一、组网需求
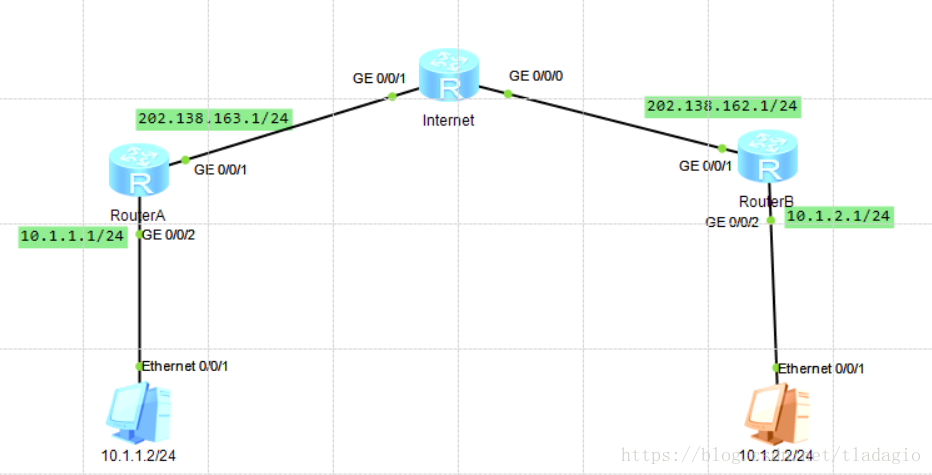
1、如图所示,RouterA为企业分支网关,RouterB为企业总部网关,分支与总部通过公网建立通信。分支子网为10.1.1.0/24,总部子网为10.1.2.0/24。
企业希望对分支子网与总部子网之间相互访问的流量进行安全保护。分支与总部通过公网建立通信,可以在分支网关与总部网关之间建立一个IPSec隧道来实施安全保护。由于维护网关较少,可以考虑采用手工方式建立IPSec隧道。
2、网络拓扑
3、采用如下思路配置采用手工方式建立IPSec隧道:
配置接口的IP地址和到对端的静态路由,保证两端路由可达。
配置ACL,以定义需要IPSec保护的数据流。
配置IPSec安全提议,定义IPSec的保护方法。
配置安全策略,并引用ACL和IPSec安全提议,确定对何种数据流采取何种保护方法。
在接口上应用安全策略组,使接口具有IPSec的保护功能。
二、操作步骤
1、配置接口IP地址
<Huawei>system-view
[Huawei]sysname RouterA
[RouterA]interface GigabitEthernet 0/0/2
[RouterA-GigabitEthernet0/0/2]ip address 10.1.1.1 24
[RouterA-GigabitEthernet0/0/2]q
[RouterA]interface GigabitEthernet 0/0/1
[RouterA-GigabitEthernet0/0/1]ip address 202.138.163.1 24
[RouterA-GigabitEthernet0/0/1]q
<Huawei>system-view
[Huawei]sysname RouterB
[RouterB]interface GigabitEthernet 0/0/1
[RouterB-GigabitEthernet0/0/1]ip address 202.138.162.1 24
[RouterB-GigabitEthernet0/0/1]q
[RouterB]interface GigabitEthernet 0/0/2
[RouterB-GigabitEthernet0/0/2]ip address 10.1.2.1 24
[RouterB-GigabitEthernet0/0/2]q
<Huawei>system-view
[Huawei]sysname Internet
[Internet]interface GigabitEthernet 0/0/1
[Internet-GigabitEthernet0/0/1]ip address 202.138.163.2 24
[Internet-GigabitEthernet0/0/1]q
[Internet]interface GigabitEthernet 0/0/0
[Internet-GigabitEthernet0/0/0]ip address 202.138.162.2 24
[Internet-GigabitEthernet0/0/0]q2、配置静态路由
[RouterA]ip route-static 202.138.162.0 255.255.255.0 202.138.163.2
[RouterA]ip route-static 10.1.2.0 255.255.255.0 202.138.163.2
[RouterB]ip route-static 202.138.163.0 255.255.255.0 202.138.162.2
[RouterB]ip route-static 10.1.1.0 255.255.255.0 202.138.162.2
[Internet]ip route-static 10.1.2.0 255.255.255.0 202.138.162.1
[Internet]ip route-static 10.1.1.0 255.255.255.0 202.138.163.13、在Router上配置ACL,定义各自要保护的数据流
[RouterA]acl number 3001
[RouterA-acl-adv-3001]rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
[RouterA-acl-adv-3001]q
[RouterB]acl number 3001
[RouterB-acl-adv-3001]rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[RouterB-acl-adv-3001]q4、在Router上创建IPSec安全提议
[RouterA]ipsec proposal tran1
[RouterA-ipsec-proposal-tran1]esp authentication-algorithm sha1
[RouterA-ipsec-proposal-tran1]quit
[RouterB]ipsec proposal tran1
[RouterB-ipsec-proposal-tan1]esp authentication-algorithm sha1
[RouterB-ipsec-proposal-tan1]quit查看
[RouterA]display ipsec proposal name tran1
IPSec proposal name: tran1
Encapsulation mode: Tunnel
Transform : esp-new
ESP protocol : Authentication SHA1-HMAC-96
Encryption DES5、在Router上配置手工方式安全策略
[RouterA]ipsec policy map1 10 manual
[RouterA-ipsec-policy-manual-map1-10]security acl 3001
[RouterA-ipsec-policy-manual-map1-10]proposal tran1
[RouterA-ipsec-policy-manual-map1-10]tunnel remote 202.138.162.1
