 error(s) and 27 item(s) reported on remote host
+ End Time: 2020-02-18 20:47:56 (GMT8) (37 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
4、
#vim host.txt
192.168.97.140:80
http://192.168.97.140/dvwa
:wq
# nikto -host host.txt
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.97.140
+ Target Hostname: 192.168.97.140
+ Target Port: 80
+ Start Time: 2020-02-18 20:51:13 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) DAV/2
+ Cookie PHPSESSID created without the httponly flag
+ Cookie security created without the httponly flag
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.10
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to pr otect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Root page / redirects to: login.php
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /dvwa/robots.txt, inode: 93164, size: 26, mtime: Tue Mar 16 13:56:22 2010
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brut e force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alt ernatives for 'index' were found: index.php
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 i s the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-3268: /dvwa/config/: Directory indexing found.
+ /dvwa/config/: Configuration information may be available remotely.
+ OSVDB-12184: /dvwa/?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially se nsitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /dvwa/?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially se nsitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /dvwa/?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially se nsitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /dvwa/?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially se nsitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /dvwa/login/: This might be interesting...
+ OSVDB-3268: /dvwa/docs/: Directory indexing found.
+ OSVDB-3092: /dvwa/CHANGELOG.txt: A changelog was found.
+ /dvwa/login.php: Admin login page/section found.
+ /dvwa/?-s: PHP allows retrieval of the source code via the -s parameter, and may allow command execution. See http://www.kb.cert.org/vuls/id/520827
+ /dvwa/login.php?-s: PHP allows retrieval of the source code via the -s parameter, and may allow command execution. See http://www.kb.cert.org/vuls/id/520827
+ /dvwa/CHANGELOG.txt: Version number implies that there is a SQL Injection in Drupal 7, can be used for authentication bypass (Drupageddon: see https://www.sektioneins.de/advisories/advisory-012014-drupal-pre-auth-sql-injection-vulnerability.html).
+ 7914 requests: 0 error(s) and 25 item(s) reported on remote host
+ End Time: 2020-02-18 20:51:39 (GMT8) (26 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
5、
# nikto -host www.baidu.com -port 443 --ssl
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 183.232.231.174
+ Target Hostname: www.baidu.com
+ Target Port: 443
---------------------------------------------------------------------------
+ SSL Info: Subject: /C=CN/ST=beijing/L=beijing/OU=service operation department/O=Beijing Baidu Netc om Science Technology Co., Ltd/CN=baidu.com
Ciphers: ECDHE-RSA-AES128-GCM-SHA256
Issuer: /C=BE/O=GlobalSign nv-sa/CN=GlobalSign Organization Validation CA - SHA256 - G2
+ Message: Multiple IP addresses found: 183.232.231.174, 183.232.231.172
+ Start Time: 2020-02-18 20:53:08 (GMT8)
---------------------------------------------------------------------------
+ Server: BWS/1.1
+ Cookie BAIDUID created without the secure flag
+ Cookie BAIDUID created without the httponly flag
+ Cookie BIDUPSID created without the secure flag
+ Cookie BIDUPSID created without the httponly flag
+ Cookie PSTM created without the secure flag
+ Cookie PSTM created without the httponly flag
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'traceid' found, with contents: 158203038802045693549898740171579656555
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The site uses SSL and Expect-CT header is not present.
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Server banner has changed from 'BWS/1.1' to 'Apache' which may suggest a WAF, load balancer or proxy is in place
^C^Z
[1]+ 已停止 nikto -host www.baidu.com -port 443 --ssl
6、namp+nikto
nmap -p 80 192.168.97.0/24 -oG - | nikto -host -
//-oG 输出结果
//- 输出到这里
//nikto -host - 这里的-是之前nmap出的结果
//先nmap扫描哪些ip开了80端口,再使用nikto扫描网站
# nmap -p80 192.168.97.0/24 -oG - | nikto -host -
- Nikto v2.1.6
---------------------------------------------------------------------------
+ nmap Input Queued: 192.168.97.140:80
+ Target IP: 192.168.97.140
+ Target Hostname: 192.168.97.140
+ Target Port: 80
+ Start Time: 2020-02-18 20:54:54 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) DAV/2
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.10
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ /phpinfo.php: Output from the phpinfo() function was found.
+ OSVDB-3268: /doc/: Directory indexing found.
+ OSVDB-48: /doc/: The /doc/ directory is browsable. This may be /usr/doc.
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /phpMyAdmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ Server may leak inodes via ETags, header found with file /phpMyAdmin/ChangeLog, inode: 92462, size: 40540, mtime: Wed Dec 10 01:24:00 2008
+ OSVDB-3092: /phpMyAdmin/ChangeLog: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3268: /test/: Directory indexing found.
+ OSVDB-3092: /test/: This might be interesting...
+ OSVDB-3233: /phpinfo.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpMyAdmin/: phpMyAdmin directory found
+ OSVDB-3092: /phpMyAdmin/Documentation.html: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3092: /phpMyAdmin/README: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ 8726 requests: 0 error(s) and 27 item(s) reported on remote host
+ End Time: 2020-02-18 20:55:19 (GMT8) (25 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
7、总之:发现了以下目录,我们可以在浏览器里依次遍历
/doc
/usr/doc
/test
/icons
/icons/README
/phpMyAdmin
/phpMyAdmin/Documentation.html
/phpMyAdmin/README
8、扫描过程中的一些操作:
//按一下on,再按一下off
回车 报告当前状态
v 查看扫描的过程,不只是看到扫描的结果
d 查看debug信息,最详细的扫描过程
e 查看错误
p 扫描的进度
r 显示重定向
c 显示cookie
a 显示身份认证
q 退出
N 扫下一个
P 暂停扫描
9、nikto的配置文件:/etc/nikto.conf
①、USERAGENT=Mozilla/5.00 (Nikto/@VERSION) (Evasions:@EVASIONS) (Test:@TESTID)
//可以把useragent修改为别的浏览器的useragent,从而隐藏自己
②、RFIURL=http://cirt.net/rfiinc.txt?
//测试远程文件包含的文件
③、Cookie
形如此格式:STATIC-COOKIE="cookie1"="cookie value";"cookie2"="cookie val";
修改为:COOKIE="PHPSESSID"="f78ecdb9ddabf004730e34d1c51dd450";"security"="high"
//其cookie值可以从浏览器里面获得:
第一步:进入浏览器,输入http://192.168.97.140/dvwa
第二步:键入F12(过程中可以多次刷新)
第三步:点击Storage查看cookie,把值给复制下来,粘贴到/etc/nikto.conf的配置文件里
10、nikto -evasion
nikto -host http://192.168.97.140/dvwa -evasion 167
//这里使用了1、6、7规避技术
nikto -host http://192.168.97.140/dvwa -evasion 167
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.97.140
+ Target Hostname: 192.168.97.140
+ Target Port: 80
+ Using Encoding: Random URI encoding (non-UTF8)
+ Using Encoding: TAB as request spacer
+ Using Encoding: Change the case of the URL
+ Start Time: 2020-02-18 21:04:39 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) DAV/2
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ /dvwa/fx29id1.txt: Payload for Fx29ID RFI exploit. The server may have been compromised to act as a repository for this file.
+ Cookie PHPSESSID created without the httponly flag
+ Cookie security created without the httponly flag
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.10
+ 7914 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2020-02-18 21:05:00 (GMT8) (21 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
