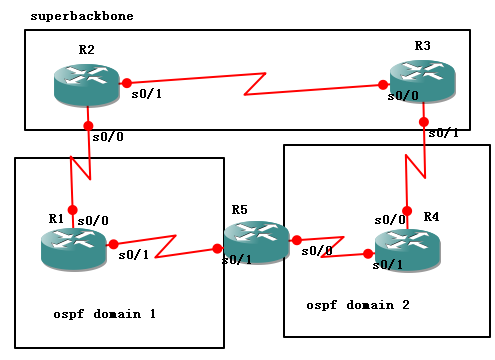
Topology:
实验目的:理解mpls vpn CE,PE运行OSPF时的环路预防机制----Tag Field 。
根据上面的拓扑图,传统的,当PE R2将路由重分发到R1时,R1是带的downbit位的,当R1传播路由到R5时也带有downbit位,但是R5处于ASBR的角色,所以R5到R4的路由是通过重分发学习的,所以是lsa 5类的路由,因为R5传播到R4的路由是不带downbit位的,这样的话,R3会接收来自R4的路由,再传给R2,因为就产生了环路。
OSPF Tage Field就是为了解决这种环路而被设计的。
原理:当R2重发分路由进R1时,不但带有downbit位,还带有tag field。路由传播到R4重分发进R3,此时R3如果看到路由带有tag field的值,会将它与自己的AS号相比较,如果相同,此路由会被拒绝。
step 1.configure the basic configuration of each icon.
| R1: lo 0:1.1.1.1/32 s0/0:12.1.1.1/24 s0/1:15.1.1.1/24 R2: lo 0:2.2.2.2/32 s0/0:12.1.1.2/24 s0/1:23.1.1.2/24 R3: lo 0:3.3.3.3/32 s0/0:23.1.1.3/24 s0/1:34.1.1.3/24 R4: lo 0:4.4.4.4/32 s0/0:34.1.1.4/24 s0/1:45.1.1.4/24 R5: lo 0:5.5.5.5/32 s0/0:45.1.1.5/24 s0/1:15.1.1.5/24 |
step 2.isp igp.isis
| R2: router isis net 49.0001.2222.2222.2222.00 int s0/1 ip router isis int lo 0 ip router isis |
| R3: router isis net 49.0001.3333.3333.3333.00 int s0/0 ip router isis int lo 0 ip router isis |
step 3.mpls
| R2: ip cef mpls label range 2000 2999 mpls label protocol ldp mpls ldp router-id lo 0 int s0/1 mpls ip |
| R3: ip cef mpls label range 3000 3999 mpls label protocol ldp mpls ldp router-id lo 0 int s0/0 mpls ip |
step 4.vrf
| R2: ip vrf vpna rd 100:1 route-target both 100:1 int s0/0 ip vrf forwarding vpna |
| R3: ip vrf vpna rd 100:1 route-target both 100:1 int s0/1 ip vrf forwarding vpna |
step 5.ce igp
| R1: router ospf 100 router-id 1.1.1.1 net 1.1.1.1 0.0.0.0 area 0 net 12.1.1.0 0.0.0.255 area 0 net 15.1.1.0 0.0.0.255 area 0 |
| R2: router ospf 100 vrf vpna router-id 2.2.2.2 net 12.1.1.0 0.0.0.255 area 0 |
| R3: router ospf 200 vrf vpna router-id 3.3.3.3 net 34.1.1.0 0.0.0.255 area 0 |
| R4: router ospf 200 router-id 4.4.4.4 net 4.4.4.4 0.0.0.0 area 0 net 34.1.1.0 0.0.0.255 area 0 net 45.1.1.0 0.0.0.255 area 0 |
| R5: router ospf 100 net 15.1.1.0 0.0.0.255 area 0 router ospf 200 net 45.1.1.0 0.0.0.255 area 0 red ospf 100 subnets |
step 6.mp-bgp
| R2: router bgp 23 no au no sy bgp router-id 2.2.2.2 no bgp default ipv4-unicast nei 3.3.3.3 remote-as 23 nei 3.3.3.3 update-source lo 0 address-family vpnv4 nei 3.3.3.3 activate exit |
| R3: router bgp 23 no au no sy bgp router-id 3.3.3.3 no bgp default ipv4-unicast nei 2.2.2.2 remote-as 23 nei 2.2.2.2 update-source lo 0 address-family vpnv4 nei 2.2.2.2 activate exit |
step 7.redistributable
| R2: router bgp 23 address-family ipv4 vrf vpna no au no sy red ospf 100 exit router ospf 100 vrf vpna red bgp 23 subnets |
| R3: router bgp 23 address-family ipv4 vrf vpna no au no sy red ospf 200 exit rotuer ospf 200 vrf vpna red bgp 23 subnets |
step 8.observe tag-field
| R4#sh ip ospf database external 1.1.1.1 OSPF Router with ID (4.4.4.4) (Process ID 200) Type-5 AS External Link States LS age: 9 Options: (No TOS-capability, DC) LS Type: AS External Link Link State ID: 1.1.1.1 (External Network Number ) Advertising Router: 3.3.3.3 LS Seq Number: 80000001 Checksum: 0xFE7C Length: 36 Network Mask: /32 Metric Type: 2 (Larger than any link state path) TOS: 0 Metric: 65 Forward Address: 0.0.0.0 External Route Tag: 3489660951 |
从RFC中可以看到tag field的格式:
0 0 0 0 0 0 0 0 0 0 1 1 1 1 1 1 1 1 1 1 2 2 2 2 2 2 2 2 2 2 3 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|a|c|p l| ArbitraryTag | AutonomousSystem |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
可以看到后16位是AS号,可以得到,
3489660951的二进制:11010000000000000000000000010111
后十六位:0000000000010111等于十进制,23
23是ISP内的BGP AS号,因此当ISP收到R4关于R1的路由带有相同的AS号,将会拒绝,从而避免了以上场景中的环路。