[RouterA-ipsec-policy-manual-map1-10]tunnel local 202.138.163.1
[RouterA-ipsec-policy-manual-map1-10]sa spi outbound esp 12345
[RouterA-ipsec-policy-manual-map1-10]sa spi inbound esp 54321
[RouterA-ipsec-policy-manual-map1-10]sa string-key outbound esp simple abc
[RouterA-ipsec-policy-manual-map1-10]sa string-key inbound esp simple cba
[RouterA-ipsec-policy-manual-map1-10]quit
[RouterB]ipsec policy use1 10 manual
[RouterB-ipsec-policy-manual-use1-10]security acl 3001
[RouterB-ipsec-policy-manual-use1-10]proposal tran1
[RouterB-ipsec-policy-manual-use1-10]tunnel remote 202.138.163.1
[RouterB-ipsec-policy-manual-use1-10]tunnel local 202.138.162.1
[RouterB-ipsec-policy-manual-use1-10]sa spi outbound esp 54321
[RouterB-ipsec-policy-manual-use1-10]sa spi inbound esp 12345
[RouterB-ipsec-policy-manual-use1-10]sa string-key outbound esp simple cba
[RouterB-ipsec-policy-manual-use1-10]sa string-key inbound esp simple abc
[RouterB-ipsec-policy-manual-use1-10]quit查看
[RouterA]display ipsec policy name map1
===========================================
IPSec policy group: "map1"
Using interface:
===========================================
Sequence number: 10
Security data flow: 3001
Tunnel local address: 202.138.163.1
Tunnel remote address: 202.138.162.1
Qos pre-classify: Disable
Proposal name:tran1
Inbound AH setting:
AH SPI:
AH string-key:
AH authentication hex key:
Inbound ESP setting:
ESP SPI: 54321 (0xd431)
ESP string-key: cba
ESP encryption hex key:
ESP authentication hex key:
Outbound AH setting:
AH SPI:
AH string-key:
AH authentication hex key:
Outbound ESP setting:
ESP SPI: 12345 (0x3039)
ESP string-key: abc
ESP encryption hex key:
ESP authentication hex key: 6、在Router接口上引用安全策略组
[RouterA]interface GigabitEthernet 0/0/1
[RouterA-GigabitEthernet0/0/1]ipsec policy map1
[RouterA-GigabitEthernet0/0/1]quit
[RouterB]interface GigabitEthernet 0/0/1
[RouterB-GigabitEthernet0/0/1]ipsec policy use1
[RouterB-GigabitEthernet0/0/1]quit7、验证结果
配置成功后,在主机PC10.1.1.2上执行ping操作仍然可以ping通主机PC 10.1.2.2,执行命令display ipsec statistics esp可以查看数据包的统计信息
[RouterA]display ipsec sa
===============================
Interface: GigabitEthernet0/0/1
Path MTU: 1500
===============================
-----------------------------
IPSec policy name: "map1"
Sequence number : 10
Acl Group : 3001
Acl rule : 0
Mode : Manual
-----------------------------
Encapsulation mode: Tunnel
Tunnel local : 202.138.163.1
Tunnel remote : 202.138.162.1
Qos pre-classify : Disable
[Outbound ESP SAs]
SPI: 12345 (0x3039)
Proposal: ESP-ENCRYPT-DES-64 ESP-AUTH-SHA1
No duration limit for this SA
[Inbound ESP SAs]
SPI: 54321 (0xd431)
Proposal: ESP-ENCRYPT-DES-64 ESP-AUTH-SHA1
No duration limit for this SA